Ports, Services, and Applications
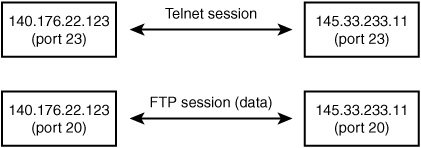
| If all applications that used the network only identified the destination for their data exchange as a single IP address, the information would arrive at the destination computer, but it would be almost impossible for the targeted system to figure out which process to give the data to. Both the TCP and the UDP protocols use port numbers to solve this problem. Each application that communicates on the network using TCP/IP also specifies a port number on the target computer. The port numbers are endpoints for the communications path so that two applications communicating across the network can identify each other. Think of a street address for a business. If all the mail arrived simply addressed with the street address, how would you determine who should get each letter? A person's name or the suite or room number is used so that the endpoint of the communication becomes more fully defined. This is how ports work. For example, suppose you've established a Telnet session with a remote computer and decide you want to download a file to that computer. Telnet doesn't transfer files, so you would have to open an FTP connection. Because the source and destination addresses would be the same in the IP packet for both of these sessions, port numbers are used to indicate the application. When you combine an address with a port number, you have an identifier that can uniquely identify both endpoints of a communication. The name used for this combination of numbers is a socket. This is illustrated in Figure 24.10, in which two computers have established two communication sessions, one for Telnet (port 23) and one for FTP (port 20). FTP actually uses two portsport 20 for sending data and port 21 for exchanging command information. Figure 24.10. A socket is composed of an address and port number, and uniquely identifies an endpoint of a network connection. It should quickly become apparent to you why a packet filter would find these port numbers useful. Instead of having to permit or deny packets based only on their source or destination addressand thereby allow or disallow all communicationsit is possible to selectively allow or disallow individual services. Although you might not want your users to Telnet to a remote host computer (or vice versa), you might not care if they exchange files through anonymous FTP sessions. By using port numbers in packet filtering rules, you can enable or disable network services one at a time. Well-Known PortsThe Internet Corporation for Assigned Names and Numbers (ICANN) is the organization that controls the first range of port numbers that are available (01023), and these are usually called "well-known ports." The use for these ports has been defined in several RFCs, most recently RFC 1700. However, in January 2002, RFC 3232, "Assigned Numbers: RFC 1700 Is Replaced by an On-line Database," made RFC 1700 obsolete. Instead, RFC 3232 is a simple memo which states that port numbers will be maintained in an online database that you can access via the IANA Web site. Note In the original BSD implementation of TCP/IP, port numbers from 0 to 1023 were called privileged ports. That is, programs that run as root (or "superuser") on the Unix machine use them. These "programs" are usually just the server program for a particular application. Following this convention, client programs would choose a port number that was greater than 1023. Note The Internet Corporation for Assigned Names and Numbers (ICANN) was created in 1998 as a technical coordination body for the Internet. ICANN assumed most of the functions that were previously performed by the Internet Assigned Numbers Authority (IANA). In addition to taking responsibility for port numbers, ICANN also is responsible for managing how Internet domain names, IP addresses, and protocol parameters are managed and assigned. At this time IANA is still responsible for some of these functions, such as managing registered port numbers, among other tasks. You can learn more about ICANN by visiting its home page at www.icann.org. You can learn more about IANA by visiting its site at www.iana.org. Well-known ports are usually accessible on a given system by a privileged process or privileged users. For example, the FTP utility uses ports 20 and 21, whereas the Telnet utility uses port 23. In most cases the User Datagram Protocol (UDP) and Transmission Control Protocol (TCP) make the same use of a particular port. This is not required, however. Understanding the application that a port is used for can be useful when deciding which ports to block when building a firewall. Some of these applications will never be used by your system, and because of that, there exists no good reason to allow network traffic through the firewall that uses these ports. Registered PortsPorts numbered from 1024 to 65535 also can be used but are not reserved by IANA. These ports are called registered ports and can be used by most any user process on the system. |
EAN: 2147483647
Pages: 411