Configuring SSL on Tomcat
The connector for the service that supports HTTPS connections must have its secure attribute set to true and its scheme attribute set to https.
Listing 9-2 shows the SSL connector from server.xml. Note that it’s commented out by default. Uncomment it, and make changes if required. If you change the SSL port (8443) to something else, you need to change the redirectPort attribute for all the non-SSL connectors to that port number, too. The non-SSL connectors redirect users to this port if they try to access pages with a security constraint that specifies that SSL is required.
Listing 9-2: The Default SSL Connector
<!-- Define a SSL Coyote HTTP/1.1 Connector on port 8443 --> <!-- <Connector port="8443" maxThreads="150" minSpareThreads="25" maxSpareThreads="75" enableLookups="false" disableUploadTimeout="true" acceptCount="100" debug="0" scheme="https" secure="true" clientAuth="false" sslProtocol="TLS" /> -->
For details of these attributes, see Chapter 4. The two important attributes here are scheme and secure. As noted previously, they’re used to indicate that this is an SSL-enabled connector.
Working with Keystores
To use an SSL connector with Tomcat, you’ll need to create a keystore. This contains the server’s digital certificates, which are used by clients to validate the server. Once clients have accepted a certificate, they can use the public key it contains to encrypt any data it wants to send. The server for its part holds a private key, which is the only way to decrypt the data. Chapter 12 covers this subject, as well as all aspects of Tomcat security, in more detail. I’ll leave the details until then, but this chapter will get your SSL connector up and running.
| Note | If you’re using JDK 1.3 or older, you’ll need to install Java Secure Socket Extension (JSSE). Download the API from http://java.sun.com/products/jsse/, and install the JAR files from JSSE_HOME/lib to JAVA_HOME/jre/lib/ext or set a JSSE_HOME environment variable to point to the location of JSSE. |
To create the keystore, use the following command (assuming the JAVA_HOME/bin directory is in your path). keytool is a utility that comes as part of the J2SE distribution.
> keytool -genkey -alias tomcat -keyalg RSA
This creates a public-private key pair (-genkey), for user tomcat, with the RSA algorithm. The MD5 algorithm is also available, but RSA is recommended for Web use because of its compatibility with other Internet-aware applications. This method creates what’s called a selfsigned certificate. If you were serious about your security, you’d use a certificate issued by a certificate authority, a process that’s discussed in Chapter 12. For now, you can test the mechanism with a self-signed certificate.
You’ll be asked for a password; make sure you specify something other than the default. Once you’ve done this, you’ll be asked for some details. The first and last name question is really asking for the name of your host. If you don’t put the name of your host, then clients will be warned and the certificate may not be accepted, as shown in Figure 9-1.
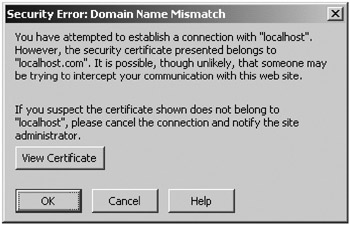
Figure 9-1: A browser warning that the certificate may not be trustworthy
Finally, add the password for the keystore to the SSL connector’s entry in server.xml, as shown in Listing 9-3.
Listing 9-3: Adding a Keystore Password to server.xml
<Connector port="8443" maxThreads="150" minSpareThreads="25" maxSpareThreads="75" enableLookups="false" disableUploadTimeout="true" acceptCount="100" debug="0" scheme="https" secure="true" clientAuth="false" sslProtocol="TLS" keystorePass="tomcat"/>
Now start Tomcat, and visit https://localhost:8443. You’ll be asked to accept the certificate because it’s likely that your browser doesn’t recognize your organization as a certificate authority. If you accept the certificate, you can continue to Tomcat’s home page and view it using an SSL connection.
EAN: 2147483647
Pages: 94