Making Sure (Internet) Drivers Have Valid Drivers Licenses
Making Sure (Internet) Drivers Have Valid Drivers' LicensesBefore you can legally drive on public roads, you need a valid driver's license. The license identifies you by name, number, and photo. Similarly, when using networks, you might be asked to verify your identity so that the network can confirm that you are allowed, or licensed, to use the network. For instance, if you've ever used a network before, you have probably been prompted for a username and password (authentication). Most people who have used web browsers figure that they can't look at some web pages that aren't appropriate for their jobs or check someone else's e-mail (authorization). And although users never see a report of foiled attempts to guess a password, you have to figure that a good security policy involves watching out for such mischief (accounting). The examples in this chapter so far presume that the PC is attached to a LAN in a physically secure office building. But people who use modems or DSL to connect to the Internet from home have to go through an additional authentication step. ISPs want to know that a user who connects to them has paid her bill, and they want to make sure they know who the user is, just in case she breaks the rules of what's legally allowed to happen over the ISP's Internet connection. In the next two sections, you'll read about how ISPs authenticate users before they can even use the network, and how the protocols prevent someone from stealing the password. No Appls Yet? Be a Good CHAP and Ask PAPEarlier in this chapter, you read briefly that the servers ask the user for his username and password. The protocols that exchange the username and password are built in to most of the application layer protocols. For instance, back in Chapter 8, "Shipping Goods over a (Network) Roadway," you read about POP3 and the messages that a POP3 server uses to ask the POP3 client for the username and password. ISPs want to authenticate the user, but it's better if they can authenticate before the user even tries to use an application. ISPs can't count on every one of their customers to have a web browser (some might just use e-mail), or they might have customers who just use a web browser but not e-mail. All the ISP wants to do is authenticate whether the user is allowed to connect, and more important, whether the user has paid the monthly service fee. As a result, the ISP has two issues regarding user authentication:
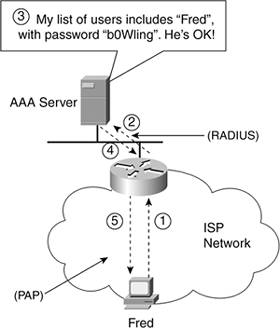
To solve the problem, ISPs use part of Point-to-Point Protocol (PPP), which defines two options for the exchange of username and password information. The names appear in the title to this sectionPAP and CHAP. Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP) are both parts of PPP, and you know from the past several chapters that PPP is a data link protocol that's often used in WAN connections, particularly when using modems or DSL to connect to the Internet. Both PAP and CHAP provide a protocol for the exchange of the username and password. Figure 17-4 shows the basic process PAP uses for username and password exchange. Figure 17-4. Basics of PAP
The process is indeed as simple as what's shown in the figure. The PAP protocol uses a two-way flow of messages, with other messages and events happening in the background:
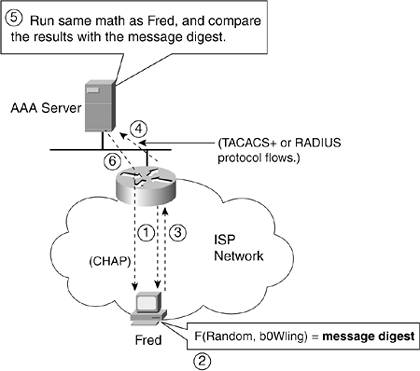
In this example, when Fred dials the Internet with a modem, PAP is used between himself and the ISP router. However, a protocol called RADIUS (RFC 2865) is used between the router and the AAA server to authenticate Fred's username and password. Although PAP and RADIUS are shown in Figure 17-4, other protocols can be used, too. TACACS+ is a popular proprietary protocol that Cisco developed before RADIUS existed and can be used in place of RADIUS. Also, CHAP can be used instead of PAP between the end user device and the ISP router. In the next section, you'll read about how the CHAP and PAP protocols are different. Stopping Someone from Using Your License (Password)Although most everyone reading this book probably has a valid driver's license, some people use fake, illegal driver's licenses. One way to make a fake driver's license work well, even when you are pulled over by a policeman, is to use a name and driver's license number of someone who has a real, valid driver's license. Sending your passwords using PAP is similar to letting everyone know your driver's license number. It's not likely that someone will make a fake driver's license using your number right away, but you are exposed to the possibility. PAP sends the username and password in clear-text. That means anyone with the right tools can actually read your username and password, as clear as you can see the words on this page. Remember: The cable over which your packets flow is between your house and the central office (CO), so it's not too hard to imagine that someone could gain physical access to your phone line and figure out the data you are sending over the wire. All someone would have to do is walk up to the side of your house and use the right tools, and he would know what bits you are sending to and from the Internet. People can use tools to see your frames that cross a LAN as well. You can attach a type of device called a network analysis tool, often called a sniffer, to a LAN to capture the frames crossing the LAN. If the protocols that transfer the usernames and passwords worked like PAP, and sent the passwords as clear-text, people could find your passwords using a sniffer. I have seen passwords dozens of times while using a sniffer (without trying)it's that easy. (Sniffer is a trademark of the Network Associates Corp.; the word sniffer is somewhat synonymous with this type of analysis and packet capture tool.) You can download free analysis tools from Internet sites and make any PC work like a sniffer. To protect against password theft, CHAP does not send the password as clear-text. Many application protocols also work similarly to CHAP, not sending the passwords in clear-text. So, whether your PC is offered a username and password prompt when you connect to the Internet, or whether you are providing a password to a web server, the protocols often don't send the password as clear text. The process of using CHAP starts when the ISP customer first connects to the ISP. With modems, that occurs when the customer clicks something on the computer that causes the modem to call a phone number at the ISP. With DSL, that happens as soon as the DSL modem comes up again after being powered off. Outwardly, the user experiences the same thing: He is prompted for his username (Fred) and password (b0Wling). (Some users set up their software so that they type in the username and password once, and then it's saved, so you might not be prompted every time you connect to the Internet.) If the username and password are correct and the account is current/paid, the ISP approves the connection. If the username or password are wrong, the ISP typically hangs up if it's a modem connection; if it's a DSL connection, the ISP just doesn't allow the PPP data link protocol to keep working. Regardless of the detail, as with other authetication tasks, the user can continue working only if the username and password are correct. CHAP has many useful features, including a way to prevent the password from being by someone using a sniffer. Figure 17-5 shows several steps about what happens behind the scenes with CHAP, including how it keeps the password private. Figure 17-5. Hashing Passwords to Create a Message Digest
The figure shows six steps that are used in this case to authenticate the user, but the password never passes over the network; therefore, even if someone captures all the packets, it doesn't allow him to steal Fred's identity. The clear-text password is configured at the ISP, typically in a AAA server. The user knows the password and types it in. However, rather than sending the password, the PC sends in a message digest. A message digest is the result of running a mathematical function that has two inputs: the password and a random number. To see how it works, compare these points to the points in Figure 17-5:
It seems laborious, but it works quickly, and it works well. Notice that the password never passed through a network connection. This scheme works well because even if someone has a sniffer or another tool and captures the packets, it doesn't matter. The math function that's used to create the message digest is purposefully chosen so that it's hard to calculate the original password, even knowing both the mathematical function and the random number. And the next time the PC needs to authenticate, the router will send a new random number, causing a new message digest value to be calculated. |
EAN: 2147483647
Pages: 173