The VLAN Trunk Protocol (VTP)
| The VLAN Trunking Protocol (VTP) is used to provide administrators an easy way of managing VLANs across a Cisco switched network. VTP enables you to configure a VLAN on one switch and have the information propagate to all of your switches in a VTP domain. This enables an administrator to fairly easily add, delete, and rename VLANs . One of the best features of VTP is its ability to maintain consistent VLAN configurations throughout the network. VTP keeps an identical VLAN configuration by propagating the VLAN mapping scheme of the VTP domain across the network. VTP provides for a plug-and-play type of connection. When you add additional VLANs, VTP provides tracking, monitoring, and reporting of VLANs in the network.
In IOS version 3.1(1) of the Catalyst software, a second version of VTP was introduced, thereby making two versions: version 1 and version 2. The primary differences between the two versions are significant enough to render them incompatible. They will not work together in the same network.
Version 1 is the default on Cisco Catalyst switches. If all the switches in the network support VTP version 2, then only one switch needs to have version 2 enabled in order to enable version 2 on all the switches participating in a VTP domain. Version 2 provides the following additional features beyond support for Ethernet:
Switches in a VTP management domain share VLAN information through the use of VTP advertisement messages. Three types of advertisement messages exist:
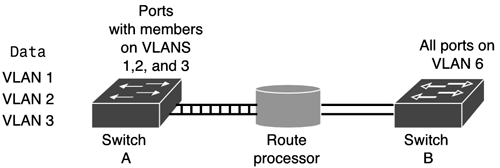
VTP AdvertisementsVTP advertisement frames are sent to a multicast address so that all the VTP devices in the same management domain are able to receive the frames . All VTP management domain clients and servers update their databases regarding all deletions and additions to the network, based on information contained in the VTP advertisements and the revision number contained in the advertisements the switch receives. Each advertisement contains a revision number, which is one of the most important parts of the VTP advertisement. When a new VTP revision number is sent throughout the VTP domain, the switches believe that the highest revision number has the most up-to-date information about all the VLANs. If a switch participating in a VTP domain receives an advertisement with different VLAN configuration information than it currently has, it updates its information only if the revision number in the received advertisement is higher than the one that allowed the last change. As a VTP server's database is modified, the VTP server increments the revision number by 1. The VTP server then advertises this information from the database with the new configure revision number. Inter-VLAN RoutingVTP aids in propagating VLAN information, and trunk links allow for the traffic from more than one VLAN to traverse a link. How do switches use these trunk links to allow VLANs to communicate with one another? Through a process called inter-VLAN routing, which is explained in this section of the chapter. Trunking protocols are designed to allow VLANs to flow from one networking device to another. These trunking protocols either tag the VLAN frames or add a header that uniquely identifies the source and destinations of the data as well as the VLAN the data is a member of. If data from one VLAN needs to be forwarded to another VLAN, it requires some type of Layer 3 device to do the routing. This process is shown in Figure 9.2, in which switch A is sending data from VLANs 1 through 3 to VLAN 6, which is configured on switch B. Figure 9.2. An inter-VLAN routing process. To route VLAN frames between VLANs requires a Layer 3 device, which can be an external router or any number of modules known as internal route processors that are located inside a switch. When a node needs to communicate with a member of another VLAN on the same network, the node sends a packet to the other node, assuming that it resides on the same network. The packet destined for another VLAN, which can even be another port on the same switch, must find a path on which to send the frame. Because switches operate at Layer 2 and are designed to isolate traffic to broadcast domains or subnets, they cannot, by default, forward data from one VLAN to another VLAN without some other Layer 3 device, such as an internal or external route processor. The Layer 3 device is known as a "router on a stick." This device is used to route the data and create routing tables of other networks and devices. This also adds a layer of security, because now access lists can be added to permit and deny certain traffic. Route processors can be used to route data between foreign VLANs and other logically segmented parts of the network, such as subnets. They also route data to remote WAN segments, networks, or the Internet. An internal route processor uses internal modules or cards located inside the switch chassis that are similar to routers to route data between VLANs. The following are some of the available types of internal route processors for Catalyst switches:
The following series of routers are external route processors with 100BaseT interfaces that support ISL:
VLAN ConfigurationBy configuring VLANs, you control the size of your broadcast domains and keep local traffic local. A problem is created, however, when an end station in one VLAN needs to communicate with an end station in another VLAN. To fix the problem, inter-VLAN routing needs to take place to resolve the address, even if the ports belonging to different VLANs are side by side in the same switch. This type of communication is called inter-VLAN routing , where a Layer 3 device resolves the address just as it would if they were nodes residing on two different network segments. You configure one or more routers to route traffic to the appropriate destination VLAN. All ports on the switch are configured as static access ports to VLAN 1 by default. VLAN 1 is also assigned as the default management VLAN. You can change the VLAN port information using the console, Cisco Visual Switch Manager (CVSM), or SNMP. This section covers the basics of VLAN configuration, as well as how to assign multi-VLAN memberships and how to view the configuration on each type of switch. It also covers configuring VLANs on a Set/Clear commandbased switch, as well as on a CLI-based switch. The following are the available options for the set vlan command: set vlan <vlan_num> [name <name>] [type <type>] [state <state>][said <said>] [mtu <mtu>] [ring <hex_ring_number>][decring <decimal_ring_number>][bridge <bridge_number>] [parent <vlan_num>][mode <bridge_mode>] [stp <stp_type>] [translation <vlan_num>] [backupcrf<offon>][aremaxhop <hopcount>] [stemaxhop <hopcount>] To begin configuring the VLANs, you need to be in Privileged Mode on your switch and identify an interface on the switch. If you have a 12-port 10/100 module in slot 7 of a Catalyst 5500 series switch that has 13 available slots, the ports are referred to as "7/112." Most of the commands on this series of switches use this method to identify the interface. Cisco routers begin with slot and port numbers that start at 0. On the Cisco Catalyst 4000, 5000, and 6000 families of switches, the slot and port numbers start at 1. The first port on a Cisco router would be 0/0, but on a Catalyst 5500, it would be 1/1. To configure the four ports on VLAN 3 for ports 3 through 6 on the module residing in slot 7, use these commands: set vlan <vlan_num> <mod/ports> set vlan 3 7/3 set vlan 3 7/4 set vlan 3 7/5 set vlan 3 7/6 You could also use a shortcut and configure all the ports at once by using this command: set vlan 3 7/3-6
You can assign a VLAN a name that is up to 32 characters to help identify it when doing troubleshooting. To assign VLAN 3 and identify it as the VLAN that engineers use, use the following command: set vlan <vlan_num> name <name> set vlan 3 name Engineering You can set the type of VLAN using one of the valid types, which are ethernet , fddi , fddinet , trcrf , and trbrf . The default is Ethernet if a type is not specified. Use the following command to map VLAN 3 to Ethernet: set vlan <vlan_num> type <type> set vlan 3 type ethernet Active is the default state for a configured VLAN, but you can configure it for active or suspend . Use the following command to suspend VLAN 3: set vlan <vlan_num> state <state> set vlan 3 state suspend SAIDs are used as a VLAN identifier when trunking across 802.10 FDDI or CDDI networks. The default SAID value is 100000 plus the VLAN number. For example, VLAN 3's SAID would be a value of 100003. You should be able to leave the SAID at the configured default. However, if a conflicting SAID exists in the network, you can use the following command to change the SAID to 100103: set vlan <vlan_num> said <said> set vlan 3 said 100103 Different media types have different maximum transmission unit (MTU) sizes. Ethernet, for example, is 1,500 bytes. If you need to change the MTU, use the following command: set vlan <vlan_num> mtu <mtu> set vlan 3 mtu 1500 If a node on the network is attached to a port on the switch and does not have the ability to negotiate the port speed, you can set the speed. To set the port speed manually, use the following command: set port speed <mod_num/port_num> <41016100auto> set port speed 7/1 100 To set the port duplex on an Ethernet module, use the following command: set port duplex <mod_num/port_num> <fullhalf> set port duplex 7/1 full
Enabling security on a Catalyst switch means that the switch will accept frames only from a particular MAC address on Ethernet modules. You can identify a specific MAC address. If the MAC address is not identified, the first interface to use the port will be the only interface allowed to use that port. If an unauthorized MAC address attempts to use the port, the port will become disabled and the light on the switch corresponding with that port will change from the color green to orange. To configure port security, use the following command: set port security <mod_num/port_num> <enabledisable> [mac_addr] set port security 3/1 enable To verify the configured VLAN information, at the Privilege EXEC Mode prompt, you can use the show vlan command, which is used for all Catalyst switches: show vlan To remove a VLAN configured on a port, at the Privilege EXEC Mode prompt, you can use the following command (the VLAN being removed is VLAN 3, affecting all ports that have VLAN 3 configured): clear vlan 3
Configuring VLAN TrunksVLAN trunks can be configured between two switches, between two routers, or between a switch and a router. In some special circumstances, a file server has an ISL- or 802.1Q-aware NIC card that understands VLAN tagging. One thing to be aware of when configuring a trunk is that your device needs to be able to handle the load so that the introduction of latency doesn't affect your network devices. This latency will not be noticeable on small data files, but it will be very noticeable when you're using voice or video if your equipment cannot handle the load placed upon it. Before you create a trunk, you must understand some of the main pieces of the trunk sub variables . You must know whether the trunking method to be used is 802.1Q, 802.10, ISL, LANE, or negotiate.
For Fast Ethernet or Gigabit Ethernet, you set the trunking mode for each port as well as the protocol to use. To configure the domain name and set the password on the switch, use the following command in Privileged Mode (the name DCS refers to the switch domain name, and the password is set to 1234): set vtp domain dcs passwd 1234
To see the VTP domain information, use the following show command from the Privileged Mode prompt: show vtp domain The output will look similar to this: Domain Name Domain Index VTP Version Local Mode Password DCS 1 2 server - Vlan-count Max-vlan-storage Config Revision Notifications 12 1023 8 disabled Last Updater V2 Mode Pruning PruneEligible on Vlans 172.1.1.1 disabled disabled 2-1000 To set the VTP mode to Server, Client, or Transparent Mode, use the following Privileged Mode command ( DCS refers to the domain that the switch will join): set vtp domain <domain name> mode [clientservertransparent] set vtp domain DCS mode server
Use the following command to configure a trunk port. The port being configured is on module 3, port 1, and the VLAN range is VLANs 2 through 12: set trunk <mod_num/port_num> [onoffdesirableautononegotiate] <vlan_range> [isldot1qdot10lanenegotiate] set trunk 3/1 desirable 2-12 isl To remove a VLAN from a trunk, use the following Privileged Mode command (in this demonstration, the module number is 3 and the port number is 1; the VLAN being removed is 13): Clear trunk <mod_num/port_num> <vlan_range> Clear trunk 3/1 13 For more than one VLAN, such as VLANs 13 through 200, issue the following Privileged Mode command: Clear trunk 3/1 13-200 To display all the trunks configured on the switch, use the following command in Privileged Mode: Switch> (enable) show trunk The output should look similar to this: Port Mode Encapsulation Status Native vlan ---- ---- ------------- ------ ----------- 1/1 desirable isl trunking 1 2/1 desirable isl trunking 1 2/2 desirable isl trunking 1 2/3 desirable isl trunking 1 3/1 desirable isl trunking 1 Port Vlans allowed on trunk ---- ---------------------- 1/1 1-100,1003-1005 2/1 1-100,1003-1005 2/2 1-100,1003-1005 2/3 1-100,1003-1005 3/1 1-100,1003-1005 Port Vlans allowed and active in management domain ---- --------------------------------------------- 1/1 1,6-9,1003-1005 2/1 1,6-9,1003-1005 2/2 1,6-9,1003-1005 2/3 1,6-9,1003-1005 3/1 1,6-9,1003-1005 Port Vlans in spanning tree forwarding state and not pruned ---- ------------------------------------------------------ 1/1 1,1003-1005 2/1 1,1003-1005 2/2 1,1003-1005 2/3 1,1003-1005 3/1 1,1003-1005 To get a statistical view of the VTP traffic, use the following command: show vtp statistics VTP PruningVTP pruning enhances the network's bandwidth by reducing unnecessary network traffic. VTP restricts flooded data traffic to those trunk links that the traffic must use to access the appropriate network devices. By default, VTP pruning is disabled. VTP pruning requires all switches to be set to Server Mode, and also requires the establishment of the same common VTP domain between all the switches. To enable pruning on a Set/Clear-based switch, use this command in Privileged Mode: set vtp pruning <enabledisable> set vtp pruning enable When you enable VTP pruning, it affects all the VLANs on the switch. If you want to enable VTP pruning only on certain VLANs, first clear the VLAN prune-eligible list using the following command for all VLANs: clear vtp pruneeligible <vlan_range> clear vtp pruneeligible 2-1000 Next , set the VLANs for which you wish to enable pruning: set vtp pruneeligible <vlan_range> set vtp pruneeligible 2-30
Assigning a VLAN Membership to a 1900 Series SwitchOn the 1900 series switch, you must choose "k" from the initial user interface menu to get into command-line interface for the switch IOS, as shown here: 1 user(s) now active on Management Console. User Interface Menu [M] Menus [K] Command Line [I] IP Configuration Enter Selection: k CLI session with the switch is open. To end the CLI session, enter [Exit]. To configure the 1900 series switch ports with VLANs, you must enter global configuration mode, as shown next; to help identify the switch, we will give it the hostname 1912EN : > enable # config terminal Enter configuration commands, one per line. End with CNTL/Z (config)#hostname 1912EN To configure VLANs on an IOS-based switch, use the following command: vlan <vlan> name <vlan name> 1912E(config)#vlan 3 name engineering You can configure each interface (port) on a switch to be in a VLAN by using the vlan-membership command. Unfortunately you must configure VLANs one by one for each port, because no command exists to assign more than one port to a VLAN. The following is the vlan-membership command and its options: 1912EN(config-if)# vlan-membership ? dynamic Set VLAN membership type as dynamic static Set VLAN membership type as static 1912EN(config-if)# vlan-membership static ? <1-1005> ISL VLAN index Static and Dynamic VLANsA static VLAN is the most common type of VLAN and the easiest to administer. The switch port always remains in the VLAN that is assigned by an administrator until an administrator changes the port assignment. Static VLAN configurations allow for VLAN configurations that are easy to configure and monitor, and that work well in a network in which the movement of users within the network remains controlled. You can also use network management software, such as CiscoWorks for Switched Internetworks (CWSI), to configure the ports on the switch. This software is available from any Cisco Value Added Reseller (VAR). If you work for a VAR, you can get this software online from the Cisco CCO Web site. A dynamic VLAN determines a node's VLAN assignment automatically using a server called a VLAN Management Policy Server (VMPS) to set up a database of MAC addresses that can be used for dynamic addressing of VLANs. VMPS is a MAC-address-to-VLAN mapping database that contains a database of allowable MAC or physical addresses that are mapped to a particular VLAN. When the user boots up, the switch learns the MAC address and checks the database for the appropriate VLAN assigned to that MAC address. This enables a user to remain in the same VLAN throughout the network regardless of the location in which the user resides. A lot of network management is required to maintain the databases of MAC addresses. Therefore, dynamic VLANs are not very effective in larger networks. Using intelligent network management software enables you to match a VLAN number to a hardware (MAC) address, protocol, or even an application address to create static VLANs. In the following code, you see that the interface configuration mode has been entered for ports 1 and 2, and then the VLAN is assigned two ports: 1912EN(config-if)# interface e0/1 1912EN(config-if)# vlan-membership static 3 1912EN(config-if)# interface e0/2 1912EN(config-if)# vlan-membership static 3 The Catalyst 1900 switch has the same options as the 5000 and 6000 series do for ISL. The 1900 switch does, however, run the Dynamic Inter-Switch Link (DISL) encapsulation method to create trunks. The Cisco Catalyst 1912EN switch has two trunkable ports that are Fast Ethernet ports: Interface 26 (Port A) and Interface 27 (Port B). The following lists the available options of the trunk command and sets the trunk to on for Port B: 1912EN(config)# interface f0/27 1912EN(config-if)# trunk ? auto Set DISL state to AUTO desirable Set DISL state to DESIRABLE nonegotiate Set DISL state to NONEGOTIATE off Set DISL state to OFF on Set DISL state to ON 1912EN(config-if)# trunk on Configuring VLAN and Enabling VTP on the 1900EN Series SwitchTo remove a VLAN from a trunk port on a 1900EN series switch, use the interface configuration mode command no trunk-vlan command. The following takes a look at the syntaxes available and then removes VLAN 3 from its ability to send VLAN traffic across the trunk: 1912EN(config-if)# no trunk-vlan ? <1-1005> ISL VLAN index 1912EN(config-if)# no trunk-vlan 3
To view the trunks on a Cisco Catalyst 1900EN, use the show trunk command just as you would on a 5000 series switch. A difference does exist, however: this command can be used only on Fast Ethernet ports 26 (Port A) and 27 (Port B). The following are the show trunk command options: 1912EN# show trunk ? A Trunk A B Trunk B 1912EN#show trunk a ? allowed-vlans Display allowed vlans joined-vlans Display joined vlans joining-vlans Display joining vlans prune-eligible Display pruning eligible vlans As an example of the show trunk command, look at the allowed VLANs on Port B: 1900EN# show trunk b allowed-vlans 1-3, 6-8 The following lists the options when enabling VTP in global configuration mode on the 1900 series switch: 1912EN(config)# vtp ? client VTP client domain Set VTP domain name password Set VTP password pruning VTP pruning server VTP server transparent VTP transparent trap VTP trap Let's go ahead and configure this switch as a VTP server for the DCS domain, and set the password using the commands in the preceding list: 1912EN(config)# vtp server 1912EN(config)# vtp domain dcs 1912EN(config)#vtp password 1234 Configuring Inter-VLAN Routing on an External RouterWhen a switch receives a packet from a port on one VLAN destined for the port of another VLAN, the switch must find a path on which to send the frame. Switches work at Layer 2 and are designed to isolate traffic to collision domains or subnets; they cannot, by default, forward data from one VLAN to another VLAN or network without some other Layer 3 devices. The Layer 3 device known as a router on a stick is used to route the data and create routing tables of other networks and devices. As discussed earlier in the chapter, route processors can be used to route data between foreign VLANs and other logically segmented parts of the network, such as subnets. They also route data to remote WAN segments, networks, or the Internet. Layer 3 routing takes place between VLANs. This can become a challenging problem for an administrator to overcome. Two types of route processors exist: external and internal. As you learned in the previous section, an external route processor uses an external router (such as the Cisco devices you are familiar with) to route data from one VLAN to another VLAN. An internal route processor uses internal modules and cards located inside the switch route data between VLANs. Each type of Layer 3 routable protocol that does not have to be IP can have its own mapping for a VLAN. In an IP network, each subnetwork is mapped to an individual VLAN. In an IPX network, each VLAN is mapped to the IPX network number. With AppleTalk, a cable range and AppleTalk zone name are associated with each VLAN. By configuring VLANs, you control the size of your broadcast domains and keep local traffic local. However, when an end station in one VLAN needs to communicate with an end station in another VLAN, this communication is supported by inter-VLAN routing. You configure one or more routers to route traffic to the appropriate destination VLAN. To understand this section, you need to become familiar with Cisco IOS software running on Cisco routers. This demonstration is going to configure a Cisco 7505, with the goal of making the process as clear as possible:
To configure inter-VLAN routing for IPX, perform this task beginning in global configuration mode:
|
EAN: 2147483647
Pages: 213
- Chapter I e-Search: A Conceptual Framework of Online Consumer Behavior
- Chapter VIII Personalization Systems and Their Deployment as Web Site Interface Design Decisions
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter X Converting Browsers to Buyers: Key Considerations in Designing Business-to-Consumer Web Sites
- Chapter XIII Shopping Agent Web Sites: A Comparative Shopping Environment