Wireless Access Module
As we have investigated in Chapter 8, wireless presents some significant security problems when used on a corporate network. So much of this insecurity is due to the fact that it can be easy for an unauthorized user to gain access to your WLAN. This presents a huge security risk if the WLAN is directly connected to the internal network, since that user has now effectively circumvented all of your perimeter protections , exposing the soft underbelly of your internal network. Using our Twinkie example, the user is now in the creme filling.
Perhaps the best method to mitigate this security issue is to implement your WLAN not as a module of your internal network but as a module of the perimeter of your network. Figure 11-10 illustrates how to design the wireless access module.
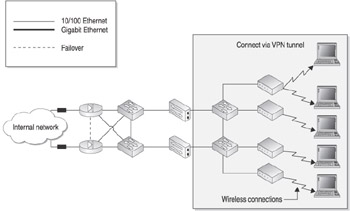
Figure 11-10: Wireless access module
In this configuration, security is provided through the use of VPN connections for the wireless clients . This is performed in addition to any wireless-specific security that is implemented such as Wired Equivalent Privacy (WEP), WiFi Protected Access (WPA), or 802.1x. Once the users are able to establish a wireless connection properly, the users must then use the appropriate VPN client to establish a connection with the VPN concentrators . Only after the VPN has been established will unencrypted traffic be allowed to pass from the concentrator to the firewall. At the firewall you need to implement ingress and egress filtering as in the other modules to ensure that the wireless clients are able to access only the specific resources to which you want to grant access.
EAN: N/A
Pages: 125
- Chapter V Consumer Complaint Behavior in the Online Environment
- Chapter VII Objective and Perceived Complexity and Their Impacts on Internet Communication
- Chapter XI User Satisfaction with Web Portals: An Empirical Study
- Chapter XIII Shopping Agent Web Sites: A Comparative Shopping Environment
- Chapter XIV Product Catalog and Shopping Cart Effective Design