Broadcast-BZT
Broadcast
-
To send information to two or more receiving devices simultaneously ” over a data communications network, voice mail, electronic mail system, local TV/radio station or satellite system. Broadcast involves sending a transmission simultaneously to all members of a group . In the context of an intelligent communications network, such devices could be host computers, routers, workstations, voice mail systems, or just about anything else. In the less intelligent world of "broadcast media," a local TV or radio station might use a terrestrial antenna or a satellite system to transmit information from a single source to any TV set or radio capable of receiving the signal within the area of coverage. See also Narrowcasting and Pointcasting. Contrast with Unicast, Anycast and Multicast.
-
As the term applies to cable television, broadcasting is the process of transmitting a signal over a broadcast station pursuant to Parts 73 and 74 of the FCC rules. This definition is deliberately restrictive : it does not include satellite transmission, and it does not include point-to-multipoint transmission over a wired or fiber network. In spite of the fact that the broadcast industry and the cable television industry are forever bound together in a symbiotic relationship, they are frequently at odds over policy issues. See Broadcast Station. Compare with Cablecast.
Broadcast Channel
BCCH. A wireless term for the logical channel used in certain cellular networks to broadcast signaling and control information to all cellular phones. BCCH is a logical channel of the FDCCH (Forward Digital Control CHannel), defined by IS-136 for use in digital cellular networks employing TDMA (Time Division Multiple Access). The BCCH comprises the E-BCCH, F-BCCH and S-BCCH. The E-BCCH (Extended-BCCH) contains information which is not of high priority, such as the identification of neighboring cell sites. The F-BCCH (Fast-BCCH) contains critical information which must be transmitted immediately; examples include system information and registration parameters. S-BCCH (System message-BCCH), which has not yet been fully defined, will contain messages for system broadcast. See also IS-136 and TDMA.
Broadcast Domain
Set of all devices that receive broadcast frames originating from any device within the set. Broadcast domains typically are bounded by routers because routers do not forward broadcast frames .
Broadcast List
A list of two or more system users to whom messages are sent simultaneously. Master Broadcast Lists are shared by all system users and are set up by the System Administrator. Personal Lists are set up by individual subscribers.
Broadcast Message
A message from one user sent to all users. Just like a TV station signal. On LANs, all workstations and devices receive the message. Broadcast messages are used for many reasons, including acknowledging receipt of information and locating certain devices. On voice mail systems, broadcast messages are important announcement messages from the system administrator that provide information and instructions regarding the voice processing system. Broadcast messages play before standard Voice Mail or Automated Attendant messages.
Broadcast Net
A British Telecom turret feature that allows each trader single key access to a group of outgoing lines. This is designed primarily for sending short messages to multiple destinations. The "net" function allows the user to set up and amend his broadcast group.
Broadcast Quality
A specific term applied to pickup tubes of any type ” vidicon, plumbicon, etc. ” which are without flaws and meet broadcast standards. Also an ambiguous term for equipment and programming that meets the highest technical standards of the TV industry, such as high- band recorders .
Broadcast Station
An over-the-air radio or television station licensed by the FCC pursuant to Parts 73 or 74 of the FCC Rules, or an equivalent foreign (Canadian or Mexican) station. Cable television systems are authorized by FCC rules to retransmit broadcast stations ; however, such retransmission is subject to a number of restrictions:
-
The cable television operator is liable for copyright royalty fees collected by the Copyright Office.
-
Under certain conditions, certain broadcast stations are eligible for mandatory carriage .
-
Under certain conditions, the cable operator must obtain the permission of the licensee of the broadcast station. This term includes satellite-delivered broadcast "superstations" such as WGN-TV and WWOR, but it does not include:
-
Satellite-delivered non-broadcast programming services (HBO, ESPN, C-SPAN, QVC, etc.).
-
Video services delivered by terrestrial microwave systems such as MDS, MMDS, or ITFS, unless the actual signal being delivered was originally picked up from a broadcast station.
-
Cablecasting programming originated by the cable operator or an access organization.
Broadcast Storm
A pathological condition that may occur in a TCP/IP network that can cause a large number of broadcast packets to be propagated unnecessarily across an enterprise-wide network, thereby causing network overload. Broadcast storms happen when users mix old TCP/IP routers with routers supporting the new releases of TCP/IP protocol. Routers use broadcast packets to resolve IP addressing requests from stations on LANs. If a station running an old version of TCP/IP sends such a request, TCP/IP routers in an enterprise-wide network misunderstand it and send multiple broadcasts to their brother and sister routers. In turn , these broadcasts cause each router to send more broadcasts, and so on. This chain reaction can produce so many broadcast messages that the network can shut down. It should be noted that this is extremely rare and it happens only in TCP/IP networks that use two specific TCP/IP protocol releases.
Broadcast Transmission
A fax machine feature that allows automatic transmission of a document to several locations.
Broadwing
The name for the merged company comprising the old Cincinnati Bell Inc., a LEC (Local Exchange Carrier), and IXC Communications, an IXC (Interexchange Carrier) which acquired Cincinnati Bell. The merged company changed its name to Broadwing Inc. in 2000. Cincinnati Bell continues to operate as a LEC division of Broadwing. www.broadwinginc.com.
Brochureware
A pejorative term for what companies can pull off with a clever copy writer, some nice graphics, and a bit of an advertising budget. Ever read a brochure and compared it to the product? You get the idea. See Webware.
Broken arrow
An error code displayed on certain computer terminals for various kinds of protocol violations and unexpected error conditions, including connection to a down computer. In the military, it is jargon for a nuclear accident .
Broken Link
A link to a file that does not exist or is not at the location indicated by the URL. In short, you click on a hyperlink on a Web page you're viewing, but nothing happens or you get an error message. Bingo, broken link. You've been sent somewhere that doesn't exist. This is neither exciting, nor good programming.
Broken Pipe
This term is usually seen in an error message by browser programs to let the user know that the stream of information which was downloading at the time has been forcibly cut. This can occur for many reasons, most commonly because you are on a very crowded network or your access provider is experiencing heavy traffic.
Broken Record
In the 1960s, 1970s and 1980s there was an expression that you sound "like a broken record." This meant that you were repeating yourself. The expression came from the fact that when a needle got stuck in the groove of a vinyl record, the sound simply repeated itself. Then came the compact disc and the needle never got stuck in the groove since there was no needle. As a result, college kids today have idea what the expression "broken record" means, since most have never owned nor seen a record player.
Broker
A company (or person) that acts as an agent, or intermediary, in contractual relationships between a buyer and a seller. A broker takes neither ownership nor physical possession of the thing being bought and sold. Equipment brokers, for example, buy and sell equipment without taking ownership, sometimes without testing or refurbishing the equipment, and often without even seeing it. The broker finds a seller and a buyer, and has the equipment shipped directly from one to the other, relying on the seller's representation of its condition. Equipment brokers have been around since about 1968, when it became legal in the US for you to own your own equipment. Actually, they have been buying and selling gear between telephone companies for many years . See also Junk Dealer and Secondary Equipment.
Bandwidth brokers are a more recent phenomenon , having been born out of the Telecom Act of 1996, which opened the local exchange to competition and spurred the growth of competitive carriers in both the voice and data and the local and long-haul markets. Bandwidth brokers put themselves in the middle of a bandwidth transaction between buyer and seller. Both buyer and seller may be carriers, or the buyer may be an end user organization and the seller a carrier ” either way, the arrangement works the same way. Most brokers act like a commodities exchange, never taking title to the capacity, and often using a Website to post example asking prices for certain levels of bandwidth (e.g., T-1 or T-3, OC-3 or OC-24) between specific points of termination (e.g., New York City and Los Angeles) for various contract terms (e.g., 6, 12, or 24 months). If you're interested, you make an offer, and the broker works with you and the seller to put a deal together. An SLA (Service Level Agreement) may be part of the negotiated terms. You may not even know the name of the seller until after the contract is signed, if ever. Some owners of telco hotels also serve as bandwidth brokers. In addition to renting space to both incumbent and competitive carriers, they serve as bandwidth brokers, and even take responsibility for establishing the physical connection between the parties. They may even go so far as to monitor the performance of the seller's network over time, providing reports to both parties on a regular basis. In addition to acting as a broker for leased lines, some also broker frame relay, VPN (Virtual Private Network), and Internet access services. See also SLA, Carrier Hotel, Telecom Act of 1996, and VPN.
Bronze
Alloy of copper and tin, widely used and known since ancient times. Copper content in bronze varies between 89% and 96%.
Brouter
Concatenation of "bridge" and "router." Used to refer to devices which perform both bridging and routing functions. In local area networking, a brouter is a device that combines the dynamic routing capability of an internetwork router with the ability of a bridge to connect dissimilar local area networks (LANs). It has the ability to route one or more protocols, such as TCP/IP and XNS, and bridge all other traffic.
Brown and Sharpe Wire Gauge
An older name for American Wire Gauge, the U.S. standard measuring gauge for non-ferrous conductors (i.e., non-iron and non- steel ), AWG covers copper, aluminum, and other conductors. Gauge is a measure of the diameter of the conductor. See AWG for a full explanation.
Brown Down
In the context of DSL, a situation that occurs when a CO (or local exchange) cannot handle all of the calls attempted and even disrupts calls in progress. Also called a "brown down".
Brownfield
The opposite of greenfield. Brownfield is the sum of all legacy material (equipment, architectures, procedures, etc.) in any given network project. Greenfield refers to the material being developed anew. See Greenfield and Legacy.
Brownout
-
When you lose all your electricity, it's called a blackout . When your voltage drops more than 10% below what it's meant to be, it's a brownout. If a brownout lasts less than about a second, it is called a SAG. Brownouts are sometimes caused by overloaded circuits and are sometimes caused intentionally by the AC utility company in order to reduce the power drawn by users during peak demand periods (like during hot summers when everyone is using their air conditioners). Studies have shown that brownouts of all durations make up the vast majority of power problems that affect telephone systems and computers.
-
In Internet terms, when a system is so overloaded by requests that it slows down to the point of near unusability, it is suffering a "brownout."
Browser
-
Also called a Web Browser. A browser is software that translates digital bits into pictures and text so you can look at them. A browser displays documents on the Internet and the World Wide Web to your computer. A Web Browser is software which allows a computer user (like you and me) to "surf" the Internet. It lets us move easily from one World Wide Web site to another. Every time we alight on a Web Page, our Web Browser moves a copy of documents on the Web to your computer. A Web Browser uses HTTP ” the HyperText Transfer Protocol. Invisible to the user of a Web Browser, HTTP is the actual protocol used by the Web Server and the Client Browser to communicate over the Internet. The most famous Web Browsers are Netscape and Microsoft's Internet Explorer. But there are others, like Opera. See Browser Sniffing, Browsing, Internet and Surf. www.netscape.com and www.microsoft.com.
-
A developed tool used to inspect a class hierarchy in an object-oriented software system.
Browser Compatibility
A term that compares the way a Web page looks on one WWW browser as opposed to another. Usually this is done with Microsoft Internet Explorer (MIE) and Netscape Navigator, but can also refer to cross-platform compatibility. (For example, the way a page renders or displays on a Windows system as opposed to a Mac.) The reason these incompatibilities exist is due to the way a browser interprets the Web page's code (HTML). The differences are usually very slight , but they're enough to annoy some Web designers and sometimes even their clients to the point in which great time and energy is spent in making a Web site compatible with any browser on any type of system. Browser compatibility is also used in conjunction with (and should not be confused with) the term browser support.
Browser Plug-in
A Plug-in is a small program that you download and install to add a specific feature to your Web browser. These features can include additional multimedia such as video and sound.
Browse List
A list of computers and services available on a network.
Browser Sniffing
The term "browser sniffing" refers to figuring a website visitor's browser and version number, and possibly any installed plug-ins. Typically, this is done in order to grant or deny access to certain features of that site that will work only on specific versions of specific browsers (there being few standards in this business). Usually accomplished with JavaScript, there are two common methods that a website can use to figure browser information. You can evaluate the User Agent (UA) string revealed in the navigator object properties or you can test for the existence of other specific objects. Using this information, you can make decisions as to what content / information your web site should serve up to specific visiting users. See Browser.
Browser Support
This refers to the ability of a particular browser to even recognize and interpret certain HTML or other Web page codes. For example, Netscape Navigator 1.0 did not have the ability to render a page layout in frames. This feature did not come along until version 2.0, therefore it can be said that Navigator 1.0 did not "support" frames.
Browsing
The act of searching through automated information system storage to locate or acquire information without necessarily knowing of the existence or the format of the information being sought.
Brush
A computer imaging term. A paint package's most basic image-creation tool. Most packages let you select a variety of sizes and shapes. Many let you customize shapes .
Brute Force Attack
A cracker term. Brute force attack means hurling passwords at a system until it cracks.
BSA
See both Basic Switching Arrangement and Open Network Architecture.
BSAC
BSAC stands for bit sliced arithmetic coding that provides one of the forms of scalability in MPEG-4 audio. See MP-4.
BSAFE
BSAFE is a cryptography engine and suite of RSA security components . BSAFE's low-level, general-purpose core crypto engine provides cryptographic base components (primitives) for securing applications or services. BSAFE uses crypto algorithms such as RSA Diffie-Hellman, DES, Triple DES, RC2, RC4, RC5 and SHA-1.
BSC
-
Binary Synchronous Communications. A set of IBM operating procedures for synchronous transmission used in teleprocessing networks, BSC has become a de facto standard protocol. BSC is a character-oriented protocol which involves the communication of data in blocks of up to 512 characters. Each block of TeXT (TXT) data is preceded by a header which includes SYNchronizing bits (SYN) in order that the receiving device might synchronize on the rate of transmission, a Start Of Header (SOH), a HeaDeR (HDR) containing application address information, and a Start of Text (STX). Each block is succeeded by a trailer which includes End Of Text (EOT), Block Checking Characters (BCC) for error detection and correction, and End Of Transmission (EOT). BSC is a polling protocol which operates in a half duplex (HDX) mode, generally over the analog PSTN (Public Switched Telecommunications Network). As each block of data is transmitted from the polled device, the receiving computer system responds with either an ACKnowledgement (ACK) indicating successful and error-free receipt of the subject data, or a Negative AcKnowledgement (NAK) indicating detection of an error created in transmission. An ACK prompts the polled device to transmit the next block of data. A NAK prompts the device to retransmit the subject block. The process continues, block-by-block, until such time as all data have been transmitted and received. By way of example, BSC is commonly used in a Call Accounting application to transfer Call Detail Recording (CDR) information to a centralized processor from a pollable buffer attached to a PBX system.
-
Base Station Controller. A wireless telecommunications term. The BSC is a device that manages radio resources in GSM (Global System for Mobile Communications), including the BTS (Base Transceiver Station), for specified cells within the PLMN (Public Land Mobile Network).
BSD
Berkeley Software Distribution. Term used when describing different versions of the Berkeley UNIX software, as in "4.3BSD UNIX".
BSE
-
Basic Switching Element. See Open Network Architecture.
-
Basic Service Elements. A term used in voice processing to describe technical telephone system features such as ANI, DID trunks, call forwarding, stutter dial tone, suppressed ringing, and directory database access.
BSGL
Branch Systems General Licence. A British term. A licence that must be obtained by any organization seeking to link a private network to the British PSTN (Public Switched Telephone Network). A separate licence must be held on each site.
BSI
British Standards Institution. The body responsible for development of UK standards across a wide range, including telecommunications. BSI also is responsible for input to European standards bodies like CEN and CENELEC, as well as international standards bodies such as the ISO and the ITU-T. BSI claims to be the oldest of the over 100 national standards bodies in the world. www.bsi.org.uk. For the U.S. counterpart see also ANSI.
BSIC
Base Station Identity Code. An attribute of a GSM (Global System for Mobile Communications) cell which is a code allowing a distinction between local cells having the same radio frequency.
BSIS
Branch Sales Information System.
BSOD
Blue Screen of Death. See Blue Screen of Death.
BSP
-
Bell System Practice. A very defined way of writing and presenting instruction and installation manuals. BSPs also establish standards for splicing cable, for installing phones, answering phones, collecting debts , finding phone taps, climbing poles. They are (or once were) the instruction manuals that dictated how to do everything. Divestiture has changed the rules. BSPs are not as important as they were when AT&T handed down all the BSPs.
-
Butt Sweat Protector. David Bomelyn, an engineer who works for a cellular phone out west, claims that "a BSP is the plastic or hard covering of a book or some technical manual that the phone tech keeps in his or her back pocket or by himself at all time. In most cases when this book is pulled out, the tech is in a real jam and his or her butt is most likely is puckered and is sweating and we don't want the pages in this book to get wet." David claims the definition was originally published in the Motorola Dictionary book. Apparently, "The big wigs at Motorola didn't know it was in their dictionary. Some one had slipped it in. When the powers to be found out, they chopped it out of the dictionary, never to been seen again. So maybe you do the world a favor and bring this back to life and give all of us fone techs a good laugh ."
BSRF
Bell System Reference Frequency. See Timing.
BSS
-
Base Station System. A wireless telecommunications term. A GSM (Global System for Mobile Communications) device charged with managing radio frequency resources and radio frequency transmission for a group of BTSs. See also GSM.
-
Business Support System. The system used by network operators to manage business operations such as billing, sales management, customer-service management and customer databases. A type of Operations Support System (OSS).
-
Broadband Switching System. A carrier (e.g., LEC or IXC) switch for broadband communications. Such switches are capable of switching frames (Frame Relay) or cells (SMDS and ATM) at a very high rate of speed. They contain multi-Gigabit busses which may be stacked or chained. For example, an "edge" switch, which is located at the edge of the network much as is a Class 5 Central Office in the voice world, may involve a 20 Gbps bus. "Core" switches, which are located in the core of the network and which are the equivalent of a tandem switch in the voice world, may involve eight busses of 20 Gbps each for a total capacity of 160 Gbps.
BT
-
British Telecom. See 1981.
-
Burst Tolerance: BT applies to ATM connections supporting VBR services and is the limit parameter of the GCRA.
-
Bit Time. See Bit Time.
BTA
-
Basic Trading Area. A wireless telecommunications term. The United States is broken down into 493 major trading areas for economic purposes. These boundaries were used for licensing PCS wireless phone systems. Several BTAs make up Metropolitan Trading Area, an area defined by the FCC for the purpose of issuing licenses for PCS. Thus, each MTA consists of several Basic Trading Areas (BTAs).
-
Broadband Telecommunications Architecture, an architecture introduced by General Instrument's Broadband Communications Division at the Western Cable Television Show on December 1, 1993. General Instrument said the plant is built to 750 MHz and can support reduced node size and add services such as video-on-demand, telephony, interactivity, data services, etc.
-
Business Technology Association. Previously NOMDA/LANDA, BTA was formed by the merger of the National Office Machine Dealers Association and the Local Area Network Dealers Association. BTA holds several conferences a year. Members include manufacturers, distributors , retailers and consultants . www.btanet.org.
BTAM
Basic Telecommunications Access Method. One of IBM's early host-based software programs for controlling remote data communications interface to host applications, supporting pre-SNA protocols. See IBM.
BTag
An ATM term. Beginning Tag: A one octet field of the CPCS_PDU used in conjunction with the Etag octet to form an association between the beginning of message and end of message. See ATM.
BTB Ratio
See Book-To-Bill Ratio.
BTI
British Telecom International.
BTL
Bell Telephone Laboratories.
BTN
Billed Telephone Number. The primary telephone number used for billing, regardless of the number of phone lines associated with that number. According to Bellcore, BTN is sometimes known as a screening telephone number. The BTN is a telephone number used by the AMA process as the calling-party number for recording purposes. See Billing Telephone Number.
BTO
-
Built To Order. PC makers like Toshiba and Dell are delivering PCs and notebooks that contain the hardware specifications that you particularly want ” RAM, size of hard disk, etc.
-
Bandwidth Trading Organization. See Bandwidth Broker.
BTOS
A UNIX program which translates binary files into ASCII.
BTRL
British Telecom Research Laboratories.
Btrieve
Btrieve is a key-indexed database record management system. You can retrieve, insert, update, or delete records by key value, using sequential or random access methods. First introduced in 1983, Btrieve was one of the first databases designed for LANs. Novell bought the company in the late 1980s and then later sold it. It's now called Pervasive Software.
BTS
Base Transceiver Station. A wireless telecommunications term. A GSM (Global System for Mobile Communications) device used to transmit radio frequencies over the air interface.
BTSM
BTS (Base Transceiver Station) Management. A wireless telecommunications term. Devices configured to manage BTS functions and equipment.
BTSOOM
Beats The S*** Out Of Me. Acronym used in e-mail, during online chat sessions, and in newsgroup postings.
BTU
-
Basic Transmission Unit.
-
British Thermal Unit. A measure of thermal energy often used in designing building heating and cooling systems. The heat output of computer equipment is often specified and must be taken into account when sizing building climate control systems. Computer equipment heat output is expressed in BTU per hour. 3.7 BTU per hour is equivalent to 1 Watt of dissipation.
BTV
See Business Television.
BTW
By The Way. An acronym used in electronic mail on the Internet to save words or to be hip, or whatever.
BTx
BTx means Base Transmit. It is the frequency on which a base station transmits and a user station receives.
Bubble Up
A new relatively vague Microsoft term that describes how information is produced in response to an inquiry in a database. Ask the database for how much my portfolio is worth and the program goes out and does some calculations which are transparent to me before it " bubbles up" (i.e. produces) the information. I first heard the term from Microsoft when they referred to their new improved www.moneycentral.com. It's neat word.
BubbleVision
An affectionate name for CNBC, CNNfn, Bloomberg TV and other 24/7 cable / satellite channels that concentrate on financial news and "interpretation."
Buck
See Passing The Buck.
Bucket
RMON terminology for a discrete sample of data. The RMON History group specifically uses buckets in its sampling functions of the different data sources. See Buckets.
Bucket o' Dial Tone
Once upon a time, every new central office technician was sent to another central office for a "bucket o' dial tone," when the CO was overloaded. There is no such thing, of course, but the old hands had a big laugh over it. It was sort of a "right of passage." It worked only once. See also Fiber Exhaust and Frequency Grease.
Bucket Shop
Brokerage firms with dubious reputations. Many of these are fly-by- night operations, consisting of many brokers making cold phone calls to little old ladies. These shops specialize in low priced "penny stocks," which they sell to one fool and then to a greater fool. The brokers tend to hop from shop to shop, just ahead of federal regulators.
Buckets
When competition in cell phones heated up in North America in the mid- 1990s, some of the newer competitors pushed increased coverage patterns, small phones, and huge packages of monthly minutes so large that their salespeople started calling the deals "buckets."
Buffer
-
In data transmission, a buffer is a temporary storage location for information being sent or received, and serves the purpose of flow control. Usually located between two different devices that have different abilities or speeds for handling the data. The buffer acts like a dam, capturing the data and then trickling it out at speeds the lower river can handle without, hopefully, flooding or overflowing the banks. Buffers can be located at the incoming ports of a switch or router, at the outgoing ports, or even internal to the switching matrix.
-
A coating material used to cover and protect the fiber. The buffer can be constructed using either a tight jacket or loose tube technique. Tight buffering is extruded directly on the fiber coating. Loose tube buffering is an extruded tube around the coated fiber to isolate the fiber from stresses in the cable system.
-
A circuit or component which isolates one electrical circuit from another.
Buffer Amplifier
An amplifier, usually in a gain of 1 or 2, used to drive a heavy capacitive or resistive load.
Buffer Box
A collection device connected to a host phone system (PBX) that collects, stores and reports data from the host phone system. Such a box could be used to collect information on phone calls and have that information downloaded once a month by a remote call accounting service and then assembled into reports, showing who made the most calls, the most expensive calls, etc. A buffer box would typically be attached to a PBX by a serial cable. A buffer box would have some of the ingredients of a PC ” a microprocessor and a storage device (e.g. hard disk).
Buffer Coating
Protective material applied to fibers. Increases apparent fiber size. May be more than one layer. Stated in microns. Usually thicker or multi-coated on tight- buffer cables.
Buffer Memory
Electronic circuitry where data is kept during buffering. See Buffer.
Buffer Overflows
Buffer overflows are sometimes called stack smashing. They are the most common form of security vulnerability in the past decade . They are also the easiest to exploit. More attacks are the result of buffer overflows than any other problem. Computers store everything -- programs, data, photographs -- in memory. If the computer asks a user for an 8-character password and receives a 200-character password, these extra characters may overwrite some other area in memory. They're not supposed to. That's the bug. If it is just the right area of memory, we overwrite it with the just the right characters, we can change a "deny connection" instruction to an "allow access" command or even get our own code executed. The Morris worm is probably the most famous overflow-bug exploit. It exploited a buffer overflow in the UNIX fingerd program. It's supposed to be a benign program, returning the identity of a user to whomever asks. This program accepted as input a variable that is supposed to contain the identity of the user. Unfortunately, the fingerd program never limited the size of the input and Morris wrote specific large input that allowed his rogue program to (install and run) itself. . . . Over 6,000 servers crashed as a result; at that time (in 1988) that was about 10 percent of the Internet. -- This explanation is from Bruce Schneier, "Secrets and Lies: Digital Security in a Networked World (2000)."
Buffer Overrun
A network security term. An attack in which a malicious user exploits an unchecked buffer in a program and overwrites the program code with their own data. If the program code is overwritten with new executable code, the effect is to change the program's operation as dictated by the attacker. If overwritten with other data, the likely effect is to cause the program to crash.
Buffer Storage
Electronic circuitry where data is kept during buffering. See Buffer.
Buffered Repeater
A device that amplifies and regenerates signals so they can travel farther along a local area cable. This type of repeater also controls the flow of messages to prevent collisions.
Bug
-
A concealed microphone or listening device or other audio surveillance device.
-
To install the means for audio surveillance.
-
A semiautomatic telegraph key.
-
A problem in software or hardware. The original computer bug, a moth, is enshrined at the Washington Navy Yard. It was the cause of a hardware failure in an early computer in 1945. The story goes like this: a team of top Navy scientists was developing one of the world's first electronic computers. Suddenly, in the middle of a calculation, the computer ground to a halt, dead. Engineers poured over every wire and every inch of the massive machine. Finally, one of the technicians discovered the cause of the problem. Buried deep inside its electronic innards, crushed between two electric relays, lay the body of a moth. These days, "bugs" in telecom or computer systems are not insects . They're indescribable glitches that adversely affect smooth operations. Bugs usually originate in software. Some programmers call bugs "undocumented features." And they are, indeed. All the above is the story the navy likes to put out. In fact, the word "bug" for problem in design has been around for eons. It's mentioned in a 1910 book called, "Edison, His Life and Inventions" by Frank Lewis Dyer. The book talks about Edison harassing his employees to "get all the bugs out."
Bug Mix
A silly term for the precise collection of bugs in a particular piece of software.
Bug Rate
The frequency with which new bugs are found during the testing cycle is referred to as the bug rate. As these bugs are fixed, and as time passes , bugs will become more and more difficult to find, and new bugs will be found less frequently, i.e., the bug rate decreases. Usually, when the bug rate drops to zero and all major bugs (and most of the minor bugs) have been fixed, a product is ready for the next stage in its lifecycle.
Bugbashing
Bugbashing is Microsoft-speak for fixing a bug in software.
Build to suit
A system made to a customer's specific specifications.
Building Core
A three-dimensional space permeating one or more floors of the building and used for the extension and distribution of utility services (e.g., elevators, washrooms, stairwells, mechanical and electrical systems, and telecommunications) throughout the building.
Building Distributor
BD. The international term for intermediate cross-connect. A distributor in which the building backbone cable(s) terminates and at which connections to the campus backbone cable(s) may be made.
Building Distribution Frame
Somewhere in the building where all telephony wiring for the building is. All the cables from the outside the building would first come here and be punched down on the building distribution frame. Additional cables would take the telephone circuits upstairs.
Building Entrance Agreement
A piece of paper that lets phone companies and utilities enter a building, gives them permission to build facilities and store equipment and lets them access their equipment. In great demand by Competitive Local Exchange Carriers (CLECS) who give residents a choice of providers and often force existing carriers to improve services or reduce rates. Often the CLECS are charged fees, which they agree to, to avoid paying the RBOCs' access charges.
Building Entrance Area
The area inside a building where cables enter the building and are connected to riser cables within the building and where electrical protection is provided. The network interface as well as the protectors and other distribution components for the campus subsystem may be located here. Typically this area is the end of the local telephone company's responsibility. From here on it's your responsibility. You should protect your equipment inside the building from spikes and surges and other electrical nonsenses which the phone company's cables might bring in. For the best disaster protection, it's wise to have two building entrances by which your telecommunications cables can enter. And they should enter from separate telephone central offices. Some telephone companies, e.g. New York Telephone, are now tariffing such services. See Building Entrance Agreement.
Building Footing
The concrete base under the foundation of a building in which copper wire may be laid to form an electrical ground.
Building Integrated Timing Supply
BITS. A clock, or a clock with an adjunct, in a building that supplies DS1 and/or composite clock timing reference to all other clocks in that building. See BITS.
Building Module
The standard selected as the dimensional coordination for the design of the building, e.g., a multiple of 100 mm (4 in), since the international standards have established a 100 mm (4 in) basic module.
Building Out
The process of adding a combination of inductance, capacitance ,and resistance to a cable pair so that its electrical length may be increased by a desired amount to control impedance characteristics.
Building Steel
The structural steel beams that make up the frame of a building. If the steel frame is buried deep in the earth, it can be used as an electrical ground. But you'd better be careful: Unbalanced three-phase power is also probably using the frame as a ground, and you may pick up huge quantities of 60 hz hum.
Bulk Billing
A method of billing for long distance telephone services where no detail of calls made is provided. WATS is a bulk billed service. Therein lies the problem for the cost conscious user. There's no verification of calls made. See Call Detail Recording.
Bulk Encryption
Simultaneous encryption of all channels of a multichannel telecommunications trunk.
Bulk Storage
Lots of storage. Usually reels of magnetic tape or hard disks.
Bullet Amplifier
A Satellite Term. Small device used to increase signal power and offset signal loss caused by coaxial cable and splitting devices.
Bulletin Board System
A fancy name for an electronic message system running on a microcomputer. Call up, leave messages, read messages. The system is like a physical bulletin board. That's where the name comes from. Some people call bulletin board systems electronic mail systems. See also BBS.
Bulletproof
Used to describe an algorithm or implementation that's thought to be capable of recovering from any imaginable exception or condition ” a rare and valued quality. It implies that the programmer has covered all bases.
Bumper Beeper
Radio beacon transmitter, hidden in or on a vehicle for use with radio tailing equipment.
Bunched Frame-Alignment Signal
A frame-alignment signal in which the signal elements occupy consecutive digit positions .
Bundle
-
A group of fibers or wires within a cable sharing a common color -code.
-
In T-1, specifically M44 Multiplexing, a bundle consists of 12 nibbles (4 bits) and may represent 11 channels of 32 Kbps compressed information plus a delta channel. A bundle is typically a subset of a DSI and treated as an entity with its own signaling delta channel.
-
Some telecommunications carriers have tried to entice buyers to buy more than one service, i.e. long distance, local service, call forwarding, call waiting, Internet access, etc. It's gotten harder to sell a bundle of services as telecommunications has become more competitive in recent years and large telecom carriers have lacked marketing skills, preferring to sell on cheaper price, which is easier. the better carriers sell bundles.
Bundle Fodder
Junk software included on CD-ROMs or packaged with peripherals such as modems and designed to bulk up the presumed value of the total package to entice an unsuspecting consumer to buy. See Shovelware.
Bundled
Combining several services under one telephone tariff item at a single charge. See Bundled Services.
Bundled Cable
An assembly of two or more cables continuously bound together to form a single unit prior to installation (sometimes referred to as loomed, speed-wrap or whip cable constructions).
Bundled Rates
See Bundled Services.
Bundled Services
Combining several services under one telephone tariff item at a single charge. Bundled services sound like a good idea, especially since you tend to think that you're getting some sort of discount for a suite of services. Oftentimes, that's just not true. Rather, bundling is a way of getting you to subscribe to a bundle of services, some of which you may not even need and will never use, at a potentially inflated price. In a bundle of services, you never quite know the price of a given component of the bundle, so you really can't objectively compare different companies' offerings. Of course, that's part of the reason for the bundling.
Bundling
A marketing term used by local, long-distance, and cable companies whereby several services are combined into one package. The idea is to derive economies of scale. Bundling allows companies to exploit existing brand value. It may allow for cross- subsidization (when allowed by the regulator ) or package discounts and the ability to channel a new product into an existing stream of demand for another product. In some cases, bundling allows a company to leverage an existing channel or network to distribute additional product. Examples of bundling are rife within telecom. Cable companies, for example, have bundled cable TV and telephony together. Some users believe they get two "bar- gains" ” cheaper service and easier service calls (only one carrier to deal with ” no fingers to point). Sometimes they're right. Usually they're not. See Bundled Services.
Bunny Suit
A layered, hooded outfit that covers every part of your body, except your eyes. Bunny suits are worn by people who work in places where cleanliness is absolute. The human skin sheds about 30,000 particles of skin a second. If one of these particles made it into a semiconductor or a piece of optical fiber it could seriously impair the usability of the device.
Burbling
What my wife, Susan, calls my endless lectures about telecommunications and other subjects of great fascination to me, but not, sadly, to her.
Burden Test
A semi- legitimate test used in regulation to determine if the offering of a new or continued service will cause consumers of other services to pay prices no higher than if the service were not offered . In other words, the question is "Who carries the Burden?" It's sometimes called the "avoidable cost test."
Buried Cable
A cable installed under the surface of the ground in such a manner that it cannot be removed without disturbing the soil.
Buried Service Wire Splice
A watertight splice filled with an encapsulant.
Burn In
To run new devices and printed circuits cards, often at high temperatures , in order to pinpoint early failures. The theory is all semiconductor devices show their defects ” if any ” in the first few weeks of operation. If they pass this "burn-in" period, they will work for a long time, so the theory goes. "Burn-in" should probably be 30-days under full power and working load. Burn-in should also take place in a room with lots of heat and at least 50% humidity, since this will simulate the poorly-ventilated places most people install telephone systems.
Burn Out
A condition, where stress causes agents to be apathetic and lethargic, caused by intensity of calling, lack of variety and poor working conditions. It is particularly associated with outbound cold calling and inbound complaint handling, both of which are stressful for agents if not carefully managed.
Burn Rate
Cash divided by operating expenses plus non cash charges (depreciation and amortization) in the most recent quarter. This is a measure of how long a company can survive before it runs out of cash. In short, burn rate is the speed at which a new company uses up its cash en route to developing a product before it turns cash positive.
Burned-in Address
The hardware address on a network interface card (NIC). This address is assigned by the manufacturer of the interface card, which ensures that every card has a unique address.
Burning A Pole
Slang expression to describe when an installer accidentally slides down a telephone pole. This usually happens on an old pole full of gaff holes when his gaff breaks out of the pole. Burning a pole results in painful chemical burns because the installer usually winds up with a chest and legs full of splinters coated with creosote, a coal tar distillate used to preserve the wooden pole. Installers are taught to "kick out," rather than hug the pole and suffer burns.
Burrus Diode
A surface-emitting LED with a hole etched to accommodate a light-collecting fiber. Named after its inventor , Charles Burrus.
Burst
-
In data communication, a sequence of signals, noise, or interface counted as a unit in accordance with some specific criterion or measure.
-
To separate continuous-form or multipart paper into discrete sheets.
-
A small reference packet of the subcarrier sine wave, typically 8 or 9 cycles, which is sent on every line of video. Since the carrier is suppressed, this phase and frequency reference is required for synchronous demodulation of the color information in the receiver.
Burst Isochronous
Isochronous burst transmission. See Isochronous.
Burst Mode
A way of doing data transmission in which a continuous block of data is transferred between main memory and an input/output device without interruption until the transfer has been completed.
Burst Switching
In a packet-switched network, a switching capability in which each network switch extracts routing instructions from an incoming packet header to establish and maintain the appropriate switch connection for the duration of the packet, following which the connection is automatically released. In concept, burst switching is similar to connectionless mode transmission, but it differs from the latter in that burst switching implies an intent to establish the switch connection in near real time so that only minimum buffering is required at the node switch.
Burst Traffic
Burst traffic is many phone calls (usually incoming telephone calls) that simultaneously arrive at a computer telephony system. Burst traffic tests are usually performed as part of a systems load and stress testing. Burst traffic tests are particularly important for computer telephony systems as usually they must perform a lot of processing to set up to handle a call. The arrival of many calls simultaneously, such as in response to a television sales offer (or when Oprah asks you to call 1-800-xxxxxxx to vote on whether OJ is guilty or innocent), can place significant strain on a computer telephony system.
Burst Transmission
-
A method of transmission that combines a very high data signaling rate with very short transmission times.
-
A method of operating a data network by interrupting, at intervals, the data being transmitted. The method enables communication between data terminal equipment and a data network operating at dissimilar data signaling rates.
Bursty
Refers to data transmitted in short, uneven spurts. Or, discontinuous signals occurring at random intervals.
Bursty Information
Information that flows in short bursts with relatively long silent intervals between. LAN traffic is characterized as "bursty" in nature, as devices tend to transmit substantial amounts of data at irregular intervals.
Bursty Seconds
Bursty seconds is a measure of the amount of time spent at maximum data transfer rate.
Bursty Traffic
Communications traffic characterized by short periods of high intensity separated by fairly long intervals of little or no utilization. Data traffic and certain kinds of video traffic are inherently bursty.
Bus
-
An electrical connection which allows two or more wires or lines to be connected together. Typically, all circuit cards receive the same information that is put on the bus. Only the card the information is "addressed" to will use that data. This is convenient so that a circuit card may be plugged in " anywhere on the Bus." There are two common buses inside a PC ” the older ISA bus, capable of only five megabytes per second and the newer PCI bus, capable of transmitting up to 132 megabytes per second. All computers and most telephone systems use buses of some type. Computer buses are typically open. Telephone system buses are typically closed. See also Backplane and Bus Network.
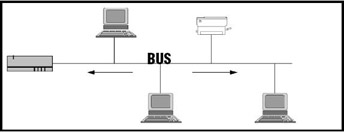
-
BUS (Broadcast and Unknown Server). An ATM term. More specifically, a LAN Emulation (LANE) term. This server handles data sent by a LAN Emulation Client (LEC) to the broadcast MAC address ('FFFFFFFFFFFF'), all multicast traffic, and initial unicast frames. The BUS works in conjunction with a LES (LAN Emulation Server), which automatically registers and resolves differences between LAN MAC addresses and ATM addresses. This is accomplished by labeling each device transmission with both addresses. See also ATM and LANE.
Bus Card
An expansion board that plugs into the computer's expansion bus. See also PCMCIA.
Bus Enumerator
A Windows 95 term. A new type of driver required for each specific bus type, responsible for building ("enumerating") the hardware tree on a Plug and Play system.
Bus Extender
A device that extends the physical distance of a bus and increases the number of expansion slots.
Bus Hog
A device connected to a transmission bus which, after gaining access to the transmission medium, transmits a large number of messages regardless of whether other devices are waiting.
Bus Interface Unit
BIU. In LANs, the device furnishing direct connection of a DTE to the LAN bus.
Bus Master
A VME board (usually a CPU) that can contend for, seize and control the VME bus for the purpose of accessing bus resources such as voice boards or even other CPUs. See VME.
Bus Mastering
A bus design that enables add-in boards to process independently of the CPU and access the computer's memory and peripherals on their own. Bus mastering is a way of transferring data through a bus in which the device takes over the bus and directly controls the transfer of data to the computer's memory. Bus mastering is a method of Direct Memory Access (DMA) transfer.
Bus Mouse
A mouse that is attached to your computer's not via a serial port or a USB port but through a special card attached to the motherboard. Note that such a mouse takes up an expansion slot in a PC. Bus mice are increasingly rare.
Bus Network
All communications devices share a common path . Typically in a bus network, a "conversation" from each device is sampled quickly and interleaved using time division multiplexing. Bus networks are very high-speed ” millions of bits per second ” forms of transmission and switching. They often form the major switching and transmission backbone of a modern PBX. The printed circuit cards which connect to each trunk and each line are plugged into the PBX's high-speed "backbone" ” i.e. the bus network. Similarly, Broadband Switching Systems (BSSs) make use of internal buses, which run at Gbps rates.
In the LAN world, bus networks include Ethernet, which is by far the most common LAN standard. The Ethernet bus specification provides for a common electrical highway which can be shared by as many as 1,024 attached devices per physical Ethernet or Ethernet segment. The Ethernet bus runs at 10 Mbps, although throughput is typically much less. See also BUS.
Bus Slave
A VME board (usually a subsystem or I/O board) which can only respond to VME bus accesses mapped to its address. Slaves can usually interrupt the VME bus on one of 7 levels. See VME.
Bus Speed
-
The speed at which the computer's CPU (central processing unit) communicates with other elements of the computer. For example, the speed at which data moves between the CPU and its various bus-attached devices, such as video controller, disk controllers, voice cards, etc. In defining bus speed, Walt Mossberg of the Wall Street Journal wrote: A "bus" is a techie term for a pathway through which bits of data travel among various components inside a PC. In recent years, computer makers have been increasing the "bus" speeds, to keep up with advances in the speeds of processors. Though these high speeds sound enticing, they have little relevance to an average computer user. As with memory speeds, faster bus speeds won't make Web surfing or word processing discernibly faster. Again, the publicizing of bus speeds is mainly a marketing trick to get unfamiliar consumers to pay more." See AGP, AT BUS and PCI.
-
The speed at which the internal bus operates in a network switch. For example, an ATM Broadband switch may provide multiple, redundant buses, each of which might operate at 20 Gbps, yielding a total rate of 160 Gbps for an 8-bus switch.
-
The speed at which a network bus operates. For instance, an Ethernet bus provides a raw transmission rate of 10 Mbps, although the rate of data throughput typically is much less.
Bus Topology
A network topology in which nodes are connected to a single cable with terminators at each end. One form of Ethernet LANs used bus topology, joining the various PCs along one piece of coaxial cable.
Business Analytics Software
Software that helps businesses understand what makes their customers happy and how to keep them that way so companies can improve retention and increase sales. Business analytic applications extract the events and attributes locked away in the text fields of transactional software systems, integrating them with structured and numeric data for automated analysis. The software has several aims: customer retention, new idea testing, loyalty measuring, product and price testing, brand assessment and web analytics. According to one brochure I read on this area, "Analysis of behavior can tell a company that support call volume, customer attrition or sales dropout rates are on the rise, but only analysis of communications can explain why customers are calling, why they're dropping out of the sales pipeline, and why they're closing existing accounts."
Business and Residential Custom Services
BRCS. Also known as Custom Calling Features (CCF) including call waiting, call forwarding, 3-way calling, etc., available through the central office without requiring the subscriber to use special equipment.
Business Audio
At one stage business audio was thought to involve voice annotating spreadsheets. Now it means making phone calls through and by your PC.
Business Card
The electronic date equivalent to a printed business card. This electronic version of the business card is treated like a file and can be exchanged between Bluetooth devices. See vCard.
Business Management Computer
BMC. The computer system used at a CATV (Cable TV) or MMDS (wireless) business office to keep track of subscriber accounts.
Business Model
The term business model came into use in the late 1990s with the advent of the investor enthusiasm for the Internet and the resulting stock market boom. The concept was the Internet was so revolutionary it would allow the creation of companies that worked differently to normal companies. For example, one popular business model was that you could give away your product and services on the Internet and pay for them by taking advertisements. Another concept was that you could sell things without direct mail catalogs, advertising and salespeople. All you needed was a web site. In fact very few of the new business models ultimately succeeded. But the term crept into the English language. Now when someone asks you "what's your business model?" they're really asking, how do you intend to get paid for whatever you intend to do?
Business PCS
Advanced communications technology that adds wireless capability to create an in-building or campuswide wireless communication network. This is also called Wireless PBX or Enterprise PCS. See those definitions.
Business Service
Service used primarily for any purpose other than that of a domestic or family nature. A telephone industry definition.
Business Support System
See BSS.
Business Technology Association
An association formerly known as Nomda/Landa.
Business Television
BTV. Point-to-multipoint videoconferencing. Often refers to the corporate use of video for the transmission of company meetings, training and other one-to-many broadcasts. Typically uses satellite transmission methods and is migrating from analog to digital modulation techniques.
Business to Business
Basically there are three types of ecommerce: First, where one business sells something to another. Second, where one business sells to a consumer, i.e. you or me. Third, where one consumer sells to another consumer. The medium for all this ecommerce is typically the Internet or a private Intranet, i.e. a network confined to one or several organizations. See also eCommerce.
Business to Consumer
See Business to Business.
Busker
A person who entertains in public places, especially for money. When Singapore decided to legalize street performances in 1997, artists were required to audition and to donate any money collected to charity.
Busy
In use. "Off-hook". There are slow busies and fast busies. Slow busies are when the phone at the other end is busy or off-hook. They happen 60 times a minute. Fast busies (120 times a minute) occur when the network is congested with too many calls. Your distant party may or may not be busy, but you'll never know because you never got that far.
Busy Back
A busy signal.
Busy Call Forwarding
When you call a busy phone extension, your call is automatically sent to another predetermined telephone extension.
Busy Hour
The hour of the day (or the week, or the month, or the year) during which a telephone system carries the most traffic. For many offices, it is 10:30 A.M. to 11:30 A.M. The "busy hour" is perhaps the most important concept in traffic engineering ” the science of figuring what telephone switching and transmission capacities one needs. Since the "busy hour" represents the most traffic carried in a hour, the idea is if you create enough capacity to carry that "busy hour" traffic, you will be able to carry all the other traffic during all the other hours. In actuality, one never designs capacity sufficient to carry 100% of the busy hour traffic. That would be too wasteful and too expensive. So, the argument then comes down to, "What percentage of my peak busy or busy hour traffic am I prepared to block?" This percentage might be as low as half of one percent or as high as 10%. Typically, it's between 2% and 5%, depending on what business you're in and the cost to you ” in lost sales, etc. ” of blocking calls.
PSTN busy hours during the past 20 years or so were from 2:00 to 3:00 P.M., when children arrived home from school and called their working parents to let them know that they were O.K. During the past year or so that busy hour has shifted to 7:00 to 11:00 P.M., reflecting the fact that working parents have put the children to bed and started to "surf the 'Net." See Busy Hour Usage Profile.
Busy Hour (Average Busy Season )
A telephone company definition. A time-consistent hour, not necessarily a clock hour, having the highest average business day load throughout the busy season. This must be the same hour for the entire busy season.
Busy Hour Call Attempts
BHCA. A traffic engineering term. The number of call attempts made during the busiest hour of the day.
Busy Hour Call Completion
BHCC. A measurement of telephone traffic determined by the system's busiest hour and used to determine system capacity.
Busy Hour Usage Profile
The busy hour usage profile identifies how a system will normally be used (i.e., who the users are and what type of transactions they are performing) during the busy hour. Different things that users of CT systems do stress the CT system in different manners. For example, sending a broadcast message in voice mail (where one message is automatically sent to many recipients) may force the system to perform 10 times as much disk I/O as sending messages to single recipients. Or, updating an account balance in an IVR transaction forces a strain on the IVR to mainframe link. Or, setting up conference calls across a switch or network stresses the use of the network database resources. Understanding and characterizing the type and mix of calls that will take place during the busy hour is key to designing and placing a real-world load on the CT system. Load testing a system should always incorporate tests using the busy hour call profile. See Busy Hour.
Busy Lamp
A light on a telephone showing a certain line or phone is busy. See Busy Lamp Field.
Busy Lamp Field
A device with rows of tiny lights that shows which phones in a telephone system have conversations on them, which phones are ringing, which phones are on hold. Each light corresponds to a telephone extension on the system. The busy lamp field usually sits attached to the attendant's console, telling the attendant if an extension is busy, free, on hold, etc. The benefit of having a busy lamp field is that the operator does- n't have to dial the number to find out what's happening with the extension. This saves the attendant time in handling incoming calls and gives the caller better service. A busy lamp field is often combined with DSS (Direct Station Select.) Next to each light on the busy lamp field there is a button which the operator can push which will dial the corresponding extension (i.e. directly select it) and will typically transfer the call automatically. This button is like an autodial button. This saves the time of dialing the two, three or more numbers of the extension. These days, busy lamp fields are often built into phones on a key system, and everyone, not just the operator, can have one. This gives everyone information on what's happening in the system. It makes transferring calls, etc. easier. See also Direct Station Select.
Busy Out
Let's say you have three lines in a hunt group. Let's say your first line dies. This will mean that your callers will now receive an endless ring tone ” with no one answering, even though you're in the office or at home. The best solution is to ask your friendly local phone company to "busy out" the broken line. This means to fool its switch that your line is busy, i.e. someone is speaking on it, and that the calls should be forwarded over to the next line. The easiest way to busy out a line is simply to short it, i.e. physically connect the two conductors ” tip and ring ” together. Just remember when you do get the line fixed, to unbusy out your line. Busying out lines going into a computer is useful when the computer is not available, i.e. during maintenance. This way callers do not get connected to modems with no computers to talk to. This is also known as "taking the phone off the hook." In a voice phone system with trunks that rotary (or hunt) on, sometimes busying one or more broken trunks out helps calls progress onto trunks that are still working. This way, someone doesn't end up on your third trunk with endless ringing, while your 4th, 5th, 6th etc. trunks are free. See Rollover Lines.
Busy Override
A feature of some PBXs which allows the attendant or other high priority user to barge in on a telephone conversation. A warning tone is usually thrown into the conversation to alert the parties to an override. The feature is also called "Barge-In." Sometimes when conversations are overridden, only the person within the organization can hear the barge -in.
Busy Period
A telephone company definition. A three to eight month period within which the three busy season months will occur. Example: November through April.
Busy Redial
Another name for Automatic Callback. (Verizon and some other companies use this name.) See also Automatic Callback.
Busy Season
An annual recurring and reasonably predictable period of maximum busy hour requirements ” normally three months of the year, and typically the three months preceding Christmas.
Busy Season Prior To Exhaust
A telephone company definition. The busy season prior to exhaust of an addition is defined as the latest busy season for which an addition will provide objective levels of service.
Busy Signal
A signal indicating the line called is busy. The busy signal is generated by the central office. There are two types of busy signals. See Busy.
Busy Test
A method of figuring whether something which can carry traffic is actually doing so or whether it's broken or free and available for use.
Busy Tone
See Busy Signal.
Busy Verification Of Station Lines
-
An attendant can confirm that a line is actually in use by establishing a connection (dialing in and listening) to that apparently busy line.
-
In the public switched telephone network, a switching system service feature that permits an attendant to verify the busy or idle state of station lines and to break into the conversation. An alternating tone of 440 Hz is applied to the line for 2 seconds, followed by a 0.5-second burst every 10 seconds to alert both parties that the attendant is connected to the circuit.
Busy/Idle Flag
A cellular radio term. A busy/idle flag is an indicator that is transmitted by the Mobile Data Base Station (MDBS) periodically to indicate whether the reverse channel is currently in the busy state or the idle state.
Butcher
Colloquial term for a telephone technician who tends to use cutters without verifying whether the cabling is active or inactive.
Butt in Chair
BIC. Butt in Chair is the designation for a technician who has to work on Saturday or Sunday, traditionally light days when not much happens. The purpose of the BIC is to be there just in case something happens.
Butt Set
See Buttinsky.
Butt Splice
Connecting the ends of two wires with a "butt splice connector," from such manufacturers as AT&T and 3M.
Buttinsky
Or Butt Set. The one-piece telephone carried on the hips of telephone technicians. It's called buttinsky or butt set because it allows technicians to "butt in" on phone calls, not because the device is worn on their butts. Butt sets used to be essentially telephones without ringers. But now they are much more sophisticated. They will pulse out in rotary or dial out in touchtone and allow you to talk or to monitor a call. They will run computerized tests on the line. Some even have the equivalent of an asynchronous computer terminal built in, which can be used to talk to a distant computer over a phone line. This distant computer could assign them their next jobs, allow them to check and assign features (touchtone, rotary, hunt), report the time spent on this job, etc. In short, the terminal and the computer could replace a raft of clerks and a deluge of paperwork.
The derivation of the term "buttinsky" has long been lost in history. Butt can also mean to attach the end of something to the end of something else. If the clips of a butt set are attached to a pair of wires, it is a "butt" connection. There are those people who also think that the term buttinsky came from some middle European language ” Polish or Yiddish ” and is slang for someone who butts in a lot, which is what you can do with a Butt Set. I shall keep researching this one. If you can help, let me know, please .
Button Caps
Interchangeable plastic squares fit over the buttons of electronic telephones, and are used to label the features programmed onto each programmable button location. Button caps can be either pre-printed or have clear windows which allow features, lines, and Autodial numbers to be labelled on the button.
Buttons
Why do men's clothes have buttons on the right while women's clothes have buttons on the left? Answer: When buttons were invented, they were very expensive and worn primarily by the rich. Because wealthy women were dressed by maids, dressmakers put the buttons on the maid's right. Since most people are right-handed, it is easier to push buttons on the right through holes on the left. And that's where women's buttons have remained since.
Buyside
Term that describes institutional investors and members of the investment community including mutual funds, hedge funds, trusts, and financial advisers. Sellside are brokerage firms.
Buzz
-
To check the continuity of a cable pair by putting an audible buzzer on one end and then checking with a "buttinsky" to see if you can hear the buzz and thus identify the correct cable pair.
-
A feature of a Rolm CBX which lets the user signal one Rolm desktop product without picking up the handset. Only one buzz per extension is permitted.
Buzzer
An electromechanical device that makes a buzzing noise when power is applied, often used to signal someone to answer an intercom call. Battery- powered buzzers were once used to help trace phone circuits. TONE GENERATORS are more common today, but old terminology is still used, as in "buzzing out a line."
Buzzer Leads
The wires inside a telephone intended for the connection of a buzzer, usually as part of an intercom system.
BVA
AT&T's exclusively-owned Billing Validation Application database. Today, BVA contains all the Regional Bell Operating Companies (RBOCs) calling cards, and other billing information such as billed number screening and payphone numbers. The RBOCs and AT&T access that database today. Prior to Divestiture three market players, the RBOCs, AT&T and most Independent Companies, dominated the "O" Operator Services business which provided alternate billing arrangements such as collect calls, bill to third number and charging calls to calling cards. The three market players still exclusively employ BVA which allows them to validate or authorize alternate billing arrangements. No other long distance carrier or a company needing access to the data for billing validation can use the system. The database is owned by AT&T and is updated daily by the RBOCs and Independent Companies with local exchange information, billing number screening and calling card information. The scenario is further complicated by the 1984 AT&T Plan of Reorganization's exclusive BVA access restrictions. In other words, the three original market players (AT&T, the RBOCs and Independent Companies) have exclusive access to BVA for a predetermined contract length. In most cases these arrangements run into the 1990's. See BVS.
BVS
Business Validation Service. US West Service Link was the first in the nation to develop and make available a nationwide Billing Validation Service open to any company that needs to verify the legitimacy of their callers' requests to place charge calls to their local telephone calling cards. US West Service Link developed BVS in 1987 and turned up the system for "on-line" customers in early 1988. Today, the US West BVS system is a national validation source containing calling card data of customers served by the RBOCs, GTE, Southern New England Telephone, United Telecommunications, Cincinnati Bell, Rochester Telephone and Telecomm Canada, a consortium representing all of Canada's local telephone operating companies. In all, more than 60 million records are stored. Sprint, MCI and ITI are among the carriers using BVS. BVS uses X.25 and SS7 protocol. See BVA.
BW
Bandwidth: a numerical measurement of throughput of a system or network. See Bandwidth.
BWA
Broadband Wireless Access.
BWM
Bandwidth Management System.
BX.25
AT&T's rules for establishing the sequences of events and the specific types and forms of signals required to transfer data between computers. BX.25 includes the international rules known as X.25 and more.
By-Wire
In days gone by, when you turned the steering wheel in a car or an airplane, it moved some wires which moved the wheels or the rudder. Ditto for the brakes. Nowadays, when you do something, the motion you make is detected by some electronic sensors, which is relayed to some computer chips. These chips then signal motors to turn the wheels or make the brakes work. Such a system is said to be more reliable and to allow the injection of computer "intelligence" into the process. For example, the computer might determine that you shouldn't be pushing the brakes because that will make the car skid and it will not apply the brakes.
Bypass
-
A term coming from the idea of using a method to bypass the local exchange network of the Local Exchange Carrier (LEC). Also known as Facilities Bypass, this approach is employed for several reasons:
-
Because the phone company is too expensive, or
-
Because the phone company can't provide the desired levels of bandwidth, quality, or responsiveness.
Bypass means you might be transmitting between two of your offices in the same city, perhaps between your office and your factory, using private microwave or lines you lease from the local power company. You might bypass both the LEC and IXC to link two or more company sites through microwave or satellite transmission systems. You also might be bypassing the LEC to connect directly to your friendly long distance carrier, which then carries your calls to distant cities. In the last case, fiber optic networks deployed by AAVs (Alternative Access Vendors), also known as CAPs (Competitive Access Providers) typically are used, although private microwave may be used as well. Bypass vendors increasingly include CATV providers, some of which have upgraded their coaxial cable networks to support two-way, interactive, switched voice and data communications.
Bypass is a word created by the local telephone industry to sound very threatening . The theory is major users will bypass their local phone company, depriving their phone company of needed revenues . This will drive the local phone company close to imminent bankruptcy, or at the very least, to the state regulators for huge rate increases, hurting the remaining customers, who would, presumably, be customers in areas where bypass is not available (i.e. the poor and the disadvantaged). Additionally, the thought is that the Universal Service Fund would be threatened, thereby depriving users in high cost areas (read "remote and rural") of the right to affordable telephone service. The reality of this threat has not been proven. Nevertheless, the rhetoric frightens sufficient regulators to look at the evils of bypass and to outlaw it, or at least severely restrict it ” as several states have done. The Telecommunications Act of 1996 changed the rules on bypass. Now it will happen big-time in the United States. See Telecommunications Act of 1996.
-
-
An AC power path around one or more functional units of a UPS. An automatic bypass is controlled by UPS control logic and activated when some part of the UPS malfunctions or intentionally shuts down due to an overload or other abnormal condition in order to maintain power to the protected load. A manual bypass is a user controlled switch on a UPS that allows a complete electrical bypass of the unit and may be engaged when there is a total UPS failure or when performing certain types of diagnostics or repair. A service bypass is a manual bypass that allows complete maintenance, or even removal, of the UPS without shutting off the load. A true service bypass is commonly a separate device from the UPS. This definition courtesy APC, a maker of UPSes.
Bypass Cabling
Bypass cabling or relays are wired connections in a local area ring network that permit traffic between two nodes that are not normally wired next to each other. Such bypass cabling might be used in an emergency or while other parts of the system are being serviced. Usually such bypass relays are arranged so that any node can be removed from the ring and the two nodes on either side of the removed node can then talk.
Bypass Circuitry
Circuits that automatically remove a device from the data path when valid signals are dropped.
Bypass Relay
A relay used to bypass the normal electrical route in the event of power, signal, or equipment failure.
Bypass Switcher
An audio-follow-video switcher usually associated with a master control switcher. Used to bypass the master control switcher output during emergencies, failures, or off line maintenance.
Bypass Trunk Group
A trunk group circumvents one or more tandems in its routing ladder.
Byte
Abbreviated as "B" (big "B."). A set of bits (ones and zeros) of a specific length represent a value, in a computer coding scheme. A byte is to a bit what a word is to a character, which is why a byte sometimes is referred to as a "word." A byte might represent a letter, number, punctuation mark or other typographic symbol (e.g., ,, : , $, @, &, or !), or control character (e.g., carriage return, line feed, beginning/ending flag, or error check). The term generally is thought as designating a computer value consisting of eight bits, which technically is known as a "physical byte." For example, ASCII code makes use of an 8-bit byte, comprising seven information bits and one parity bit for error control. EBCDIC (IBM's invention) makes use of an 8-bit byte, with all bits being information bits. In some circles, a byte is called an octet. This is the case in the world of broadband networking, although an octet, more correctly, is a set of 8 bits, which may comprise more than one byte. A "logical byte," as opposed to a "physical byte," may comprise fewer than 8 bits, or more. A 4-bit byte is often referred to as a "nibble," proving that humor is pervasive, even in the world of computer code. A byte can consist of more than 8 bits, as is the case with Unicode, which involves 16-bit bytes. Unicode is a standard coding scheme used to accommodate complex alphabets such as Chinese and Japanese. Note that computer storage capacity is measured in bytes, while transmission capacity and speed (also called bandwidth) is measured in bits per second (bps). The exceptions to this rule are Fibre Channel, ESCON and other transmission standards which are used in Storage Area Networks (SANs); those standards measure bandwidth in Bytes per second (Bps). See also Bps and Byte Count.
Now, let's have some fun with numbers as we count bytes. The real fun starts when we get a Kilobyte (KB). The actual definition can be confusing, since there are two measurements. In the metric system, a kilobyte is 1,000 bytes, or 10 to the third power. In the computer world, things tend to be measured in binary terms ” 1s and 0s. In other words, we work with powers of 2, rather than powers of 10. In binary terms, a kilobyte is 2 to the 10th power, or 1,024. It's not exactly 1,000 bytes, but it's pretty close. Following is a summary of sizes, in binary terms, noting that each step in the progression involves a multiplier of 1024, with the exception of googolbyte:
KB = Kilobyte = 1,024 bytes (2 to the 10th power)
MB = Megabyte = 1,048,576 bytes (2 to the 20th power)
GB = Gigabyte = 1,073,741,824 bytes (2 to the 30th power)
TB = Terabyte = 1,099,511,627,776 bytes (2 to the 40th power)
PB = Petabyte = 1,125,899,906,842,624 bytes (2 to the 50th power)
EB = Exabyte = 1,152,921,504,606,846,976 bytes (2 to the 60th power)
ZB = Zettabyte = approximately 1,000,000,000,000,000,000,000 bytes (2 to the 70th power)
YB = Yottabyte = 2 to the 80th power, i.e., approximately 10 with 80 zeroes
One googolbyte equals 2 to the 100th power bytes, i.e., approximately 10 with 100 zeroes bytes.
Byte Bonding
From Wired Magazine. Byte Bonding occurs when computer users get together and discuss things that noncomputer users don't understand. When byte-bonded people start playing on a computer during a noncomputer- related social situation, they are "geeking out."
Byte Code
The executable form of Java code that executes within the Java virtual machine (VM). Also called interpreted code, pseudo code, and p-code .
Byte Count
The number of 8-bit bytes in a message. Since ASCII characters typically have 8 bits, the byte count is also called the character count.
Byte Count Protocol
A class of data link protocols in which each frame has a header containing a count of the total number of data characters in the body of the frame.
Byte Interleaving
Byte interleaving is the process used in TDM (Time Division Multiplexers) in applications such as digital voice. Using PCM (Pulse Code Modulation) and T-1 TDM as an example, 24 uncompressed voice conversations can be supported over a single T-1 facility. The amplitude (i.e., volume level) of the native analog voice signals are sampled 8,000 times a second by a codec ( coder /decoder). Each sample is expressed in the form of an eight-bit byte. The bytes are interleaved, beginning with a byte from conversation #1, then conversation #2, and so on through conversation #24. The process continues over and over again, always in the same order. On the receiving end, the process is reversed , and the analog voice signals are reconstructed. See also Byte, PCM, T-1, and TDM.
Byte Multiplexer Channel
An IBM mainframe input/output channel that allows for the interleaving, or multiplexing, of data in bytes. Compare with block multiplexer channel.
Byte Multiplexing
A byte (or value, or character) from one channel is sent as a unit, with bytes from different channels following in successive time slots. In this manner the bytes are interleaved. See Multiplex .
Byte Stuffing
The process whereby dummy bytes are inserted into a transmission stream so that the net data transmission rate will be lower than the actual channel data rate. The dummy bytes are identified by a single controlling bit within the byte.
Byte Synchronous
A SONET term describing the manner in which channelized DS- 0 level data is mapped into the SONET frame. There are two approaches: Floating Mode and Locked Mode. Floating Mode requires that each frame in the originating T-1 frame be identified in order that the constituent DS-0 bytes can be mapped into the SONET frame effectively through alignment with SONET bytes. The individual T-1 frames, which are converted into VT1.5s as they are mapped into the SONET frame, can float within the SONET frame; this approach is highly effective, but complex and expensive. Locked Mode mapping involves the direct mapping of a T-1 frame into a VT1.5 established at a fixed and inflexible location within the SONET SPE (Synchronous Payload Envelope). This latter approach is much simpler and more efficient than is Floating Mode, but not as effective in maximizing the load balance of the SONET network. In any case, the timing of incoming DS-0 signals must be maintained as they enter the SONET network, are transported through it, and exit it to re-enter the T-carrier network digital hierarchy to be presented to the target device.
Loss of timing renders the data useless. Timing is everything. Compare and contrast with Bit Synchronous. See also SONET and VT.
Byte Time
Byte time is the time it takes to transmit a byte at wireline speed. Examples of Usage: Frame Relay is much faster than X.25: frames are switched to their destination with only a few byte times delay, as opposed to several hundred milliseconds delay on X.25. Late collisions (of Ethernet packets) are detected by the transmitter after the first "slot time" of 64 byte times. They are only detected during transmissions of packets longer than 64 bytes. Its detection is exactly the same as for a normal collision; it just happens "too late."
Byte Timing Circuit
Optional X.21 circuit used to maintain byte or character synchronization.
Bytecode
A Java compiler creates platform-independent bytecode, an intermediate data format between the source code written by a programmer and the machine code required by the target computer. The bytecode then is morphed into machine-specific executable code by the a Java Virtual Machine (JVM), a real-time interpreter that resides on the client computer. Bytecode allows a Java applet to be executed on any machine that is running a Java Virtual Machine. See also Compiler, Interpreter, and Java Virtual Machine.
BZT
Bundesamt fur Zulassungen in der Telekommunikation. The name of the German telecom approval authority. It was established in 1982 under the name of the Central Approvals Office for Telecommunications. The name was changed to BZT on March 10, 1992. It is currently based in Saabrucken.