Accessing Signatures Through Signature Groups
| [ LiB ] |
We've seen in the previous section how to configure global sensing. Now we go through the signature groups, which you need to understand to access a signature for tuning or to create a custom signature. You access signatures from Configuration, Settings, Signatures. You use a drop-down menu to access the signature group of interest. Figure 10.3 shows how you can use the signature drop-down menu to select a group of signatures to access.
Figure 10.3. Use the signature drop-down menu to access signatures by group or Signature ID.
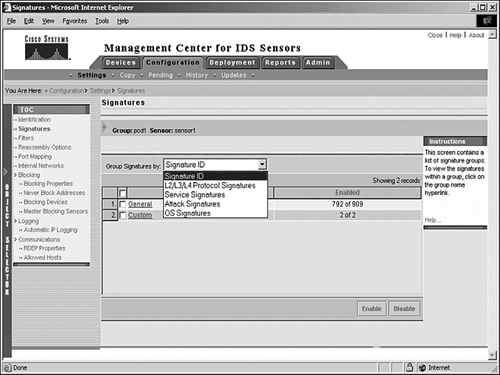
The signatures are grouped in the following way:
-
Signature ID
-
L2/L3/L4 protocol
-
Service signatures
-
Attack signatures
-
OS signatures
Figure 10.3 also shows that by selecting Signature ID from the drop-down menu, you can select the General check box to access all preloaded signatures or the Custom check box, which allows you to access all custom signatures.
L2/L3/L4 Protocol Signatures
L2/L3/L4 signatures operate at Layers 2, 3, and 4 and include Address Resolution Protocol (ARP), TCP, User Datagram Protocol (UDP), and Internet Control Message Protocol (ICMP) signature engines. When you select the L2/L3/L4 option in the drop-down menu from the Signatures page, the list of signatures and numbers appears (see Table 10.2).
Table 10.2. L2/L3/L4 Signatures and the Numbers Enabled
| L2/L3/L4 Signatures Group Name | Enabled |
|---|---|
| ARP Signatures | 2 of 4 |
| General IP Signatures | 22 of 23 |
| General TCP Signatures | 585 of 667 |
| TCP Flood Signatures | 0 of 1 |
| TCP Hijacks Signatures | 2 of 2 |
| TCP Host Sweeps Signatures | 8 of 8 |
| TCP Anomalies Signatures | 8 of 8 |
| TCP Port Sweeps Signatures | 12 of 12 |
| General UDP Signatures | 180 of 191 |
| UDP Flood Signatures | 1 of 2 |
| UDP Protocol Anomalies Signatures | 1 of 1 |
| UDP Port Sweeps Signatures | 2 of 2 |
| General ICMP Signatures | 8 of 22 |
| ICMP Floods Signatures | 1 of 4 |
| ICMP Host Sweeps Signatures | 3 of 3 |
| ICMP Protocol Anomalies Signatures | 1 of 2 |
| Miscellaneous Protocol Signatures | 5 of 5 |
| TCP/UDP Combo Sweeps Signatures | 2 of 2 |
The steps to edit and enable a specific signaturein this example, the Back Door UDP port 21 signatureare as follows :
- Navigate to Configuration, Settings, Signatures.
- Select the L2/L3/L4 options from the Signatures drop-down menu.
- Click on the General UDP Signatures group name to display the list of signatures in the group.
- Click on the name of the signature that you want to configure, in this case, the Back Door UDP port 21 signature.
- Choose settings within the Edit Signatures page. These settings are listed and described in Table 10.3.
Table 10.3. Options in the Edit Signatures Page
| IDS MC Edit Signatures Settings | Description |
|---|---|
| Enable check box | Allows you to enable or disable the signature. |
| Severity drop-down menu | Allows you to set the severity level for the signature. The available options are info , low, medium, and high. |
| Actions check boxes | Allow you to set the action that will be performed when the signature is triggered. The available options are log, reset, block host, and block connection. |
You can enable a set of signature groups by selecting the check boxes to the left of the signature group and clicking the Enable button. Figure 10.4 shows that all ARP Signatures, General TCP Signatures, and TCP Floods Signatures will be enabled when you click Enable.
Figure 10.4. Enable multiple signature groups by selecting the check boxes and clicking the Enable button.
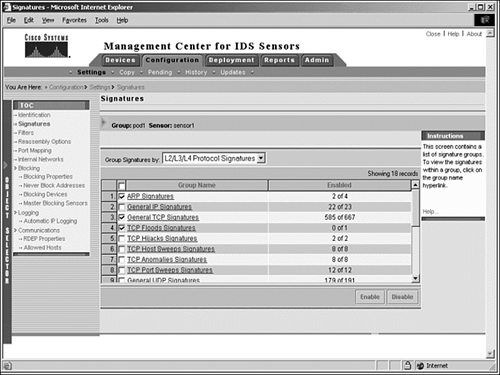
| | You can enable multiple signature groups by selecting a signature group using the Group Signatures drop-down menu on the Configuration, Settings, Signatures page, selecting the check boxes for the desired signature groups, and then clicking the Enable button. |
The steps listed here to edit and enable a signature or to enable a group of signatures are the same for all signatures, so we don't repeat them for the remaining signature groups.
Attack Signatures
The attack signature group consists of signatures which detect attacks that have predefined host or network targets. Table 10.4 lists the attack signature groups and the number of signatures enabled within the group.
Table 10.4. Attack Signatures and the Numbers Enabled
| Attack Signatures Group Name | Enabled |
|---|---|
| General Attack Signatures | 76 of 118 |
| DoS (Denial-of-Service) Signatures | 69 of 81 |
| DDoS (Distributed DoS) Signatures | 12 of 12 |
| Information Signatures | 82 of 86 |
| Reconnaissance Signatures | 163 of 177 |
| File Access Signatures | 100 of 124 |
| Code Execution Signatures | 231 of 246 |
| Viruses/Worms/Trojans Signatures | 27 of 27 |
Service Signatures
Signatures based on services that are operating systemindependent are grouped together in the service signature group.
| | Service signatures are based on services provided on the network that are operating systemindependent. |
Table 10.5 lists the service signatures and the numbers enabled.
Table 10.5. Service Signatures and the Numbers Enabled
| Service Signatures Group Name | Enabled |
|---|---|
| General Service Signatures | 149 of 197 |
| SQL (Structured Query Language) Signatures | 1 of 1 |
| DNS (Domain Name Service) Signatures | 34 of 34 |
| Finger Signatures | 10 of 10 |
| FTP (File Transfer Protocol) Signatures | 27 of 28 |
| HTTP (Hypertext Transfer Protocol) Signatures | 344 of 397 |
| Ident Signatures | 4 of 4 |
| IMAP (Internet Message Access Protocol) Signatures | 2 of 2 |
| NNTP (Network News Transfer Protocol) Signatures | 2 of 2 |
| LPR Signatures | 1 of 1 |
| NetBIOS/SMB (Server Message Block) Signatures | 18 of 18 |
| NTP (Network Time Protocol) Signatures | 1 of 1 |
| POP (PostOffice Protocol) Signatures | 5 of 5 |
| R-services Signatures | 3 of 3 |
| RPC (Remote Procedure Call) Signatures | 66 of 70 |
| SMTP (Simple Mail Transfer Protocol) Signatures | 22 of 22 |
| SNMP (Simple Network Management Protocol) Signatures | 51 of 51 |
| SSH (Secure Shell) Signatures | 2 of 2 |
| Telnet Signatures | 12 of 13 |
| SOCKS Signatures | 0 of 1 |
| TFTP (Trivial File Transfer Protocol) Signatures | 3 of 3 |
| HTTPS (Secure HTTP) Signatures | 1 of 1 |
| DHCP (Dynamic Host Configuration Protocol) Signatures | 0 of 1 |
OS Signatures
OS signature groups target specific operating systems. You can use OS signature option to access these signatures. Table 10.6 lists the OS signature groups and the numbers enabled.
Table 10.6. OS Signatures and the Numbers Enabled
| OS Signatures Group Name | Enabled |
|---|---|
| General Unix Signatures | 182 of 188 |
| General Linux Signatures | 1 of 1 |
| Red Hat Linux Signatures | 1 of 2 |
| SuSE Linux Signatures | 2 of 2 |
| Mandrake Linux Signatures | 1 of 1 |
| General Solaris Signatures | 17 of 18 |
| HP-UX Signatures | 1 of 1 |
| AIX Signatures | 2 of 2 |
| IRIX Signatures | 9 of 11 |
| General Windows Signatures | 108 of 124 |
| General Windows NT Signatures | 48 of 55 |
| WinNT Signatures | 13 of 14 |
| IOS Signatures | 11 of 14 |
| General OS Signatures | 353 of 431 |
| NetWare Signatures | 1 of 1 |
| MacOS Signatures | 3 of 3 |
| [ LiB ] |