Inbound Traffic
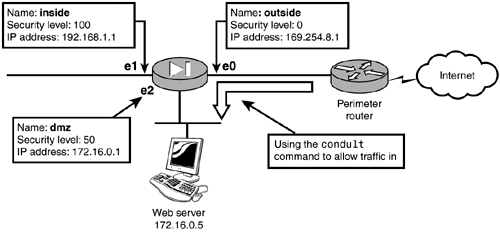
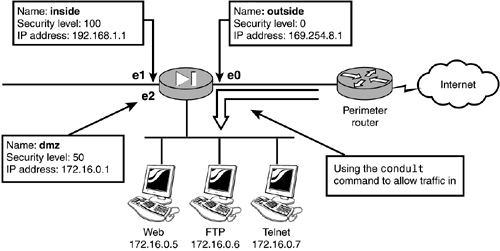
| By default, the PIX prevents any traffic initiated on the lower security levels from accessing higher security level interfaces. However, when computers such as Web servers are located in a DMZ, you might need to open the firewall and allow external users to access the Web server. By using the static and conduit command, you can allow traffic initiated from the outside in to the DMZ or inside interfaces. Access lists can also be used to allow traffic in (they are covered in Chapter 6, "Access Control Lists and Traffic Control"). For example, to allow Peter access to your Web server located in the DMZ, you first need to create a static mapping of the Web server to a global IP or port address. Then, you must use either the conduit command or an access list to allow traffic to pass from the lower security level interface to the DMZ. You've seen the static command in action, and you know how to create a one-to-one mapping of IP addresses. But the conduit command is a special case because it is currently being replaced by the introduction of the access control list commands into the PIX IOS. Cisco doesn't recommend using the conduit command, but you do need to be familiar with it. Using conduits enables you to control inbound access to the PIX. In Figure 5.10, any traffic from the outside is allowed to access the Web server. Figure 5.10. The static and conduit commands. Listing 5.9 demonstrates the conduit command. Listing 5.9 The conduit CommandPixfirewall(config)# static (dmz, outside) 169.254.8.2 172.16.0.5 Pixfirewall(config)# conduit permit tcp host 169.254.8.2 eq www any Pixfirewall(config)# Pixfirewall(config)# exit Pixfirewall# clear xlate The static command in Listing 5.9 maps the Web server's internal address to the global address of 169.254.8.2. The conduit command permits any traffic destined to global address 169.254.8.2 with port 80 ( www ) to enter the PIX. Once inside, the PIX translates the destination of the global address of 169.254.8.2 to the mapped internal address of 172.16.0.5 and passes the traffic. This setup works well when you have several NAT-able addresses. Figure 5.11 displays three servers in the DMZ that need to be accessed via the outside interface. The static commands map global addresses to DMZ addresses, and the conduits create exceptions to the ASA for certain protocols using the static mappings. Figure 5.11. Static and conduit to multiple DMZ servers. Listing 5.10 shows the static and conduit commands allowing traffic from any host to any of the three servers. Listing 5.10 conduit Commands for Multiple DMZ ServersPixfirewall(config)# static (dmz, outside) 169.254.8.2 172.16.0.5 Pixfirewall(config)# static (dmz, outside) 169.254.8.3 172.16.0.6 Pixfirewall(config)# static (dmz, outside) 169.254.8.4 172.16.0.7 Pixfirewall(config)# Pixfirewall(config)# conduit permit tcp host 169.254.8.2 eq www any Pixfirewall(config)# conduit permit tcp host 169.254.8.3 eq ftp any Pixfirewall(config)# conduit permit tcp host 169.254.8.4 eq telnet any Pixfirewall(config)# Pixfirewall(config)# exit Pixfirewall# clear xlate
Port RedirectionUsing NAT is great for creating one-to-one mappings of internal and global external addresses. However, if your ISP gives you only a single address to work with and you still want internal computers to be accessed via the Internet, port redirection is your solution. By using a single IP address on the outside, you can direct the traffic to the desired internal server by mapping the port numbers . For example, if Jack has only one outside address (169.254.8.1) but needs to access three servers via the Internet, he could create a mapping as shown in Table 5.4. Table 5.4 shows that external global addresses and ports are mapped to internal addresses and ports. Table 5.4. Port Redirection Example
Whenever traffic comes in entering 169.254.8.1:80, it is redirected to the internal server at 172.16.0.1:80. This enables Jack to use a single IP address and still access several services hosted behind the firewall. Listing 5.11 is an example of using the static command with the port option to make one-to-one mappings using a single address and a specific port. Listing 5.11 Port RedirectionPixfirewall(config)# static (dmz, outside) 169.254.8.1 80 172.16.0.1 80 Pixfirewall(config)# static (dmz, outside) 169.254.8.1 21 172.16.0.2 21 Pixfirewall(config)# static (dmz, outside) 169.254.8.1 23 172.16.0.3 23 Pixfirewall(config)# Pixfirewall(config)# conduit permit tcp host 169.254.8.1 eq www any Pixfirewall(config)# conduit permit tcp host 169.254.8.1 eq ftp any Pixfirewall(config)# conduit permit tcp host 169.254.8.1 eq telnet any Pixfirewall(config)# Pixfirewall(config)# exit Pixfirewall# clear xlate
|
EAN: 2147483647
Pages: 218