ASA Security Rules
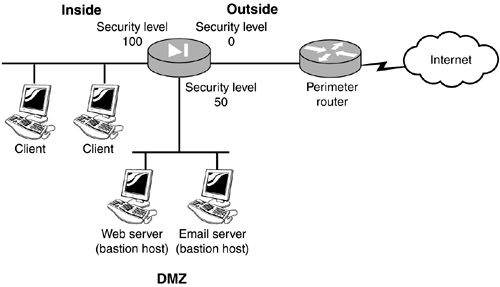
| A PIX firewall has a very simple mechanism to control traffic between interfaces. The ASA uses a concept of security levels to determine whether traffic can pass between two interfaces. The higher the security level setting on an interface, the more trusted it is. Security LevelsThe ASA allows traffic to pass from trusted to untrusted, but not the reverse. Therefore, traffic can pass from interfaces with higher security levels to interfaces with lower security levels. Correspondingly, ASA blocks traffic from interfaces with lower settings from passing through to interfaces with higher settings. To illustrate , consider a common scenario where the inside interface has a security level number of 100 and the outside has a level of 0. The ASA allows traffic to pass from the inside to the outside; however, the ASA prevents traffic from flowing from the outside to the inside because the inside has a higher security level. Figure 3.7 shows a three-pronged firewall with different security levels on each interface. Interface e0 has security a level of 0, which makes it the lowest security level of all the interfaces. Any traffic initiated on this side of the firewall will not be able to communicate with computers on the other side of the firewall. Figure 3.7. Security levels. The following are the primary security levels created and used on the PIX firewall:
Connection and Translation TablesThe ASA uses two tables to track traffic flowing through the PIX ”the connection table and the translation ( xlate ) table. The connection table contains a reference to the session connection between the two computers that are talking. The translation table maintains a reference between the inside IP address and the translated global IP address. These topics are covered in further detail later. |
EAN: 2147483647
Pages: 218