The Secure Network
| Obtaining a secure network is not a destination, but a never-ending quest to provide the best protection while the environment is constantly changing. A secure system today could be a very insecure system tomorrow, as hackers discover new vulnerabilities and security holes. Security policies and processes help set rules and guidelines to assist in acquiring and maintaining the most secure network environment possible. The Security PolicyThe security policy is the core document or set of procedures used to describe how an organization's information, data, and services will be protected. The policy supports the organization's primary security objectives, as defined by who will be allowed access, who will be denied access, and what explicitly the policy aims to protect. Lastly, this document should define roles, responsibilities, and managed expectations and provide guidelines in the event of a security breach or noncompliance .
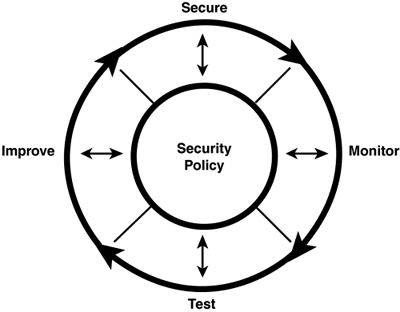
The Security ProcessSecurity requires an ongoing process of evaluation and adaptation. What works today might not be secure enough tomorrow. Cisco has created the security wheel to represent graphically the continuously evolving process of security. This process entails securing, monitoring, testing, and improving the security policy and technical changes necessary to protect the environment. Figure 2.1 shows the Cisco security wheel. Figure 2.1. The Cisco security wheel. The Cisco Security Wheel contains four basic steps to help visually display the process needed to maintain a secure environment. These steps are listed here:
Step 1: Securing the EnvironmentSecuring the environment involves the implementation of various tools addressing different points of vulnerability. Authentication systems, such as One-Time-Passwords (OTP) support and Cisco Secure Access Control Server (CSACS), aid protection by allowing only authenticated users into the environment. Encryption techniques can be used to disguise data traveling across insecure media; virtual private network (VPN) tunnels encrypted using Internet Protocol Security (IPSec) are a good example of this. Implementing firewalls, which filter incoming and outgoing traffic, can provide another layer of protection between a corporate inside network and outside intruders. Systems with known security holes should be kept up-to-date through the use of vulnerability patching. Physical security, which is often overlooked, involves keeping equipment secure behind locked doors. For example, if an intruder can physically access Cisco equipment, he can employ password-breaking procedures and have his way with your systems. Step 2: Monitoring the Environment for Violations and AttacksMonitoring for violations plays a critical role in determining how effective the secured environment is in supporting the security policy requirements. Using intrusion detection systems, such as Cisco Secure Intrusion Detection Systems (CSIDS), can provide an excellent solution for monitoring and blocking unwanted traffic. In addition, logging information such as user access and modifications to system settings can be recorded. Because the recording of log files can accumulate large amounts of raw data, you should store this data in a separate location, such as the Syslog server. Step 3: Testing the Security of the EnvironmentAfter establishing your secure environment and security monitors , testing your environment is the only way you can ensure that your security measures are upholding your policy. Also, testing helps find new security holes in the environment before hackers find them. Cisco Secure Scanner is a tool you can use to test and identify such security holes. Step 4: Improving the Security PolicyImproving the security policy within a varying and highly unpredictable external environment is an ongoing job. Continuously monitoring, testing, and identifying flaws and attacks against the network are imperative in refining and tuning the security policy. Vulnerability reports enable administrators to maintain an awareness of new potential attacks and should be considered during this step. This chapter introduced the types of security threats that can be present against your networks. The security policy can be used to help you document what in your company needs protecting and how you will go about protecting that data. Cisco's security wheel demonstrates the ever-evolving enhancements you need to make to your security policy to keep you on the leading edge of protection and monitoring. |
EAN: 2147483647
Pages: 218
- Chapter II Information Search on the Internet: A Causal Model
- Chapter III Two Models of Online Patronage: Why Do Consumers Shop on the Internet?
- Chapter VIII Personalization Systems and Their Deployment as Web Site Interface Design Decisions
- Chapter XIII Shopping Agent Web Sites: A Comparative Shopping Environment
- Chapter XIV Product Catalog and Shopping Cart Effective Design