Internet Protocol Security
| Internet Protocol Security (IPSec) is not really a protocol, as the name would suggestit is actually a framework of many protocols and mechanisms working together to produce a secure connection between two peers. The heart of IPSec works at the Network layer of the OSI model. Some of the features this framework provides are as follows :
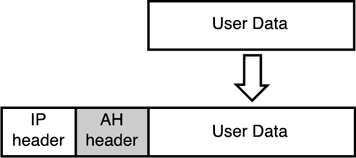
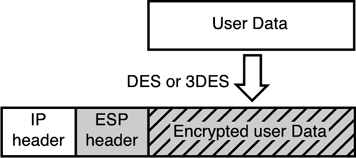
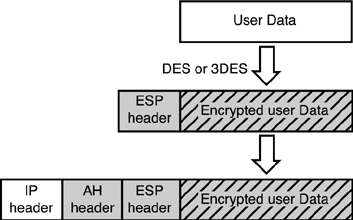
IPSec ComponentsIPSec contains several separate components that all work together to make a secure connection between two peers. This section highlights these components; then we will link them all together to make an IPSec Security Association (SA). Authentication HeadersThe authentication header (AH) mode of IPSec provides data authentication and anti-replay protection. Data authentication is also known as data integrity , meaning that AH checks to ensure that the data has not been altered . AH also provides data origin authentication to ensure that the data is coming from the correct source. AH doesn't actually encrypt data. Also, if it's used alone, it does not provide data confidentiality. Figure 12.6 shows user data being placed in an AH-protected packet. Figure 12.6. An AH example. Encapsulation Secure PayloadEncapsulation Secure Payload (ESP) performs what most people need, data confidentiality. ESP also performs data authentication and anti-replay protection. ESP encrypts the whole payload, which contains layer 4 headers and the data. ESP uses protocol port 50 and can either be used with AH or stand alone to provide data confidentiality. Figure 12.7 shows user data being encrypted and protected within ESP. Figure 12.7. An ESP example.
Internet Key ExchangeInternet Key Exchange (IKE) is a hybrid of several other protocols such as ISAKMP and the Oakley and Skeme key exchange. When two computers (peers) connect, they need to exchange policies and keys for hashing and encryption. IKE and ISAKMP perform these functions.
Diffie-HellmanThe Diffie-Hellman (D-H) algorithm is actually part of the IKE process to exchange keys safely and securely. D-H uses a pair of asymmetric keys, and each peer's public key is exchanged with the other peer's. These public keys are then combined with the others' private keys to generate an identical symmetric key on both peers. This new shared secret (symmetric) key is used to provide encryption and decryption during the IKE establishment phases. The PIX is capable of using either 768-bit (group 1) or 1024-bit ( group 2) D-H groups. AuthenticationWhen two IPSec peers connect, they need to authenticate before secure data can be transmitted. This authentication can be done in several ways; the following list describes three methods that can be used to authenticate peers:
Security AssociationThe security association (SA) is similar to a session between TCP hosts . Whenever two peers make a successful transfer of data using IPSec, an SA is created in the background to maintain the connection. This SA identifies each peer by IP address, security protocols, and a security parameter index (SPI).
How IPSec WorksNow that we've reviewed hashing, keys, encryption, AH, and ESP, let's put them all together and see how the IPSec framework makes a secure connection between two peers. IPSec is similar to creating a TCP connection that uses a three-way handshake. The peers exchange several parameters to create a security association; then, after the security association has been established, data can be sent in a protected manner. This exchange is comprised of two main phases called phase 1 and phase 2. Following are some of the steps needed to create an IPSec security association between two peers:
To prepare you, phase 1 and phase 2 are where most of your parameters need to be configured between two peers. If they match, a successful security association can be made. Phase 1IKE controls phase 1 to create a management connection between the two peers. The management connection exchanges ISAKMP policies, keys, and authentication information. ISAKMP polices are negotiated parameter sets that each peer uses to communicate. Some of the parameters inside an ISAKMP policy include
Peers can contain multiple policies; as peers connect, they iterate through the policies until a matching set is found on both sides. For example, say Jack's policy uses DES and MD5 and Peter's policy uses 3DES and MD5. Because these polices don't match, Jack and Peter will not be able to connect. However, if Peter's policy contains a second policy that matches Jack's, this phase will succeed and they can move on to the next step. Phase 1 also uses Diffie-Hellman to generate symmetric keys for encryption or hashing. Finally, the authentication is completed between the two peers. When all this is completed, enough information exists to make a secure connection to send IPSec parameters in phase 2.
Phase 2After phase 1 is completed, IKE starts phase 2. Phase 2 creates a user connection that negotiates IPSec parameters such as the transform sets. Transform sets are the modes or methods the two peers use to protect user datafor instance, AH, ESP, or both. Phase 2 also negotiates the encryption key, hash keys, and lifetime of how long the keys are valid before regeneration is necessary. When all these processes are complete, an SA is formed . The parameters contained on a crypto map that are sent between peers are as follows:
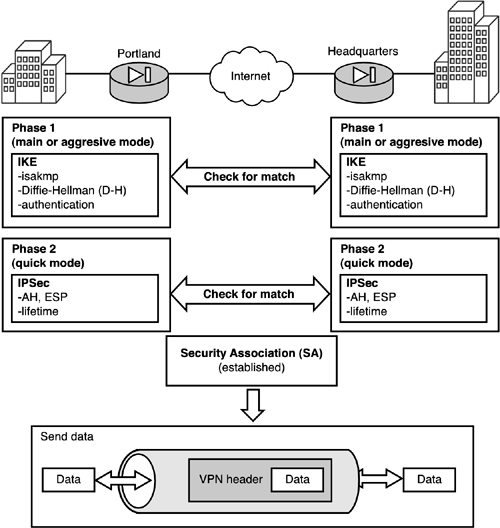
After phase 2 is complete, peers start to send data securely. Figure 12.9 displays phase 1 and phase 2 checking for matching parameters before creating a security association and sending data. Figure 12.9. Phase 1 and phase 2 example.
|
EAN: 2147483647
Pages: 218