Introduction to AAA Services
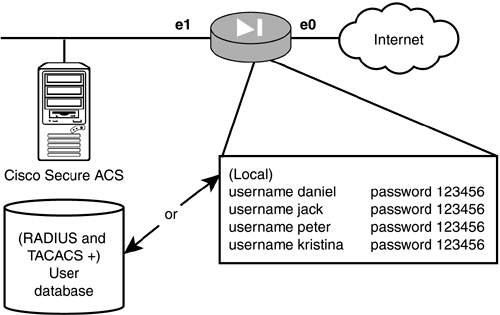
| In any Cisco environment, several features can provide administration overhead issues on your devices. The first administration feature your devices have is the enable or privilege exec password. This provides access to all the configuration commands on a device; however, managing this password could become an issue. For example, if Jack supports 300 Cisco routers and firewalls, trying to keep the enable password the same or changing it on all the devices could be an overwhelming task. A second feature of Cisco devices is the capability to create several levels of access on the device. For example, if you have several different network engineers , each engineer can be restricted to a subset of commands and not the entire privilege exec list. However, if Jack had to create the same users on each of his 300 devices, it could take several days to configure and maintain the systems. A third feature is providing access through devices. The PIX supports several features, such as cut-through proxy, that can require a user to authenticate before Internet access is granted. Again, if Jack had to manage 1,000 employee usernames and passwords on multiple PIX firewalls, he would have to spend all of his time managing and changing passwords. AAA services help administrators manage Cisco devices by offloading authentication, authorization, and accounting tasks from local devices to centrally located servers. These servers can contain databases of users, passwords, dynamic ACLs, authorization settings, and account tracking features, just to name a few. Using central servers in the example with Jack, he could manage the central server username list in one location and just point all 300 devices to that location for AAA services. Figure 10.1 displays two of these locations for usernames and passwords. One is called local and resides within the PIX configuration file; the other is called Cisco Secure ACS and is a user database located on a AAA server. The third place where users can exist, though not shown in Figure 10.1, is in external user databases such as Microsoft Windows. Figure 10.1. Username locations. AuthenticationAuthentication is the process of validating a username and password. The PIX can check the local database or a remote AAA server database for valid usernames and passwords. After the user establishes positive authentication, authorization is the next step. AuthorizationSuccessful authentication is required before authorization can occur. Authorization defines what a user can and cannot do. For example, a dynamic ACL can be downloaded to the PIX, restricting a user to or from particular networks. AccountingAccounting is the feature that enables administrators to keep track of what their users do. For example, when a user logs in to the system, a log entry can be made. |
EAN: 2147483647
Pages: 218