NetStumbler
|
| < Day Day Up > |
|
The NetStumbler tool, http://www.netstumbler.com, identifies wireless access points and peer networks. It does not sniff TCP/IP protocol data. Instead, it provides an easy method for enumerating wireless networks. You just launch the application, walk (or drive as in “wardriving”) around an area, and watch as wireless devices pour into the list.
Implementation
Even though NetStumbler appears to grab SSIDs from the ether, it works on a simple principle. It transmits connection requests to any listening access point with an SSID of ANY. Most APs respond to the request by sending their own SSID. Consequently, NetStumbler is not a passive sniffer. In other words, its traffic can be seen on the victim or target networks.
When you launch NetStumbler and start a capture file, it begins to search for access points. Figure 17-1 shows some examples of access points. The right pane displays the MAC address of the AP and its corresponding information such as its WEP status, SSID, signal strength, and coordinates if a GPS unit is attached to the computer.
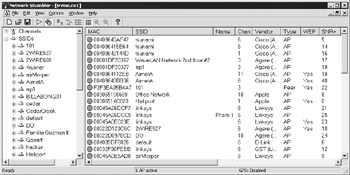
Figure 17-1: Detecting wireless networks
The left pane contains three tree views: Channels, SSIDs, and Filters. The Channels and SSIDs views break down the results into obvious fields. The Filters view also shows APs, but only if they meet certain criteria. Table 17-1 describes each of the default filters.
| Filter Name | Description |
|---|---|
| Encryption Off | List all devices that do not have WEP enabled. This implies that you would be able to sniff the network's traffic. |
| Encryption On | List all devices that have WEP enabled. Early WEP implementations were insecure, and their traffic could be decrypted. |
| ESS (AP) | The Extended Service Set ID (ESSID) is an alphanumeric code shared by all APs and wireless clients that participate on the same wireless network. It enables multiple APs to serve the same network, which is important for physically and logically large networks. Thus, two APs could use the same channel and even have overlapping coverage but serve two unique wireless networks. The default ESSID is well known for a few APs: Cisco (tsunami), 3COM (101), and Agere (WaveLAN network). |
| IBSS (Peer) | This filter represents another wireless card in a peer-to-peer or ad-hoc mode. The concept is similar to a crossover cable on wired networks. This allows two (or more) wireless cards to communicate with each other without the presence of an AP. |
| CF Pollable | These APs respond to specific beacon packets to determine periods in which to broadcast. An AP that supports contention-free (CF) transmission is used to reduce collisions and improve bandwidth. |
| Short Preamble | An alternate method for specifying data in the 802.11b physical layer. The abbreviated preamble is used for time-sensitive applications such as voice-over IP or streaming media. |
The most difficult part of using NetStumbler is locating wireless networks. NetStumbler’s web site enables users to upload their own capture files, complete with SSID and GPS information. Then anyone can query the web site’s database to view the geographic location of access points.
| Note | Many access points support the ability not to broadcast the SSID. In this case, NetStumbler will not discover the AP. |
Wardriving grew out of the same culture that spawned war dialing (see Chapter 18). Instead of looking for computers by randomly dialing phone numbers, wardriving looks for computers by wandering an area. The amount of information that becomes available ranges from solely the SSID to IP addresses, usernames, and passwords. In some cases, a network will even offer a DHCP address to the wandering wireless card. Obviously, the security implications are severe. The NetStumbler web site contains a map of North America that contains access points discovered by casual observers. Although this tool doesn't grab every username or password on the wireless network (check out AiroPeek or kismet for that), it provides a clear illustration of the pervasiveness of wireless networks and the necessity for strong protocols to support the security of these networks.
Simply being able to view the SSID does not mean that the wireless network is insecure. Network administrators can encrypt access with strong WEP implementations or layered cryptography implementations and lock down access based on a card's MAC address. A wireless network's security increases greatly when combined with a VPN implemented on a protocol such as IPSEC. In fact, many network administrators place wireless access points in an untrusted segment of the network. Then they require legitimate users to authenticate to a centralized authentication server (such as LDAP or an Active Directory) or establish a VPN into the network. The ease in which unauthorized users can obtain a wireless signal outside of the physical boundaries of a building necessitates such steps. As we will see in the upcoming tools, there are more threats to the network than merely finding out its name, or SSID.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 189