Ettercap
|
| < Day Day Up > |
|
We’ve told you that sniffers work only on hubs, where network packets get sent to every connected machine on the hub. That’s not entirely true. Sniffers work only when network packets between other machines are forced to pass through the network interface of the sniffing machine. Having the sniffer connected to a hub is the easiest way to accomplish this. Another way to accomplish this is to configure a particular switch port so that all traffic on the switch also gets sent to that “switch monitoring” port. Our discussion of dsniff introduced us to another way of intercepting traffic that is not meant for the sniffer—ARP and DNS poisoning. Another tool that lets you sniff in this manner (and much, much more) is called ettercap, which is billed as a sniffer for switched LANs.
Installation
Ettercap can be obtained from http://ettercap.sourceforge.net/ and runs on Linux, BSD, Solaris 2.x, most flavors of Windows, and Mac OS X. You can download the source code and compile it yourself or you can download available binaries for your platform. Compiling on standard Linux and FreeBSD systems is rather simple, as the only library requirement is the Gimp Tool Kit 2 (GTK2) and OpenSSL libraries.
| Tip | The GTK interface for ettercap is new. You can disable it during compile time by running ./configure –disable-gtk. |
Ettercap allows other users to build their own ettercap plug-ins. These plug-ins can be used to extend the functionality of ettercap. The current distribution of ettercap (0.6.b as of the writing of this book) comes with 32 different plug-ins. You have to build and install the plug-ins separately using the make plug-ins and make plug-ins_install commands.
Implementation
When you run ettercap without any options, it will ARP scan your LAN and display a table of all the machines found on your LAN, as shown in Figure 16-7.
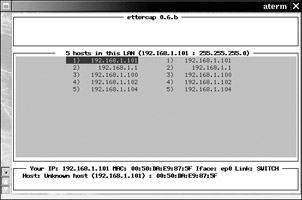
Figure 16-7: Ettercap main screen
Your next task is to choose either a source and destination to sniff or a sniffing mode. To select a source target, highlight an IP address on the left of the main screen and press ENTER. To select a destination target, highlight an IP address on the right and press ENTER. To clear targets, press the SPACEBAR. When you’re finished selecting targets, you can choose from three main sniffing modes.
IP-Based Sniffing
This is just standard sniffing; it simply displays traffic that passes over the network interface. For this mode, you don’t need to select any destinations; however, if the sniffer is on a switch, you won’t get any traffic but your own. You can access this mode by pressing S from the main screen shown in Figure 16-7. You can go back to the main screen by pressing Q.
MAC-Based Sniffing
MAC-based sniffing is just like IP-based sniffing, except it filters based on a system’s MAC address instead of its IP address. How is this different? When a machine on your LAN wants to talk to a machine that is not on the LAN, the traffic is sent to the LAN’s default gateway. The gateway forwards that traffic on to its external destination. Because any traffic destined for the external net must be sent to the local gateway, the Ethernet MAC address of those packets will be that of the gateway. By sniffing traffic with a destination MAC address of your gateway, you will intercept all outbound traffic passing through your gateway. This method also works only on traffic passing over the interface. You can access this mode by pressing M from the main screen.
ARP-Based Sniffing
ARP-based sniffing is ettercap’s calling card. This mode requires that you choose at least a source or destination. This allows you to intercept traffic, even on a switched network. Ettercap will ARP spoof the targeted host so that any ARP requests for the target’s IP will be answered with the sniffer’s MAC address, allowing traffic to pass through the sniffer before ettercap forwards it on. You can access this mode by pressing A from the main screen.
| Note | Ettercap’s ARP poisoning can sometimes cause disruptions on the LAN. For example, when attempting to do ARP-based sniffing on a source target that was running an instant-messaging (IM) client, the IM client lost connection with the server. When we performed ARP-based sniffing with a destination target of our default router, however, we were able to sniff all traffic with no disruptions. |
Because of its nature, ettercap’s ARP-based sniffing mode uses a “man-in-the-middle” attack similar to the one dsniff’s sshmitm tool uses to sniff clear-text SSH connections (version 1 only).
Navigating Sniffed Connections
Once you’ve activated a sniffer mode, you’ll see a list of open connections similar to the ones shown in Figure 16-8. Use your arrow keys to navigate the connections and press ENTER to select one. Once you’ve made a selection, you’ll see traffic coming from the source in the left-hand window and traffic coming from the destination in the right-hand window. At this point, you can do a number of things (press H at any time for a full list of available options), including setting up connection filters, replacing specific character data in network packets, killing the connection, and even injecting characters into the connection. The uses of some of these features are questionable, making this a dangerous tool in the hands of a hacker. If someone were running ettercap on your LAN, she could wreak havoc with your network connectivity. A nice thing about ettercap is that you can use it to check for other ARP poisoners on the network.
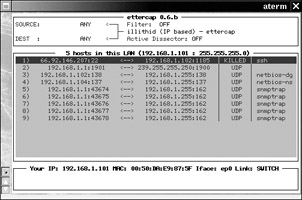
Figure 16-8: Ettercap list of connections
Additional Tools
Ettercap has some other handy tools. When you’re on the main screen shown in Figure 16-7, press F at any time to have ettercap tell you the OS and NIC manufacturer of the highlighted machine. Alternatively, you can press O to have ettercap watch passing network packets and attempt to determine passively the operating system of a host. One of ettercap’s coolest features is its ability to bind sniffed data to a port on the system. Someone connecting to that port with a client will be able to receive and interpret the sniffed data and even inject her own data.
Potential for Disaster
A lot of very technical, sneaky, and potentially disastrous features are buried in ettercap, and there’s no way we can cover them all here. Our main goal in this admittedly brief section is to make the reader aware of the existence of this tool. If you’re curious (or concerned) about this multifaceted wonder, visit ettercap’s web site at http://ettercap.sourceforge.net/ . The development forum in particular is a great place to learn about ettercap.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 189
- The Second Wave ERP Market: An Australian Viewpoint
- Data Mining for Business Process Reengineering
- Intrinsic and Contextual Data Quality: The Effect of Media and Personal Involvement
- Relevance and Micro-Relevance for the Professional as Determinants of IT-Diffusion and IT-Use in Healthcare
- Development of Interactive Web Sites to Enhance Police/Community Relations