Winfingerprint
|
| < Day Day Up > |
|
The Winfingerprint utility is in active development, has readily available source code, and pulls the most information possible across an IPC$ share. The development builds support Simple Network Management Protocol (SNMP) enumeration, accessing the event log and delving into the Active Directory structure.
Implementation
Winfingerprint is GUI-based, so keep your mouse finger in shape. The utility can scan a single host or a continuous network block. The information desired, from a port scan to registry information, is selected from any of the multiple checkboxes on the interface. The only confusing aspect is that clicking the OK button actually means “scan the target(s).” Figure 6-1 shows a scan against a single IP address using the “NT Domain” network type. The “Network Type” decides which Windows API Winfingerprint will use to enumerate the target hosts.
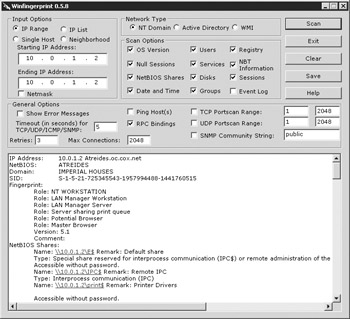
Figure 6-1: Winfingerprint scan using the “NT Domain” network type
-
NT Domain Use the Win32 API that has evolved from Windows NT 4.0. It will gather shares, users, password policies, and system information.
-
Active Directory Use the Active Directory Service Interface (ADSI) API to enumerate system information. This will not work correctly against Windows 2000 systems. It works well against Windows XP and Windows 2003 systems.
-
WMI Use the Windows Management Instrumentation API to enumerate system information. This may also be able to report service packs, hotfixes, and running services.
There’s no real trick to running Winfingerprint. Do take note, however, of some useful information:
-
Role Winfingerprint can determine, with some detail, the type of server and its operating system. This identifies primary domain controllers (PDCs), backup domain controllers (BDCs), and any domain to which the computer belongs.
-
Date/Time This helps you deduce (to some degree) the physical location of the server. The server’s local time is also useful when you’re trying to schedule remote jobs with the AT command.
-
Usernames Winfingerprint lists each user’s system ID (SID). This identifies the administrator (SID 500).
-
Sessions This lists the NetBIOS name of other systems that have connected to the target. Many times this helps narrow down a target list to BDCs, databases, or administrator systems.
-
Services A complete service list tells you what programs are installed and potentially active.
| Note | Saving a file prompts you for “Winfingerprint Output,” but that’s simply a fancy way of saying text file. |
In spite of the amount of information that Winfingerprint pulls from a target, it suffers the same drawback as many GUI tools—that is, it cannot be scripted. Although the interface allows you to specify a large target range, the results do not come in an easy-to-use format. A Perl script could parse the file based on key fields and indentation, but it would be clumsy for a large network.
Running a Development Build
Source code is available for the intrepid (or impatient) administrator who wants the latest functionality of Winfingerprint. Use Concurrent Versions System (cvs—you installed Cygwin, right?) to grab the latest snapshot (the password is left blank):
$ cvs -d:pserver:anonymous@cvs.winfingerprint.sourceforge.net :/cvsroot/winfingerprint login (Logging in to anonymous@cvs.winfingerprint.sourceforge.net) CVS password: $ cvs -z3 -d:pserver:anonymous@cvs.winfingerprint.sourceforge.net :/cvsroot/winfingerprint co winfingerprint
The resulting Winfingerprint directory contains a Visual Studio workspace. Open the Visual Studio Project (DSP) file and compile! If you have problems, make sure that the application type uses MFC Shared DLL in the General compile options.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 189