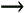Testing Switches for Vulnerabilities
| < Day Day Up > |
| Routers are not the only networking devices that are vulnerable to attack. You should also thoroughly test your switches on your LAN. Following are some of the methods for testing switches:
VLAN HoppingVLANs are a Layer 2 method of segmenting your broadcast domains. VLANs are also often used to provide additional security on networks because computers on one VLAN cannot talk to users on another VLAN without explicit access through the use of inter-VLAN routing or a multilayer switch. However, as you shall soon see, VLANs by themselves are not enough to secure your environment. Through VLAN hopping, a malicious hacker can hop from one VLAN to another, even if he is not authorized. VLAN hopping relies on the Dynamic Trunking Protocol (DTP). If you have two switches that are connected, DTP can negotiate between the two to determine if they should be an 802.1Q trunk. Negotiation is done by examining the configured state of the port. There are five states, as described in Table 10-2.
Both switches need to agree to be trunks before a trunk link is established. Table 10-3 shows the required states necessary for a trunk to be made.
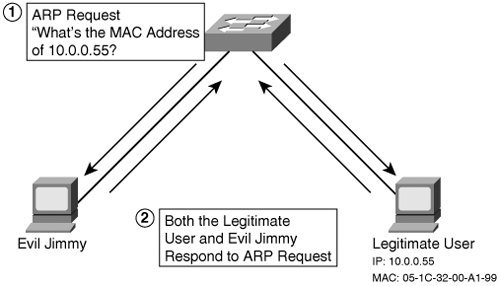
Trunk links carry traffic from all VLANs. In 802.1Q trunking, which DTP negotiates, four bytes are added to the Ethernet header to define what VLAN a frame is a member of. When a frame leaves the trunk and enters another switch, the 802.1Q shim header is removed, the frame check sequence is recalculated, and the frame is brought back to its original form. VLAN hopping exploits the use of DTP. In VLAN hopping, you spoof your computer to appear as another switch. You send a fake DTP negotiate message announcing that you would like to be a trunk. When the real switch hears your DTP message, it thinks it should turn on 802.1Q trunking. When trunking is turned on, all traffic for all VLANs is sent to your computer. Figure 10-6 illustrates this process. Figure 10-6. VLAN Hopping After a trunk is established, you either can proceed to sniff the traffic, or you can send traffic by adding 802.1Q information to your frames that designate which VLAN you want to send your attack to. Spanning Tree AttacksThe Spanning Tree Protocol (STP) prevents loops in redundant switched environments. If the network has a loop, the network can become saturated, broadcast storms can occur, MAC table inconsistencies can arise, and, ultimately, the network can crash. All switches running STP share information through the use of bridge protocol data units (BPDUs), which are sent every two seconds. When a switch sends a BPDU, it includes an identifier called a bridge ID. This bridge ID is a combination of a configurable priority number (default is 32768) and the base MAC address of the switch. Switches send and listen to these BPDUs to determine which switch has the lowest bridge ID. The switch that has the lowest bridge ID becomes the root bridge. A root bridge is like a neighborhood grocery store in a small town. Every small town needs a grocery store, and every citizen needs to determine the best way to get to the grocer. Paths that take longer than the best route are not used unless the main road is blocked. Root bridges operate in a similar way. Every other switch determines the best path back to the root bridge. This determination is based on cost, which, if not manually configured, is based on values assigned to bandwidth. Any other paths are put into blocking mode and only come out of blocking mode if they detect that doing so would not create a loop, such as if the primary path went down. A malicious hacker might take advantage of the way STP works to cause a denial-of-service (DoS) attack. By connecting a computer to more than one switch and sending crafted BPDUs with a low bridge ID, a malicious hacker can trick a switch into thinking that it is a root bridge. This can cause STP to reconverge and can subsequently cause a loop, which in turn might crash the network. MAC Table FloodingSwitches operate by recording the source MAC address as a frame enters a switch. The MAC address is associated with the port it entered so that subsequent traffic for that MAC address only goes out that port. This saves on bandwidth utilization because traffic does not need to go out all ports, but only those ports that need to receive the traffic. MAC addresses are stored in content addressable memory (CAM), which is 128 K of reserved memory to store MAC addresses for quick lookup. If a malicious hacker can flood CAM, he can cause the switch to begin flooding traffic everywhere, opening the door to man-in-the-middle (MITM) attacks or, even worse, crashing the switch in a DoS attack. dsniff (http://www.monkey.org/~dugsong/dsniff/) is a collection of Linux-based tools for penetration testing. One of the tools included in the dsniff package is macof. The macof tool attempts to flood the CAM of a switch with random MAC addresses so that frames are flooded out all ports. This facilitates sniffing in a switched environment. ARP AttacksThe Address Resolution Protocol (ARP) maps Layer 3 logical IP addresses with Layer 2 physical MAC addresses. ARP requests are sent out when a device knows the IP address but does not know the MAC address of a requested host. ARP requests are sent out as broadcasts so that all hosts receive the request. A malicious hacker can send a spoofed ARP reply to capture traffic directed toward another host. Figure 10-7 illustrates an example in which an ARP request is sent as a broadcast frame asking for the MAC address of a legitimate user. Evil Jimmy is also on the network, trying to capture traffic being sent to this legitimate user. Evil Jimmy spoofs an ARP response declaring himself as the owner of IP address 10.0.0.55 with the MAC address of 05-1C-32-00-A1-99. The legitimate user also responds with the same MAC address. Now the switch has two ports associated with this MAC address in its MAC address table, and all frames that are destined for this MAC address are sent both to the legitimate user and to Evil Jimmy. Figure 10-7. ARP Spoofing ARP spoofing is a popular tactic that is often used in session hijacking attacks. For more on session hijacking, see Chapter 6, "Understanding and Attempting Session Hijacking." VTP AttacksThe VLAN Trunking Protocol (VTP) is a management protocol that reduces the amount of configuration in a switched environment. With VTP, a switch can be a VTP Server, VTP Client, or VTP Transparent switch. VTP Transparent switches do not participate in VTP, so the discussion here focuses on Server and Client. Using VTP, you can configure all your VLAN declarations on a switch operating in VTP Server mode. Any time you make a change, whether it is the addition, modification, or removal of a VLAN, the VTP configuration revision number increments by one. When VTP Clients see that the configuration revision number is greater than what they currently have, they know to synchronize with the VTP Server. Example 10-4 shows the output of the show vtp status command, which illustrates both the configuration revision number and the VTP mode of a switch. Example 10-4. show vtp status Command OutputCat2950#show vtp status VTP Version : 2 Configuration Revision : 4 Maximum VLANs supported locally : 68 Number of existing VLANs : 6 VTP Operating Mode : Server VTP Domain Name : HackMyNetwork VTP Pruning Mode : Enabled VTP V2 Mode : Disabled VTP Traps Generation : Disabled MD5 digest : 0x3D 0x02 0xD4 0x3A 0xC4 0x46 0xA1 0x03 Configuration last modified by 10.1.1.40 at 5-4-02 22:25:A malicious hacker can use VTP to his advantage to remove all VLANs (except the default VLANs) on a network. This allows the malicious hacker to be on the same VLAN as every other user. The users might still be on separate networks, however, so the malicious hacker would need to change his IP address to be on the same network as the host he wants to attack. A malicious hacker exploits VTP to his advantage by connecting into a switch and establishing a trunk between his computer and the switch. (See the earlier "VLAN Hopping" section for more on establishing a trunk.) A malicious hacker then sends a VTP message to the switch with a higher configuration revision number than the current VTP Server but with no VLANs configured. This causes all switches to synchronize with the computer of the malicious hacker, which removes all nondefault VLANs from their VLAN database. |
| < Day Day Up > |
EAN: 2147483647
Pages: 209