Chapter 15. Denial-of-Service Attacks
| < Day Day Up > |
If you have ever had a system crash on you, you know how frustrating it is when you lose your data and are unable to work. This is the goal of a denial-of-service (DoS) attack. A DoS attack is one in which a malicious hacker renders a system unusable. He can do this through overloading a system so that it crashes, resulting in no one being able to access it, or by sending traffic with exceptional conditions in a way that the system was never prepared to handle. Malicious hackers cause DoS attacks when they are unable to access data otherwise or simply want the notoriety. DoS attacks are categorized into one of three types:
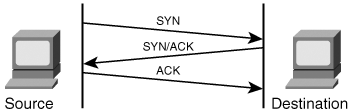
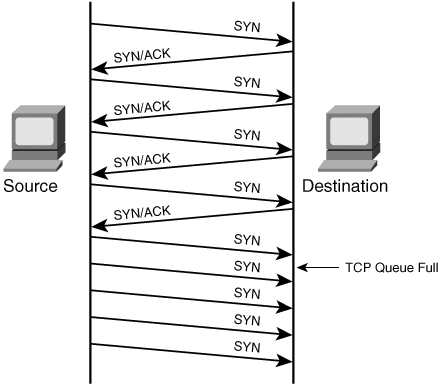
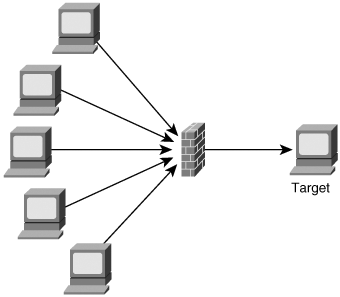
A bandwidth attack is the oldest and most common DoS attack. In this approach, the malicious hacker saturates a network with data traffic. A vulnerable system or network is unable to handle the amount of traffic sent to it and subsequently crashes or slows down, preventing legitimate access to users. A protocol attack is a trickier approach, but it is becoming quite popular. Here, the malicious attacker sends traffic in a way that the target system never expected, such as when an attacker sends a flood of SYN packets. Figure 15-1 illustrates normal TCP traffic, and Figure 15-2 shows what happens with a SYN flood protocol attack. Figure 15-1. Normal TCP Traffic Figure 15-2. SYN Flood Note SYN floods are a unique type of attack in that they are both a protocol attack and a bandwidth attack. Some attacks, such as SYN floods, combine multiple tactics. The third type of attack is a logic attack. This is the most advanced type of attack because it involves a sophisticated understanding of networking. A classic example of a logic attack is a LAND attack, where an attacker sends a forged packet with the same source and destination IP address. Many systems are unable to handle this type of confused activity and subsequently crash. Although a simple DoS attack from a single host might often be effective, it is more effective if several hosts are involved in the attack. This is called a Distributed Denial of Service (DDoS) attack. Many firewalls and intrusion detection systems (IDS) can block a single host if they detect an active DoS attack, but imagine if 10,000 hosts are involved in the attack. Few firewalls can handle this much traffic. (See Figure 15-3.) Figure 15-3. Distributed Denial of Service (DDoS) Attacks Although a penetration tester might be asked to test a host against DoS attacks, it is even less common to find a penetration tester testing using DDoS attacks. For this reason, this chapter focuses primarily on DoS attacks as they relate to penetration testing. |
| < Day Day Up > |
EAN: 2147483647
Pages: 209