Detecting Trojans and Backdoor Applications
| < Day Day Up > |
| Now that you have learned about the dangerous viruses, worms, and Trojans, it is time to learn how to detect and prevent these malware applications from infiltrating your network. Detecting Trojans and backdoors depends largely on their age and sophistication. Older traditional Trojans will most likely be detected easily based on the signatures they have, whereas new Trojan/backdoors can remain undetected for a long period of time. This section covers some examples of detecting backdoor programs. You have several tools in your arsenal to aid in detection of these malware products, including the following:
MD5 ChecksumsWhenever you acquire software from an unknown source, you should either get rid of the software or produce an MD5 checksum from the file and then compare it against that published on the vendor website. For example, when you go to http://packetstormsecurity.org and download software, you see the MD5 Check value listed with the link. When the software is downloaded, use an MD5 tool such as MD5-tool (found at http://www.bindview.com) to generate the MD5 hash of the downloaded file. Next, compare this hash value to the ones located on the official trusted vendor site to check for any discrepancy. This is the first step in detecting a compromised file. By using system integrity products such as those by Tripwire, you can monitor entire server hard drives for any type of file or folder modification. The software scans and records signatures of your drives and scans for any changes on a routine basis. Tripwire also can notify you if anything changes. You can use such a tool to inform you that a new file has just appeared on the system or even that an existing file has changed, all pointing to some unexpected difference that could be a backdoor or Trojan being installed on the system. See http://www.tripwire.com for more details. Monitoring Ports LocallyMonitoring ports can be a good way of detecting installed backdoors. The basic function of a backdoor program is to create and open one or more ports that a client (attacker) can connect to. By monitoring for any unusual ports opened on a computer, you can detect Trojan/backdoor software waiting for just such a connection. You can use several tools to monitor locally open ports, including the following:
Table 12-5 displays a small subset of some possible malicious port numbers. (For more detail, look at http://www.onctek.com/trojanports.html or http://www.simovits.com/sve/nyhetsarkiv/1999/nyheter9902.html.)
Note Consult http://www.iana.org/assignments/port-numbers, provided by IANA, to see the list of properly assigned port numbers. NetstatNetstat is an administrative command-line tool that ships standard with most Windows systems. It provides the capability to "Display protocol statistics and current TCP/IP network connections" as the Microsoft help displays. You can use this tool to detect and identify open ports on a local computer. Example 12-1 displays Netstat in action. Example 12-1. Using netstatC:> netstat -a Active Connections Proto Local Address Foreign Address State TCP WEB2:echo WEB2:0 LISTENING TCP WEB2:discard WEB2:0 LISTENING TCP WEB2:daytime WEB2:0 LISTENING TCP WEB2:qotd WEB2:0 LISTENING TCP WEB2:chargen WEB2:0 LISTENING TCP WEB2:ftp WEB2:0 LISTENING TCP WEB2:smtp WEB2:0 LISTENING TCP WEB2:http WEB2:0 LISTENING TCP WEB2:epmap WEB2:0 LISTENING TCP WEB2:microsoft-ds WEB2:0 LISTENING TCP WEB2:1025 WEB2:0 LISTENING TCP WEB2:1026 WEB2:0 LISTENING TCP WEB2:1027 WEB2:0 LISTENING TCP WEB2:2239 WEB2:0 LISTENING TCP WEB2:3372 WEB2:0 LISTENING TCP WEB2:3389 WEB2:0 LISTENING TCP WEB2:1212 WEB2:0 LISTENING TCP WEB2:7777 WEB2:0 LISTENING TCP WEB2:12345 WEB2:0 LISTENING TCP WEB2:12346 WEB2:0 LISTENING TCP WEB2:23476 WEB2:0 LISTENING TCP WEB2:23477 WEB2:0 LISTENING TCP WEB2:27374 WEB2:0 LISTENING TCP WEB2:ms-sql-s WEB2:0 LISTENING TCP WEB2:netbios-ssn WEB2:0 LISTENING TCP WEB2:ms-sql-s WEB2:0 LISTENING UDP WEB2:echo *:* UDP WEB2:discard *:* UDP WEB2:daytime *:* UDP WEB2:qotd *:* UDP WEB2:chargen *:* UDP WEB2:epmap *:* UDP WEB2:snmp *:* UDP WEB2:microsoft-ds *:* UDP WEB2:1028 *:* UDP WEB2:1029 *:* UDP WEB2:ms-sql-m *:* UDP WEB2:3456 *:* UDP WEB2:netbios-ns *:* UDP WEB2:netbios-dgm *:* UDP WEB2:isakmp *:* As you can see, several open ports are waiting for action. Notice that if Windows recognizes the port number, it displays the associated service or program name. The a switch displays all connections on active listening ports. As the output shows, you can see several typical Trojan ports open and waiting for connection: Tini, Netbus, Donald Dick, and SubSeven. (Refer to the port numbers in Table 12-5.) fportfport is a free command-line tool created by Foundstone that can assist in basic detection. fport provides the capability to list ports similar to netstat; however, it provides just a little more detail by showing which program on the hard drive is owning the port and where the program is located on the disk. Example 12-2 shows sample output from fport. Example 12-2. Using fportC:>fport.exe FPort v2.0 - TCP/IP Process to Port Mapper Copyright 2000 by Foundstone, Inc. http://www.foundstone.com Pid Process Port Proto Path 864 tcpsvcs -> 7 TCP C:\WINNT\System32\tcpsvcs.exe 864 tcpsvcs -> 9 TCP C:\WINNT\System32\tcpsvcs.exe 864 tcpsvcs -> 13 TCP C:\WINNT\System32\tcpsvcs.exe 864 tcpsvcs -> 17 TCP C:\WINNT\System32\tcpsvcs.exe 864 tcpsvcs -> 19 TCP C:\WINNT\System32\tcpsvcs.exe 948 inetinfo -> 21 TCP C:\WINNT\System32\inetsrv\inetinfo.exe 948 inetinfo -> 25 TCP C:\WINNT\System32\inetsrv\inetinfo.exe 948 inetinfo -> 80 TCP C:\WINNT\System32\inetsrv\inetinfo.exe 440 svchost -> 135 TCP C:\WINNT\system32\svchost.exe 8 System -> 139 TCP 8 System -> 445 TCP 492 msdtc -> 1025 TCP C:\WINNT\System32\msdtc.exe 828 MSTask -> 1026 TCP C:\WINNT\system32\MSTask.exe 948 inetinfo -> 1027 TCP C:\WINNT\System32\inetsrv\inetinfo.exe 728 sqlservr -> 1433 TCP C:\PROGRA~1\MICROS~3\MSSQL\binn\sqlservr.exe 948 inetinfo -> 2239 TCP C:\WINNT\System32\inetsrv\inetinfo.exe 492 msdtc -> 3372 TCP C:\WINNT\System32\msdtc.exe 916 termsrv -> 3389 TCP C:\WINNT\System32\termsrv.exe 1515 nc -> 1212 TCP C:\nc.exe 1516 tini -> 7777 TCP C:\tini.exe 1544 patch -> 12345 TCP C:\19 Netbus17\patch.exe 1544 patch -> 12346 TCP C:\19 Netbus17\patch.exe 1600 pmss -> 23476 TCP C:\WINNT\System32\pmss.exe 1600 pmss -> 23477 TCP C:\WINNT\System32\pmss.exe 1580 aepfefug -> 27374 TCP C:\WINNT\aepfefug.exe Notice that fport displays the file location of a process called patch.exe using ports 12345 and 12346 (Netbus). Then Tini.exe is on port 7777, pmss.exe is on port 23476 (Donald Dick), aefefug.exe is on port 27374 (which, according to the port listing in Table 12-5, is SubSeven), and port 1212 points to NetCat. (See Example 12-1.) fport is quite handy for discovering open ports to programs that might otherwise have gone undetected with Netstat. For more information on fport, see http://www.foundstone.com/index.htm?subnav=resources/navigation.htm&subcontent=/resources/proddesc/fport.htm. TCPViewTCPView is a great graphical tool created by Mark Russinvoch at http://www.Sysinternals.com. It is very much like a graphical Netstat tool that dynamically displays connection opening and closing. The tool also allows you to reset the connection and even close the process that is listening on the port. Figure 12-67 displays a screen shot of TCPView. Figure 12-67. TCPView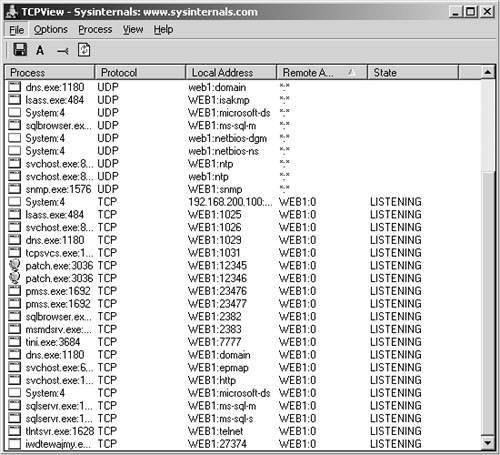 For more information and details about TCPView, see http://www.sysinternals.com/ntw2k/source/tcpview.shtml. By monitoring ports locally, you can easily find processes that you might not have expected to be running. These can in turn lead to the malware that gives hackers easy access to your system. Monitoring Ports RemotelyMonitoring local ports is quite important for finding backdoors and Trojans running on a computer. However, by monitoring ports remotely, you can greatly increase the efficiency of your time. Think of scanning an entire network range just looking for backdoor/Trojan horse ports. By using tools such as NMap, you can quite easily schedule network port scanning on a daily basis and output the results to a file that you can parse or grep later for future analysis. (See http://www.openxtra.co.uk/support/howto/nmap-scanning-at-intervals.php for directions on how to configure NMap to run at intervals.) Example 12-3 displays NMap output from a remote computer that contains Tini, Netbus, Donald Dick, and SubSeven Trojan/backdoors. Example 12-3. Using NMapc:>nmap -sS -PT -PI -p 1-30000 -O -T 3 192.168.200.100 Starting nmap V. 3.00 ( www.insecure.org/nmap ) Interesting ports on WEB1 (192.168.200.100): (The 29980 ports scanned but not shown below are in state: closed) Port State Service 23/tcp open telnet 53/tcp open domain 80/tcp open http 135/tcp open loc-srv 139/tcp open netbios-ssn 445/tcp open microsoft-ds 1025/tcp open NFS-or-IIS 1026/tcp open LSA-or-nterm 1029/tcp open ms-lsa 1031/tcp open iad2 1433/tcp open ms-sql-s 1434/tcp open ms-sql-m 2382/tcp open unknown 2383/tcp open unknown 1212/tcp open unknown 7777/tcp open unknown 12345/tcp open NetBus 12346/tcp open NetBus 23476/tcp open unknown 23477/tcp open unknown 27374/tcp open subseven Remote operating system guess: Microsoft Windows.NET Enterprise Server (build 3604- 3615 beta) Nmap run completed -- 1 IP address (1 host up) scanned in 2 seconds Although Nessus is typically known as a full-featured vulnerability scanner, it is also useful in the detection of Trojan horse ports. Also look to this tool when sweeping a network for installed malware. For more details on Nessus, see http://www.nessus.org/. Anti-virus and Trojan Scanners SoftwareIn the early days, anti-virus programs did not detect Trojans as well as the viruses that they were designed to scan for. Trojan/backdoor programs could be located anywhere and executed several ways, which made detection a little more difficult than the standard virus, which always behaved in a standard manner. However, now anti-virus programs are much improved and generally perform well at finding and removing the standard Trojans, backdoors, and viruses. Even spyware scanners such as http://www.aluria.com detect several Trojans, including Donald Dick and Tini. Table 12-6 displays some generally useful AV programs.
Using dedicated Trojan detection tools combined with a standard AV program give you a pretty thorough detection and protection program. Some of the scanners listed in Table 12-6 have been around for a long time. For example, TDS has been around since 1997 and offers a wealth of features in the hands of an expert. Table 12-6 displays a list of Trojan horse scanners. You should review and compare these tools in your own environment to find which one works best for you. Intrusion Detection SystemsIDSs can be used with a degree of success when it comes to detecting backdoor connections. Older backdoors, such as Netbus and SubSeven, can be detected quite easily when the client and server use the default port numbers and communication is in progress. Unfortunately, after you move from those default numbers, the detection success rate goes down rapidly. Backdoors such as NetCat and Beast, which can use any port, are virtually undetectable if you are not manually searching for anomalies in traffic patterns. For sample tests, NetCat, Tini, Netbus, Donald Dick, SubSeven, and Beast were installed on a Windows 2003 Server and used the client tools to control the server and create some traffic. The results showed that only Netbus and SubSeven communications were detected, leaving all the others to run freely, undetected. Figure 12-68 displays the alarms detected on the Cisco 4200 Series Sensor. Figure 12-68. Trojans Detected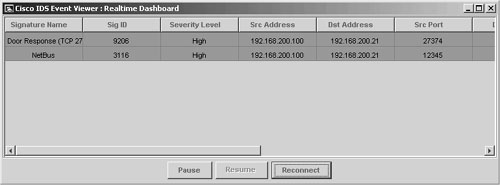 Because so many of the Trojans were not detected, it is important not to rely on IDS alone to detect Trojans and backdoors in your environment. |
| < Day Day Up > |
EAN: 2147483647
Pages: 209
- Step 1.1 Install OpenSSH to Replace the Remote Access Protocols with Encrypted Versions
- Step 3.1 Use PuTTY as a Graphical Replacement for telnet and rlogin
- Step 3.4 Use PuTTYs Tools to Transfer Files from the Windows Command Line
- Step 4.1 Authentication with Public Keys
- Step 4.4 How to Generate a Key Using PuTTY