| Note Evil twin attack: A homemade wireless AP that masquerades as a legitimate one to gather personal or corporate information without the knowledge of the end user.
The twin of Evil Jimmy, Evil Johnny, has been spending a little time war driving, and even he is surprised to discover that around 50 percent of the wireless networks he has discovered using NetStumbler are unsecured. More interestingly are the number of wireless hotspots appearing. There seems to be at least one new one every time he checks, and this has given him a great idea. Step 1. | Johnny arrives at Stacey's Bagels Inc., which has recently announced its wireless hotspot launch.
| Step 2. | He turns on his laptop and enables his wireless card. Sure enough, he sees BagelNet appear in the list of available wireless networks, as illustrated in Figure 11-8. He connects to BagelNet, and when he opens a new browser window, he is presented with a login screen showing payment options for the company's wireless pay-as-you-surf service. Johnny takes a quick screen shot of this page and heads home to brush up on his HTML.
Figure 11-8. Windows Available Wireless Networks 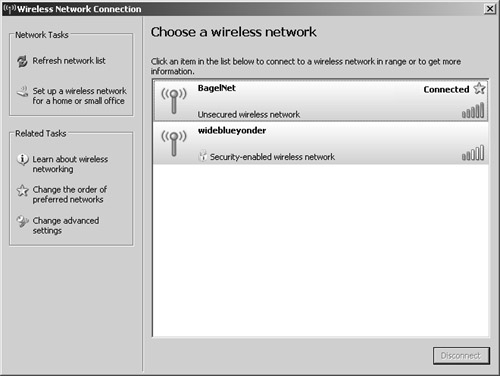
| Step 3. | Johnny needs to configure his laptop so that he can successfully impersonate the AP at Stacey's. He is using Windows, so he needs several tools
- a. First, he installs SoftAP from PCTEL (http://www.pctel.com/softap.php), which allows his laptop to function as an AP. (See Figure 11-9.)
Figure 11-9. SoftAP Options Configuration 
- b. Next, Evil Johnny installs Airsnarf (http://airsnarf.shmoo.com/) on his laptop and begins customizing a web page to replace the default index.html, which Airsnarf provides by default. He has the copy of the login page from BagelNet as a template, but he is not too worried about getting an exact match. Airsnarf is a utility tool that enables a rogue AP to be set up. Users are fooled into believing they are connected to the genuine AP because Airsnarf can mimic the look and feel of the real thing.
- c. He configures the SSID of his new AP to be BagelNet.
- d. Johnny sets up his laptop to be a primary DNS server using TreeWalk (http://ntcanuck.com/DL-kN/TreeWalk.zip). This tool provides the functionality of a DNS server and ensures that he can control the website that any users will see if they associate with his AP.
| Step 4. | The following day, Johnny once again visits Stacey's Bagels. He finds a quiet corner, turns on his laptop-turned-AP, and sits back with his coffee and a cinnamon bagel to wait.
| Step 5. | Before too long, a fellow bagel eater opens up his laptop to connect to the Internet. It is really a matter of luck whether the wireless device of this customer will associate with the real AP or Johnny's, but Johnny keeps his fingers crossed anyway. Sure enough, SoftAP helpfully pops up a message to let him know that a user has connected to his AP.
| Step 6. | The user is presented with Johnny's fake login screen and, eager to get onto the Internet and check his e-mail, he fills out his credit card details and clicks Submit. The credit card details the user just entered are written to a log file on Johnny's laptop. Johnny then quickly downs his AP, because he was never planning to serve up Internet access in the first place.
|
If Johnny had wanted to be a little more clever, he could have set up an Internet connection for his unsuspecting users, with all of their traffic directed through his laptop/AP. However, collecting some credit card details will be enough for now. After all, there is no shortage of opportunities. |

