Detecting Wireless Attacks
| < Day Day Up > |
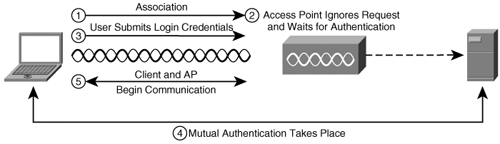
| The convenience of WLANs is also often their downfall. With the only "physical" network layer being the air itself, the risks are obvious. Unprotected WLANsA poorly secured wireless network is easy picking for even the least experienced hacker. If no authentication is required, any user in the vicinity of that AP can detect and associate with its WLAN. You can detect this type of attack only through monitoring network traffic, and even then, it is effective only if you can accurately identify legitimate connections to your network. DoS AttacksAn attacker can accomplish a denial-of-service (DoS) attack against a wireless device in various ways, including a deauthentication attack, as illustrated in Figure 11-3. Figure 11-3. Deauthentication Attack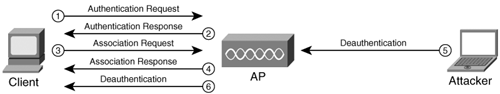 In this attack, the attacker sends a deauthenticate frame to the AP, causing the client to deauthenticate from the AP and consequently lose its connection. Similar types of attack include the authentication and association flood attacks which, as their names suggest, flood the AP with requests and prevent genuine requests from being serviced. Attacks of this type exhibit characteristic signatures and can be detected easily using a wireless IDS tool such as AirDefense (http://www.airdefense.net) or Airespace (http://www.airespace.com/index.php). Rogue Access PointsDuring the authentication process, mutual authentication between the client and the AP is not required even if shared-key authentication is implemented. The result is that although the AP authenticates the client, the client has no way of authenticating the AP. A rogue AP might be one an ignorant employee brings from home and associates with your wireless infrastructure. Or it might be one an attacker places on your network and masquerades as a genuine AP. In the first case, the rogue AP is likely a hole in your firewall security, which means it is wide open to attack. More worryingly in the second case, clients who are already authenticated on your genuine network might inadvertently associate with the rogue AP, giving an attacker access to the unsuspecting client. Tools such as AirMagnet (http://www.airmagnet.com) and AiroPeek (http://www.wildpackets.com/products/airopeek_nx) are able to detect and block such rogue APs. Snort also produces Snort-Wireless, a freeware, configurable IDS tool available on a Linux platform from http://snort-wireless.org/. MAC Address SpoofingIn smaller networks where cost is a factor and high-end security measures are not feasible, MAC address filtering can provide a measure of protection. However, MAC spoofing is a straightforward process even with manufacturers of wireless cards providing built-in functionality to alter the hardware MAC address. Detecting an attack using a spoofed MAC address is not a simple process, but you can identify such attacks by their signature. When you examine normal traffic between a host and a client, you see an incrementing sequence number in each packet. When an attacker spoofs a legitimate MAC address, his packets show a change in this sequence number. For more information, see http://home.jwu.edu/jwright/papers/wlan-mac-spoof.pdf. Unallocated MAC AddressesAn attacker can evade detection on the network by manually changing a MAC address or using programs such as Wellenreiter, which can generate random MAC addresses. However, the IEEE must allocate hardware manufacturers a unique 3-byte identifier for use as a MAC address prefix for all of their products. You can compare spoofed MAC addresses against this list; any detected anomaly can signify an attack. Preventing Wireless AttacksYou can take numerous simple measures to reduce the risk of attack. Although this chapter emphasized the security flaws in using WEP as a method of securing your network, if a casual attacker is faced with the scenario illustrated in Figure 11-4, it is clear which AP he will target first. Figure 11-4. NetStumbler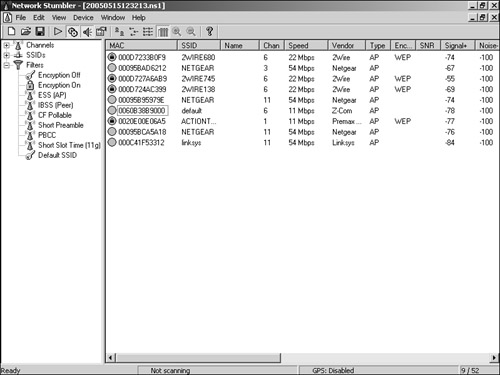 Provided your network is not a specific target, these simple steps can make your AP a less attractive option:
If your requirement is simply to analyze and protect your home network, you can use a tool such as AirDefense Personal, which reveals potential risks with the configuration of your wireless network. This tool also serves as a monitor, detecting potential security risks and firing alerts accordingly. Figure 11-5 shows the summary page detailing the current security and alert status. Figure 11-5. AirDefense Personal System Summary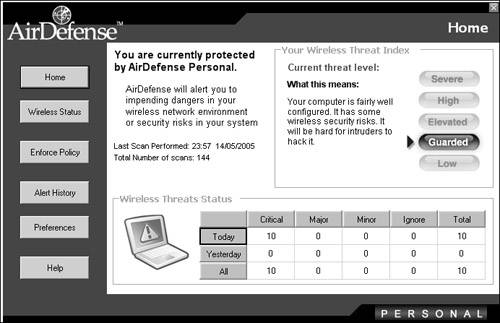 Another feature of the tool is the ability to enable only the features of wireless connectivity that are specifically required (see Figure 11-6). This can prevent accidental vulnerabilities from being exposed. Figure 11-6. AirDefense Personal Policies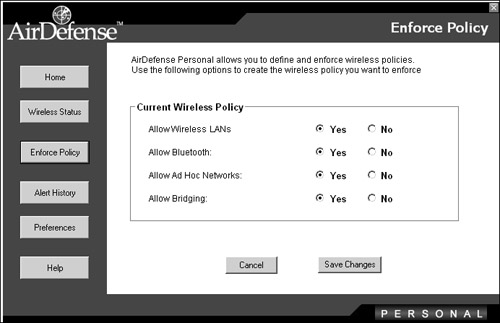 Preventing Man-in-the-Middle AttacksWireless networking is especially vulnerable to MITM attacks because intercepting wireless network traffic is so straightforward. Nevertheless, you can reduce the vulnerability significantly by making careful configuration decisions, such as these:
WPA uses Temporal Key Integrity Protocol (TKIP), which provides a much stronger encryption algorithm than WEP. WPA has two main implementations:
Note WPA and WPA2 use variations of the Extensible Authentication Protocol (EAP) mechanism to provide authentication and optionally encryption methods. You can find various implementations with each offering differing levels of security and excellent definitions at http://en.wikipedia.org/wiki/Extensible_Authentication_Protocol. Establishing and Enforcing Standards for Wireless NetworkingAs with all security issues in an organization, implementing wireless networking policies and standards as part of your overall security management can go a long way toward maintaining the security of your wireless network. Regulate the use of wireless equipment across your network. For example, if you deploy only Cisco wireless hardware, the presence of a NETGEAR AP on your network immediately alerts you to a security breach. Ensure that you document and standardize AP configuration. Also, carefully control deployment. In this way, you can detect rogue APs more easily if they do not meet the standard configuration. Always assume that someone can breach your APs, and treat their integrity with caution. Implement a process to regularly evaluate the security of your wireless network. |
| < Day Day Up > |
EAN: 2147483647
Pages: 209