Securing the Application Server Control Utility
| | ||
| | ||
| | ||
When running the ASC on production systems, you should usually shut it down unless you need it. If you need to restart a component or deploy an application, you can use the opmnctl and dcmctl tools. When the ASC is started, it should be accessible only behind your firewall, if possible. Changing the port is a good idea and of course the ias_admin password should be changed regularly. You should also configure the ASC for use with HTTPS .
In the following section we'll show you how to change the default port, password, and enable HTTPS for the ASC.
Changing Default ASC Port
To change the ASC port, follow these steps:
-
Stop the ASC process, as shown here:
$ emctl stop iasconsole
-
Find a free port. In this case you'll attempt to use port 1820, as follows :
$ netstat -a grep 1820 $ grep 1820 /etc/services
Based on the previous results, it's safe to assume that 1820 is available.
-
Go to the sysman configuration directory, as shown here:
$ cd $ORACLE_HOME/sysman/j2ee/config
-
Edit the website configuration file emd-web-site.xml and change the port value to 1820, as follows:
$ cp emd-web-site.xml emd-web-site.xml.orig $ vi emd-web-site.xml <web-site host="[ALL]" port="1820" display-name="Oracle Enterprise Manager iAS Console Website" secure="false">
-
Go to the sysman daemon directory, as shown here:
$ cd $ORACLE_HOME/sysman/emd
-
Edit the targets.xml file for the new port 1820, as follows:
$ cp targets.xml targets.xml.orig $ vi targets.xml <Property NAME="StandaloneConsoleURL" VALUE="http://mike.wessler.name:1820/emd/console"/>
-
The $ORACLE_HOME/install/portlist.ini file will not automatically be updated with new information so you would have to change it there manually.
-
Restart the ASC and access the URL at http://mike.wessler.name:1820 , as follows:
$ emctl start iasconsole
The ASC is now accessible on port 1820.
Changing the ASC ias_admin Password
The ias_admin password can be changed either with the emctl utility or from within the ASC utility.
emctl Command Line
Here you can see how to change the password from the command line.
-
Use the emctl set password command, as shown here. The drawback is that the passwords are temporarily exposed in plain text on the screen, as shown here:
$ emctl set password ora123 ora567
-
It's necessary to restart the ASC in order for the new password to take effect, as follows:
$ emctl stop iasconsole $ emctl start iasconsole
The ias_admin password is now updated.
The ASC Password Change Utility
Here you can see how to change the password from the ASC utility.
-
Log in to the ASC instance home page. Click the Preferences link at the bottom of the screen.
-
A Change Password page appears, as shown in Figure 20-3.
-
Enter the old and new passwords and click OK.
There's no need to restart the ASC utility because the change has taken effect after the Confirmation page indicating that the password has been updated.
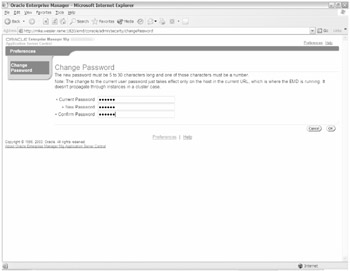
Figure 20-3: Password Change page
The ias_admin password is now updated.
Encrypting the ASC Traffic with SSL
By default HTTP traffic is unencrypted. This means if you "sniff" the network with a network sniffer you can see in plain text the data as it's passed back and forth from the client to server. If you also know what port to sniff on, such as the defaults starting with 1810, you can conceivably capture the password for the ias_admin account. At that point a hacker can access your ASC utility with full ias_admin privileges.
Changing default ports, changing passwords frequently, and doing as much as possible with command-line utilities helps to guard against these types of problems. However, one of the best ways to protect against this is to encrypt your network traffic with SSL. That way, even if your network is being watched, your passwords and data should be safe and unreadable to others.
To turn on HTTPS for the ASC, follow these steps:
-
Stop the ASC if it's currently running.
-
Run the emctl command to turn on SSL for the ASC. You only need to do this once for the initial setup, as follows:
$ emctl secure em TZ set to US/East-Indiana Oracle Enterprise Manager 10g Application Server Control 9.0.4.0.0 Copyright (c) 2002, 2003 Oracle Corporation. All rights reserved. Generating Standalone Console Java Keystore... Done. Fetching Standalone Console Root Certificate... Done. Generating Standalone Console Agent Key... Done. Storing Standalone Console Agent Key... Done. Generating Oracle Wallet for the Standalone Console Agent... Done. Configuring Agent for HTTPS... Done. EMD_URL set in /u01/app/oracle/product/9.0.4mt1/OraHome1/sysman/config /emd.properties Configuring the website ... Done. Updating targets.xml ... Done. $
-
Restart the ASC as normal, as shown here:
$ emctl start iasconsole
-
Access the same ASC URL and port as normal, except you must use HTTPS instead of HTTP. If you attempt to use HTTP again, the attempt will fail. In this example, the URL is https://mike.wessler.name:1820 .
When you first enter the URL you'll likely receive a warning message saying that the certificate used is valid, but isn't trusted. That's because the SSL certificate was dynamically generated by the Oracle tool for the ASC to run. Because the new certificate wasn't issued by a trusted default Certificate Authority (CA) such as VeriSign, your browser will display this warning message. The concepts behind this are covered in greater detail in the next section.
The initial message you'll see indicating the certificate isn't trusted by default is shown in Figure 20-4.
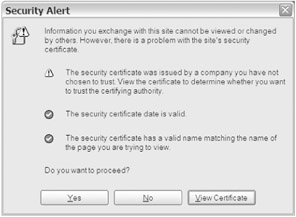
Figure 20-4: Security alert warning
To get more information and options with the certificate, click View Certificate, as shown in Figure 20-5.
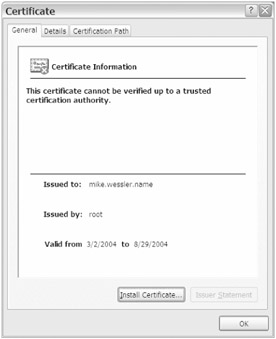
Figure 20-5: Certificate information
Here you can see that the certificate was created and issued by root to the server mike.wessler.name . This creation occurred when you ran the emctl secure em command in step 2 of the previous list. When you log in to https://mike.wessler.name:1820 the public key is downloaded and a connection with the server's private key is established. However, because the browser doesn't by default have this root issuer listed as a trusted certificate issuer, it will display this warning message.
This is only a warning notification page and to be able to access the ASC you must select Yes to proceed.
At this point you can use the ASC website because you've chosen to accept the certificate. However, this certificate isn't the normal type of certificate that you would use for a commercial site, and it will expire in six months. The expiration date is shown at the bottom of the certificate information page shown in Figure 20-5. At the end of the six months, you'll have to rerun the emctl secure em command to regenerate the certificate.
After clicking Yes to accept the certificate (shown in Figure 20-6), the ASC page is now running in encrypted SSL mode using the HTTPS protocol.
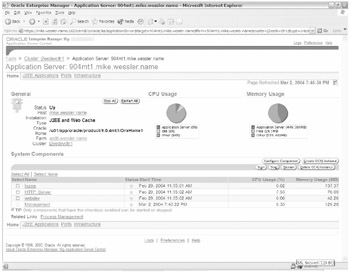
Figure 20-6: ASC running in HTTPS mode
You can tell you're running in HTTPS mode most obviously from the https in the URL. However, at the bottom of the browser on the right you can see a lock with the message label 128-bit encryption. This confirms that SSL is set up and running.
In this section we showed you how to improve the security of the ASC utility. You also glimpsed briefly at HTTPS, SSL, and certificates, which we'll explain more in the next section.
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 150