3.10 Effects of Proxies
| only for RuBoard - do not distribute or recompile |
3.10 Effects of Proxies
In Chapter 1, I talked briefly about how a proxy sits in between clients and servers. Without a proxy, clients normally connect directly to origin servers. With a proxy, however, clients connect only to the proxy. If needed, the proxy connects to origin servers for cache misses. This characteristic of proxies has two important implications for cache managers: security (of both web servers and caches) and bandwidth.
Because the server only knows about its TCP connection from the proxy, the client remains hidden. This can cause problems for origin servers that use address-based access controls. When a client's request goes through a proxy, the server gets the proxy's address, not the client's. If the server is configured to allow connections from the client's address and deny all others, requests forwarded through the proxy are denied .
As a caching proxy administrator, you must pay close attention to access controls on your web servers and on your proxy. Web servers that authorize connections from your proxy are effectively authorizing connections from anyone who can connect to your proxy. A proxy that accepts requests from any client is open to all sorts of mischief. An open -access proxy creates a back door that enables tricks similar to IP source routing and email relaying. An outsider may be able to route traffic through your proxy. Such abuse can be as harmless as consuming some of your bandwidth or as serious as credit card fraud or threatening the President.
Pay especially close attention to how your caching proxy handles the CONNECT method. This method exists so user agents can tunnel SSL/TLS and other traffic through a firewall. The client specifies a hostname and port number that the proxy should connect to. Once the tunnel is established, it's as though the client has a direct connection to the origin server. The proxy is usually configured to allow connections only to specific ports ( https and snews ). If the proxy allows connections to the smtp ports of remote servers, for example, then mischievous users can use your proxy as a mail relay, spamming others and leaving you to blame.
Figure 3-1. How to get some free bandwidth
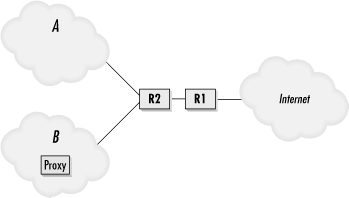
Proxies have the power to significantly affect a company's bandwidth. Consider the diagram in Figure 3-1. Two companies, A and B , receive Internet service from the same ISP. This ISP has two routers, R1 and R2 . R1 exists primarily to collect flow statistics and generate monthly bills, based on a customer's usage.
Company B has a proxy cache on its network, and the administrator failed to configure the access controls correctly. Hosts inside company A 's network are allowed to use the proxy. For the cache traffic passing through R1 , the destination IP address is B 's proxy cache. Thus, the traffic gets charged to B . Router R1 has no idea the traffic is eventually sent to hosts in company A . Since the administrators in company B are obviously careless, it's likely they'll never notice the additional traffic flowing through their network.
| only for RuBoard - do not distribute or recompile |