| Each protocol of the TCP/IP protocol suite handles certain tasks within the TCP/IP protocol stack. Figure 13-1 gives an overview of the TCP/IP protocol stack and its protocols. Figure 13-1. The protocols of the TCP/IP protocol stack. 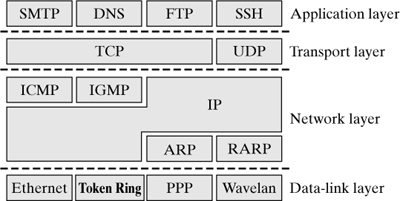
On the data-link layer in the Internet model, you find network adapters and their drivers. They allow you to exchange data packets having a specific maximum length within the connected LAN (Ethernet, token ring,...) or within a WAN (PPP over ISDN, ATM). The previous chapters introduced some protocols that also belong to the data-link layer (SLIP, PPP, ATM, Bluetooth, etc.). All adapters and protocols on this layer have the common property that they represent only one communication link between two IP routers (i.e., they don't support Internet routing). The Address Resolution Protocol (ARP) also resides on the data-link layer. Notice that there are contradictory opinions in the literature. ARP is used to map globally valid IP addresses to locally valid MAC addresses. ARP is actually not limited to IP addresses or specific physical addresses; it was designed for general use. ARP uses the broadcast capability of local area networks to find addresses. Chapter 15 describes this protocol in detail. The Internet Protocol (IP) forms the core of the entire architecture, because it allows all IP-enabled computers in the interconnected networks to communicate. Each computer in the Internet has to support the Internet Protocol. IP offers unreliable transport of data packets. IP uses information from routing protocols (OSPF, BGP, etc.) to forward packets to their receivers. The Internet Control Message Protocol (ICMP) has to be present in each IP-enabled computer; it handles the transport of error messages of the Internet Protocol. For example, ICMP sends a message back to the sender of a packet if the packet cannot be forwarded because routing information is missing or faulty. Section 14.4 deals with ICMP and its implementation in Linux. The Internet Group Management Protocol (IGMP) is responsible for managing multicast groups in local area networks. Multicast provides for efficient sending of data to a specific group of computers. IGMP allows the computers of a LAN to inform its router that they want to receive data for a certain group in the future. Chapter 17 discusses multicast in the Internet. The Transmission Control Protocol (TCP) is a reliable, connection-oriented and byte-stream-oriented transport-layer protocol. TCP is primarily responsible for providing a secured data transport between two applications over the unreliable service of the IP protocol. TCP is the most frequently used transport protocol in the Internet. It has a large functionality, and so its implementation is extensive. Chapter 24 discusses the TCP. The User Datagram Protocol (UDP) is a very simple transport protocol, providing connectionless and unreliable transport of data packets between applications in the Internet. In this context, unreliable does not mean that the data could arrive corrupted at the destination computer. It means that UDP does not offer any protocol mechanisms to guarantee that the data will arrive at the destination at all. When data arrives at the destination computer, than it can only be checked for correctness. As compared with TCP, UDP has the benefit that it has very little functionality and so can easily be extended. Many applications that normally transmit only small amounts of data (e.g., client/server applications) use UDP as their preferred transport protocol. Establishing a connection and reliable data transmission would be more costly than the retransmission of faulty or missing data. The application layer accommodates various standardized application protocols, which form the basis of a large number of applications: The HyperText Transfer Protocol (HTTP) is currently the protocol most frequently used in the Internet application layer. It allows you to exchange data in the World Wide Web say, by loading Web sites into your Web browser (Netscape, Mozilla, Lynx, etc.). The unprecedented success of the World Wide Web has led to the enormous proliferation of the Internet and its revolutionary growth. TELNET is the protocol for virtual terminals. It is used to access a computer connected to the network in the form of a terminal session. Its unsecured transmission of passwords and data has caused TELNET to be increasingly replaced by the SSH (Secure Socket Shell) protocol. The File Transfer Protocol (FTP) can be used to transport files from a local computer to another computer and vice versa. Like TELNET, its most important drawback is that passwords are transmitted in cleartext. FTP has increasingly been replaced by Secure Copy (SCP). The Simple Mail Transfer Protocol (SMTP) is the protocol used to exchange electronic mail (e-mail) in the Internet. The Domain Name Service (DNS) translates DNS names, which are most commonly used and are easy for humans to remember (e.g., www.linux-netzwerkarchitektur.de[1]) into IP addresses. It is used mainly to convert computer names and mail-server locations into IP addresses. The Network File System (NFS) is used to allow several computers to access the same file system. The NFS service represents an extension of local file systems beyond network boundaries.
Such protocols of the application layer are not discussed in this book, because they are not part of the Linux kernel. Simple application programming is normally sufficient to emulate them. For example, there are many of HTTP protocol implementations in different WWW browsers and WWW servers. Chapter 27 explains how applications with network functionality can be programmed.
The following chapters describe each protocol of the TCP/IP protocol stack and how they are implemented in Linux. These chapters also discuss various extensions, which are related to the Internet Protocol suite, but normally not mentioned together with it. This includes mainly concepts and protocols for computer security (firewalls, NAT) and the support of specific guaranteed services within the Internet Protocol (Quality of Service (QoS) with TC or KIDS). |