Section 6.1.Dress in Layers
|
6.1. Dress in LayersWhen it's cold you dress in layers, and security works the same way (Figure 6-1). The outer layer is a firewall, preventing attacks from the Internet. Next, virus detection software scans permitted attachments and other files from bringing in malicious code. Then, operating system security defines users and their permissions. Finally, Excel provides its own security layer. Data most at risk is that which is shared outside of these layers, such as a workbook posted on a public server. In that case, Excel becomes the primary security layer. Of course, not all data needs the same level (or type) of protection. Therefore, Excel itself provides layers through the following security approaches: Figure 6-1. Use layers to keep out threats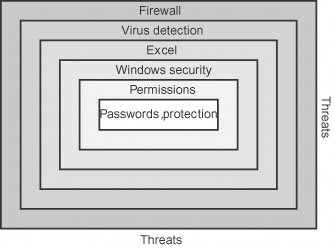
These security approaches can be combined to provide a high level of assurance while still allowing files to be shared, macros to be run, and (ultimately) work to be done. The rest of this chapter discusses each of these approaches, along with Windows file security, then provides a list of common security tasks and describes how you complete those tasks by combining Excel security features. |
|
EAN: 2147483647
Pages: 133