3.6 Apache Log Files
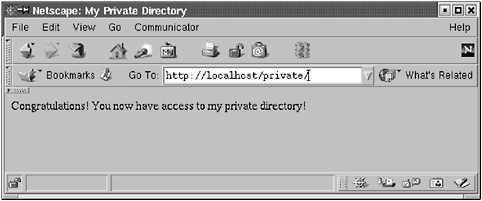
| Apache keeps detailed logs of accesses to your web site, errors, and more. The Apache logs are located at /var/log/httpd/access_log and /var/log/httpd/error_log . These locations are configurable in httpd.conf . It's a good idea to have a log monitor program running, such as swatch or logwatch , to keep an eye on these files for security violations and problems (see www.logwatch.org). It's also a good idea to rotate them regularly via logrotate , because they'll get big otherwise . Of course, the most important use of the logs is to look at them when there is a problem to figure out what went wrong. An access_log entry might look like this: 192.168.1.12 - - [21/May/2001:14:10:05 -0600] "GET / HTTP/1.0" 200 43 "http://www.onsight.com/" "Mozilla/4.77 [en] (X11; U; Linux 2.4.2-2 i686; Nav)" Earlier in the chapter, we discussed how to select the information that is displayed in the Apache log file (we suggested the combined output). This log selection displays the previous information. Most of these entries should be clear: the IP address of the requestor , the date and time of the request, the browser used (though clever programs such as Opera let you tell the server anything you want, and you can define this to be anything you want if you change the headers and recompile Mozilla), the language ( [en] ), and some system details of the requestor. "GET / HTTP/1.0" 200 43 means an HTTP request, no errors ( 200 ), and 43 bytes were sent. (A list of errors can be found at www.ietf.org/rfc/rfc2616.txt.) 3.6.1 Access Control with .htaccessEarlier we discussed how to enable .htaccess files in your configuration. Now we'll show you how they're used. This is useful for restricting access to certain portions of your web site, either by allowing access only from specific IP addresses or domains or by password control. In httpd.conf , look for the line Directory /var/www/html (or whatever the default directory is). There you will see: AllowOverride None Change this to: AllowOverride AuthConfig This change tells the server to change its behavior from allowing anyone to connect to allowing only those clients whose attributes match those in an authorization file to connect to the files in that directory. Make sure the .htaccess filename definition is uncommented. You could change the name of the .htaccess file via this directive: AccessFileName .htaccess We mentioned this directive before, but it deserves mentioning again. Since we use the file .htaccess to control access, make sure the htaccess directive is uncommented (see Section 3.4.5) ”it denies serving any file whose name begins with .ht , meaning that clients can't look at your .htaccess file to figure out what that file is and who you allow to look at this directory. Now restart the server: # /etc/init.d/httpd graceful To see how .htaccess works, create a directory for some private information: $ cd /var/www/html $ mkdir private $ chmod a+rx private $ cd private And create a simple index.html file (remember to make it readable with chmod a+r index.html ): <html> <head> <title> My Private Directory </title> </head> <body> Congratulations! You now have access to my private directory! </body> </html> Now, create a password file. It's convenient and tempting to put it in the same directory and call it something like .htpasswd . Don't. Place it outside the document tree. If someone were to get access to this directory because of a server misconfiguration (hey, it happens ”the configuration file is big and mistakes do happen), you wouldn't want them to have access to your password files (even though the passwords are encrypted), especially because many people tend to use the same passwords for many different purposes. This is a very bad idea, so not only do you as a sysadmin and webmaster want to advocate good habits, you want to defend against bad ones. $ mkdir /var/www/misc $ chmod a+rx /var/www/misc $ cd /var/www/misc Create a password file: $ htpasswd -bc private.passwords neo anderson Adding password for user neo The option -b means we are supplying the password ( anderson ) on the command line, and -c means create the file. To add new users, leave off the -c . [13]
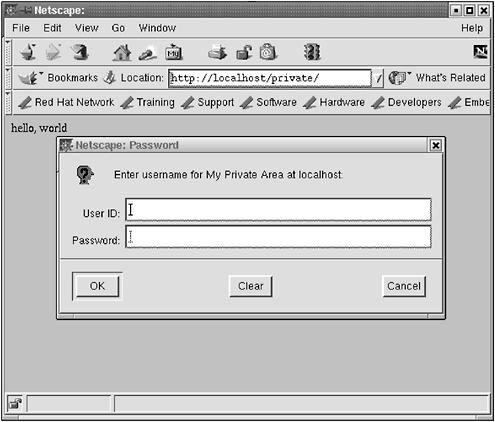
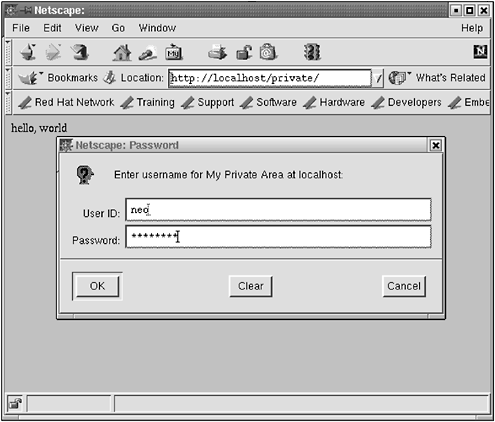
$ htpasswd -b private.passwords morpheus sleeps Create the .htaccess file in the /private directory. This is not the password file but the file that points to the passwords. $ cd /var/www/html/private $ vi .htaccess The file .htaccess has this in it: AuthName "My Private Area" AuthType Basic AuthUserFile /var/www/misc/private.passwords AuthGroupFile /dev/null require valid-user So when you point your browser to http://localhost/private/ or www.opensourcewebbook.com/private, you should see Figure 3.5. To get in, enter the username/password neo / anderson , as shown in Figure 3.6, and you should see Figure 3.7. Figure 3.5. Login Figure 3.6. Username, password Figure 3.7. Access granted There's no encryption when you use passwords like this ”the passwords go over the network in the clear (to be exact, the passwords are encoded, then sent in the clear, but the encoded passwords are easily decoded if a cracker knows how to decode them, and they do know how to decode them), which as you might imagine, is not an optimal configuration. Be aware that doing so makes you vulnerable to password sniffing. If you do use this, don't use the same password as your Linux login, and be aware of your vulnerabilities. You can monitor access to these directories with your log monitoring program if you desire . You can use HTTPS to have secure communications for this kind of thing, but that is (for now) beyond our scope. You can also do simple IP verification by putting the following in your .htaccess file: Order deny,allow Deny from all Allow from 192.168.1.100 Allow from 10.0.1.0 Allow from 127.0.0.1 In the preceding example, the first two IP addresses are special local networks. Although most IP addresses are assigned by ICANN and distributed by DNS, the 192.168 and 10.0 IP subnets are not unique and are used for internal networks behind a firewall. The third IP address, 127.0.0.1 , is a special IP address, that of localhost . Everyone's computer assigns this IP to itself, in addition to any external IP address. If you point your web browser to localhost or 127.0.0.1 , it will serve up the default page of the local Apache host. Your localhost is not the same as the fellow in the next cubicle , though. You can combine passwords and IP verification for additional security. |
EAN: 2147483647
Pages: 136