4.3 User Management Files
4.3 User Management Files
The user system in Unix allows different people to log in to the same machine without interfering with one another. At the lowest level, users are nothing more than numbers ( user IDs ), but login names help to avert confusion and boredom.
The plain-text file /etc/passwd maps login names to user IDs, and it looks something like this:
root:x:0:0:Super-user:/root:/bin/sh daemon:*:1:1:daemon:/usr/sbin:/bin/sh bin:*:2:2:bin:/bin:/bin/sh sys:*:3:3:sys:/dev:/bin/sh nobody:*:65534:65534:nobody:/home:/bin/false juser:x:3119:1000:J. Random User:/home/juser:/bin/bash beazley:x:143:1000:David Beazley:/home/beazley:/bin/bash
The format is straightforward. Each line represents one user, with seven fields separated by colons:
-
The user (login) name .
-
The user's encrypted password. On most Linux systems, the password is not actually stored in the passwd file, but in the shadow file. shadow is similar to passwd , but normal users do not have read permission on shadow . The second field in passwd or shadow is the encrypted password, and it looks like a bunch of garbage, such as d1CVEWiB/oppc (in Unix, passwords are never stored in clear text). The rest of the fields in shadow deal with matters such as password expiration dates.
An x in the second field in the passwd file indicates that the encrypted password is stored in shadow . An * indicates that the user cannot log in, and if the field is blank (that is, appears as :: ), no password is required to log in. Watch out for blank passwords. You should never have a user without a password.
-
The user ID (UID), the user's representation to the kernel. It should be unique. You can have two entries with the same user ID, but it will confuse you and some of your software.
-
The group ID (GID). It should be one of the numbered entries in the /etc/group file. Groups determine file permissions and little else. This group is also called the user's primary group .
-
The user's real name (often called the GECOS field). Sometimes there are commas in this field, denoting room and telephone numbers.
-
The user's home directory.
-
The user's shell (the program that runs when the user logs in).
Figure 4-1 identifies the various fields in one of the entries in the preceding example.
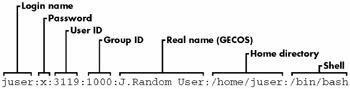
Figure 4-1: An entry in the password file.
| Note | A user and home directory are collectively known as an account. |
There are a few special users in /etc/passwd . The superuser (root) always has UID 0 and GID 0, as in the preceding example. There are other users with no login privileges, such as daemon. These generally vary from system to system, and you should leave them alone. "Nobody" is a special under-privileged user that some processes run as, because the nobody user cannot write to anything on the system.
These special users are called pseudo-users . They can't log in to the system, but the system can start processes with their user IDs for security reasons.
| Note | The /etc/passwd file syntax is special and fairly strict, allowing for no comments or blank lines. |
4.3.1 Manipulating Users and Passwords
Regular users interact with /etc/passwd with the passwd command. By default, the passwd command changes the user's password, but you can also use -f to change the user's real name, or -s to change the user's shell to one listed in /etc/ shells . (Two other commands for changing the real name and shell are chfn and chsh .) passwd is an suid-root program, running as the superuser when changing the /etc/passwd file.
Changing /etc/passwd as the Superuser
Because the passwd file is in plain text, the superuser may use any text editor to make changes. To add a user, you need to do nothing more than add an appropriate line and create a home directory for the user; deleting is the opposite . There is a special program called vipw that allows you to lock the passwd file and edit it as the superuser. To set another user's password, use passwd user as the superuser.
However, most distributions frown on editing passwd directly because it is easy to make a mistake. For example, Red Hat Linux has the commands adduser and userdel to add and remove users. Even if you use these commands or vipw , though, you should still know about the password file format, because you may need to edit it in a pinch .
4.3.2 Working with Groups
Groups in Unix offer a way to share files with certain other users on the system, but deny access to all other users. The idea is that you can set read or write permission bits (described in Section 1.17) for the group, but not the world (everyone else). This was once important because many users shared one machine, but this has become less significant in recent years as workstations have become more personal.
As mentioned earlier, /etc/passwd has a group field. The /etc/group file defines the group IDs, as shown in this example:
root:*:0:juser daemon:*:1: bin:*:2: sys:*:3: adm:*:4: disk:*:6:juser,beazley nogroup:*:65534: user:*:1000:
The fields in /etc/group are as follows :
-
The group name. (This is what shows up when you run a command like ls -l .)
-
The group password. This is hardly ever used; you can use * or any other default value.
-
The group ID (a number). The GID must be unique within the group file. This number goes into a user's group field in their /etc/passwd entry.
-
An optional list of users that belong to the group. In addition to the users listed here, users with the corresponding group ID in their passwd file entries also belong to the group.
Figure 4-2 identifies the fields in a group file entry.
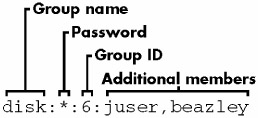
Figure 4-2: An entry in the group file.
To see the groups you belong to, run the groups command.
| Note | Linux distributions have a convention of creating a new group for each new user with the same name as the user. |
EAN: 2147483647
Pages: 189