1.17 File Modes and Permissions
1.17 File Modes and Permissions
Every Unix file has a set of permissions that determine whether you can read, write, or run the file. Running ls -l displays the permissions. Here's an example of such a display:
-rw-r--r-- 1 juser somegroup 7041 Mar 26 19:34 endnotes.html
The first column represents the mode of the file, and it is shown in bold. The mode represents the file's permissions and some extra information. There are four parts to the mode; Figure 1-1 on the next page illustrates the pieces. The first character of the mode is the file type . A dash (-) in this position, as in the example, denotes a regular file, meaning that there is nothing special about it. This is by far the most common kind of file. Directories are also common, carrying d in the file type slot. The rest of the file types are listed in Section 2.3, but you don't need to know about them just yet.
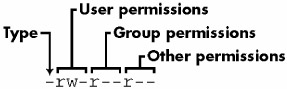
Figure 1-1: The pieces of a file mode
The rest of a file's mode contains the permissions, which break down into three sets: the user , group , and other permissions, in that order. For example, the rw- characters in the example are the user permissions, r-- are the group permissions, and r-- are the other permissions.
Four basic things can appear in each permission set:
-
r Means that the file is readable
-
w Means that the file is writable
-
x Means that the file is executable (that is, you can run it as a program)
-
- Means nothing
The user permissions (the first set) pertain to the user who owns the file. In the preceding example, that's juser .
The second set, group permissions, are for the file's group ( somegroup in the example). Any user in that group can take advantage of these permissions. (Use the groups command to see what group you're in, and see Section 4.3.2 for more information.)
Everyone else on the system has access according to the other permissions. These are sometimes called world permissions.
| Note | Each read, write, and execute permission slot is sometimes called a permission bit . Therefore, you may hear people refer to parts of the permissions as "the read bits." |
Some executable files have an s in the user permissions listing instead of an x . This indicates that the executable is setuid , meaning that when you execute the program, it runs as the file owner instead of you. Many programs use this setuid bit to run as root to get the special privileges they need to change system files. One example is the passwd program, which needs to change the /etc/passwd file.
1.17.1 Modifying Permissions
To change permissions, use the chmod command. First, pick the set of permissions that you want to change, and then pick the bit to change. For example, say that you want to add group ( g ) and world ( o , for "other") read ( r ) permissions to file . You can do it with two commands:
chmod g+r file chmod o+r file
Or you can do it all in one shot like this:
chmod go+r file
To remove these permissions, use go-r instead of go+r .
| Note | Obviously, you shouldn't make your files world writable because it gives anyone on your system the ability to change them. But would this give anyone connected to the Internet a chance to change your files? Probably not, unless your system has a network security hole. In that case, file permissions aren't going to help you. |
You may sometimes see people changing permissions with numbers , for example:
chmod 644 file
This is called an absolute change , because it sets all of the permission bits at once. To understand how this works, you need to know how to represent the permission bits in octal form (each numeral represents an octal number and corresponds to a permission set). If you're curious about this, look at the chmod(1) manual page or the info page.
It is actually not that important to know how to construct absolute modes; it is easier to just memorize the modes that you use. Table 1-4 lists the most common absolute modes.
| Mode | Meaning | Used For |
|---|---|---|
| 644 | user: read/write; group, other: read | files |
| 600 | user: read/write; group, other: none | files |
| 755 | user: read/write/execute; group, other: read/execute | directories, programs |
| 700 | user: read/write/execute; group, other: none | directories, programs |
| 711 | user: read/write/execute; group, other: execute | directories |
Directories also have permissions, as you can see from the preceding list. You can list the contents of a directory if the directory is readable, but you can only access a file inside if the directory is executable. One common mistake people make when setting the permissions of directories is to accidentally remove the execute bit when using absolute modes.
Finally, you can specify a set of default permissions with the umask shell command that are applied to any new file you create. Without going into too much detail, use umask 022 if you want everyone to be able to see all of the files and directories that you make, and use umask 077 if you don't. You need to put the umask command with the desired mode in one of your startup files to make your new default permissions apply to later sessions (see Chapter 16).
1.17.2 Symbolic Links
A symbolic link is a file that points to another file or a directory, effectively creating an alias. It is similar to a shortcut in Windows. Symbolic links offer a quick way to provide access to an obscure directory path .
In a long directory listing, these links look like this (notice the l as the file type in the file mode):
lrwxrwxrwx 1 ruser users 11 Feb 27 13:52 funk -> /home/skunk
If you try to access funk in this directory, the system gives you /home/skunk instead. Symbolic links are nothing more than names that point to other names .
The names of the symbolic links and the paths to which they point don't actually have to mean anything. In the preceding example, /home/skunk doesn't need to exist. If /home/skunk does not in fact exist, any program that accesses funk just reports that funk doesn't exist (except for ls funk , a command that stupidly informs you that funk is funk ). This can be baffling, because you can see something named funk right there in front of you.
This is not the only way that symbolic links can be confusing. Another problem is that you cannot identify the characteristics of a link target just by looking at the name of the link. You must follow the link to find out if it goes to a file or directory. Your system may also have links that point to other links, which are called chained symbolic links .
To create a symbolic link from target to linkname , use this command:
ln -s target linkname
The linkname argument is the name of the symbolic link, the target argument is the path of the file or directory that the link points to, and the -s flag specifies a symbolic link (see the warning on the next page).
When making a symbolic link, check the command twice before you run it, because there are a number of things that can go wrong. For example, if you reverse the order of the arguments ( ln -s linkname target ) you're in for some fun when linkname is a directory that already exists. In this case, ln creates a link named target inside linkname (the link points to itself unless linkname is a full path). Therefore, if something goes wrong when you create a symbolic link to a directory, check that directory for errant symbolic links and remove them.
Symbolic links can also cause headaches when you're not aware of their presence. For example, you can easily edit what you think is a copy of a file but is actually a symbolic link to the original.
| Warning | Don't forget the -s option when creating a symbolic link. Without it, ln creates a hard link, giving an additional real filename to a single file. The new filename has all of the status of the old one; it points (links) directly to the file data instead of to another filename, as a symbolic link does. Hard links can be even more confusing than symbolic links. Avoid them. |
With all of these warnings regarding symbolic links, you may wonder why anyone ever bothers with them. The simple reason is that they offer a convenient way to share files and patch up small problems.
EAN: 2147483647
Pages: 189