HOW DIFFERENT VIRUSES INFECT A COMPUTER
|
|
Viruses use one or more of the following methods to infect a computer:
-
Infecting program files
-
Infecting the boot sectors of floppy disks
-
Infecting documents using the macro capabilities of a word processor or spreadsheet
Spreading a file-infecting virus
File infectors only infect programs, such as WordPerfect or Microsoft Excel. A file-infecting virus spreads whenever you run an infected program. The two most common ways to spread a file-infecting virus is through a removable disk (such as a floppy disk, a Zip disk, or even a CD) or by email.
Parasitic program infectors
When a virus infects a file, it has three choices: It can attach itself to the front or back of a file, or it can plant itself in the middle. (If the virus deletes part of the file it's infecting, it's known as an overwriting virus.)
When a virus attaches itself to the front or back of a file, it changes the file's size and usually doesn't harm the infected file. This virus is known as a parasitic program infector and can easily be spotted by the change in file size (see Figure 7-1). While it's possible to notice a change in file size by browsing through your files, you're more likely to detect an infected virus by running an antivirus program instead.
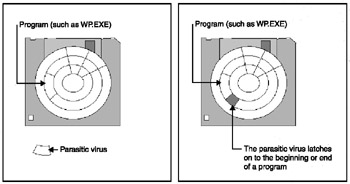
Figure 7-1: How a parasitic program infector works.
Overwriting file infectors
Overwriting viruses are a bit more dangerous. Because they physically alter any files they infect by replacing some of the program's code with their own, they can damage or destroy files. If you run a program infected by an overwriting virus, the program usually won't work. Overwriting viruses can often escape detection because they infect a file without changing its size (see Figure 7-2).
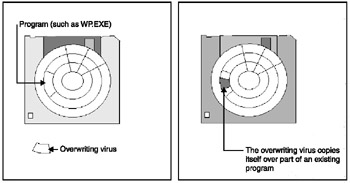
Figure 7-2: How an overwriting file infector works.
Chernobyl virus
On April 26, 1999, a virus struck in Korea and infected as many as one million computers, resulting in more than $250 million in damages. Dubbed the Chernobyl virus (or the CIH virus), this virus was written by 24-year-old Chen Ing-hau and is considered one of the most destructive viruses ever written.
The virus can infect 32-bit Windows 95 and higher executable files but can only run under Windows 95/98/ME. If you run an infected program, the virus resides in your computer's memory and infects every file that your computer accesses.
To avoid detection, the CIH virus never alters the size of any files it infects. Instead, it searches for empty space in the infected file, breaks itself up into smaller pieces, and inserts those pieces in the unused spaces.
There are three known variants of the CIH virus. Version 1.2 and Version 1.3 attack on April 26 (the date of the Chernobyl Soviet nuclear disaster) and Version 1.4 attacks on the 26th of every month.
When the CIH virus triggers, it launches two separate attacks. The first attack overwrites the hard disk with random data until the computer crashes, ultimately preventing the computer from booting up from the hard disk or floppy disk, and making the overwritten data on your hard disk nearly impossible to recover. The second attack targets the data stored in your computer's Flash BIOS (the Basic Input Output System, which is the part of your computer that controls all system devices, including the hard drive, serial and parallel ports, and the keyboard). Fixing this problem requires replacing or reprogramming the BIOS.
While every antivirus program can protect against the CIH virus, the 26th of every month still finds some companies getting their data wiped out.
Spreading a boot virus
Boot viruses only infect the boot sector of a disk, which is the part of every disk that tells the computer how to use that particular disk. A boot virus spreads whenever you boot from (or access) an infected hard or removable disk (floppy, Zip, CD, etc.). Since every disk has a boot sector with instructions that tell the computer how to use that particular disk, it's possible for a boot virus to infect any removable storage device as well.
When you turn on your computer, it first checks to see if there's a floppy disk in the disk drive. If a disk is present, the computer reads the boot sector of that floppy disk. If the floppy disk in your drive has been infected by a boot virus, that boot virus now infects your hard disk and could spread to every floppy disk you insert in your computer from this point on (see Figure 7-3). If no floppy disk is present, the computer uses the boot sector on the hard disk, called the Master Boot Record (MBR).
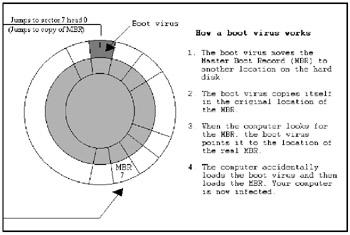
Figure 7-3: How a boot virus works.
You can also boot from a CD, which means if a boot sector virus has managed to infect your CD when you created it, it's possible for that boot sector virus to spread each time you boot up from the infected CD.
Michelangelo virus
The Michelangelo virus became, in 1992, the first virus to warrant worldwide media coverage. The virus scare began when Leading Edge, a major computer manufacturer, accidentally shipped several hundred computers infected with the Michelangelo virus, and it was another boot virus. Within a month, two software publishers, DaVinci Systems and Access Software, also shipped disks infected with the Michelangelo virus.
For some odd reason, the media quickly latched on to the Michelangelo virus story and spread hysteria far and wide, warning computer users that the Michelangelo virus would destroy their hard disks on March 6, Michelangelo's birthday. The Houston Chronicle called the virus "a master of disaster." USA Today warned that "Thousands of PCs could crash Friday." The Washington Post displayed its own scare tactic headline, "Deadly Virus Set to Wreak Havoc Tomorrow."
Estimates about the number of infected computers ranged wildly, from a low of five thousand to a high of five million. In the meantime, antivirus software publishers sold thousands of antivirus programs to a hysterical public. When March 6 arrived, computer users around the world braced themselves for the impending attack—and nothing happened.
Although the Michelangelo virus is real and did attack a few computers, the danger was nowhere near what the media proclaimed. Some experts say that if the media had failed to warn the public of the virus, the Michelangelo virus would have proven more disastrous. Others claim that the Michelangelo virus was never widespread to begin with, and that the media hype simply made antivirus program publishers wealthier.
Whatever the case, the great Michelangelo virus scare of 1992 did make the general public aware of the virus threat for the first time. And every year, around March 6, software publishers report that sales of their antivirus programs increase dramatically, much to the delight of their stockholders.
Spreading a multipartite virus
Both file infectors and boot viruses have their strengths and weaknesses. File-infecting viruses can only spread if you run an infected program. If the virus happens to infect a seldom-used file, then the program may be infected, but the virus may never spread and do any damage. Some computers can be infected for years without ever having any problems.
Similarly, boot viruses spread only when you boot up from an infected floppy or hard disk. If you don't boot up or use an infected disk, the virus can't spread.
To increase their chances of spreading, some viruses combine the features of both file infectors and boot viruses. Called multipartite viruses, these viruses can infect either (or both) files and boot sectors. Although this increases their chances of infecting a computer, multipartite viruses also make themselves more vulnerable to detection by increasing the places an antivirus program can find them. They're also more complicated to write, so there are fewer multipartite viruses in the wild to worry about.
Natas virus
The Natas (Satan spelled backward) virus is one of the more common multipartite viruses, originally discovered running rampant in Mexico. Natas can infect both files and boot sectors on both hard disks and floppies while also changing its appearance in an attempt to hide from antivirus programs.
Besides being one of the more common and destructive viruses in the wild, Natas also has the odd distinction of being written by a hacker, dubbed Priest, who later accepted a consulting job at Norman Data Defense Systems, an antivirus company. The company later decided they could not trust a known virus writer and let him go, but not before the entire antivirus community screamed in protest and vowed that they would never stoop so low as to hire virus writers to help write antivirus software.
Spreading a macro virus
Macro viruses only infect files created by a specific program, such as documents created in Microsoft Word or spreadsheets created in Microsoft Excel. Macro viruses spread when you load an infected file, such as an infected Word document.
Unlike other types of viruses that are written using assembly language, C/C++, BASIC, or Pascal, macro viruses are written using the macro programming language in a specific program. Most macro viruses are written using Microsoft's macro language, called Visual Basic for Applications (VBA), although a few older macro viruses are written in WordBasic, an older macro programming language for Microsoft Word.
Macro viruses infect the templates that define the margins, font, and general formatting for documents. Every time you create a new document from a template infected by a macro virus, the macro virus tries to infect another template and your new document.
Because most people share document files instead of template files, macro viruses cleverly convert infected documents into template files, while maintaining their appearance of ordinary document files. So while you think you're opening up a document for editing, you're actually opening up a template instead.
Despite their prevalence in the wild, macro viruses (at least at the time of this writing) have been limited to infecting documents created by Microsoft products such as Word, Excel, or PowerPoint. Although some people have tried writing macro viruses to infect WordPro or WordPerfect documents, these don't spread as easily because WordPro and WordPerfect documents store their macros in a separate file. In contrast, when you copy a Word or Excel document file onto a floppy disk, through a network, or over the Internet, you're automatically copying both your document and any macros in a single file, which gives the macro virus a chance to spread.
The Concept macro virus
The world's first macro virus, dubbed the Concept virus, can infect Microsoft Word documents on both Windows and the Macintosh. This virus was written in the macro language found in Microsoft Word version 6.0, although it can also infect Word documents created by other versions.
The Concept macro virus appears to have been written to prove that viruses really could be written using a macro programming language. As a result, Concept simply displays a dialog box announcing its existence, but it won't deliberately wreck any files on your disk.
Melissa
Taking macro virus programming one step further was the Melissa virus, which made headlines in early 1999 by becoming the fastest spreading virus in history. This virus infects Word documents and then uses VBA macro commands to read the address book of Microsoft Outlook, a common email program that comes with Microsoft Office.
The Melissa virus then creates an email message and sends it to the first 50 names in the Outlook address book, where each message appears with the subject "Important Message From" (followed by your name), with a body text that states, "Here is that document you asked for … don't show anyone else;-)." The virus then attaches a copy of the infected Word document to the email message.
As soon as the recipient opens the infected Word document, the virus spreads to that computer and repeats the process of emailing itself to another 50 people stored in that person's Microsoft Outlook address book.
If you peek inside the macro virus source code, you'll find the following message:
'WORD/Melissa written by Kwyjibo 'Works in both Word 2000 and Word 97 'Worm? Macro Virus? Word 97 Virus? Word 2000 Virus? You Decide! 'Word --> Email | Word 97 <--> Word 2000. . . it's a new age!
The original Melissa virus didn't do anything destructive, but variants do cause damage by erasing files.
|
|
EAN: 2147483647
Pages: 215