Chapter 19: Computer Forensics: Recovering and Deleting Data
|
|
This invention involves a device, referred to herein as a "cabinet," which provides physical and biochemical support for an animal's head which has been "discorporated" (i.e., severed from its body).
--UNITED STATES PATENT NUMBER 4666425: A DEVICE FOR KEEPING A SEVERED HEAD ALIVELIKE MOST CRIMINALS, HACKERS OFTEN BRING ABOUT THEIR OWN DOWNFALL BY FAILING TO REMOVE ALL TRACES OF THEIR CRIME. Not only do many hackers leave incriminating notes and printouts of their latest exploits scattered around their computers, but they also can't resist bragging to others about their exploits in public chat rooms. Yet even this blatant disregard for secrecy and indiscretion wouldn't be so damaging if these same hackers didn't unwittingly leave incriminating evidence stored all over their computers, as well.
DELETING DATA
The biggest problem with data is that once you store it on any form of magnetic media, it stays there forever. When you delete a file, your computer takes a shortcut. Instead of physically destroying the file, the computer simply pretends that the file no longer exists by replacing the first letter of the file name with a special character (hex byte code E5h), which leaves the contents of the file intact.
This process is like taking your name off an apartment building directory to make it look like you no longer live there, but staying in the apartment until someone else moves in. Only when the computer needs the space taken up by the deleted file will it actually overwrite the old file with new data. If your disk has plenty of extra space available, you could go weeks, months, or even years without ever overwriting previously deleted files. (Although, when you defragment your hard disk, your computer will likely overwrite many of these "deleted" files.)
If you delete a file, you can usually undelete it if you run an undelete utility program right away. Undelete utilities simply give a previously deleted file a new name so the computer will recognize it again. However, the longer you wait, the more time your computer will have to overwrite some or possibly all of the deleted file with new data, making it difficult, if not impossible, to recover the original deleted file.
Some utility programs, such as Norton Utilities, come with a file-deletion protection feature that saves any deleted files in a special folder so you can quickly and accurately undelete a file any time in the future. Obviously this feature can save you if you accidentally delete something, but it can also work against you by preserving those sensitive files that you thought you deleted months ago.
To find an undelete program, try one of the following:
| Norton Utilities | http://www.symantec.com |
| Active@UNDELETE | http://www.active-undelete.com |
| Restorer2000 | http://www.bitmart.net |
| Undelete | http://www.execsoft.com |
Executive Software, the makers of Undelete, also offers a free Deleted File Analysis Utility, so that you can analyze your own hard disk and see how many files may still be recoverable, as shown in Figure 19-1. The results may surprise you.
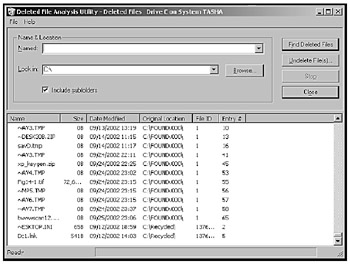
Figure 19-1: The Deleted File Analysis Utility from Executive Software can reveal all the files you deleted in the past that someone may still be able to undelete and read.
File shredders
If you deliberately erase a file and then overwrite it, most undelete programs will not be able to recover it. But if you want to make sure you've deleted a file as much as possible, use a file shredder to be sure.
File shredders overwrite deleted files one or more times using random characters, such as zeroes and ones. As a result, when an undelete program tries to recover the deleted file, the file shows only random data.
Levels of file-shredding security
Not all file shredders are equal. A good one offers several ways to shred your files, balancing speed and security (see Figure 19-2). To defeat ordinary undelete programs and wipe files quickly, a file shredder may make one pass at overwriting your deleted file with random data. While this quick wipeout defeats most undelete programs, it will not defeat specialized computer forensics tools.
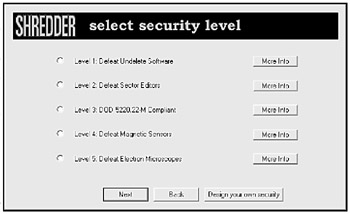
Figure 19-2: A file shredder can offer you different ways to shred your files, giving you a choice between speed and security.
For additional security, file shredders make multiple passes over a deleted file; the more passes, the longer the deletion takes, but the more likely you'll delete all data beyond hope of recovery. The Department of Defense (DoD) even has its own shredding standard, dubbed DoD 5220.22-M (http://www.dss.mil/isec/nispom.htm), which defines the government standards for deleting computer files.
The DoD file-shredding technique wipes a file seven times, each pass replacing the deleted data with a different set of random data. Since each additional pass adds another layer of random data to obscure the original, seven passes can virtually destroy all traces of the original file, although it will always be possible to recover data later using a magnetic sensor or electron microscope (discussed below).
Shredding temporary, web cache, email, and slack-space files
If you shred your sensitive files, don't forget to delete all your temporary and web cache files too. Many file shredders, such as 12Ghosts Wash (http://www.12ghosts.com) or the Macintosh-based Shredlt (http://www.mireth.com/pub/sime.html), can automatically find and destroy these types of files. BCWipe (http://www.jetico.com) can even wipe the slack space of specified files and simultaneously delete temporary and web cache files.
For further security, you can even configure some file shredders, such as the Macintosh-based NetShred (http://www.mireth.com) and the Windows-based Evidence Eliminator (http://www.evidence-eliminator.com), to delete your old email messages.
If you're really paranoid, shred your files and then defragment your hard drive. Then shred the free space remaining on your hard drive to get rid of any traces of files you don't want others to find.
Integrating a shredder into your operating system
Loading the file shredder every time you want to delete a file can be a nuisance, and you may not use it as often as you need to. Fortunately, file shredders such as Shredder95/98/NT (http://www.gale-force.com), CyberScrub (http://www.cyberscrub.com), and Shred-X (http://www.bsoft.ic24.net) can integrate themselves into your operating system so that when you delete a file, the file shredder automatically shreds the file without any additional effort on your part.
Shredding swap files
One particularly vulnerable area of your computer is the swap file. A swap file allocates part of your hard disk for storing data so the computer can free up room in random access memory (RAM) for other programs that may be running.
Any time you run a program such as a word processor, your operating system may temporarily store your data in the swap file. When you save or delete the document, much of your information still remains in the swap file for anyone to look at. For complete protection, make sure you shred your swap file regularly (ideally, every time you turn off your computer) with a file shredder such as AbsoluteShield File Shredder (http://www.sys-shield.com).
Panic-mode shredding
Your file shredder may work perfectly if you methodically delete incriminating files. But what happens if you're sitting at your computer and the police suddenly barge into your house? Some file shredders offer a panic mode for just such emergencies. To use it, you define ahead of time which files and directories you want to delete in an emergency; then, you assign a unique keystroke combination to activate the panic mode (see Figure 19-3).
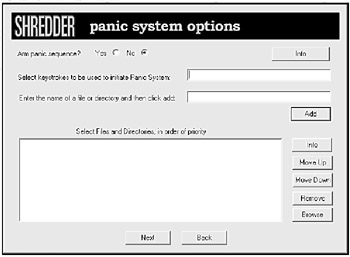
Figure 19-3: Many file shredders offer a panic mode to wipe out your files quickly in an emergency.
When the police (or other unwanted authorities) break in, press your magic panic-mode keystroke and the file shredder starts deleting all your predefined important files. If you're serious about protecting your privacy, a panic-mode feature is essential.
Password protecting your shredder
Since file shredders make undeleting files nearly impossible, they can be powerful weapons in the hands of a particularly malicious person. Just run a file shredder on your enemy's computer and you can irreparably shred the contents of an entire hard disk in minutes. Even worse than having someone deliberately shred your files is if you accidentally shred files you really wanted to keep.
To protect against an enemy or your own clumsiness, some file shredders offer a password protection feature. Before you can shred any files, you have to type in your password. Not only does this keep you from shredding your own files by mistake, but it also keeps your enemies from turning your file shredder against you.
| Caution | Password protection can stop you from accidentally deleting any files, but you wouldn't want this feature turned on if you might need to use panic-mode shredding to delete a bunch of files instantly. |
Writing your own file shredder
If you want to see exactly how a file shredder works, download the source code to the file shredder called Eraser (http://www.tolvanen.com/eraser), written by Sami Tolvanen. Not only is this file shredder absolutely free for anyone to use, but it also includes Microsoft Visual C++ source code, so you can examine how it works and even customize the program for your own particular needs.
Linux users can download a file-deleting program called Wipe (http://gsu.linux.org.tr/wipe). Like Eraser, Wipe is free to use and includes C source code so you can see how the program works and modify the program to add new features if you want.
Self-destructing email
Email can form a long incriminating trail of evidence, so you should also delete your email regularly and shred your email message directories. Since this can be a nuisance, several companies have come up with self-destructing email. The idea is that after a certain amount of time, the email message either shreds itself (using a secure file-shredding method that can defeat ordinary undelete programs) or encrypts itself so it can't be read after a certain date.
Omniva (http://www.disappearing.com) offers a unique self-destructing version of email. When you send a message to someone and run the Omniva Policy Manager program, you receive a unique encryption key from the Omniva Access server. Using this key, you can encrypt your message and send it out on the Internet. When someone wants to read your email, the email has to get the encryption key from the Omniva Access server, which opens the message.
However, once the expiration date of the message has passed, the Omniva Access server destroys the encryption key needed to open the message, effectively locking out anyone who tries to read the message ever again. In this case, the email isn't physically destroyed, but is rendered useless.
Another company that offers self-destructing email is Infraworks (http://www.infraworks.com), which offers a program called InTether. The InTether program consists of a Receiver and a Packager. To send a file (text, video, audio, etc.), you encrypt it using the Packager program. To read, view, or hear the file, another person needs the Receiver program. After a specified date, or after someone opens the file a certain number of times, the Receiver package can delete and shred the file.
While self-destructing email can protect your information in transit and at its final destination, it still won't protect prying eyes from finding traces of your data on the computer where you created the email in slack space, temporary files, and swap files. Self-destructing email can be one step to protecting your privacy, but don't count on it to protect your privacy all by itself.
|
|
EAN: 2147483647
Pages: 215