HOW COMPANIES FIGHT BACK
|
| < Day Day Up > |
|
While no one knows exactly how much piracy hurts software publishers, piracy undoubtedly translates into significant lost sales, especially when people buy counterfeit goods while thinking they’re getting a legitimate copy at a greatly reduced price. With millions of dollars at stake, software companies fight back against the pirates using a variety of tactics.
SERIAL NUMBERS: THE KEY TO INSTALLING SOFTWARE
To prevent people from copying their programs and handing them out to everyone, many programs won’t run on your computer until you enter a serial number, which is usually a series of seemingly random letters and numbers. Of course, any legitimate buyer of a program can simply pass out the serial number along with the pirated copy of the program. Because the serial number was valid to begin with, it will work on any number of pirated copies of that same program. In fact, many warez websites, such as MSCracks.com (http://www.mscracks.com), shown in Figure 12-3, contain nothing but lists of valid serial numbers for popular programs, and people can just match the version of their pirated program with the correct serial number and start using the pirated copy right away.
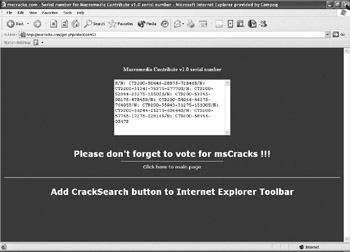
Figure 12-3: Many warez websites let you click a program name to view a list of valid serial numbers.
It’s even possible to download a database program, such as Serials2000 (http://www.serialz.to), that contains nothing but valid serial numbers for the latest programs. By running these programs and searching for the name of a pirated program, such as Photoshop or CorelDRAW, pirates can find a valid serial number (see Figure 12-4).
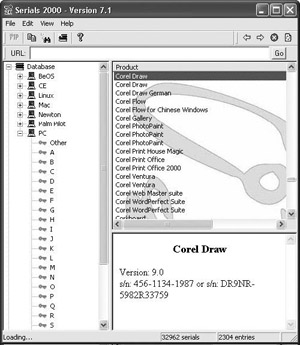
Figure 12-4: A serial number database program, such as Serials2000, lists valid (though stolen) serial numbers for use in different versions of pirated programs.
One problem with using a serial number found on a website or posted on a newsgroup is that other people will likely use that same serial number, and the software makers can use that against the thieves. For example, when Microsoft discovered a batch of stolen serial numbers used to register Windows XP, it fought back by reprogramming its Windows Update service to stop patching any copy of Windows XP that used one of these serial numbers.
For those who can’t find a valid serial number or who don’t want to risk using a serial number that dozens of others may be using, there is the serial number generator. Although serial numbers appear to consist of randomly jumbled letters and numbers, they’re actually generated by an algorithm, and the program just applies that algorithm to typed-in serial numbers to determine whether they’re valid. Serial number generators mimic a program’s algorithm to generate a list of serial numbers that the program mindlessly accepts as valid, as shown in Figure 12-5.
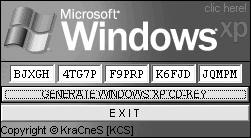
Figure 12-5: This serial number generator creates serial numbers to use in pirated copies of Microsoft Windows XP.
COPY PROTECTION: LOCKING THE GATES
Because serial numbers alone will never keep people from pirating software, some software publishers also try to prevent pirates from copying their programs. Many specialized programs, such as AutoCAD, cost several thousand dollars because they have a limited market and are highly technical. Few warez traders need the computer-aided design features of a program like AutoCAD, but companies may try to save money by buying one copy and pirating additional copies for the rest of the company. To prevent dishonest businesses from pirating software, many companies copy-protect their programs.
The two most popular methods for copy-protecting software involve software-and hardware implementations. Software-based copy-protection schemes work in two ways: they prevent someone from copying a program, and they stop people from removing the program’s copy-protection method altogether.
At the simplest level, a software copy-protection scheme might require shipping an additional file with your program. Before the program runs, it checks for this file, typically a DLL (dynamic link library) or OCX (OLE custom control). If this file doesn’t exist, the program assumes that it’s an illegal copy and either refuses to run or runs in limited demo mode. Naturally, it’s possible to just copy this missing DLL or OCX file and pass it along with a pirated copy, and lo and behold, the program will still work.
Some software publishers copy-protect their installation CDs by including a hidden file on the disc. If someone tries to copy the CD, their computer will likely miss the hidden file, so when they try to install the program from a copy of the CD, it won’t work.
Once again, this problem can be overcome by copying a CD in Raw mode. Instead of copying the files from a CD and storing them on a duplicate copy, Raw mode captures an exact image of the CD, snaring any hidden files in the process and duplicating them exactly on the copy of the CD. Some CD burning programs that offer Raw copying mode include Alcohol 120% (http://www.alcohol-soft.com), Raw CD Copy (http://www.mpegx.com), and BlindWrite (http://www.vso-software.fr).
Any type of software copy protection can eventually be overcome with enough patience, because crackers can keep probing a program until they find a way to break the copy-protection method. That’s why many software publishers prefer hardware copy-protection schemes that require users to attach a device, called a dongle, to the parallel or USB port of the computer.
With hardware-based copy protection, it doesn’t matter if people copy the program or not—the program won’t run unless it detects the presence of the dongle attached to the computer. Because you can’t duplicate dongles and pass them around as easily as you can duplicate CDs, hardware copy-protection schemes tend to offer more security, but at greater inconvenience to legitimate users. If you lose the dongle, you can’t use the program, even though you paid for it. Too, sometimes the mere presence of the dongle can interfere with other devices.
Although dongles can’t be easily duplicated, they can be mimicked. The whole copy-protection scheme revolves around the program periodically checking for the presence of the dongle, but if you emulate the existence of the dongle without the dongle itself, the program won’t know the difference.
For example, there are two companies that can create software to mimic dongles: Virtual Dongles (http://www.endlessvisions.com) and Soft-Key Solutions (http://www.software-key.org). For a price, these companies will sell you a program to mimic the dongle protecting a program so you can copy it, along with your dongle program, to any other computer you want.
PRODUCT ACTIVATION: TYING SOFTWARE TO ONE COMPUTER
One problem with ordinary copy protection is that you can install dozens of copies of a program using the exact same serial number for each of them. To prevent this, the latest copy-protection method involves product activation, where a program creates a unique key based on the installed components of a computer, such as the following:
-
Display adapter
-
SCSI adapter (if available)
-
IDE adapter
-
Network adapter MAC address (if available)
-
RAM amount
-
Processor type
-
Processor serial number
-
Hard drive
-
Hard drive volume serial number
-
CD-ROM, CD-RW, or DVD-ROM drive
This unique key is tied in with a serial number and sent to the software publisher. Then, if somebody tries to reuse that serial number, the product activation feature notices that the program has been installed on a different computer and stops the program from working. That’s the theory, anyway. The reality is that product activation can sometimes cause more problems for legitimate users.
For example, when Intuit added product activation to its TurboTax tax preparation program, customers immediately complained that the product activation slowed down or crashed their computers and prevented them from installing the same copy of the program on both a desktop and a laptop computer, essentially forcing them to buy multiple copies of the same program to run on different computers. Intuit eventually dropped product activation after enough customers howled, which showed that product activation can sometimes hurt legitimate users just as much as it might discourage software piracy.
Symantec ran across similar product-activation glitches when it added product activation to their Norton AntiVirus program. A small percentage of users soon found that the program kept asking to be reactivated every day, eventually stopping altogether. Symantec soon released a patch to fix this problem, but not before angering some customers for the unnecessary nuisance.
Naturally, crackers have found ways to fool product activation. Some have developed programs that trick the product activation feature into believing that it’s already been activated, or into thinking that the user hasn’t used the program past its initial time limit.
Because product activation ties a specific serial number to your computer hardware, you may find that you can’t use software activated in this way when you upgrade your computer. While product activation may allow you to change a handful of devices, such as swapping out a video card or plugging in a new sound card, a radical upgrade may trigger the product activation anti-piracy feature and stop the program from working.
Product activation by itself can’t stop piracy, but it can slow it down and discourage casual piracy among friends. Although product activation may currently be limited to a handful of high-profile software publishers like Microsoft, Symantec, Quark, Adobe, and Macromedia, expect more programs to include product activation in the near future.
INFILTRATION AND LEGAL ACTION
All the copy-protection methods in the world are nothing more than locks designed to slow down a determined cracker, but they do nothing to catch the people breaking the law in the first place. To find software pirates, government agencies and a handful of major software companies have hired hackers to infiltrate warez trading groups.
By masquerading as traders (who trade pirated software), couriers (who deliver fresh versions of software to crack), crackers (who remove copy protection), and collectors (who try to store as many programs as possible), these hired guns can learn who’s involved, how they find and transfer files, and where they save them. Once they collect enough evidence to track a major warez trading ring, they attempt to identify everyone involved so they can be prosecuted.
Through massive sweeps and high-profile arrests, government authorities and software publishers hope to punish the larger and more prominent warez group members while sending a message to others that warez trading will not be tolerated. Still, for every warez cracker who gets busted, more pop up to replace them, so it’s a never-ending battle. Catching warez traders can temporarily slow down the process of warez distribution but can never stop it completely. Nevertheless, the threat of prosecution and the fear of infiltration keeps warez groups cautious about attracting too much attention.
| Note | To learn more about piracy from the corporate point of view, visit FAST (Federation Against Software Theft), a UK software industry group (http://www. fast.org.uk); the Software & Information Industry Association (http://www. siia.net/piracy); the Business Software Alliance (http://www.bsa.org); and the Entertainment and Leisure Software Publishers Association (http://www.elspa. com/piracy). |
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 98