Protecting the Network
| There are a few ways we can protect the network in which our web application resides. While the exact details of these are well beyond the scope of this book, they are easy to learn about and will protect more than your web applications. FirewallsJust as we need to filter all the input that comes into our web application, so too do we need to filter all the traffic that comes at our network, whether it be into our corporate offices or a data center. You do this via a firewall, which can be software running on a known operating system (such as FreeBSD, Linux, or Microsoft Windows) or a dedicated appliance you purchase from a networking equipment vendor. A firewall's job is to filter out unwanted traffic and block access to parts of our network that we wish to be left alone. Recall from Chapter 13 that TCP/IP traffic operates on ports, with different ports dedicated to different types of traffic (for instance, HTTP is port 80). There are large numbers of ports that are used for internal network traffic and have little use for interaction with the outside world. If we simply prohibit traffic to enter or leave our network on these ports, we reduce the risk of our computers or servers (and therefore our web applications) being compromised. DMZsAs we alluded to earlier, our servers and web applications are not only at risk of attack from external customers, but also from internal malicious users. Although the latter attackers will be fewer and farther between, they often have the potential to do more damage with their intimate knowledge of how the company works. One of the ways to mitigate this risk is to implement a demilitarized zone (DMZ). In this, we isolate the servers running our web applications (and other servers, such as corporate e-mail servers) from both the external Internet and the internal corporate networks, as shown in Figure 17-3. Figure 17-3. Setting up a demilitarized zone (DMZ).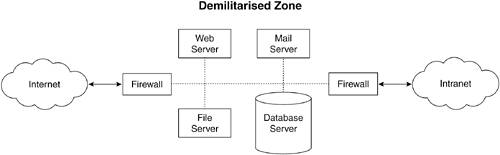 DMZs have two huge advantages:
The design, installation, and maintenance of a DMZ is something that should be coordinated with the network administrators for your host location. Educate Yourself About Network DoS and DDoS AttacksOne of the more frightening attacks seen today is known as the denial-of-service (DoS) attack, which we mentioned in the "Denial of Service" section in Chapter 16, "Securing Your Web Applications: Planning and Code Security." Network denial-of-service attacks and the more alarming distributed-denial-of-service (DDoS) attacks use hijacked computers, worms, or other devices to exploit weaknesses in software installations, or those inherent within the design of protocols, such as TCP/IP, to swamp a computer and prevent it from replying to connection requests from legitimate clients. Unfortunately, this type of attack is very difficult to prevent and respond to. Some network appliance vendors sell equipment to help mitigate the risks and effects of DoS attacks, but there are no comprehensive solutions against them. At the very least, your network administrator should do some research to understand the nature of the problem and the risks that your network and installations face. This, in combination with discussions with your ISP (or whoever will be hosting the machines running your ISP), will prepare you for the eventuality of such attacks. Even if the attack is not directed specifically at your servers, they may still become victims. |
EAN: 2147483647
Pages: 255