How Do Spammers Get My Email Address?
| Spammers are a crafty bunch. They source email addresses wherever they can get their hands on them. Website HarvestingPrograms are available that scan public address books on web-based email sites. Spammers also have software that looks for email addresses embedded in websites . If you have a personal web page, an email address you post is almost guaranteed to be found by spammers. In fact, the people who receive the most spam tend to be webmasters. After emails are harvested they are compiled into lists and sold on the Internet. Dictionary SpammingThere are also programs that combine random words and common names and pop them together in an effort to come up with valid email addresses. With so many people using email, all the common names for email addresses such as Bob Smith are long gone at the big ISPs. So people make up their email addresses from common words. So let's say your ISP is called reallybigisp.com and your email address is topdog@reallybigisp.com. Spammers might find you by running their dictionary program and combining the words top and dog together. They'll try sending an email to topdog@reallybigisp.com. They try this address combination against all the other major ISPs as well, so all the top dogs at aol.com, msn.com, and beyond get spam. And don't think that becoming topdog1967@reallybigisp.com will help because after the spammers run through the most obvious words, they start combining them with numbers . They'll even send email to aaaaaaa@reallybigisp.com, then aaaaaab@reallybigisp.com, then aaaaaac@reallybigisp.com, and so on. Because computers do all this work they can try billions of combinations in hours. Then they spam to all these potential addresses. If they don't receive a bounced email from the address, they log it as valid and put it on their active list. Commercial Email ListsMillions of email addresses are available for sale via Internet download or on CD-ROM. Out of curiosity , I bought a list of 10 million Canadian email addresses for $49. The company claimed they were all opt-in email addresses, meaning that the owners of the addresses had agreed to be put on the list. I found one of my addresses that is used for inbound mail only, however. It was never used to opt into anything (see Figure 5.4). Figure 5.4. A list of so-called opt-in emails shows email addresses whose owners never authorized their inclusion, including one owned by me (highlighted). Emails are blurred intentionally. Newsgroups, Discussion Forums, and Interactive WebsitesWhen you post your email address to the Web to receive a newsletter or to sign up for a discussion forum, for example, you expose yourself to spammers. Email addresses can also be easily harvested from Internet-based discussion groups called newsgroups (see Figure 5.5) and the Web at large. Some companies sell these lists of verified email addresses. Before making this information available, you might want to look for a privacy statement on the website to see what they are going to do with any personal information you give them. Credible websites stick to their privacy policies closely. Figure 5.5. Atomic Newsgroup Explorer is a program that can extract thousands of email addresses and user names from Internet newsgroups in mere seconds. Here it has scanned the newsgroups at msnnews. msn.com.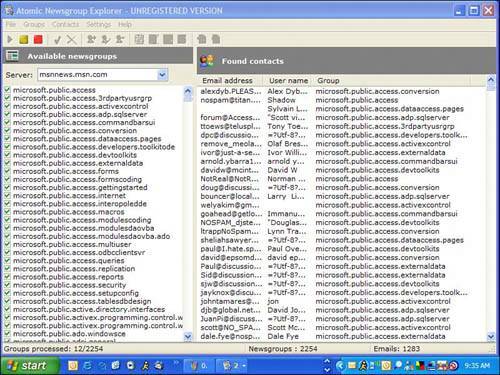 Contests and Other Free OfferingsYou can sign up to receive spam legitimately by entering contests or engaging in offers that appear to give you something for nothing. Oftentimes, these deals are email harvesting schemes. Sometimes they even explicitly tell you in the fine print that you will receive bulk commercial email and you actually agree to this. Email ForwardingIf you forward an email to dozens of people, make sure you send it to yourself in the To: field and put everyone else in the Bcc: field. Bcc means blind carbon copy. It's used to send a copy of the email to someone without revealing her email address (see Figure 5.6). If Bcc is not used, you expose everyone's email address to dozens of other people. It's been suggested that your email can be exposed to spammers that way. I know a few public relations people who have scooped my email for press release lists when another person has failed to hide my address in the Bcc: field. Figure 5.6. The Bcc: field is used when you want to send a copy of an email to someone, but hide her email address from others copied on the email.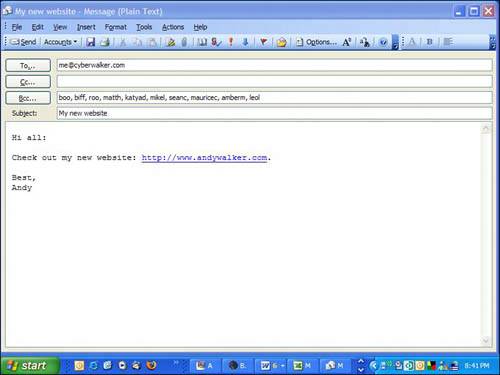 |
EAN: 2147483647
Pages: 168