How Does Phishing Work?
| A phisher's email looks like it has been sent from an organization you trust, such as your bank, but of course, it hasn't been. The trickery is achieved using a technique called spoofing , which is a techie term that basically means to electronically fool. Phishers use a series of tricks to deceive you and make you think you are corresponding with a legitimate organization. Here's how they do it. Caution
Email Address SpoofingFirst off, phishers change the sender's address in an email to make it appear as if your bank and not a tongue-pierced kid in a dumpy apartment in Warsaw sent the correspondence. This is done by simply changing the coding in the header of the email (see Figure 4.3). The header is a set of information roughly equivalent to the address information written on an envelope. Figure 4.3. This email header was taken from a phishing email that purported to be from eBay. The phisher has changed the From: field to make it look like it came from the email address suspension@ebay.com.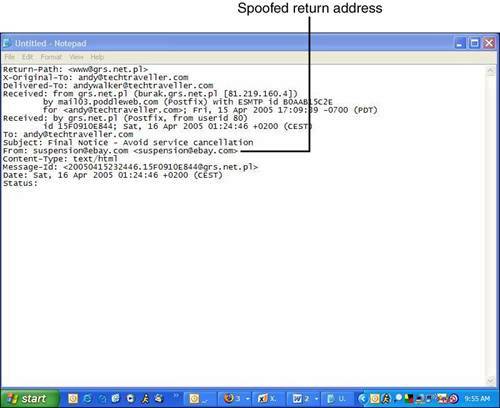 Imagine if you sent your best friend a letter by mail but instead of putting your own return address on it, you put the return address of his angry ex-wife's lawyer. On receiving it he might freak out because he'd think that she might be trying to make a claim on his new golf clubs. All you've done is spoofed the return address. Tip
Link SpoofingThe links you are urged to click on in some phishing emails are also spoofed. In the case of web address spoofing, the link looks like a legitimate address, but through some very simple technology redirects to another link. The phishing email is created with a programming language used to create web pages. In fact, when you receive an email with pictures, fancy fonts, and a nice layout, it is what's called an HTML email. It looks exactly like a web page because it is made with HTMLthe same programming language used to create web pages. HTML is short for HyperText Markup Language. To create a clickable link in HTML, you use programming code like this: <a href="http://www.realsafebank.com">www.reallysafebank.com</a> This results in a web link that looks like this: www.reallysafebank.com Tip
Note that the web address inside the angle brackets between the quotes and after the <a href= is the web address where you are taken if you click on the link (see Figure 4.4). Figure 4.4. These two actual web links look exactly the same but the programming used to create them, which appears below each one, have different destinations on the Web.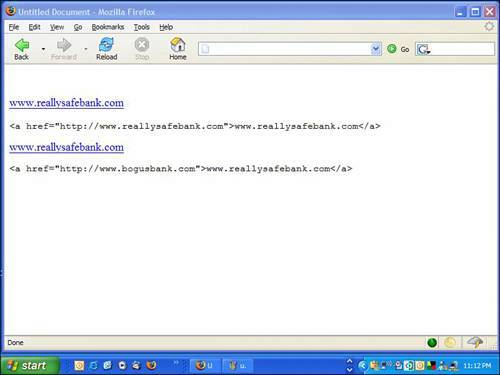 Phishers use this programming trick to make it appear as if you are going to one site, but really they put the address of a bogus page in the HRef tag, like this: <a href="http://www.bogusbank.com">www. reallysafebank.com</a> So you think you're about to go to www.reallysafebank.com but you're actually taken to www.bogusbank.com, which looks like your legitimate bank's webpage and might actually contain a series of web pages to make it look like an actual banking site. Web Address SpoofingPhishers have been exploiting a bug (an error) in the programming of Microsoft web browser Internet Explorer so they can display a fake web address in the browser. When you visit a website that exploits this bug, its web address is not displayed in the browser. Instead, another more trustworthy web address is displayed. So you could be fooled into visiting www.bogusbank.com by a phishing email but your web browser shows you are on www.reallysafebank.com. Tip
The bug affects versions 5.01, 5.5, and 6 of Internet Explorer. However, patches for the vulnerable browser have been issued by Microsoft to fix it. If you run Windows Update and download the latest patches, you will have the patch already installed. To test if you are vulnerable, open Internet Explorer and visit security firm Secunia.com at http://secunia.com/internet_explorer_address_bar_spoofing_test/. If your web browser is not up-to-date with the latest Microsoft fix, you'll see how the spoofing trick works and a fake address appears in your address bar. If the bug is fixed in your browser, you'll see "This page cannot be displayed." Caution
|
EAN: 2147483647
Pages: 168

