CISCO APPLIANCE PASSWORD CRACKING. (cisco network infrastructure)
| | ||
| | ||
| | ||
CISCO APPLIANCE PASSWORD CRACKING
In complex networks with a great number of network devices, there are good reasons to deploy centralized authentication servers; however, many hosts store the passwords on the appliances themselves in the configuration files in the Non-volatile RAM (NVRAM). Historically, Cisco has moved from storing passwords in cleartext to employing various forms of cryptographic protection, so that the passwords cannot be understood by an attacker who manages to get hold of the configuration file or sees it on a screen during a shoulder-surfing session. The methods of obtaining the config files have been described in great detail in previous chapters, so we assume that you have already obtained config files in the process of pentesting or are able to execute show running-config .
If you are lucky, you can also find a cleartext password in the config file. To do this, you search for the enable password in the config or execute show running-config include enable and you would then see enable password <password> . Although rather rare nowadays as compared to the '90s, such mistakes are not that uncommon, and the number of security-careless administrators grows larger since more and more low-qualified personnel get administrative access to devices. To address the problem of carelessness, Cisco introduced a foolproof mechanism of protection for sensitive information with the introduction of service password encryption . Once set, the new passwords would automatically be encrypted with Cisco's own cryptographic algorithm, more commonly known as Type-7 .
Cracking Type-7 Passwords
| Attack |
|
Someone unfamiliar with cryptography may not notice or recognize that a Type-7 (Vigenere) password can be easily decrypted. The string to look for in the config file is similar to this:
password 7 08314942060D0E16
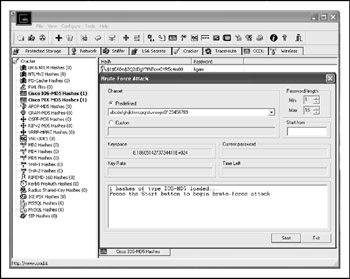
Figure 9-1: Instant password decryption with Cain & Abel
You could go straight to one of the many sites on the Internet that offer straightforward online password 7 decryption services, such as the Cisco Password 7 Hash Decoder at http://www.securecode.net/CiscoCrack.html . You could also use various applications that do this for you, such as SolarWinds' ( http://www.solarwinds.net/ ) network management utilities password 7 cracker and GetPass ( http://www. boson .com/promo/utilities/getpass/getpass_utility.htm ). Cain & Abel ( http://www.oxid.it/cain.html ) would be able to help you to crack the Type-7 password (see Figure 9-1).
For geeks using Linux, several utilities, such as ciscocrack, can do the same. This simple Perl program can easily deal with this weak cipher:
#!/usr/bin/perl -w # $Id: ios7decrypt.pl,v 1.1 1998/01/11 21:31:12 mesrik Exp $ # # Credits for orginal code and description hobbit@avian.org, # SPHiXe, .mudge et al. and for John Bashinski <jbash@CISCO.COM> # for Cisco IOS password encryption facts. # # Use for any malice or illegal purposes strictly prohibited! # @xlat = (0x64, 0x73, 0x66, 0x64, 0x3b, 0x6b, 0x66, 0x6f, 0x41, 0x2c, 0x2e, 0x69, 0x79, 0x65, 0x77, 0x72, 0x6b, 0x6c, 0x64, 0x4a, 0x4b, 0x44, 0x48, 0x53, 0x55, 0x42); while (<>) { if (/(passwordmd5)\s+7\s+([\da-f]+)/io) { if (!(length() & 1)) { $ep = ; $dp = ""; ($s, $e) = (=~ /^(..)(.+)/o); for ($i = 0; $i < length($e); $i+=2) { $dp .= sprintf "%c",hex(substr($e,$i,2))^$xlat[$s++]; } s/7\s+$ep/$dp/; } } print; } For the reader who wants a bit of in-depth explanation of the decryption process and does not mind taking a pen and paper and performing some mental exercises, the process is explained here. Let's try decrypting the small string 121B0A15001E051721 . First, note that all operations are performed with hexadecimal numbers . The first two symbols of the password indicate an offset in the string that we will be using to XOR against. The length of the password (in decimal) would equal half the length of the encrypted password, minus one. In the case of the string 121B0A15001E051721 , (18 / 2)1 = 8; so we know that the password is only eight characters in length.
Cisco uses a stream cipher against which to XOR the password; in our example, such a string is dsfd;kfoA,.iyewrkldJKDHSUBsgvca69834ncx .
Converting the string into the hex ASCII code produces the following result:
ASCII d s f d ; k f o A , . i y e w r k l d J HEX 64 73 66 64 3b 6b 66 6f 41 2c 2e 69 79 65 77 72 6b 6c 64 4a ASCII K D H S U B s g v c a 6 9 8 3 4 n c x HEX 4b 44 48 53 55 42 73 67 76 63 61 36 39 38 33 34 6e 63 78
Note that for each of the following pairs of digits, the offset is increased by shifts on one position. Searching the key stream for the 13th offset, then, we get the value 65.
12 1B 0A 15 00 1E 05 17 21 Type-7 password XOR 79 65 77 72 6B 6C 64 4A Part of stream -------------------------- 62 6F 62 72 75 69 73 6B ASCII Hex code b o b r u i s k ASCII Character
The values we get are hexadecimal code in the standard ASCII table. Linux users can use man ascii to view the table, or values can be looked up on the Internet at http://www.lookuptables.com . That's really as simple as it gets.
Browsing through the configuration files, we have often discovered that both enable and user passwords are stored in the MD5 and Type-7 forms of encryption simultaneously . The password stored as an MD5 secret would take precedence over the password stored as Type-7, disabling the latter. However, it often happens that for one reason or another the Cisco administrator decides to switch the encryption type and re-enters the old password in the MD5 form, leaving the old Type-7 weak entry in place. So much for the added value of the network administrator switching to the stronger cryptography!
Cracking MD5 Password Hashes
| Attack |
|
Known for paying reasonable attention to security, Cisco has implemented a cryptographically secure method of storing appliance passwords. The majority of Cisco devices support the creation of a secure MD5 hash of the password, which is a one-way hash function that makes the reversal of the encrypted password nearly impossible and provides strong cryptographic protection of sensitive information.
An administrator would use the enable secret 0 <password> or username <username> secret 0 <password> command to set strong passwords. In the configuration file, you can identify such passwords by their similarity to the following:
enable secret 5 $m.KJ$xDWtXVXmOzXEdThklkP0f0 username Cisco secret 5 $u6as$HtZ/c4fwded0mkyP.0EpI.
Let's see whether this scenario is as secure as the one who reads the security manual would believe while praising the almighty hash functions.
We need a program that would go through different password combinations and determine the correct one. A lot of these utilities exist, but our favorite one is John the Ripper, available at http://www.openwall.com/john/ .
Download and untar the tool, and then select the architecture of the platform on which you will be running John. Bear in mind that the system type you select will also affect the performance of the bruteforcing process, so choose wisely. The truncated output of supported Linux systems is shown here:
linux-x86-any-elf Linux, x86, ELF binaries linux-x86-mmx-elf Linux, x86 with MMX, ELF binaries linux-x86-any-a.out Linux, x86, a.out binaries linux-x86-64 Linux, AMD x86-64, 64-bit native linux-x86-64-mmx Linux, AMD x86-64, 32-bit with MMX linux-alpha Linux, Alpha linux-sparc Linux, SPARC 32-bit linux-ppc32 Linux, PowerPC 32-bit linux-ppc64 Linux, PowerPC 64-bit linux-ppc32-altivec Linux, PowerPC w/AltiVec
For the modern i386 architecture, you would select the linux-x86-mmx-elf system type and execute make linux-x86-mmx-elf . Once the tool compiles, you can switch to the run directory and benchmark the bruteforcing process by executing john test . You should see the number of password combinations per second that John is able to go through (the more the better, of course).
Open up a new file and paste the information you have obtained from the Cisco configuration file in the following format:
test:$EADn$ZQ2d3gY7fNTowOYR5c4m80<F255D>
Then save the file and exit.
Execute John as follows :
arhontus / # john ciscopassword Loaded 1 password hash (FreeBSD MD5 [32/32]) guesses: 0 time: 0:00:00:06 c/s: 3320 trying: ciel guesses: 0 time: 0:00:00:36 c/s: 3666 trying: f1or kgam (test) guesses: 1 time: 0:00:01:51 c/s: 3650 trying: kgam
On the AMD XP 2500+ machine, John is able to bruteforce roughly 3500 combinations per second; the time it would take to go through all the different possible combinations of passwords is (charset ˆ˜ password_length) / comb_per_second . Fortunately, John is a highly advanced and intelligent bruteforcer that implements different statistical techniques to speed up the bruteforcing process (see John's documentation for an indepth explanation of the word list, single, incremental, and external modes).
As you can see in the output, the short nondictionary password kgam was discovered in 1 minute 51 seconds. We have used the incremental cracking mode with a charset containing all the characters and the maximum password length set to 4. Although these 2 minutes might seem like a quick bruteforcing job, a longer password may take an eternity to bruteforce and might be considered safe.
Windows users, who are often antagonized by purely command line interface (CLI) tools, can use Cain & Abel to crack IOS MD5 passwords.
Another common product from the Cisco range is Secure PIX firewall. The password encryption scheme of PIX uses the Base64-encoded MD5 hashesno salt, and pretty hopeless for the product carrying the "secure" name . In comparison, the IOS MD5 encryption we described previously uses 1000 MD5 update rounds and adds 12 bits of salt to make password bruteforcing much more difficult.
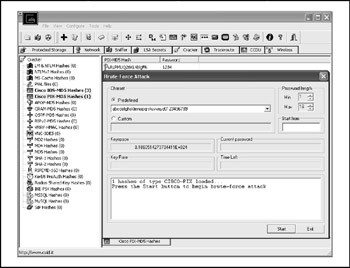
Figure 9-2: Cain & Abel PIX-Hash bruteforcing attack screen
The password entries in the config files of the PIX firewalls are easily identifiable, as shown here:
pixfw# show run include passw enable password Itn9sO/yhumXJ7Jv encrypted passwd RLPMUQ26KL4blgFN encrypted
The inbuilt mechanism of Cain & Abel can be utilized to attack the PIX hashes (see Figure 9-2).
Another tool whose job is to crack Cisco passwords is tomas, developed by Michael Thumann and available for download from https ://www.ernw.de/tools/tomas.zip .
C:\tomas>tomas Too Many Secrets v0.9 (c) 2002 by Michael Thumann (mthumann@ernw.de) Usage: tomas [options] [enable secret password] {part of passwordwordlist} a : Add known part of password string at the end b : Add known part of password string at the beginning c : Include capital letters in brute force attack h : Enable hybrid attack combined with dictionary attack (2 characters) l : Include small letters in brute force attack n : Include numbers in brute force attack p : Crack Cisco PIX passwords (use with other options) s : Include special characters in brute force attack w : Do dictionary attack Example: tomas clns $R/ep$fCKxznnW9J8JFbB7pRQD./ Example: tomas bl $R/ep$fCKxznnW9J8JFbB7pRQD./ cisc Example: tomas w $R/ep$fCKxznnW9J8JFbB7pRQD./ words.lst Example: tomas whn $R/ep$fCKxznnW9J8JFbB7pRQD./ words.lst Example: tomas pw N7FecZuSHJlVZC2P words.lst Password-Cracking Countermeasures
| Countermeasure | As is often the case, Cisco's secret method of storing passwords in the IOS configuration files can be considered relatively secure, providing you have selected a lengthy password containing a mixture of letters, numbers, and special characters. In the latter case of MD5 PIX firewall hashes, you should choose the maximum length password containing multiple special characters to make bruteforcing a more painful process for the attacker. We have already reviewed password security and related Cisco auto secure features in Chapter 6, so we won't dwell on this topic here. |
As to password Type-7, you should consider it as secure as cleartext and avoid using it by all meansit isn't even at the "kindergarten" level of encryption.
Social Engineering Attacks
| attact |
|
Social engineering is usually either the cracker's first or last resort. The cracker can either go for it straightaway if the conditions are sufficiently favorable or resort to it if everything else failed. "Traditional" social engineering techniques include the following:
-
Playing the role of an authority, such as network administrator or manager
-
Playing the role of a naive end-user
-
Playing the role of someone from a partner company or organization
-
Playing the role of an ISP technician or another individual who may have physical access to the company's systems
-
Tricking an employee into planting malicious software on internal systems, usually via e-mail or instant messengers
-
Stealing the identity of a legitimate user
-
Dumpster diving and shoulder-surfing attacks are also a form of social engineering, in that they also exploit "wetware errors."
| Tip | Lots of old, but good, documentation on various aspects of social engineering are available at http://www.packetstormsecurity.org/docs/social-engineering/ . |
Now let's see how all of the above could or could not apply to the Cisco world. First of all, normal users do not have access to routers, switches, and so on. System administrators are a much more difficult target. If an attacker goes for the authority role play, he or she must pretend to be a high-level authorityfor example, a senior IT manager of a large company when targeting a junior system administrator new to his job. Thus, this kind of attack is not easy to perform.
Playing the role of a naive user won't work at all, unless we are talking about gaining general network access rather than access to a specific device. Examples of such cases involve trying to gain access to a virtual private network (VPN) created to a Cisco VPN concentrator or to a network with 802.1x-protected access using Extensible Authentication Protocol-Lightweight Extensible Authentication Protocol (EAP-LEAP) or EAP-Flexible Authentication via Secure Tunneling (EAP-FAST). The latter case would apply mainly to wireless LANs. Stealing a legitimate user's identity would also be relevant to such examples of general network access, unless a master con artist manages to steal the identity of someone from the technical IT team (not very realistic).
Tricking a system administrator to load malicious software on a router or switch isn't very realistic either. For such an attack to succeed, the cracker must possess a backdoorpatched version of IOS, CatOS, or another relevant operating system and claim that this update is absolutely necessary due to the latest serious security flaw. While there are rumors that such trojaned IOS binaries exist, we could not find one "in the wild" even after a very extensive search (see Chapter 10 for more details on this topic). In addition, a " warned " system administrator is likely to download the OS image from an official Cisco web site, and these images aren't small enough to be sent by e-mail (it would look very strange to receive an IOS binary by e-mail anyway). Thus, the only way to succeed in this tactic is probably to send an e-mail with a link to a backdoored image that would look very much like a link to a file at http://www.cisco.com , while actually leading to a spoofed site. For now, we don't consider such an attack to be a serious threat.
A "real El Dorado" for Cisco social engineering attacks does exist: if the attacker claims to be an ISP or technical support company engineer. In many situations, the support of a Cisco network infrastructure is outsourced. Sometimes, the gateway router doesn't even belong to the target company. Instead, it is controlled by a large ISP that may send a different technician every time some problem with a gateway needs to be fixed and fixing via remote access is impossible. This usually applies to small and medium- sized companies, but even large companies may subscribe to such a scheme. Consider a social engineering attack by someone with a fake ID (and perhaps a fake Cisco Certified Network Associate [CCNA] or Cisco Certified Network Professional [CCNP] card) coming into the target company office with a proclamation like this:
Hi, I am Kevin Bloggs, a network engineer from <insert ISP name here> ( he flips out his fake ID and fake CCNA card for a second ). We need to upgrade the operation system on your gateway router to <counter the latest security flaw, increase the router's performance, tweak QoS, support some voice/multimedia streaming protocol>. At the moment, your router does not have a sufficient amount of RAM (or Flash) memory to support the upgrade. But as a courtesy to our customers, we are going to install free additional memory to the router ( a memory stick is shown to the "person under attack" ). Could you please guide me to the router? It would take only 10 or 15 minutes to do.
Convincing, no? Especially if the target has previously received a spoofed e-mail claiming to be from the ISP (or technical support company) saying
On Tuesday, at 10:00 PM, Kevin Bloggs, CCNA, will come to your office to upgrade your router because of <insert the reasons mentioned above here>. It will take only a few minutes of downtime and won't cost you anything. In fact, we are going to cover the costs of upgrade following our latest client satisfaction program. We apologize for any inconvenience caused.
And how do we determine whether a gateway belongs to the target company or the ISP? This is easy, as long as whois and traceroute are your best friends .
This type of an attack is a bit more difficult for an attacker who claims to be from a technical support company, with which a somewhat more personal contact is usually established. However, the attacker may claim to be a new employee just starting the job and may even try to elicit sympathy by asking for assistance, inquiring how the previous consultants provided help, and so on. A similar example is posing as a partner company employee and claiming that a change has been made in the configuration of its routers, saying that the change must be synchronized between both companies and organizations. Such approaches are not likely to result in an attacker being handed physical access to the company router. However, an infrastructure common between both companies can be successfully exploited.
Above all, this may apply to a routing protocol running between the companies or organizations. A cracker can claim that at a particular time the routing protocol password must be changed. Such a claim must be made to both companies simultaneously. If successful, it will hand the attacker access to the routing protocol. This may allow the cracker to redirect traffic between the companies through a rogue router he controls, using methods described in the last chapter of this book. Such redirection makes sniffing, session hijacking, and data modification attacks possible. Alternatively, a cracker may call or write pretending to be a new employee from a partner organization and asking for a VPN or dial-in access.
Finally, any system by any manufacturer is susceptible to opportunistic shoulder-surfing attacks, providing that passwords are used and the attacker could get into the company office and close enough to the system administrator's station. The same applies to dumpster diving, even though the ever-present paper shredders and the end of widespread floppy disk usage have reduced the possibility of these attacks by a significant margin. Still, security-minded employees should make sure that all hard drives that are thrown away get properly smashed with a heavy object or rubbed with a strong magnet before hitting the dumpsters. Of course, prior to that you can use a variety of hard-drive wiping utilities. You can use commercial applications or download many for free from http://www.thefreecountry.com/security/securedelete.shtml . On Linux, you can run shred .
All social engineering means we have described so far are external . The attack is launched by someone outside the company realm after finding out as much information about the company as possible by using both technical (network enumeration) and nontechnical (snooping on employees, making friends with them) means. An internal attacker, the rogue employee, is in a much better position. Perhaps he or she can simply walk into the server room and plug in a console cable. The internal attacker has time to study the system administrator's habits and invent a distraction for him or her to win some time and sneak into the racks. Buying the administrator a beer and pizza usually works. The attacker may claim curiosity and ask the administrator to show him or her "how things work" or use any other opportunity to shoulder-surf. Other cases occur with devices stored in a data center. An attacker can give the data center a phone call, claiming that he or she is arriving from a victim company "to fix stuff," and then arrive , armed with a fake ID, make a sweep of the cardlock device a couple of times, mention that "there is some glitch and it doesn't work," and ask for assistance. There is a pretty good chance that this attacker will be guided straight to the target box. In case any questions and suspicions arise, a social engineer can play the "I am a new employee and I don't know much" game.
In the opportunistic data center attack, if an attacker is a system administrator, he or she can catch a favorable moment and stick a console cable into a neighbor's Cisco device when no one is watching. This attack is likely to be limited to the same rack with a machine owned by the attacker. Beforehand, the attacker could determine who owns the device by reading a sticky label with the owner's name or device IP address attached to the box. Of course, a cracker can also try to sniff traffic to and from the device using a legitimate server, map the IPs around the server (likely to be in the same rack!), and perform other evil acts of network enumeration prior to the social engineering attack.
In theory, these kinds of attacks should never happen, because every visitor in a data center is supposed to be closely watched all the time. In reality, the data center can be understaffed, its personnel can be distracted by other visitors , they may trust the attacker if he or she is a longtime client of the center, and so on. The authors have caught a few moments in different data centers when no one was watching for a time period sufficient to stick a console cable into someone else's router and reboot it. It was even somewhat tempting to try.
Social Engineering Attack Countermeasures
| Countermeasure | One may say that there is no reliable way to defend against social engineering attacks. We would disagree , however; the way to fend them off is called paranoia . Some paranoia is goodit is a form of total awareness. With that in mind, trust no one. If someone calls or writes claiming to be from an ISP, technical support, or a partner company and asks to come in and upgrade or reconfigure your systems, call the ISP or company and ask for details. If someone shows up with similar demands, call his or her superiors as the person waits and watch the person's reactions as you ask whether such an employee exists and whether the tasks he or she talks about were really ordered, when they were ordered, and by whom. |
If someone's sweep card or token doesn't work, don't let the person into the data centerno matter what. Instead, question the individual. Carefully observe all visitors to the company premises and spot whether they try to shoulder-surf, connect any devices to a local network, or tweak with the company computers. Don't let anyone , apart from the legitimate employed IT personnel, into the server room and keep the racks locked at all times unless physical upgrade or reboot is absolutely necessary and you've made sure that this is the case. Conduct a proper exit interview and ensure that fired employees completely lose their free access to the company premises as well as their system accounts. Don't let any sensitive information go to dumpsters undestroyed. Simply deleting the data on a hard drive or router/switch flash is not enough! If company equipment is sold to a third party, completely erase its configuration before handing the equipment to buyers . Above all, educate your users and junior technical personnel about social engineering and the means attackers may use to con them into obtaining device or network access.
The professionals at Cisco Systems understand the threat of social engineering attacks and the importance of user security awareness; the company has built a web page specifically devoted to creating a security-aware corporate or organizational culture. We strongly advise you to consult it at http://www.cisco.com/en/US/about/security/intelligence/mysdn-social-engineering.html .
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 117