SNIFFING FOR CISCO-SPECIFIC PROTOCOLS
| | ||
| | ||
| | ||
During the two decades since it was founded, Cisco Systems has developed a variety of useful proprietary network protocols on all layers of the Open System Interconnection (OSI) model. In this book, we are not concerned with their functionality and cool features; instead, we focus on the fact that these protocols give away all Cisco-made devices on an investigated network with ease and without a malicious hacker needing to send a single packet to the enumerated device. The hacker can simply look at the hosts sending the proprietary protocol's Protocol Data Units (PDUs) and hosts responding to them and log their MAC and IP addresses. Some of these protocols have known security flaws that allow exploitation of hosts sending them without any further device fingerprinting necessary. This helps an experienced attacker stay as quiet as possible on the attacked network. A list of common Cisco proprietary and related protocols, layer by layer, is presented in Table 5-1.
| Protocol | Destination Multicast MAC or IP Address Used | Comments |
|---|---|---|
| Data-Link Layer | ||
| Port | 01-00-0c-cc-cc-cc | SNAP High-level Data Link Control (HDLC) protocol type 0x0104. Used to bundle ports on Catalyst switches into an EtherChannel. Similar to Ethernet bonding in the Linux world. |
| VLAN Trunking Protocol (VTP) | 01-00-0c-cc-cc-cc | SNAP HDLC protocol type 0x2003. Exploitable and gives away a lot of data about configured virtual LANs (VLANs) (see Chapter 12). |
| Inter Switch Link (ISL) | 01-00-0c-00-00-00 | Functionally similar to 802.1q. Watch out for baby giant frames . Not to be confused with the Internet Security Label, also abbreviated as ISL. |
| Dynamic Trunking Protocol (DTP) | 01-00-0c-cc-cc-cc | SNAP HDLC protocol type 0x2004. Negotiates trunk port mode between Cisco Catalyst switches. Exploitable to jump VLANs (see Chapter 12). |
| Spanning Tree PVST+ | 01-00-0c-cc-cc-cd | SNAP HDLC protocol type 0x010b. Cisco proprietary version of the Spanning Tree Protocol (STP). Exploitable (see Chapter 12). |
| STP Uplink Fast | 01-00-0c-cd-cd-cd | SNAP HDLC protocol type 0x200a. Speeds up STP convergence time in the presence of redundant links on networks consisting of Catalyst switches. |
| VLAN Bridge STP | 01-00-0c-cd-cd-ce | SNAP HDLC protocol type 0x010c. Operates on top of IEEE STP to bridge VLANs while running single instance of STP. Indicates presence of Catalyst 6000/6500 switches with Multilayer Switch Feature Cards (MSFCs) installed. |
| Cisco SYNC | 01-00-0c-ee-ee-ee | Sent by the root bridge on VLAN 1 every 2 minutes. Helps to maintain an accurate STP topology. |
| System Network Architecture (SNA) Switching (SNASw) | N/A | Carries SNA traffic directly across IP network without being encapsulated. IBM mainframe is nearby. |
| Data-Link Switching (Cisco DLSwt) | N/A | Transports SNA and NetBIOS traffic over IP. IBM mainframe is nearby. |
| Cisco Discovery Protocol (CDP) | 01-00-0c-cc-cc-cc | SNAP HDLC protocol type 0x2000. CDP is your best friend, and some attacks are CDP-related, too (see Chapter 12). |
| Cisco Group Management Protocol(CGMP) | 01-00-0c-dd-dd-dd | SNAP HDLC protocol type 0x2001. Limits the forwarding of IP multicast packets only to those ports associated with IP multicast clients on Catalyst switches. |
| Layer 2 Forwarding (L2F) protocol | N/A | Old Cisco data-link layer proprietary protocol; see RFC 2341. |
| Network Layer | ||
| Hot Standby Routing Protocol (HSRP) | 224.0.0.2 (all routers) | Creates a virtual router for redundancy reasons. Exploitable (see Chapter 13). |
| Generic Routing Encapsulation (GRE) | N/A | Originally Cisco tunneling protocol, now supported by many non-Cisco devices and systems. Often indicates a presence of virtual private network (VPN) above it. Exploitable (see Chapter 13). |
| Enhanced Interior Gateway Routing Protocol (EIGRP) | 224.0.0.10 | Exploitable (see Chapter 14). |
| Interior Gateway Routing Protocol (IGRP) | 224.0.0.10 | Exploitable (see Chapter 14). |
| Application Layer | ||
| Skinny Client Control Protocol (SCCP) | N/A | Cisco proprietary protocol used between Cisco Call Manager and Cisco VoIP phones. Indicates the presence of these devices and VoIP in use. |
| Web Cache Communication Protocol (WCCP) | N/A | Provides transparent caching by diverting HTTP traffic to the Cisco Cache Engine. Has a security flaw (Cisco bug ID CSCdk07174). |
| Tip | Many of the MAC addresses listed for Cisco proprietary data-link protocols can be viewed by executing the show cam system command on CatOS or show mac self command on IOS-like Catalyst switches |
As you can guess from Table 5-1, by passively sniffing network traffic, it is possible to ob-tain far more data than many could have imagined. This includes the precise type of the Cisco device in use (for example, Cisco Cache Engine, Cisco VoIP phone, high-end Catalyst switch with Multilayer Switch Feature Card [MSFC]) and even the characteristics of a specific inter-face exposed to your eavesdropping (for example, the presence of a trunk port on a switch).
Remember that CDP, VTP, and PAgP updates are always forwarded on trunks with a VLAN 1 tag. So do not assume that you are on VLAN 1 (as you would love to be) if you see them. On the contrary, 802.1q updates are forwarded untagged on the VLAN 1 for interoperability reasons, unless VLAN 1 has been cleared from the trunk port. Cisco PVST+ updates are sent and tagged for all other VLANs. Watching for these small details helps you determine which VLAN you are on, an important prerequisite for VLAN jumping/trunk port-forcing attacks, described later in the book.
Other vital considerations when strolling through Cisco proprietary protocols flying across the network include the presence of H.323 (VoIP) and VPN traffic and the struc-ture of the STP tree. An STP root switch should be the "fattest" switch on the network, and you want your box to become a root switch instead of the legitimate one (we cover STP attacks in Chapter 12). Finally, the detailed enumeration of interior gateway proto-cols (IGPs) (such as IGRP) was discussed in Chapter 4.
Dissecting CDP Frames
| Attack |
|
Cisco Discovery Protocol (CDP) is so important in Cisco device enumeration and fingerprinting that it deserves a section on its own. Wouldn't it be wonderful if a finger-printed device would effortlessly tell an attacker everything about itself? CDP does precisely thatalas, on the same broadcast domain only. Even better, it would run prac-tically over any Layer 2 protocol that supports Subnetwork Access Protocol (SNAP) encapsulation (all LAN media, HDLC, frame relay, and asynchronous transfer mode [ATM]) and is enabled by default on the majority (if not all) of Cisco hosts. To add insult to injury , an existing efficient Denial of Service (DoS) attack against Cisco routers ex-ploits CDP, and a method is available to extract the CDP and other data remotely by using a memory leak in old, but still frequently encountered , IOS 11.X versions.
| Note | In agreement with Cisco, HP ProCurve switches also support and use CDP. Thus, not all CDP broadcasting (well, multicasting) devices are Cisco-made, but you'll see it in the CDP frames anyway. |
The best way to see the characteristics and capabilities of CDP is by example:
cisco-2611b#show cdp Global CDP information: Sending CDP packets every 60 seconds Sending a holdtime value of 180 seconds Sending CDPv2 advertisements is enabled Source interface is Loopback0 cisco-2611b#show cdp interface Ethernet0/0 is up, line protocol is up Encapsulation ARPA Sending CDP packets every 60 seconds Holdtime is 180 seconds Serial0/0 is up, line protocol is up Encapsulation PPP Sending CDP packets every 60 seconds Holdtime is 180 seconds Ethernet0/1 is up, line protocol is up Encapsulation ARPA Sending CDP packets every 60 seconds Holdtime is 180 seconds cisco-2611b#sh cdp traffic CDP counters: Total packets output: 56241, Input: 17528 Hdr syntax: 0, Chksum error: 0, Encaps failed: 0 No memory: 0, Invalid packet: 0, Fragmented: 0 CDP version 1 advertisements output: 18713, Input: 17528 CDP version 2 advertisements output: 37528, Input: 0 cisco-2611b#sh cdp neighbors Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge S - Switch, H - Host, I - IGMP, r - Repeater Device ID Local Intrfce Holdtme Capability Platform Port ID cisco2503 Ser 0/0 150 R 2500 Ser 1 002660741(Gromozeka) Eth 0/0 171 T S WS-C5000 4/11 cisco-2611b#sh cdp neighbor detail ------------------------- Device ID: cisco2503 Entry address(es): IP address: 192.168.30.50 Platform: cisco 2500, Capabilities: Router Interface: Serial0/0, Port ID (outgoing port): Serial1 Holdtime : 176 sec Version : Cisco Internetwork Operating System Software IOS (tm) 3000 Software (IGS-I-L), Version 11.0(8), RELEASE SOFTWARE (fc1) Copyright (c) 1986-1996 by cisco Systems, Inc. Compiled Sat 27-Apr-96 01:23 by vprasadadvertisement version: 1 ------------------------- Device ID: 002660741(Gromozeka) Entry address(es): IP address: 192.168.77.250 Platform: WS-C5000, Capabilities: Trans-Bridge Switch Interface: Ethernet0/0, Port ID (outgoing port): 4/11 Holdtime: 136 sec Version: WS-C5000 Software, Version McpSW: 4.5(12a) NmpSW: 4.5(12a) Copyright (c) 1995-2002 by Cisco Systems advertisement version: 1
Now, let's log in to the discovered neighbor devices:
cisco2503#sh cdp neighbor detail ------------------------- Device ID: cisco-2611b.core.arhont.com Entry address(es): IP address: 192.168.254.254 Platform: cisco 2611, Capabilities: Router Interface: Serial1, Port ID (outgoing port): Serial0/0 Holdtime: 168 sec Version: Cisco Internetwork Operating System Software IOS (tm) C2600 Software (C2600-IK9O3S3-M), Version 12.3(6), RELEASE SOFTWARE (fc3) Copyright (c) 1986-2004 by cisco Systems, Inc. Compiled Wed 11-Feb-04 19:24 by kellythw Gromozeka (enable) show cdp neighbors detail Port (Our Port): 4/11 Device-ID: cisco-2611b.core.arhont.com Device Addresses: IP Address: 192.168.254.254 Holdtime: 162 sec Capabilities: ROUTER Version: Cisco Internetwork Operating System Software IOS (tm) C2600 Software (C2600-IK9O3S3-M), Version 12.3(6), RELEASE SOFTWARE (fc3) Copyright (c) 1986-2004 by cisco Systems, Inc. Compiled Wed 11-Feb-04 19:24 by kellythw Platform: cisco 2611 Port-ID (Port on Neighbor's Device): Ethernet0/0
All this information flies across the network in plaintext, and you don't need to log in to a router or switch and execute the commands shown above to see it. The output of the show cdp and show cdp interface commands demonstrates the default send-time and CDP cache holdtime values and shows that these two parameters can be adjusted on a per-interface basis. Note that while cisco-2611b can see both cisco2503 and Gromozeka, cisco2503 and Gromozeka do not see each other. From the output above, it is clear that cisco2503 and cisco-2611b are connected via a serial cable (encapsulation Point-to-Point Protocol, or PPP), and there is no direct link between cisco2503 and Gro-mozeka. Also, the 192.168.254.254 IP address advertised by cisco-2611b does not really fit into the IP ranges used on the network. Indeed, it's a loopback interface of a designated Open Shortest Path First (OSPF) router.
How you sniff-out CDP is entirely your choice. All common sniffers can dissect and present CDP frames. Figure 5-1 shows a CDP frame dissected by Ethereal and containing a wealth of informationfor example, the management VLAN number being changed from the default 1 to 9 .
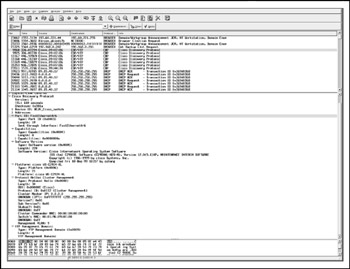
Figure 5-1: A CDP frame caught by Ethereal
Very often, CDP traffic is in the air on the completely unprotected wireless networks. Thus, Kismet, a war-drivers' all-time favorite, has a CDP dissector and stores CDP data in plain ASCII in .cisco files. One would expect that the majority of CDP traffic on open wireless networks would originate from Cisco Aironet access points; however, we have seen all types of Cisco devices advertising themselves across the streets . Here is an entry for a VoIP phone caught somewhere in central London as we were war-driving in 2003:
Network: "Wireless" BSSID: "00:30:AB:0A:F0:B7" CDP Broadcast Device 1 Device ID: SEP003094C44EEA Capability: Level 2 switching Interface: Port 1 IP : 0.0.0.0 Platform: Cisco IP Phone 7960 Software: P00303010107
Max Moser had also planned to include a CDP sniffer in his Wellenreiter, but he de-cided to release it as a standalone tool called cdpsniffer.pl . The only variable it takes is the name of an interface on which you want to sniff for CDP frames.
So if CDP gives away a lot of useful information for the attackers , why not turn it off by default? What is CDP good for? One case of a specific CDP use is for on-demand rout-ing (ODR), enabled by a router odr command. When multiple hub routers, many stub networks, or asynchronous connections exist between hubs and spokes , statically config-uring all stub networks on the hub routers becomes daunting. ODR allows easy install of IP stub networks with the "hubs" dynamically maintaining routes to the stub networks connected. To do that, ODR uses CDP updates to propagate its routing information. Thus, if you want to use ODR, you have to enable CDP.
Of course, CDP is a network monitoring protocol. As such, it is used by network management software suites such as CiscoWorks, IBM Tivoli NetView, or Netdisco (a nice, free, and open source network management tool). To enjoy the full functionality of these suites, running CDP is necessary. And in many cases, various show cdp com-mands can greatly assist system administrators in troubleshooting problems on their networks. It deserves to be mentioned that CDP version 2 (CDPv2) is far more helpful than the original CDPv1. It supports more rapid error tracking, covers unmatched switch port duplex states ( %CDP-4-DUPLEXMISMATCH: Full/half-duplex mismatch de-tected o1 error), and reports unmatched VLAN ID errors. Network management applications learn CDP information using SNMP with the CDP Management Informa-tion Base (CISCO-CDP-MIB). Since CISCO-CDP-MIB allows retrieval of CDP information via SNMP many hops away from the enumerated host, it can come in very handy for a remote attacker, providing that a read-only (RO) SNMP community is known.
In the next example, we use cdppoll.pl , written by user fingers ( http://www.perlmonks.thepen.com/80979.html ), to collect neighbor information from the small test network pre-viously used to show CDP capabilities:
arhontus# perl cdppoll.pl 192.168.66.202 community: public CDP Neighbor Details for 192.168.66.202 ----------------------------------------------------------------------- Neighbor IP Name Interface Type ----------------------------------------------------------------------- 192.168.77.250 002660741(Gromozeka) 4/11 WS-C5000 192.168.30.50 cisco2503 Serial1 cisco 2500 CDP Neighbor Details for 192.168.77.250 ----------------------------------------------------------------------- Neighbor IP Name Interface Type ----------------------------------------------------------------------- 192.168.254.254 cisco-2611b.core.arhont.com Ethernet0/0 cisco 2611 <snip>
All three Cisco devices on the network can be seen remotely; again the output from Gro-mozeka shows the loopback and not the Ethernet (192.168.66.202) address of Cisco 2611.
Countermeasures Against CDP and Other Cisco Proprietary Protocols-Based Enumeration
| Countermeasure | The first thing you would like to do is to assure that no unauthorized sniffers are access-ing your network. We already discussed some means of searching for unauthorized promiscuous mode interfaces on LANs in Chapter 4 and suggest you review these recommendations. However, you can never be sure that no one is sniffing. There are anti-antisniffers to counter antisniffers, then there are anti-anti-antisniffers, and so onthe arms race continues. Thus, the only reliable countermeasure to analyzing Cisco-specific protocols with nefarious aims is not to use these protocols. In the case of CDP, use these commands to turn it off completely: cisco-2611b#conf t cisco-2611b(config)#no cdp run |
However, for some described cases you do want to run CDP. If you need it for trouble-shooting and the connectivity on the network is not lost, enable CDP only for the troubleshooting period. If you use ODR or network management applications that em-ploy CDP, use this protocol on a per-interface basis.
To turn off CDP for the interface on which it is not needed, go to that interface configuration mode and execute the no cdp enable command. On a CatOS switch, turning off global and interface CDP is done via a set cdp disable command:
Gromozeka (enable) set cdp disable Usage: set cdp disable all set cdp disable <mod/ports...> (An example of mod/ports is 2/1-12,3/5-12)
There is no point to keeping CDP running on an interface not connected to other devices that understand CDP. And, of course, no CDP frames should ever leak away from the LAN and be sniffable on the "dirty" side of your gateway.
Passive Enumeration and Fingerprinting of Cisco Devices
| Attack |
|
Since we are trying to be as stealthy as we can and avoid sending unnecessary pack-ets to the target, the next logical step after sniffing for CDP and other Cisco-specific protocols is passive fingerprinting . Passive fingerprinting is a methodology of discovering remote operating systems via analyzing the peculiarities of packets sent by those sys-tems. You can perform passive fingerprinting when a remote host connects to your machine or when you are able to sniff the media linking you to the host of interest. A variety of techniques includes semi-active fingerprinting , in which a single packet is sent to the enumerated host and the reply is analyzed . The ST-divine tool (available on the web site for the book at http://www.hackingexposedcisco.com ) performs semi-active finger-printing automatically. Of course, you can also run any passive fingerprinting tool of your choice and then Telnet or Secure Shell Protocol (SSH) to the target host and watch the tool analyze the received response. This is less intrusive than a classical portscan and demonstrates that passive fingerprinting tools can be just as useful outside the realm of a LAN you can sniff.
We have evaluated the following passive fingerprinting tools against the Cisco hosts in the testing lab:
-
p0f
-
discopads
-
passmon
-
passifist
-
passfing
-
ST-divine
We didn't use Siphon (the first publicly released passive fingerprinting utility) and Siphon-based Windows tools, since they haven't been updated for a very long time and are unlikely to show more recent versions of operational systems run by Cisco hosts used to write this chapter.
Our verdict is that, unfortunately , current passive fingerprinting techniques are not very reliable when used to discover and fingerprint Cisco devices. In fact, the only host reliably discovered to run Cisco IOS was the Aironet 1200 access point. At the same time, none of the tools tested could correctly identify 2503 and 2611 Cisco routers, 5005 and 2950 Catalyst switches, 515E and 501 PIX firewalls, and 3020 Cisco VPN concentrators . We'll illustrate it with a few examples.
In the following example, the device discovered as a Cisco 7200 router or Catalyst 3500 switch is, in fact, a Cisco Aironet 1200 access point on the same subnet. The sup-posed-to-be SunOS machine is a 5005 Catalyst switch merely one hop away from the machine running p0f.
arhontus# ./p0f -i eth1 -M -V -S -v -p -C 192.168.77.235:54273 - Cisco 7200, Catalyst 3500, et [tos 192] Signature: [4128:255:0:44:M1460:Z] -> 192.168.77.5:22 (distance 0, link: ethernet/modem) 192.168.77.250:1024 - SunOS 4.1.x Signature: [4096:30:0:44:M1460:.] -> 192.168.77.5:23 (distance 34, link: ethernet/modem)
Next, the only discovered Cisco host is the access point. Two other hosts with "un-known" signatures are Cisco 2503 and 2611 routers:
arhontus# ./disco -i eth0 -f -A -v Disco v1.2 192.168. 66.202: 4128:254:1448:1:-1:1:1:60:A 192.168. 30. 50: 2144:253:536:0:-1:0:0:44:A 192.168. 77.235: Cisco IOS (A)
In the next example, the Perl tool has discovered the access point, but the version of IOS shown is incorrect:
arhontus# perl passivefingerprint.pl PACKET 192.168.77.235:23 -> 192.168.77.5:41789 SRC(Cisco 12.0 [2514]) TOS(192) TTL(255) DF(n) WINDOW(4078) PACKET 192.168.77.235:23 -> 192.168.77.5:41789 SRC(Cisco 12.0 [2514])
Our observations discredit neither the available passive fingerprinting methodologies nor the tools implementing them. After all, the tools we evaluated performed very well against various Linux machines to determine the correct (or nearly correct) kernel ver-sions. However, more effort is needed to create up-to-date passive fingerprinting signature databases reflecting the behavior of IOS, CatOS, PIX OS hosts, and Cisco VPN concentrators.
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 117