Running the Example
To demonstrate the TDI connection, first start GhostTracker (GT.exe). GhostTracker provides a simple list control that is filled with the IP addresses of connecting clients. Because c:\config32 is set to the IP address of the machine running GhostTracker, Ghost will open a TDI connection to GhostTracker and send a connection string to the controller via SendToRemoteController. All you need to do to initiate this connection is start Ghost using the same “SCMLoader” and “net start MyDeviceDriver” commands you have been using throughout this book. Figure 6-2 shows a typical rootkit environment.
Figure 6-2
If you have two or more machines, you can put GhostTracker on one machine and Ghost on the others. Just be sure to add the IP address of the machine running GhostTracker to the config32 file(s) on the other machine(s). This will give you an idea of how rootkits are used in the field. GhostTracker is shown in Figure 6-3.
Figure 6-3
Once the list box in GhostTracker begins to fill with client connections, you can double-click on any IP address to spawn a remote control panel for that client. However, don’t look for much more from this example. GhostTracker is a simple mock-up with no operational capability. The GhostTracker control panel is shown in Figure 6-4.
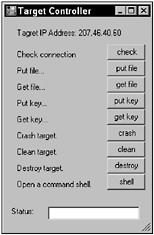
Figure 6-4
EAN: 2147483647
Pages: 229