OSI REFERENCE MODEL
The International Organization for Standardization (ISO), an international engineering organization based in Paris, first published the Open Systems Interconnection (OSI) reference model in 1978. This seven-layer model has become the standard for designing communication methods among network devices, and was the template used to design the Internet Protocol (IP).
The goal of the OSI reference model was to promote interoperability. Interoperability means the ability for otherwise incompatible systems to operate together in such a way that they can successfully perform common tasks. A good example of interoperability would be an Ethernet LAN transparently exchanging messages with an IBM Token Ring LAN.
The Seven-Layer Stack
The OSI model divides networks into seven functional layers, and thus is often called the seven-layer stack. Each layer defines a function or set of functions performed when data is transferred between applications across the network. Whether the network protocol is IP, Novell NetWare, or AppleTalk, if it adheres to the OSI model, more or less the same rules are applied at each of the seven layers. The seven layers are outlined in Figure 2-1.
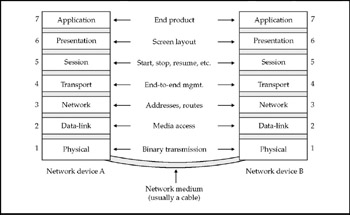
Figure 2-1: Each OSI layer runs protocols to manage connections between devices
The Layers
As depicted in Figure 2-1, each layer is a protocol for communications between linked devices. Concerning network operations, the key thing to understand is that each layer on each device talks to its counterpart device to manage a particular aspect of the network connection. Concerning interoperability, the key is the fixed interface sitting between each layer. Abstract layering reduces what would otherwise be daunting complexity.
-
Layer 1, the physical layer Controls the transport medium by defining the electrical and mechanical characteristics carrying the data signal. Examples include twisted-pair cabling, fiber-optic cabling, coaxial cable, and serial lines.
-
Layer 2, the data-link layer Controls access to the network and ensures the reliable transfer of frames across the network. The best known data-link specification is Ethernet's Carrier Sense Multiple Access with Collision Detection. Token Ring and Fiber Distributed Data Interface (FDDI) adhere to the token-passing data-link architecture.
-
Layer 3, the network layer Manages the movement of data between different networks. Protocols at this layer are responsible for finding the device for which the data is destined. Examples include IP, Internetwork Packet Exchange (IPX), and AppleTalk.
-
Layer 4, the transport layer Ensures that data reaches its destination intact and in the proper order. The Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) operate at this layer.
-
Layer 5, the session layer Establishes and terminates connections and arranges sessions between two computers. Example session layer protocols include Remote Procedure Call (RPC) and the Lightweight Directory Access Protocol (LDAP).
-
Layer 6, the presentation layer Formats data for screen display or printing. Examples of presentation layer protocols include the Lightweight Presentation Protocol (LPP) and NetBIOS.
-
Layer 7, the application layer Contains protocols used to perform useful tasks over a network. Examples of network application protocols include the Simple Mail Transfer Protocol (SMTP) for e-mail, the Hypertext Transfer Protocol (HTTP) for Web browsers and servers, Telnet for remote terminal sessions, and hundreds of others.
Layer 7 network applications are the reason the lower six layers exist. Many of these protocols saw their first use in UNIX systems, given that the UNIX operating system developed in parallel with the Internet.
| Note | Don't be misled by the name "application layer." This layer runs network applications, not applications software, such as spreadsheets or inventory. Network applications include e-mail, Web browsing (HTTP), FTP, and other useful network tasks. |
Peer Layers Form Protocol-Independent Virtual Links
Each layer in the stack relies on the layers above and below it to operate, yet each operates independently of the others, as if it were having an exclusive conversation with its counterpart layer on the other computer. Each layer on the device is said to have established a virtual link with the same layer on the other device. With all seven virtual links running, a network connection is established, and the two devices are talking as if they were wired directly together.
For example, in Figure 2-2 the sending computer, the Wintel PC on the left (Host A), processes downward through the stack to send a message, and the IBM mainframe (Host B) receives the message by processing it upward through its stack to understand the data-an FTP download request, in this example. The computers then reverse the process by working through their stacks the other way, this time, for the IBM mainframe to download a file to the Wintel PC through the FTP application.
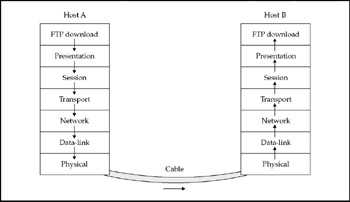
Figure 2-2: Messages are processed up and down through the seven-layer stack
In Figure 2-2, you begin to see how the Internet was able to interconnect the world's computers. Because the layers are abstracted and operate independently of one another, the FTP application can successfully run over different implementations of the OSI model-in this example, Ethernet and Token Ring. You can see that the FTP application doesn't care about the incompatibilities inherent between Windows XP and IBM mainframes, or even those between the Ethernet and Token Ring network technologies. Its only concern is whether the connected devices are talking FTP in compliance with OSI rules.
OSI Implementation by Layer
Although the seven-layer stack is expressed in vertical terms, looking at things horizontally might help you understand how it works. This is because as a message is processed through the stack, its horizontal length changes.
The first three layers handle the network application being run (application layer), data representation formats (presentation layer), and connection logistics (session layer). These first three layers represent very little of the message. For example, which application to run is defined by a port number-the HTTP HTML Web page application is identified by port number 80.
| Note | The name "port number" was an unfortunate choice by the IETF (Internet Engineering Task Force) engineers. It takes a while to get used to the fact that an IP port number refers to a software type, not a hardware port. On a related note, the term "socket" is an IP address paired with a port number. |

At the transport layer, the message gets wider. Tasks performed here include making sure the receiver knows the message is coming, ensuring that the receiver won't be overwhelmed with too many packets at a time, making sure that packets sent were indeed received, and retransmitting packets that were dropped. Transport protocols include the Transmission Control Protocol (TCP) and User Datagram Protocol in the TCP/IP suite and the Sequenced Packet Exchange (SPX) layer of the NetWare IPX/SPX suite.

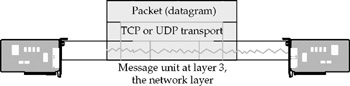
At the network layer, the message gets a bit wider and becomes a packet (also called a datagram). Each packet's header has a logical (not physical) network address that can be used to route the message through the internetwork. Network layer protocols include the IP portion of the TCP/IP protocol suite and the IPX layer of the Novell NetWare IPX/SPX protocol suite, among others.
At the data-link layer, the binary information is read and encased into a format called a frame. The precise format for a frame is specified by the network protocol on which the NIC is operating-Ethernet or Token Ring, for example. Each frame's header contains so-called media access control (MAC) addresses, which are unique identifiers that act as a kind of serial number for hardware devices.
At the physical level, a message is a series of pulses. The device works to encode or decode the pulses into binary 0's or 1's to begin sorting out discrete message units. This signal processing is done in hardware on the network interface card, not in software.
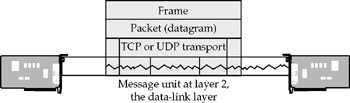
Once all the message-handling protocol information has been stripped away, you're left with payload data. There are many individual message units within a transmission. A network connection is made using a stream of packets, and each individual packet's data cargo contributes to the complete data file the connection needs-a Web page download, for example.
Payload data differs by application. For example, a Telnet session will send tiny data files to indicate a keystroke or a carriage return, which may be all contained in a packet or two. At the opposite extreme, an FTP file transfer may send millions of bytes of data spread across thousands of packets.
EAN: 2147483647
Pages: 102