PUBLIC AGENCIES AND YOU
| < Day Day Up > |
Private Lives, Public InformationThe Annoyance:I thought I led a fairly private life. Then I got into a dispute with a business partner, who decided to tweak me by sending me a dossier he'd compiled about me the names and birthdates of my children, some quiet property investments I'd made, and the details of my very messy divorce. Is this legal? The Fix:It is. Not only is all of that public information, but in most states it would be illegal to conceal this information from the general public. Birth and death, marriage and divorce, home and business ownership, nearly every major rite of passage is considered part of the public record in most states. Until fairly recently, this information was hard to get at. Most of these records were kept in dusty credenzas in the bowels of county courthouses; anyone who wanted a look had to ask to see your paper file, and if they wanted to take the record home they had to make photocopies or scribble down the information by hand. Now, thanks to the wonder of the Web, many of these records are available easily and often for a modest fee online (see Table 6-1). Public records serve a useful purpose. It's helpful to know who owns the house you're thinking of buying, or whether your ex-spouse is hiding assets, or if a convicted sex offender has moved into your neighborhood. But computers allow you to do things that the original authors of public records statutes surely never dreamed of, such as instantly looking up
every piece of property owned by a particular person, or finding every legal dispute involving a particular business. In the age of the Internet, everyone is a gumshoe. Some local governments are taking steps to limit online access to this information. Last July, Douglas County in Kansas removed the ability to search across property records by an individual's name, citing citizen complaints about potential privacy violations. Officials in Nassau County, New York, did something similar in 2002. You might try approaching local county officials and see if they'd consider restricting the ability to search for records online. Private data brokers also mine public records databases and sell the information they find there. You may be able to convince some data brokers to stop selling information about you they've culled from public databases (see Chapter 3, "Fend off Cyber Stalkers"), but this won't remove the data from the public record or prevent state or county governments from sharing it with the world. (The Privacy Rights Clearinghouse publishes a partial list of information brokers at http://www.privacyrights.org/ar/infobrokers.htm).
Your best recourse is to understand what information is available about you and try to limit the potential for harm (see Chapter 4, "Be Your Own Gumshoe"). If, for example, the public record includes transcripts from a family court case or some other potentially embarrassing legal proceeding, you might be able to petition the court to seal the record. At the very least, you won't be surprised when the details show up in your inbox. Keep the USPS From Selling Your AddressThe Annoyance:I recently moved across country. To make sure that all my magazine subscriptions and personal mail find me when I arrived, I filled out a US Postal Service Change of Address form. Now I'm getting even more junk mail than before. Am I being paranoid, or is there a connection? The Fix:Connect away. Fill out the Postal Service's National Change of Address (NCOA) form and you're just begging for junk mail. According to the USPS privacy policy, if you file a permanent change of address (Form 3575), anybody who has your old address is entitled to obtain your new one. The Postal Service uses about 20 private contractors to process 40 million changes of address each year. Those contractors then sell your address to thousands of direct mail companies, who proceed to fill your mailbox with dead trees. One partial solution is to mark your change of address as temporary; you use the same form, you just indicate a date when you want mail forwarding to stop (see Figure 6-1). Mail will be forwarded for up to 12 months, but your new address won't be added to the NCOA rolls that are shared with marketers. Most of the junk mail won't be forwarded, while some types of mail (like periodicals), may only be forwarded three times. Once the temporary change expires, you'll need to directly contact those magazines and people you owe bills to and give them your new, permanent address. Another way to reduce the junk is to use the Direct Marketing Association's Mail Preference Service (http://www.dmaconsumers.org/cgi/offmailinglist). This will eventually reduce but not entirely eliminate the crap you receive. annoyances 6-1. Moving? You can file a change of address at USPS.gov, but be sure to use the Temporary Move option unless you want your junk mail to follow you.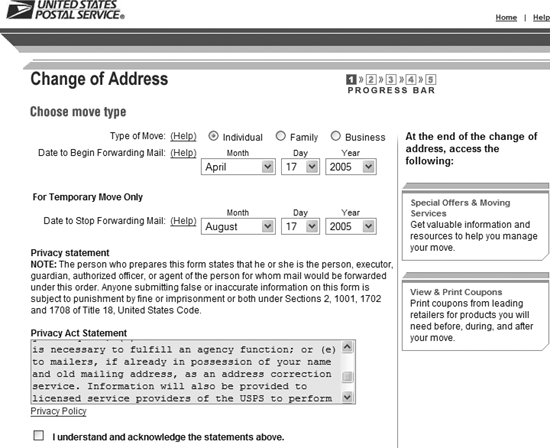
Take Leave of Your CensusThe Annoyance:I got a U.S. census form in the mail that asked me a bunch of highly intrusive questions from my national ancestry and level of education, to how much money I make and whether I have flush toilets in my home. Do I have to answer these questions? And if I do, how safe are my answers? The Fix:Gotta answer? Yep. Safe? More or less. The census was originally created to gather information about the U.S. population for the purpose of creating new Congressional districts, which of course, are based on population. Over the years, however, it's expanded to serve a wide range of other uses, such as calculating how to distribute funds for government programs like Medicaid or where to build future roads and schools. The data is also used extensively by businesses for example, Starbucks uses census data to determine where to plant its next coffee franchise. Not surprisingly, the amount of information the Census Bureau gathers has grown dramatically. And instead of gathering this data once every 10 years, the Bureau now collects data from different households every month. In 2000, U.S. citizens received either a short form survey (7 questions) or a long form (53 questions). Starting in 2005, the Bureau will distribute the long form under a new name (the American Community Survey) to 250,000 U.S. households each month (see Figure 6-2). The short form will continue to be mailed to every household every 10 years and will be used solely to determine Congressional representation. The problem? Census data has occasionally been abused. It played a pivotal role in the identification and internment of Japanese Americans during World War II. More recently, the Department of Homeland Security (DHS) requested information from the 2000 Census regarding the makeup of Arab populations in the U.S. Bureau spokesman Stephen Buckner says the DHS's purpose was benign (the agency wanted to know what languages to use on signs at certain airports), and that this data was already publicly available on the bureau's web site. Still, it prompted the Census Bureau to change its policies; Bureau staff must now get the thumbs up from a higher-up before they release potentially sensitive information. annoyances 6-2. Do you heat your home with kerosene? Are you a high school dropout? Do you have trouble dressing yourself? These are some of the questions on the new U.S. Census long form. Approximately one in four households will receive this form in the mail over the next 10 years.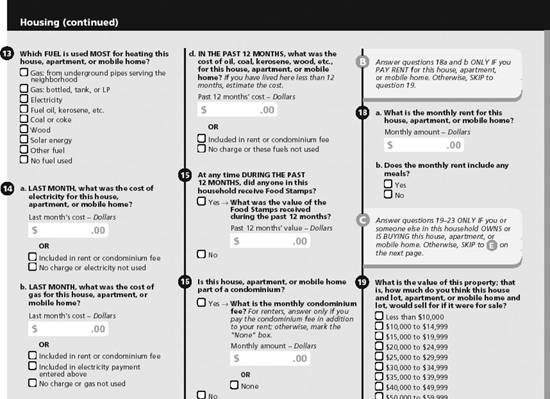 By law, census information is supposed to remain confidential; the Census Bureau does not reveal the names of anyone who fills out a form. Yet marketers combine census data with data gathered from other sources to identify you a practice known as re-identification, which is perfectly legal. Carnegie Mellon computer scientist Latanya Sweeney has found that 87 percent of the U.S. population can be uniquely identified using just three bits of information (date of birth, gender, and ZIP code). At the very least, private firms can take small units of census data and extrapolate a great amount of detail about your income and interests, if not your actual identity. (For more information on census data and privacy, see EPIC's page at http://www.epic.org/privacy/census/.) Unfortunately, filling out either the community survey or the standard short form is not optional. If you don't return the ACS form you'll get a follow-up phone call, and one in three non-responding households will find a Census Bureau employee on their doorstep. Even leaving some items blank can subject you to a $100 fine, though Bucker says the bureau doesn't usually press the issue. Despite the penalty, one out of three households never mailed back the 2000 census (Buckner says the new ACS has response rates above 97 percent). If the survey questions truly bug you, a hundred bucks is a cheap way to tell the Census Bureau to shove off.
Taking License with Your LicenseThe Annoyance:I've heard that my DMV records including photos can be obtained by anyone for practically nothing. Is this legal? The Fix:Not anymore. The Drivers Protection Privacy Act, a part of the Violent Crime Control and Law Enforcement Act of 1994, made it illegal for DMVs to provide public access to its records, though law enforcement, insurance firms, subpoena servers, and businesses doing ID checks may still access these records in most states. (Whether a business's request is truly legitimate or anyone at the DMV bothers to check is another question.) The law was inspired by the 1989 murder of Rebecca Schaeffer, an actress killed by a stalker who obtained her home address through her California DMV records. Later amendments to the law allowed states to sell driver data to marketers, provided they obtain your permission first. Some states, such as Arkansas and Wyoming, are stricter, limiting access to your DMV records to you, government entities, or anyone who has your written permission. (For a directory of state DMV web sites, see http://www.dmv-department-of-motor-vehicles.com/.) Still, privacy advocate Robert Gellman notes such laws may be cold comfort for anyone who's been driving for more than ten years. Because so many states sold motor vehicle records prior to the law's passage, odds are good your information was purchased by marketers years ago. The Taxman ComethThe Annoyance:Yikes! I'm about to be audited by the Internal Revenue Service! Is there still time for me to shave my head, change my name, and move to Bolivia? The Fix:A tax audit can be an incredibly invasive experience, but leaving the country or going underground probably isn't the best strategy for dealing with it. If you're unlucky enough to be audited, there are some things you can do to protect your privacy, says Frederick W. Daily, author of several books on taxpayer rights, including Stand Up to the IRS and Tax Savvy for Small Business (both from Nolo Press):
For more information, visit the IRS's Taxpayer Rights page at http://www.irs.gov/advocate/article/0,,id=98206,00.html.
| ||||||||||||||||||||||||||||||
| < Day Day Up > |