In Microsoft Systems Management Server (SMS), an object that defines software to the SMS system. Packages store information about software so that various components of the software can be identified as a group. You use SMS to install a package on client computers, share the package so that it can be run from network servers, and maintain inventory information about the package. You can create packages for all types of software, including Microsoft, third-party, and in-house applications; data files; batch files; and scripts.
How It Works
A package contains a definition of the files that make up the software, plus other configuration and identification information. You create packages using the Systems Management Server Administrator program. Packages are stored in the SMS database at your site and at all subsites. After you create a package, you must also create a job that can be used to install the package on clients or share the package on servers.
You use a package server—a type of server in an SMS implementation—to install and maintain packages. There are two kinds of package servers:
Source servers, which contain the original source files for software to be distributed
Distribution servers, which store and distribute the package files
TIP
If you want to perform software inventory, you need not explicitly create a job for this purpose. When you define the inventory properties for a package, SMS automatically creates a system job to update the SMS inventory components. This allows SMS to maintain inventory information on the package.
The fundamental unit of information transmitted over a network or over a digital communication link. Packets usually contain a header with control information about the packet type, source address, and destination address. They can also contain error-checking information. Packets have a logical structure based on the protocol used, but the general structure of a packet includes a header followed by a payload (data) and an optional trailer (footer). Packets can also have different sizes and structures depending on the underlying network architecture. A packet might also be called a datagram, a frame, or a cell.
NOTE
From the perspective of the Open Systems Interconnection (OSI) reference model, the terms “packet” and “frame” have precise definitions. A packet is an electronic envelope containing information formed in one of the layers from layer 3 through layer 7 of the OSI model. A frame is an electronic envelope of information that includes the packet as well as other information from all seven layers of the OSI model.
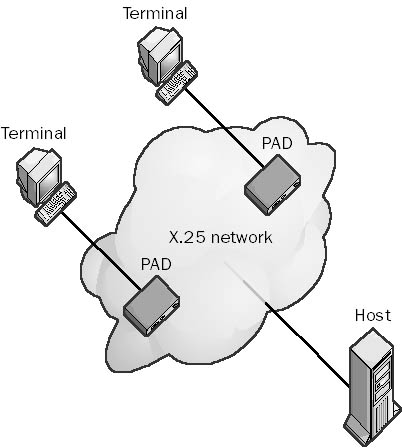
A telecommunications device that breaks a data stream into individual packets and formats the packet headers for asynchronous transmission over an X.25 network. It also accepts packets from the network and translates them into a data stream. Packet assembler/disassemblers (PADs) are a form of data communications equipment (DCE) for connecting asynchronous data terminal equipment (DTE) such as computers and dumb terminals to the X.25 packet-switching service.

Graphic P-1. Packet assembler/disassembler (PAD).
How It Works
When one computer on an X.25 network wants to communicate with another computer in a remote location, the first computer sends a signal to its attached PAD requesting a connection to the remote computer. The remote computer responds by either accepting the request and initiating full-duplex communication or rejecting the request. Either computer can terminate the link at any time. Note that this communication link is for data only—X.25 does not support voice transmission. Note also that PADs are DCEs, and even though they are located at the customer premises, they are considered nodes on the X.25 network.
The PAD’s function is simply to assemble data such as strings of characters into packets to transmit over the X.25 network to the remote host and to disassemble packets that are received. PADs are often used for providing remote access via dumb terminals over X.25 to mainframe or minicomputer hosts. In this scenario, the terminals require PADs but the mainframe hosts do not—they are directly connected to the X.25 network. To configure the PAD, the administrator must specify a number of PAD parameters such as echo control, data forwarding, break signals, line folding, and binary speed. The PAD parameters (usually 22 for each terminal that the PAD services) are defined by an International Telecommunication Union (ITU) protocol called X.3. Communication between terminals and PADs is governed by the protocol X.28, and communication between the PAD and the remote host is governed by X.29.
PADs come in different configurations. Some PADs support eight or more asynchronous DTE connections and have multiple DCE interfaces for maximum configurability. Typically, you connect your asynchronous hosts (computers) to the PAD using RJ-45 connectors on twisted-pair cabling. The PAD then connects to a Channel Service Unit/Data Service Unit (CSU/DSU), which interfaces with the X.25 connection using a serial interface such as RS-232 or V.35.
NOTE
The Remote Access Service (RAS) on Microsoft Windows NT and Windows 2000 supports PADs and other ways of connecting to X.25 networks, such as X.25 smart cards and special modems for dialing up X.25 carriers such as SprintNet and Infonet.
TIP
Some PADs support both X.25 and frame relay packet-switching services and can be used to ease the migration path from X.25 to frame relay.
The process of controlling the flow of packets based on packet attributes such as source address, destination address, type, length, and port number.
How It Works
Many routers and proxy servers use some form of packet filtering that provides firewall capabilities for protecting the network from unauthorized traffic. Administrators can create rules for filtering out unwanted packets and can arrange these rules in the most efficient order. A packet that passes all the rules is allowed through, while a packet that violates any rule is dropped.
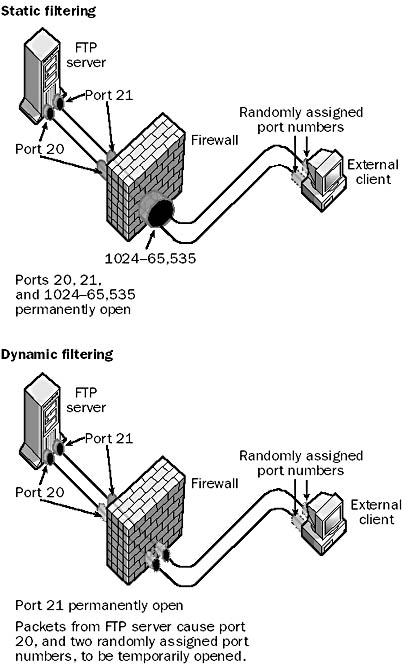
Packet filtering can be implemented on routers and firewall devices in two ways: static filtering and dynamic filtering.
Static packet filtering provides limited security by configuring selected ports as either permanently open or permanently closed. For example, to deny outside packets access to a company intranet server on port 80 (the standard port number for the Hypertext Transfer Protocol, or HTTP) you could configure the router or firewall to block all incoming packets directed toward port 80.
Dynamic packet filtering provides enhanced security by allowing selected ports to be opened at the start of a legitimate session and then closed at the end of the session to secure the port against attempts at unauthorized access. This is particularly useful for protocols that allocate ports dynamically—for example, with the File Transfer Protocol (FTP). If you want to grant outside users secure access to an FTP server behind the firewall (within the corporate network), you need to consider the following:
Port 21 (the FTP control port) needs to be left permanently open so that the FTP server can “listen” for connection attempts from outside clients. A static filtering rule can accomplish this.
Port 20 (the FTP data port) needs to be opened only when data will be uploaded to or downloaded from the FTP server. With static filtering this port would have to be configured as permanently open, which could provide a door for hacking attempts. Dynamic filtering allows this port to be opened at the start of an FTP session and then closed at the end of the session.
In order to establish an FTP connection with the client, the FTP server randomly assigns two port numbers in the range 1024 through 65,535 to the client, one for the control connection and one to transfer data. Because these ports are assigned randomly, there is no way to predict which ports above 1024 must be able to be opened by the firewall. With static filtering, you would therefore have to leave all ports above 1024 permanently open if you wanted to allow FTP access through the firewall, which would be a real security risk. With dynamic filtering, however, you can configure rules on the firewall that will read the packets issued by the server, dynamically open the two randomly assigned ports to allow a session to be opened, monitor the flow of packets to ensure that no attempt is made to hijack the session by an unauthorized user, and close the randomly assigned ports when the FTP session ends.
Graphic P-2. Packet filtering.
TIP
Microsoft Proxy Server includes a number of predefined filters that you can use to configure exceptions for common protocols. You can use these to quickly configure Proxy Server for securing your network from the Internet.
Packet filtering on a typical router can cause a performance hit of about 30 percent on the router’s ability to handle network traffic. This suggests that instead of using a packet-filtering router for a firewall, you should consider installing proper firewall software such as Microsoft Proxy Server on a dedicated server. Proxy Server includes dynamic packet filtering among its security features. If packet filtering is enabled, all incoming and outgoing packets are rejected unless an exception is explicitly created that allows them to pass. Packet filters can be enabled on Proxy Server only if the machine has an external network interface, such as one connected to a distrusted network (the Internet, for example).
NOTE
Some routers and firewalls can actually ping the source address of each packet to ensure that addresses local to the company network are coming from inside the network and are not being spoofed by a hacker outside the network.
Proxy Server also supports domain filters for allowing or denying access to World Wide Web (WWW) or FTP services based on the source IP address or Domain Name System (DNS) domain name. Proxy Server can issue alerts to inform you when packets are rejected or illegal packets are detected. It will also keep a log of alerts that occur for analysis and record keeping.
The process of a networking component accepting a packet and transmitting it to its destination. For example, a router receives packets from hosts on one attached network and forwards them to hosts on another attached network or to another router for further forwarding. How a packet is forwarded is based on a comparison of the packet’s destination address with the routing table stored in the router. Each act of forwarding performed by a router is called a hop across the internetwork.
The process by which a networking or telecommunications device accepts a packet and switches it to a telecommunications device that will take it closer to its destination. Packet switching allows data to be sent over the telecommunications network in short bursts or “packets” that contain sequence numbers so that they can be reassembled at the destination. Wide area network (WAN) devices called switches route packets from one point on a packet-switched network to another. Data within the same communication session might be routed over several different paths, depending on factors such as traffic congestion and switch availability.
Packet switching is the transmission method used for most computer networks because the data transported by these networks is fundamentally bursty in character and can tolerate latency (due to lost or dropped packets). In other words, the transmission bandwidth needed varies greatly in time, from relatively low traffic because of background services such as name resolution services, to periods of high bandwidth usage during activities such as file transfer. This contrasts with voice or video communication, in which a steady stream of information must be transmitted in order to maintain transmission quality and in which latency must remain minimized to preserve intelligibility.
The Internet is the prime example of a packet-switched network based on the TCP/IP protocol suite. A series of routers located at various points on the Internet’s backbone forward each packet received on the basis of destination address until the packet reaches its ultimate destination. TCP/IP is considered a connectionless packet-switching service because Transmission Control Protocol (TCP) connections are not kept open after data transmission is complete.
X.25 public data networks are another form of packet-switching service, in which packets (or more properly, frames) formatted with the High-level Data Link Control (HDLC) protocol are routed between different X.25 end stations using packet switches maintained by X.25 service providers. Unlike TCP/IP, X.25 is considered a connection-oriented packet-switching protocol because it is possible to establish permanent virtual circuits (PVCs) that keep the logical connection open even when no data is being sent. However, X.25 can be configured for connectionless communication by using switched virtual circuits (SVCs). An X.25 packet-switched network typically has a higher and more predictable latency (about 0.6 seconds between end stations) than a TCP/IP internetwork. This is primarily because X.25 packet switches use a store-and-forward mechanism to buffer data for transmission bursts, which introduces additional latency in communication. In addition, X.25 uses error checking between each node on the transmission path, while TCP/IP uses only end-to-end error checking.
Frame relay (also called fast packet switching) is another connection-oriented packet-switching service that gives better performance than X.25. It does this by switching packets immediately instead of using the store-and-forward mechanism of X.25 networks. Frame relay also eliminates flow control and error checking to speed up transmission. This is possible because frame relay networks use modern digital telephone lines, which are intrinsically much more reliable than the older analog phone lines on which much of the X.25 public network still depends. Frame relay supports only connection-oriented PVCs for its underlying switching architecture.
Finally, Asynchronous Transfer Mode (ATM) is another packet-switching service in which small fixed-length packets called cells are switched between points on a network.
NOTE
Packet switching is different from circuit switching, in which switches are configured in a fixed state for the duration of the session so that the route the data takes is fixed. A network that is circuit-switched requires a dedicated switched communication path for each communication even if its full bandwidth is not being used. In packet switching, bandwidth can be used when available for more efficient transmission. Circuit switching is generally used in telephone systems, while packet switching is used for computer networks. Digital cellular phone services are generally also circuit-switched, but Personal Communications Services (PCS) cellular systems are gradually being migrated to packet-switched networks for greater efficiency in data transmission.
Another difference between packet switching and circuit switching is that circuits must first be established before any data is sent, and this generally involves a certain amount of setup time. During this process, the request for a circuit connection must pass through the circuit-switched network, resources must be reserved for the connection, and a signal must be returned to the initiating station when the circuit is established and data transmission can begin. Circuit-switched networks are thus useful only when the duration of the data transmission is much longer than the setup time involved in establishing the circuit. With packet switching, data can be sent at the start of transmission, which is better suited to the bursty, irregular nature of short network transmissions over a computer network or WAN link.
See also packet-switching services
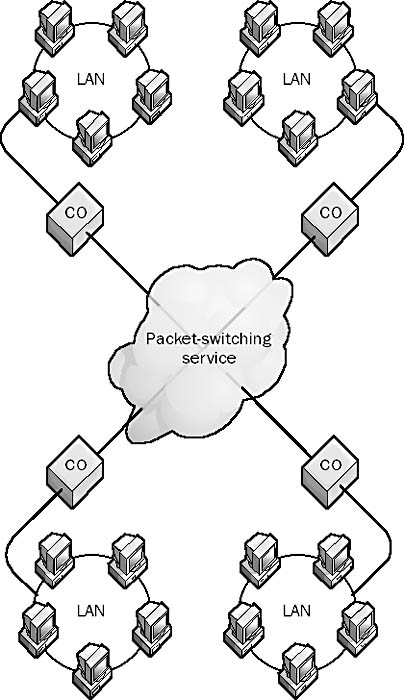
Telecommunications services provided by telcos and long distance carriers that route packets of data between local area networks (LANs) in diverse geographical locations to form a wide area network (WAN). Packet-switching services are used to connect multiple LANs into a point-to-multipoint configuration, usually called a multipoint WAN.
How It Works
A customer’s local network is typically connected through routers, bridges, frame relay access devices (FRADs), or other devices to a telco’s central office (CO). These devices either have built-in technology for connecting directly to packet-switching services or use intermediary devices located at the customer premises. Packet-switching devices take network frames and “package” them into packets suitable for the type of packet-switching service being used. These services can include frame relay, X.25, Asynchronous Transfer Mode (ATM), or Switched Multimegabit Data Services (SMDS) public or private packet-switched networks. If virtual private network (VPN) technologies are used, the public Internet can also be used as a packet-switching service for multipoint WAN connections.
Graphic P-3. Packet-switching services.
The packaging process varies with the particular service used, but it basically consists of breaking down network frames into relatively small individual packets of data and tagging the packets with the destination address of the remote node to which the packet is directed. Each end node (local network access device) connected to the cloud has a layer 2, or data-link layer, address that is known to every other end node. These addresses are used to route packet data between individual nodes on the WAN or to broadcast packets to all nodes when needed. Other information is also tagged onto the packets for error correction and other purposes, depending on the service used. The packets are usually small to lessen the load on the switching devices and to enable quick retransmission when transmission errors occur.
Packets are individually placed onto the carrier’s packet-switched network and switched from circuit to circuit until they reach their destination. Two packets forming part of the same network message might take entirely different routes to reach their destination node—it depends on the best route available at any given moment, as determined by the packet-switching services themselves. This is different from circuit-switched networks, in which all packets are sent over the same switched circuits for the duration of the connection. At the destination, the packets are reassembled into network frames and delivered to the remote network, where they are routed to their destination computers.
In networking diagrams, a public packet-switched network is typically depicted as a cloud because the details of the switches and connections are not of interest to the customer—they are the responsibility of the carrier or carriers providing the services.
Advantages of packet-switching services include the following:
Customers are not restricted to a single destination, as with point-to-point connections using leased lines.
Packets can be routed to any destination that supports similar services, so businesses are not tied to a particular carrier or telco.
Packet-switched networks have low latency and are suitable for hosting dedicated services such as company Web servers if the connection has sufficient bandwidth.
Customers usually pay monthly rates plus additional charges based on bandwidth use, which means that the primary charges are on a per-transaction basis. The less you use the service, the less you pay.
See also circuit-switched services, leased line
See packet assembler/disassembler (PAD)
A condition that occurs in Microsoft Windows operating systems when a process looks for application code or data in its working set and doesn’t find it, causing the Virtual Memory Manager to swap the necessary information into memory. Windows handles process information in 4-KB blocks called pages. This information can be stored as virtual memory that can be swapped from the hard disk to RAM. Pages are the basic building blocks of virtual memory in Windows and are managed by the Virtual Memory Manager.
See also virtual memory
See paging file
A file on a hard disk that Microsoft Windows NT or Windows 2000 uses to store program code that is temporarily not needed to maximize the functionality of the limited RAM on most machines. The paging file, sometimes referred to as the pagefile, is managed by the Virtual Memory Manager.
NOTE
The default size for the paging file on Windows NT is equal to the amount of installed RAM plus 12 MB. The default size for the paging file on Windows 2000 is equal to 1.5 times the amount of installed RAM. The minimum allowed paging file size is 2 MB. The default location of the paging file is %SystemRoot%\pagefile.sys
TIP
During installation of Windows NT and Windows 2000, the paging file is automatically installed on the partition that has the most free space. You achieve the best performance by moving the paging file to a separate hard drive with its own controller. Use the System utility in Control Panel to configure the paging file.
See also virtual memory
See Password Authentication Protocol (PAP)
A form of signal transmission that sends information 8 or more bits at a time over a cable. Parallel interfaces are used mainly to connect printers, hard drives, and other peripherals to computers.
How It Works
While a serial interface such as RS-232 transfers only 1 bit of data at a time, parallel interfaces typically transfer 8 bits (1 byte) of data at a time. A typical parallel interface for a computer uses a port that accepts a female DB25 connector. The parallel interface for a printer often uses a 36-pin Centronics connector.
For the DB25 connector, all 25 of the leads must be working for parallel transmission to function. In contrast, serial interfaces, which sometimes use DB25 connectors, require only three active leads to transmit data. The parallel 25-pin connector has 17 leads for carrying signals and 8 leads for grounding. Of the 17 leads, 8 are used for data bit signals, 5 for status signals, and 4 for handshaking. Typical throughput of a parallel interface is 16 KBps or 128 Kbps. Parallel communication is usually limited to cables of up to 6 meters, but devices can be used to boost signals for longer distances.
NOTE
A new type of parallel interface, conforming to the IEEE 1284 standard, supports bidirectional parallel communication at speeds of up to 1 MBps over distances of up to 10 meters. Parallel ports that support this standard are referred to as Enhanced Parallel Ports (EPPs) or Extended Capabilities Ports (ECPs).
See also serial transmission
A domain in a Microsoft Windows 2000 domain tree whose Domain Name System (DNS) name forms the basis of subdomains called child domains. For example, the parent domain named microsoft.com could include three child domains named dev.microsoft.com, marketing.microsoft.com, and support.microsoft.com. A two-way transitive trust exists between a parent domain and its associated child domains.
See also Active Directory, domain tree
Redundant information associated with any block of information that provides fault tolerance. Parity information calculated from the block of data can be used to reconstruct the block of data in the event of data loss or failure.
How It Works
RAID-5 volumes stripe data and parity information across a set of physical disks in such a way that for each stripe one disk contains the parity information while the other disks contain the data being stored. Each stripe uses a different (rotating) disk for storing its parity data.
The parity information for the stripe is created using an exclusive OR (Boolean XOR) operation on the data in the stripe. As a simple example, suppose that the block of binary data 10011 is to be written to a stripe on a RAID-5 volume that comprises six physical disks. Bit “1” is written to the first disk, bit “0” to the second disk, bit “0” to the third disk, and so on. The sixth, or parity, disk in the stripe contains the parity bit:
1 XOR 0 XOR 0 XOR 1 XOR 1 = 1
If the first disk fails so that the “1” bit stored on it is lost, the missing bit can be mathematically reconstructed using the remaining data bits and the parity bit for the stripe as follows:
? XOR (0 XOR 0 XOR 1 XOR 1) = 1 ? XOR 0 = 1 Therefore: ? = 1
A logical divider for organization information in Active Directory in Microsoft Windows 2000. Partitions divide Active Directory into separate sections and enable it to store large numbers of objects in a distributed directory over the network. They also allow Active Directory to scale millions of objects. A partition functions as a physical storage container for a portion of the directory data for an organization. Each domain’s directory information is stored in a separate partition and is identified using the distinguished name of the domain. The global catalog server can find an object in Active Directory by using the object’s distinguished name, which can be used to identify a replica of a partition that contains the object.
A portion of a physical disk that functions like a completely separate physical disk. Partitions allow physical disks to function as multiple separate storage units for isolating operating systems from applications data on a single-boot system or for isolating operating systems from one another on a multiboot system.
Disks can have two types of partitions:
Primary partitions: You can install a bootable operating system along with its associated file system on primary partitions. A physical disk can have up to four primary partitions.
Extended partitions: A series of logical drives can be created on extended partitions. You can create an extended partition on a disk to overcome the limitation of four primary partitions per disk.
NOTE
You can create partitions by using the fdisk command in MS-DOS and all versions of Microsoft Windows, by using Disk Administrator in Windows NT, or by using the Disk Management tool in Windows 2000. Using the fdisk command, you can create one primary partition and one extended partition. Disk Administrator can create up to four primary partitions or three primary and one extended partition. Disk Management can create partitions only on basic disks, not on dynamic disks.
A file in Microsoft Windows NT Service Pack 3 or later that allows administrators to increase password strength. The file establishes the following rules for password creation:
The minimum password length is six characters.
The password cannot contain a username or any part of the user’s full name.
The password must contain characters from at least three of the following categories:
Uppercase letters
Lowercase letters
Numbers
Non-alphanumeric characters, specifically:
. , ; : * & % !
TIP
To install passfilt.dll, first install Windows NT Service Pack 3 or later on your domain controller, which copies passfilt.dll into the %SystemRoot%\system32 directory. Then use registry editor to edit the following key:
HKEY_LOCAL_MACHINE System CurrentControlSet Control Lsa
and create or modify the following values:
Value: Notification Packages
Type: REG_MULTI_SZ
Data: passfilt.dll
See also Account policy
See patch panel
A terminator such as a resistor that absorbs signal energy and prevents signal bounce. Passive terminations are generally used in bus topology networks such as 10Base2 and 10Base5 networks of the Ethernet variety. Termination is not required in star topology networks because the central concentrator (hub) provides the termination for each signal path. Ring topology networks such as Token Ring also do not require termination points because the signal path has no beginning or end. Passive termination is also used in some forms of Small Computer System Interface (SCSI) systems for terminating a chain of SCSI devices. Active termination, which involves electronically canceling the signal incident on the end of a transmission system, is generally more expensive than passive termination but more efficient.
In Microsoft Windows NT–based networks, a method of performing authentication to a domain controller that resides in a trusted domain. Pass-through authentication enables users to log on to computers in domains in which they do not have a valid user account. Users in a multidomain Windows NT–based network can thus access resources anywhere in the enterprise for which they have suitable permissions.
How It Works
Consider the example of an enterprise consisting of three domains—two resource domains (the trusting domains) in which network resources such as shared folders or printers reside, and a master domain (the trusted domain) in which all user accounts are defined. The resource domains trust the master domain using Windows NT one-way nontransitive trusts. When a user attempts to log on to a computer in a resource domain, pass-through authentication takes place in one of two ways:
When the user first logs on to the computer, the domain controller in the resource domain passes the user’s credentials to the domain controller in the master domain. The user is authenticated, and the user’s security identifier (SID) and group membership are returned to the domain controller in the resource domain.
If the user tries to access a shared folder or printer in the other resource domain, the user’s credentials are passed to the domain controller in the master domain in order to be authenticated for resource access.
A secure identifier that enables a user to access a secured resource. For example, a password can be used to log on to a network and access personal files. Passwords are a part of a user’s credentials, which include, at a minimum, the username and password, and in a multidomain Microsoft Windows 2000–based or Windows NT–based enterprise also include the user’s domain. Passwords are generally known only to users themselves and possibly to members of the Administrators or Account Operators group on Windows 2000–based or Windows NT–based networks.
NOTE
If a user forgets his or her password, the user cannot log on to the network without contacting the administrator. On a Windows NT network, the administrator uses the tool User Manager for Domains to create a new password for the user. On a Windows 2000–based network, the administrator uses the Computer Management tool to create a new password for the user.
TIP
When establishing a password policy for your company, you should determine
Who will control passwords—the administrators or the users. Giving users control over their own passwords makes them completely responsible for their systems and personal folders. You can configure Windows NT and Windows 2000 so that the first time users log on to the network they must change their initial password to one that only they know. This is usually the best solution.
How complex passwords should be and how often they should be changed. If you make passwords too complex, such as random scrambles of letters, numbers, and symbols, the network might be less secure instead of more because users are likely to write down a difficult-to-remember password and tape it under their keyboard or in some other handy location. Also, if passwords must be changed frequently, users will typically make simple changes such as adding an incremental number to the end of each new password. The best policy is usually to require a password of six to eight characters that doesn’t change and to teach users to select passwords that do not include family names, addresses, postal codes, and so on. Passwords should usually be simple combinations of letters and numbers, such as “blue144” or “max13one.”
See also Account policy, username
A clear-text authentication scheme used in Point-to-Point Protocol (PPP) connections over WAN links that is outlined in Request for Comments (RFC) 1334. Password Authentication Protocol (PAP) is not a secure form of authentication because the user’s credentials are passed over the link in unencrypted form. For this reason, Challenge Handshake Authentication Protocol (CHAP) or some other authentication protocol is preferable if the remote client supports it. If the password of a remote client using PAP has been compromised, the authentication server can be attacked using replay attacks or remote client impersonation.
How It Works
PAP uses a two-way handshake to perform authentication. Once the PPP link is established using the Link Control Protocol (LCP), the PPP client sends a username and password to the PPP server. The server uses its own authentication scheme and user database to authenticate the user, and if the authentication is successful, the server sends an acknowledgment to the client.
PAP is typically used only if the remote access server and the remote client cannot negotiate any higher form of authentication. The remote client initiates the PAP session when it attempts to connect to the PPP server or router. PAP merely identifies the client to the PPP server; the server then authenticates the client based on whatever authentication scheme and user database are implemented on the server.
TIP
You should disable PAP on the Remote Access Service (RAS) for Microsoft Windows NT to ensure that user passwords are never sent as clear text over an unsecured connection.
See Provider Architecture for Differentiated Services and Traffic Engineering (PASTE)
A short cable, usually unshielded twisted-pair (UTP) cabling, that connects a port on a patch panel to a port on a hub or a switch. Patch cables are usually terminated at both ends with RJ-45 connectors. Cable vendors usually supply patch cables in fixed lengths such as 1, 3, 6, 10, 25, 50, and 100 feet, and also in custom lengths. Patch cables usually come in various colors, which can be helpful in organizing the cabling joining devices on your equipment racks and avoiding “spaghetti.” You should use patch cables that meet the requirements of the equipment you are using. Category 5 patch cables, which are certified to 100 MHz, or enhanced category 5 patch cables, which are certified to 350 MHz and higher, are generally recommended.
Graphic P-4. Patch cable.
NOTE
Be sure to purchase the correct type of patch cable. For example:
The wiring type (pinning) of the cable should match that of your installed premise cabling. Pinning types include TSB 568A, TSB 568B, and USOC, which are described in the table.
Use straight-pinning or crossover cabling. Crossover cabling, which has the send and receive wire pairs switched, is used primarily for connecting hubs.
TIP
Use patch cables with molded boots to prevent kinks from forming and to prevent pins from becoming bent through rough handling. Molded boots can also reduce the amount of crosstalk in the cable and allow it to perform at higher frequencies.
TIP
Category 5 UTP patch cables should be no longer than 10 meters.
Color Codes by Cable Type
| UTP Pinning Type | Pinning for Each Wire Pair |
| 568A | Blue 4 and 5 Orange 3 and 6 Green 1 and 2 Brown 7 and 8 |
| 568B | Blue 4 and 5 Orange 1 and 2 Green 3 and 6 Brown 7 and 8 |
| USOC | Blue 4 and 5 Orange 3 and 6 Green 2 and 7 Brown 1 and 8 |
A rack-mounted panel with a series of connectors that provides a branching-out point for network cabling to leave the wiring closet and make horizontal runs to wall plates in the work areas.
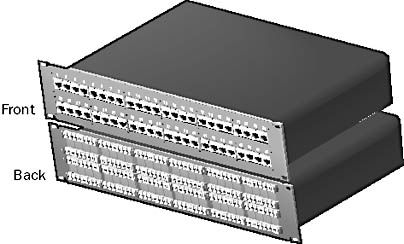
Graphic P-5. Patch panel.
Patch panels are usually standard 19-inch-wide panels for mounting in equipment racks in wiring closets. They typically contain between 16 and 96 ports for connecting to hubs and switches using patch cables. Patch panels themselves cannot be used to network computers; they are mainly used to organize wiring and to avoid “spaghetti.” The horizontal cables running from the wiring closet to the wall plates are usually connected to the back of the patch panel, while the patch cords connecting to the hubs and switches plug into the front of the patch panel. The back of the patch panel is a form of punchdown block—wires are not soldered but punched down using a sharp tool called a punchdown block tool.
NOTE
Another name for a patch panel is passive hub. A patch panel is a hub only in the sense that it is a physical device in which wires are concentrated, but it cannot be used to network computers. All true hubs used in networking are active hubs, which are powered devices that regenerate signals coming into one port for transmission through other ports on the hub. The term “passive hub” is an older term that is not generally used today.
In telephony applications, the termination point for twisted-pair wiring is usually called a punchdown block instead of a patch panel.
There are a few things you should be aware of when selecting patch panels:
Be sure that your patch panels are category 5–approved if you plan to upgrade your network.
Do not remove excessive amounts of cable jacket when you terminate category 5 cables to terminal blocks.
Purchase patch panels with built-in surge protection to protect expensive Ethernet switches.
Front-access patch panels are easiest to install in cramped conditions. You can use hinged or folding patch panels as a convenient alternative to full-size, rack-mounted patch panels. Modular patch panels allow the greatest flexibility of configuration. Use cable managers to organize and support cables connected to patch panels.
The route that a user or application follows to locate a file in a file system, an object in a directory, a server on a network, or some other kind of resource in a hierarchical system. A path to an object can be one of the following:
An absolute path, which starts from the root of the file system or directory
A relative path, which starts from the user’s current directory or location
Example
On a system running Microsoft Windows, the absolute path to a file is expressed using backslashes, as follows:
C:\Windows\Profiles\Administrator\User.dat
If the current directory is C:\Windows\Profiles, the relative path to the same file is as follows:
\Administrator\User.dat
To access files in shared folders on a Windows network, you can use the Universal Naming Convention (UNC) path:
\\server16\pub\readme.txt
On UNIX platforms, forward slashes are used instead of backslashes, as in this example:
/user/bin/blah.gz
To request a Web page on the Internet, you specify the page’s Uniform Resource Locator (URL), which is essentially the path to the page in the hierarchical Domain Name System (DNS):
http://www.microsoft.com/support/FAQ.htm
See Private Branch Exchange (PBX)
See pulse code modulation (PCM)
See Personal Communications Services (PCS)
See Personal Digital Assistant (PDA)
See primary domain controller (PDC)
See primary enterprise controller (PEC)
A computer that functions as a server for a group of users in a peer-to-peer network. For example, in a small office with only five users running Microsoft Windows 95 or Windows 98, you can set aside an additional machine running Windows 95 or Windows 98 as a peer server for storing company files.
You should use peer servers only in small networks with no great need for security. Security on peer servers is limited to share-level security, which allows only three kinds of access:
Read-only access based on a password
Full-control access based on a password
A combination of the above, based on two separate passwords
If security is an issue, consider using a dedicated server running Windows NT.
A network in which the computers are managed independently of one another and have equal rights for initiating communication with each other, sharing resources, and validating users.
How It Works
A peer-to-peer network has no special server for authenticating users. Each computer manages its own security, so a separate user account might need to be created for each computer that a user needs to access. Users usually store files on their own computers and are responsible for ensuring that those files are appropriately backed up. In a peer-to-peer network, each computer typically runs both client and server software and can be used to make resources available to other users or to access shared resources on the network.
Peer-to-peer networks are simple to set up and are often ideal for small businesses that have fewer than 10 computers and that cannot afford a server-based solution. The disadvantages of peer-to-peer networks are poor security and lack of centralized file storage and backup facilities.
Microsoft Windows 98 is an ideal operating system for peer-to-peer networks. Networking is easy to set up and configure, folders and printers can be shared, user profiles allow multiple users to share one computer, and you can create an office intranet using the Microsoft Personal Web Server.
See also server-based network
See Performance Monitor
A Microsoft Windows NT administrative tool for monitoring the performance of Windows NT servers on a network. (In Windows 2000, this tool is called System Monitor.)
You can use Performance Monitor to
Capture real-time performance objects and counters
Log, graph, and set alert conditions for performance data
Identify bottlenecks and trends in resource usage
Observe the effect of system configuration changes
Establish a baseline and determine system capacity
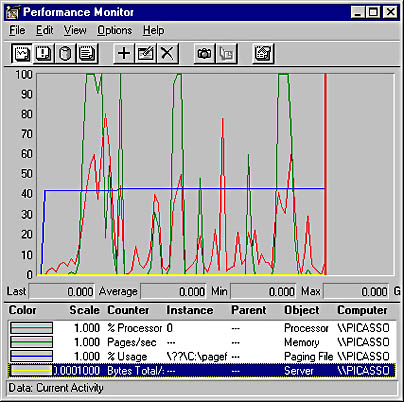
Graphic P-6. Performance Monitor.
How It Works
When you use Performance Monitor, you should collect data on the four main system resources (the memory, processor, disk, and network subsystems) in addition to resources specific to the aspect of server usage you are studying. The following table shows the recommended objects to monitor.
Recommended Objects to Monitor
| System Resource | Performance Objects to Monitor |
| Memory | Memory, cache |
| Processor | Processor, system |
| Disk | Logical disk, physical disk |
| Network | Network segment, network interface, server |
TIP
In Windows NT, Performance Monitor can run as a background service without user intervention. Use the monitor.exe utility from the Microsoft Windows NT Server Resource Kit, and use the Windows NT at command to schedule the service to run at appropriate times.
See also System Monitor
A Microsoft Exchange Server tool that automatically analyzes your hard disk subsystem and suggests where to locate various Exchange components such as the information store and transaction logs. Performance Optimizer also modifies certain registry settings to improve messaging performance.
Performance Optimizer runs when you finish setting up a new Exchange server. You should also run it whenever you change the configuration of a server’s core services—for example, if you change the configuration of the information store, Exchange directory service, or Message Transfer Agent (MTA), if you install or remove a connector or gateway, or if you add more RAM or another disk or processor.
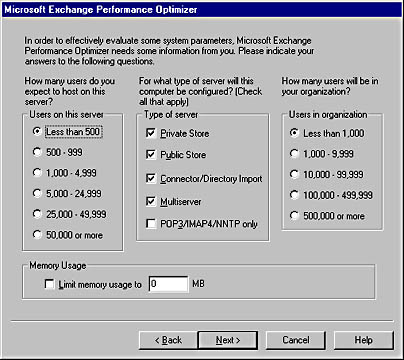
Graphic P-7. Performance Optimizer.
An acronym for Practical Extraction and Reporting Language, an interpreted scripting language that is often used on UNIX platforms to develop Common Gateway Interface (CGI) programs. CGI scripts written in Perl are often used as input handlers for Hypertext Markup Language (HTML) forms because of Perl’s powerful string manipulation capabilities. However, because Perl is an interpreted scripting language, applications such as form handlers for Web pages that are written in Perl run more slowly than if they were compiled programs written in C or some other high-level programming language.
NOTE
You can use Microsoft’s Windows Script Host (WSH) to run administrative scripts written in Perl by installing a third-party ActiveX scripting engine for Perl. Administrators from UNIX backgrounds can do this to leverage their knowledge of Perl to administer Microsoft Windows NT and Windows 2000.
A form of telecommunications service for wide area networks (WANs) that provides a dedicated switched circuit between two nodes in a circuit-switched network.
How It Works
The switches of a permanent virtual circuit (PVC) are set up and configured by the telco or carrier to provide a permanent, point-to-point connection between the two nodes. These circuits are called “permanent” because the telco dedicates specific resources (switches) to your company—they can’t be used by anyone else as long as you lease the service. The switches are called “virtual” because the customer does not have a physical wire connecting two networks but rather a logical connection between switches configured by the telco’s management software. In fact, the customer does not even need to know how the circuit is set up.
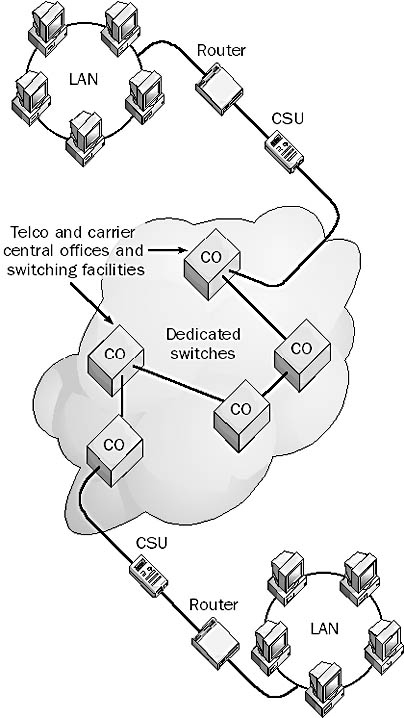
Graphic P-8. Permanent virtual circuit (PVC).
PVCs offer guaranteed bandwidth and extremely low latency for establishing a connection. Also, because the switching pathway is permanent, the quality of the connection does not vary with time. The result is more reliable service than switched virtual circuits (SVCs). However, PVCs are more expensive than SVCs because telco resources are dedicated to the customer and cannot be used for other purposes. Furthermore, with a PVC you pay for the bandwidth whether or not you use it; with SVCs, the amount you pay depends on how much bandwidth you use.
PVCs are best for WAN links that carry steady, high volumes of network traffic. They are commonly used in leased lines for point-to-point WAN links between two networks.
NOTE
The term “permanent virtual circuit” is also used in frame relay networking. This type of circuit is configured in a similar fashion to those used in leased line connections.
See also switched virtual circuit (SVC), virtual circuit
Settings that you establish for a resource to control which users and groups can access the resource and what degree of access they have. Permissions are implemented at several levels in Microsoft Windows operating systems and other Microsoft BackOffice applications. Permissions are implemented in Microsoft systems using discretionary access control lists (DACLs), which are attached to the object they control.
Examples of permission types include the following:
Shared folder permissions: Can be applied to shared folders on Windows systems to control access to network shares by users
NTFS permissions: Can be applied to files and folders on NTFS volumes for both local and network control of access to the resources
Print permissions: Can be assigned to printers to control who can manage printers, manage documents, or print documents
Active Directory permissions: Can be assigned to objects within Active Directory of Windows 2000 using Active Directory Users and Computers
Exchange permissions: Can be assigned to objects in the Microsoft Exchange Server directory hierarchy to control who can administer different parts of an Exchange organization using the Exchange Administrator program
Public folder permissions: Can be assigned using Microsoft Outlook to files in public folders to control who can read, edit, or delete those files
A licensing mode in which a client access license (CAL) is assigned to a particular client computer for a particular Microsoft BackOffice server product. A CAL allows the client to access the services of a particular BackOffice product that can be running on any server within the network. Per Seat licensing can be applied to any BackOffice product that requires CALs, such as Microsoft Windows 2000 Server, Windows NT Server, Microsoft Exchange Server, Microsoft SQL Server, Microsoft SNA Server, Microsoft Site Server, and Microsoft Systems Management Server (SMS).
Example
Consider a network that consists of three servers running Windows 2000 Server and 50 assorted client computers running Windows 2000 Professional, Windows 98, Windows for Workgroups, Mac OS, and so forth. If you purchase 50 Per Seat licenses for Windows 2000 Server, one for each client, each client computer can connect to any of the three Windows 2000 Servers.
NOTE
If you use Per Seat licensing, you must purchase a CAL for every client that accesses the BackOffice product, including non-Microsoft clients such as Macintosh and UNIX clients.
TIP
Per Seat licensing is often the preferred mode of licensing on networks with a large number of servers. On networks with only one or two servers, Per Server licensing might be a more economical option.
See also client access license (CAL), Per Server licensing
A licensing mode in which a client access license (CAL) is assigned to a particular server computer running a particular Microsoft BackOffice server product. Each CAL allows only one connection per client computer to the particular BackOffice product. Per Server licensing can be applied to only the following BackOffice products: Microsoft Windows 2000 Server, Windows NT Server, Microsoft SQL Server, Microsoft SNA Server, and Microsoft Site Server.
Example
Consider a server computer on a network running Windows 2000 Server that has 25 Windows 2000 Server Per Server CALs. A total of 25 client computers can simultaneously connect to the Windows 2000 Server and access its services. If a twenty-sixth client tries to connect, it will be denied access and an entry will be written to the application log.
NOTE
One client computer can connect to multiple shares on the server, but this is counted as only one connection for licensing purposes.
TIP
Per Server licensing is the preferred mode of licensing on small networks. However, you must purchase licenses equal to the maximum number of simultaneous connections you anticipate on each server for a particular BackOffice product. If you are not sure whether to use Per Seat or Per Server licensing, choose Per Server licensing. As more servers are added to your network, you can perform a one-time, one-way conversion of Per Server to Per Seat licenses as required. However, you cannot convert Per Seat licenses to Per Server licenses.
See also client access license (CAL), Per Seat licensing
Generally, any network connection that is opened and then is kept open in case it is needed again.
Example
The Windows Internet Name Service (WINS) for Microsoft Windows 2000 Server uses persistent connections between WINS replication partners. Windows 2000 Server WINS replication partners maintain persistent connections among themselves so that replication can be initiated at any time without the network traffic overhead associated with establishing new connections. This means that WINS databases are updated immediately and shared network resources are always available.
In the earlier version of WINS for Windows NT Server, however, replication partners had to open a new connection between each other every time WINS replication was initiated. As a result, most administrators of large networks configured WINS replication to occur at certain time intervals or after a certain number of updates to the WINS database had accumulated. Because of delays in updating WINS databases on WINS servers, clients sometimes could not access shared network resources.
An index created by Microsoft Indexing Service. Persistent indexes are stored on disk and are more efficient and compressed than word lists, which are stored in volatile RAM. All persistent indexes are ultimately merged into a single, highly efficient persistent index called the master index. The process by which this occurs is known as a master merge.
A general term for digital cellular phone technologies that are used for personal wireless mobile communication. Personal Communications Services (PCS) technologies were developed in the early 1990s because the existing Advanced Mobile Phone Service (AMPS) technologies were running out of available bandwidth in the electromagnetic frequency spectrum. PCS systems are end-to-end digital in nature and are more secure than analog cellular systems. PCS networks can be used for voice, fax, and data applications such as e-mail and file transfers. PCS systems are generally circuit-switched, although some are being migrated to packet-switched networks.
Some of the standards and technologies that developed from the PCS initiatives include the following:
Time Division Multiple Access (TDMA) digital cellular systems based on the TDMA IS-136 standard. TDMA divides frequency bands into time slots and then multiplexes user conversations within these slots. TDMA operates in both the 800-MHz and 1900-MHz frequency bands, but only frequencies at 1900 MHz are specifically referred to as PCS, while those in the 800-MHz range are referred to as cellular.
Code Division Multiple Access (CDMA) digital cellular systems based on the CDMA IS-95 standard, which was developed by QUALCOMM. CDMA uses spread-spectrum transmission technologies and assigns codes to individual users transmitting within the same broad frequency spectrum. CDMA operates at both the 800-MHz and 1900-MHz frequencies, but only frequencies at 1900 MHz are specifically referred to as PCS, while those in the 800-MHz range are referred to as cellular.
Global System for Mobile Communications (GSM) digital cellular systems based on the GSM 1900 standard. GSM is based on TDMA technologies and divides frequency bands into time slots. GSM has the advantage of supporting roaming between Europe and North America. GSM operates in the 1900-MHz frequency range (or the 1800-MHz range in Europe).
PCS systems and services can also be classified as follows:
Narrowband PCS: Uses the 900-MHz portion of the electromagnetic spectrum, specifically the frequency bands 901–902, 930–931, and 940–941 MHz. Narrowband PCS is used for wireless telephony, wireless data transmission, voice message paging and text-based paging, and other services.
Broadband PCS: A newer technology that uses the 2-GHz portion of the electromagnetic spectrum, specifically the frequency band from 1850 to 1990 MHz, with the exception of a 20-MHz band reserved for unlicensed voice and data services. Broadband PCS with its greater bandwidth allocation is used or intended for wireless telephony, high-speed wireless data transmission, portable facsimile transmission, wireless Personal Digital Assistants (PDAs), and wireless video telephony services.
A handheld computer that is programmed for functions such as keeping track of appointments, sending and receiving e-mail, browsing the Internet, composing memos, performing spreadsheet calculations, managing contacts, banking, and viewing stock quotes.
Personal Digital Assistants (PDAs) typically have a small, grayscale liquid crystal display (LCD) with either a small keyboard or a pen-based user interface for entering data. Information can be exchanged with a desktop or laptop PC by using a docking cradle, serial port, or infrared (IR) communication port, depending on the model. A PDA’s processing power is similar to that of a 386 processor, and its memory is limited to a few megabytes (but is sometimes expandable). Many PDAs also support standard or even wireless modems for sending and receiving e-mail or accessing specialized Internet content.
Some PDAs run a proprietary operating system. For example, 3Com’s Palm Pilot runs Palm OS; about 7500 developers produce software for this platform. One of the earliest PDAs was the Apple Newton. Other PDAs run Microsoft Windows CE, a version of the Windows operating system for devices with a small screen and a nonstandard user interface. Microsoft offers Windows CE versions of many of its popular applications, including Microsoft Word, Excel, Outlook, PowerPoint, and Internet Explorer.
PDA management is becoming an increasingly important job for network administrators. It’s often a good idea to standardize the type of PDA that is used in a company to reduce the headache and overhead of administering multiple PDA-to-PC software interfaces.
A hierarchy of folders in Microsoft Outlook and other Microsoft Windows messaging clients that users can create and modify and that stores users’ messages and attachments. Personal folders, which can be stored on the client machine or on a network share, have the extension .pst.
NOTE
In many situations, it is advantageous not to use personal folders. Using personal folders can make messages less accessible. For example, Microsoft Exchange Server stores users’ messages in the information store on the Exchange server. This allows users to access their messages from any messaging client that can access the Exchange server. If messages are moved to personal folders, those messages can be read only from clients that can access the personal folders file. It is possible to use a combination approach, in which messages that need to be accessible from different clients can be left on the server and messages that are rarely accessed can be moved to personal folders. Here are some reasons why you might want to use personal folders:
For backing up folders and their messages
For archiving old messages
For reducing the space taken up by messages on the server (a disk space limit for messages is typically set on the server)
For moving some messages to the disk of a laptop computer to work off-site
Users can password protect their personal folders, but if they forget the password they cannot reset it.
Related components of Microsoft Site Server that enable Web site administrators to personalize content for site visitors and provide secure content based on site membership. Features of the Personalization and Membership servers include the following:
Personalized content suited to individual visitors’ needs. Site administrators can build rules governing personalized content and store user profiles in the Membership Directory.
Members-only areas on a site with controlled access for users. Site administrators can register users, protect and share their data, verify users’ identities, and control access to sites. User information is stored in a Lightweight Directory Access Protocol (LDAP) directory based on Microsoft SQL Server.
Direct mail for delivering personalized content to site visitors through scheduled e-mail based on their site usage patterns.
How It Works
Membership Authentication on the Personalization and Membership servers builds on Microsoft Windows NT security by letting administrators store user accounts and group permissions in the Site Server Membership Directory. Access to Web content is controlled by granting users and groups permissions on Web content using the same Windows Explorer method that Windows NT and Internet Information Services (IIS) administrators use.
By storing user and group accounts in the Membership Directory, you can enable sites to scale beyond the capabilities of the Windows NT Security Account Manager. In other words, instead of managing tens of thousands of accounts using the Windows NT domain model, you can use Personalization and Membership servers to manage millions of user accounts. This is particularly important if a cookie account and a user profile must be created for every user visiting the site.
Tools are also included for creating registration pages to handle creating new user accounts in the Membership Directory, adding users to groups, and upgrading cookie users to secured accounts. You can manage membership by using Microsoft Management Console (MMC) or through Web-based Administration (WebAdmin).
TIP
When you plan an implementation of Site Server, you must decide whether to use Windows NT Authentication or Membership Authentication. You cannot reverse your decision later without rebuilding the Membership Directory, which essentially means redoing all your initial implementation work. Use Windows NT Authentication for Windows NT–based intranets in which user accounts already exist for network users. Use Membership Authentication for Internet sites and for intranet sites in which Windows NT accounts do not yet exist. Membership Server is also suitable for any type of site in which users must self-register and thus create and manage their own profiles, which eases the burden on the Site Server administrator. For example, the information that intranet users create in the Membership Directory can form the basis of your corporate information directories with little administrative overhead.
See Microsoft Personal Web Server (PWS)
See Pretty Good Privacy (PGP)
See MAC address
Layer 1 (or the PHY layer) of the Open Systems Interconnection (OSI) reference model. The physical layer is the bottom layer of the seven-layer OSI networking architecture model. It establishes the physical interface and mechanisms for placing a raw stream of bits onto the wire. It defines the voltage, current, modulation, bit synchronization, connection activation and deactivation, and various electrical characteristics for the transmission media (such as unshielded or shielded twisted-pair cabling, coaxial cabling, and fiber-optic cabling). Protocols at the PHY layer include IEEE 802.3, RS-232C, and X.21. Repeaters, transceivers, network interface cards (NICs), and cabling operate at the PHY level.
See also Open Systems Interconnection (OSI) reference model, protocol
Stands for Packet Internet Groper, a TCP/IP utility that verifies the integrity of a network connection with a host on a TCP/IP network. The ping command is one of the first commands to use to troubleshoot communication problems on a TCP/IP network.
How It Works
At the command prompt, type ping followed by either the IP address or the fully qualified domain name (if the Domain Name System is implemented) of the host for which you want to test networking connectivity. One or multiple Internet Control Message Protocol (ICMP) echo packets are sent to the host, and if connectivity is working, an equal number of echo replies are received. The replies show the packet size in bytes, response time in milliseconds, and Time to Live (TTL) of the echo reply. The TTL is decremented for each hop along the way and indicates the number of routers (hops) passed through along the network path.
The usual procedure for using ping to troubleshoot a TCP/IP network follows:
Verify that TCP/IP is installed and running by pinging the local loopback address using ping 127.0.0.1.
Ping your own IP address and host name.
Ping the IP address of the default gateway for your local network.
Ping the IP address of a host on a remote network.
If these steps produce the expected results, TCP/IP is installed and running on your network.
TIP
For advanced syntax features, simply type ping instead of ping /?.
If you can ping a host’s IP address but not its fully qualified domain name (FQDN), you probably have a name resolution problem. Check your Domain Name System (DNS) configuration and make sure that the DNS server is running, or check your Hosts file if it is implemented.
Stands for Public Key Cryptography Standards, a set of standards developed by an industry consortium headed by RSA Laboratories and including Microsoft that specifies how a public key cryptography system should be implemented and operated. The following table shows the standards that are important to public key cryptography.
Public Key Cryptography Standards
| Standard | Description |
| PKCS #1 | Specifies how to encrypt and sign data using RSA encryption |
| PKCS #2 | Now included in PKCS #1 |
| PKCS #3 | Describes the Diffie-Hellman key exchange protocol |
| PKCS #4 | Now included in PKCS #1 |
| PKCS #5 | Specifies how to encrypt data using a secret key derived from a user’s password |
| PKCS #6 | Specifies the syntax standard for extended certificates |
| PKCS #7 | Specifies the general syntax of messages that include cryptographic enhancements such as encryption and digital signatures |
| PKCS #8 | Specifies the format for private key information |
| PKCS #9 | Specifies various attribute types that are used in other PKCS standards |
| PKCS #10 | Specifies the syntax for requesting digital certificates |
| PKCS #11 | Specification for the Cryptoki application programming interface (API), which is used in smart cards |
| PKCS #12 | Specifies a portable format for storing and transporting certificates, private keys, and so forth |
| PKCS #13 | Specifies standards for elliptic curve cryptography (under development at the time of this writing) |
| PKCS #14 | Specifies standards for generating pseudo-random numbers (under development at the time of this writing) |
| PKCS #15 | Specifies the standard format for cryptographic token information (under development at the time of this writing) |
On the Web
•
RSA Security home page : http://www.rsasecurity.com
See also PKCS #7, PKCS #12
Also called the Cryptographic Message Syntax Standard, a cryptographic standard from RSA Security for the exchange of digital certificates in public key cryptography. PKCS #7 specifies the syntax of digital certificates and other encrypted information—specifically, the method by which data is encrypted and digitally signed, as well as the algorithms involved.
How It Works
You can use PKCS #7 to encrypt two types of data:
Base data: Data that has not been encrypted and contains no cryptographic enhancements such as hashes or digital signatures.
Enhanced data: Data that is encrypted or contains cryptographic enhancements or both. Enhanced content encapsulates one form of content within another.
A variety of content types are defined by the PKCS #7 standard, including the following:
Data: String of bytes or octets.
Signed data: Data along with an encrypted message digest. A message digest is the value produced when a hashing algorithm is applied to data. (The terms “digest” and “hash” are synonymous.) The message digest is used by the recipient to confirm that the original message was not tampered with during transit and to validate the identity of the sender.
Enveloped data: Encrypted data plus the public key that can decrypt the data. You use this method to keep the contents of the message secret from all but trusted recipients.
Signed-and-enveloped data: Encrypted content with its public key and doubly encrypted message digest.
Digested data: Data plus a message digest.
Encrypted data alone: The public key for decrypting the data must be transmitted by some other mechanism in this case.
When you use PKCS #7 to sign data, it usually includes the signing certificates, a list of relevant certificate revocation lists, and any other certificates in the certification path. If you use PKCS #7 to encrypt data, it usually includes references to the issuer and the serial number of the certificate that is associated with the public key that can be used to decrypt the encrypted data.
PKCS #7 supports additional features, such as the following:
Recursion, in which a digital envelope is enclosed in a digital envelope, which is enclosed in another digital envelope, and so on
Time-stamping of encrypted messages and digital signatures
Counter-signatures and user-defined attributes
See also PKCS
A cryptographic standard for the exchange of digital certificates in public key cryptography. PKCS #12 is an industry-standard format for the transfer, backup, and restoration of digital certificates and their associated public or private keys. PKCS #12 is the export format that is usually used to export a digital certificate with its private key, because exposing a user’s private key using a less secure method of export poses a security risk. PKCS #12 is used to export certificates to other computers, to removable media for backup purposes, or to smart cards to enable smart card authentication schemes.
See also PKCS
See public key infrastructure (PKI)
The basic analog telecommunications service provided by a local telco. Plain Old Telephone Service (POTS) was the only type of telephone service until the 1970s.
How It Works
Starting from your home or customer premises, two-pair copper twisted-pair wire runs to your local telco’s central office (CO). This copper wire connection forms what is known as the local loop. The CO has switches that connect you to another local subscriber, to another CO, or to a long-distance provider, depending on whether your call is local or long distance. POTS is an inexpensive circuit-switched telecommunications service, but it supports data transfer speeds up to only 56 Kbps. It typically takes 15 to 30 seconds to establish connections for data transfer using modems.
Also known as CMP cabling, a grade of cabling that is resistant to combustion and is used for horizontal cable runs in building plenums and vertical rises such as elevator shafts. A plenum is a horizontal space within a building that houses building components and allows the movement of air. False ceilings are not considered plenums. Plenum cabling is less flexible and costlier than polyvinyl chloride (PVC) cabling. The external insulating jacket of plenum cabling is usually a fluoropolymer such as Teflon FEP.
A design philosophy and set of specifications for PC architectures that enables computer hardware, peripherals, device drivers, and operating systems to be easily reconfigured with minimal user understanding and intervention. Plug and Play frees users from having to manually configure devices and device drivers when they add or remove peripherals from computer systems. For example, to configure a non–Plug and Play sound card, a user typically has to manually change jumpers or dual inline package (DIP) switches on the sound card itself, a task that is often difficult for the inexperienced user. With Plug and Play, you simply plug in the device and follow a series of prompts (if any are necessary) to configure the appropriate drivers for your device.
How It Works
A true Plug and Play system consists of the following three elements:
A Plug and Play operating system such as Microsoft Windows 95, Windows 98, or Windows 2000.
A Plug and Play system BIOS that supports Advanced Power Management 1.1 (Windows 95) or Advanced Configuration for Power Management (Windows 98), automatic configuration of boot and motherboard devices, hot docking, and other features.
Plug and Play system buses such as PCI or universal serial bus (USB) and Plug and Play peripheral devices (internal or external) and their associated drivers. Plug and Play peripheral devices include USB, IEEE 1394, SCSI, PCMCIA, and PCI devices. ISA, EISA, and VESA devices are not fully Plug and Play. Other Plug and Play devices include IDE controllers, ECP parallel ports, and video adapters.
If a system does not support all three of these features, it is not truly Plug and Play, although it might have some limited Plug and Play support. In a completely Plug and Play system, these features work together to automatically enumerate (identify) new devices installed on or connected to the system, determine their resource requirements, establish a system configuration that can support these requirements without device conflicts, program the devices as necessary and load their device drivers, and notify the user of the changes to the system’s configuration.
The Windows 95 and Windows 98 components that work together to support Plug and Play include the following:
Configuration Manager: Manages the device configuration process by communicating with the BIOS, motherboard, and peripheral devices.
The hardware tree: Contains the current system configuration information. The hardware tree is dynamically constructed by Configuration Manager upon each reboot and uses information in the registry to configure the system’s devices. You can display information stored in the hardware tree by using the Device Manager tab of the System Properties dialog box (double-click the System icon in Control Panel).
Bus and port enumerators: Build the hardware tree by enumerating attached devices. Different enumerators are used for each type of system and peripheral bus.
Resource arbitrators: Allocate system resources such as interrupt requests (IRQs) and input/output (I/O) ports to devices and resolve conflicts between devices.
Setup and Device Installer: Creates the configuration database during initial system setup and can assist in installing non–Plug and Play devices by using the Add New Hardware Wizard.
When you add a new hardware device to a Plug and Play system, the Add New Hardware Wizard starts and installs the necessary drivers for the hardware. The wizard selects suitable hardware resources for the device, which might include an IRQ line, I/O address, direct memory access (DMA) channel, and memory range. If the system cannot properly detect the hardware, you can manually run the Add New Hardware Wizard to configure the hardware.
TIP
Be sure that the new device is attached to the computer and is turned on before you run the Add New Hardware Wizard.
A NetBIOS name resolution method used for name registration and resolution. P-node is one of the types of NetBIOS over TCP/IP nodes defined in Request for Comments (RFC) numbers 1001 and 1002, and is supported by computers running Microsoft Windows NT and Windows 2000.
How It Works
Name resolution is the process of converting the name of a host on the network into a network address (such as an IP address). Name resolution must be performed to establish communication over a network. P-node is one of four basic methods supported by Windows NT for resolving NetBIOS host names (that is, computer names) into IP addresses.
If a computer running Windows NT is configured as a P-node machine, it does not use broadcasts to resolve the names of the hosts. Instead, it tries to query a NetBIOS name server to resolve names of other hosts on the network. The advantage of doing this is that name resolution can function across large internetworks consisting of IP subnets connected with routers. Routers normally block broadcasts but will forward packets directed toward a specific name server.
A server running the Windows Internet Naming Service (WINS) is a typical example of a NetBIOS name server. If the WINS server is unavailable to the client issuing the query, the requested name cannot be resolved into its associated IP address. Furthermore, each client must be configured with the IP address of the WINS server in order for P-node name resolution to work. For this reason, M-node or H-node methods are usually preferred; they can use both broadcasts and directed traffic to resolve NetBIOS names of hosts.
See also B-node, H-node, M-node, NetBIOS name resolution
A resource record in a zone file that contains a record associating an IP address with a host name in the in-addr.arpa domain. Pointer (PTR) records are used for reverse name lookups and provide host name to IP address mappings. Here is an example of a PTR record:
1.141.205.202.in-addr.arpa IN PTR server9.microsoft.com.
In this PTR record, the IP address 202.205.141.1 is mapped to the host Server9 within the microsoft.com domain. Note that the IP address of the host appears in the reverse order in the in-addr.arpa domain.
NOTE
With the DNS service installed on Microsoft Windows NT or Windows 2000, you can automatically create an associated PTR record for each host when you create its host record.
See also Domain Name System (DNS)
The local access point for an Internet service provider (ISP). A point of presence (POP) consists of the high-speed telecommunications equipment and technologies that enable users to connect to the Internet via their ISP. The POP might include call aggregators, modem banks, routers, and high-speed Asynchronous Transfer Mode (ATM) switches. A POP has one or more unique IP addresses plus a pool of assignable IP addresses for its permanent and dial-up clients. The actual POP for an ISP might be located within the telecommunications facility of a telco or a long-distance carrier. The ISP rents or leases space in the facility to install the routers and access servers that provide Internet connectivity for clients and for the equipment that provides the ISP with a high-speed T1 or T3 connection to the Internet’s backbone.
A form of communication that provides a path from one fixed point to a number of other points.
How It Works
A point-to-multipoint (or simply multipoint) wide area network (WAN) consists of more than two end nodes connected using a packet-switching telecommunications network. A number of layer 2, or data-link layer, protocols support multipoint WANs, including frame relay, Switched Multimegabit Data Services (SMDS), Asynchronous Transfer Mode (ATM), and X.25 packet-switched networks.
A public or private frame relay network can be used to connect multiple networks into a multipoint WAN configuration, as shown in the following diagram. Each end node is configured with a unique data-link address, which allows any node on the WAN to communicate with any other node.
NOTE
The various data-link layer protocols can also be used for point-to-point WAN connections, but other layer 2 protocols such as the Point-to-Point Protocol (PPP) are simpler to implement for point-to-point WAN communication.
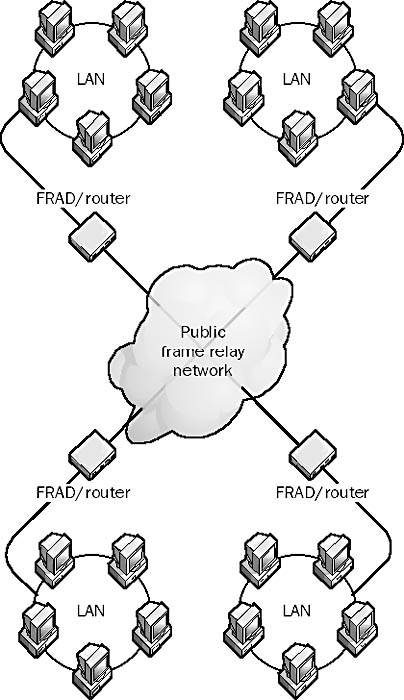
Graphic P-9. Point-to-multipoint.
See also point-to-point
A form of communication that provides a direct path from one fixed point to another.
How It Works
A point-to-point wide area network (WAN) consists of two end nodes connected by a leased line. In a typical configuration, a router on the network is connected using a serial transmission interface such as V.35 to a Channel Service Unit (CSU) at the local customer premises. The CSU provides the interface between the router and the telco’s leased line. An identical setup is configured at the remote customer premises. Because there are only two end nodes in a point-to-point WAN link, addressing need not be provided for the end nodes at the data-link layer.
Point-to-point WAN connections typically use High-level Data Link Control (HDLC), Point-to-Point Protocol (PPP), or one of their derivatives—such as Point-to-Point Tunneling Protocol (PPTP)—as the layer 2, or data-link layer, protocol for encapsulating local network traffic into frames for transmission over the WAN link.
NOTE
The term “point-to-point” is also used more generally. For example, the configuration of a terminal connected to a minicomputer using two short-haul asynchronous modems is referred to as a point-to-point connection.
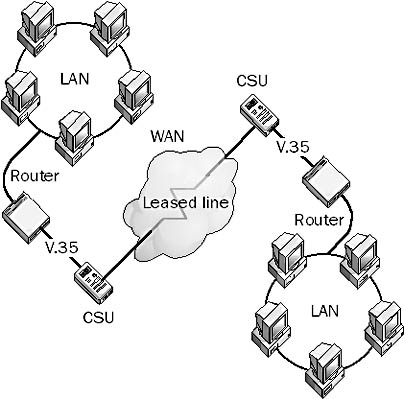
Graphic P-10. Point-to-point.
TIP
PPP is usually used in heterogeneous networking environments in which the routing and access equipment comes from different vendors, while HDLC tends to be used in homogeneous networking environments in which the routers and access equipment run only Cisco’s Internetwork Operating System (IOS) software.
See also point-to-multipoint
An industry standard data-link layer protocol for wide area network (WAN) transmission that was developed in the early 1990s. Point-to-Point Protocol (PPP) allows Remote Access Service (RAS) products and devices from different vendors to interoperate for WAN communication.
How It Works
PPP supports the transmission of network packets over a serial point-to-point link by specifying framing mechanisms for encapsulating network protocols such as Internet Protocol (IP), Internetwork Packet Exchange (IPX), or NetBEUI into PPP frames. PPP encapsulation is based on the High-level Data Link Control (HDLC) derived from the mainframe environment. These PPP frames can be transmitted over serial transmission lines such as Plain Old Telephone Service (POTS), Integrated Services Digital Network (ISDN), and packet-switched networks such as X.25. PPP includes an extensible Link Control Protocol (LCP) for establishing, tearing down, and testing data-link WAN connections, as well as a number of Network Control Protocols (NCPs) for establishing and configuring network communication using each network protocol. PPP also supports a number of authentication schemes, such as Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP).
A typical dial-up session using PPP is completely automated and requires no real-time user input. It has four stages:
Link establishment: PPP uses LCP to establish and maintain a PPP link over a serial transmission line. LCP frames are sent over the data link to test its integrity and establish the link.
User authentication: PPP uses one of several authentication protocols, including PAP, CHAP, and Microsoft Challenge Handshake Authentication Protocol (MS-CHAP).
Callback: PPP Callback Control (Microsoft’s implementation of PPP) uses Callback Control Protocol (CBCP) if it is configured.
Configuration: NCPs are used to establish network connections, perform compression and encryption, lease IP addresses using Dynamic Host Configuration Protocol (DHCP), and so on. NCP frames are sent over the link to establish a network connection between the PPP server and the remote PPP client.
NOTE
PPP is superior to the older Serial Line Internet Protocol (SLIP) in that it offers error correction and dynamic negotiation without user intervention, supports multiple network protocols simultaneously, and is faster. PPP is the basis for the Point-to-Point Tunneling Protocol (PPTP) and the Layer 2 Tunneling Protocol (L2TP), which can be used to create virtual private networks (VPNs). PPP is supported by Microsoft Windows 2000, Windows NT, Windows 95, and Windows 98 and is the default setting for Network and Dial-up Connections, RAS, and connectivity to the Internet.
TIP
If you can connect to a remote PPP server but you can’t ping the remote server, try turning off IP header compression. Windows 98 also allows you to record all PPP communication in a ppplog.txt log file for troubleshooting purposes. Open the property sheet of your dial-up networking icon, select the Server Types tab, and select the Record A Log File For This Connection option.
A data-link layer protocol for wide area networks (WANs) based on the Point-to-Point Protocol (PPP) and developed by Microsoft that enables network traffic to be encapsulated and routed over an unsecured public network such as the Internet. Point-to-Point Tunneling Protocol (PPTP) allows the creation of virtual private networks (VPNs), which tunnel TCP/IP traffic through the Internet. Remote users can securely access corporate local area network (LAN) resources using the Internet instead of having to use direct modem connections over the Public Switched Telephone Network (PSTN) or dedicated leased-line connections.
How It Works
PPTP is an extension of PPP and is based on PPP negotiation, authentication, and encryption schemes. PPTP encapsulates Internet Protocol (IP), Internetwork Packet Exchange (IPX), or NetBEUI packets into PPP frames, creating a “tunnel” for secure communication across a LAN or WAN link. The PPTP tunnel is responsible for authentication and data encryption and makes it safe to transmit data over unsecured networks.
PPTP supports two types of tunneling:
Voluntary tunneling: Initiated by the PPTP client (such as Microsoft Windows 95, Windows 98, Windows NT, or Windows 2000). This type of tunneling does not require support from an Internet service provider (ISP) or network devices such as bridges.
Compulsory tunneling: Initiated by a PPTP server at an ISP. This type of tunneling must be supported by network access servers (NAS’s) or routers.
No matter which type of tunneling you use, you must use a PPTP server. Corporations can set up dedicated PPTP-enabled servers on their networks using Windows NT Server.
NOTE
Microsoft’s Remote Access Service (RAS) for Windows NT supports PPTP through both dedicated and dial-up Internet connections. To enable Windows NT Server to act as a PPTP server, click Network in Control Panel, click the Advanced button on the TCP/IP property sheet, and select Enable PPTP Filtering.
TIP
Because PPTP supports multiple network protocols, including IP, IPX, and NetBEUI, two computers can establish a tunnel over the Internet only if they are running the same network protocol. To troubleshoot PPTP over a TCP/IP connection, use ping to determine whether you are connected to your PPTP server. Also be sure that you have trusted credentials in the domain of the PPTP server, and be sure that you don’t have an active Winsock Proxy client that might be redirecting PPTP packets to a proxy server instead of to your VPN.
A grade of network cabling that uses polyvinyl chloride (PVC) plastic for its outer protective insulating jacket. Polyvinyl chloride cabling is cheap and flexible but gives off dangerous gases during combustion. Building codes usually require that plenum cabling be used instead of polyvinyl chloride cabling for horizontal runs from wiring closets to wall plates. Polyvinyl chloride cabling is usually used to connect wall plates to computers. Both coaxial and twisted-pair cabling are generally available in either polyvinyl chloride or plenum-grade jackets.
See point of presence (POP)
See Post Office Protocol version 3 (POP3)
In TCP/IP networking, an endpoint of a logical connection between two hosts on an internetwork. Ports are identified by port numbers. A port identifies a unique process for which a server can provide a service or the client can access a service. Ports can be Transmission Control Protocol (TCP) ports or User Datagram Protocol (UDP) ports, depending on the type of service supported.
In general networking terminology, a port is a connector for attaching cables or peripherals to a computer—for example, a parallel port for connecting a printer to a computer or a serial port for connecting a serial mouse or modem to a computer. Connectors on networking components, such hubs or routers, are also sometimes called ports, although a better term for a connector on a router is a “router interface.”
A Web site that provides a collection of services for Internet users, such as the following:
A directory of interesting or useful sites
A search engine for finding sites on the Internet
Public information services such as weather, white pages, yellow pages, maps, and stock quotes
Opportunities to purchase goods and services on line
Information and frequently asked questions (FAQ) for new users of the Internet
Registration services for receiving free newsletters via e-mail
Chat areas for discussing various topics and for building online communities
Games
Some of the leading Internet portals are listed below.
On the Web
•
Microsoft Network (MSN) : http://www.msn.com
•
Yahoo! : http://www.yahoo.com
•
America Online (AOL) : http://www.aol.com
•
Lycos : http://www.lycos.com
•
Netscape Netcenter : http://www.netscape.com
A 16-bit integer assigned to a port on a TCP/IP host that enables the host to communicate with another host on the network. Ports can have numbers between 0 and 65,536 and are divided into two types:
Well-known port numbers, which are fixed numbers between 0 and 1023 and are assigned by the Internet Assigned Numbers Authority (IANA). Some of these numbers are currently unassigned or reserved for future use.
Dynamically assigned port numbers, which the operating system assigns as needed when a TCP/IP application or service requests a port. These numbers are between 1024 and 65,536 and can be released and reassigned as needed.
NOTE
Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) ports are different, but TCP and UDP ports use the same assigned port numbers for a given TCP/IP application or service whenever possible.
See also well-known port numbers
An acronym for Portable Operating System Interface for UNIX, one of several standards developed by the Institute of Electrical and Electronics Engineers (IEEE) for cross-platform implementations of UNIX. POSIX is a standard operating system interface and environment that supports portability of applications at the source code level. POSIX arose because different vendors were producing different “flavors” of UNIX; code written for one platform would not run on another platform unless it was modified appropriately. The solution was to develop a standard in which code could be portable between all UNIX flavors, so that a POSIX call in one program would work on any other POSIX-compliant system.
Because of vendor-specific enhancements most UNIX systems are not 100 percent POSIX-compliant. The POSIX.1 standard defines the portability of C language code by specifying a standard application programming interface (API). Microsoft Windows NT and Windows 2000 are fully compliant with the POSIX.1 standard, which means that the POSIX subsystem of Windows NT or Windows 2000 can run native C language code written to the POSIX.1 standard. Windows NT does not support other POSIX standards.
POSIX Standards
| Standard | Description |
| POSIX.1 | Specifies the base system interfaces for C language programming |
| POSIX.2 | Specifies standards for shells and system utilities plus additional C language interfaces |
| POSIX.3 | Specifies methods for testing conformance to POSIX |
| POSIX.4 | Adds real-time extensions to POSIX.1 |
| POSIX.5 | Extends POSIX.1 to the Ada programming language |
| POSIX.9 | Extends POSIX.1 to the FORTRAN77 language |
See power-on self test (POST)
The central message store in a legacy Microsoft Mail system.
How It Works
The postoffice consists of a series of message storage directories on the Microsoft Mail file server. The postoffice stores information such as user ID, password, user preferences, message folders, mail messages, and attachments. The postoffice is a passive file system; no active software runs on it. The International Telecommunication Union (ITU) refers to this component of a mail system as the “message store.”
An Internet standard protocol for storing and retrieving messages from Simple Mail Transfer Protocol (SMTP) hosts.
How It Works
SMTP provides the underlying transport mechanism for sending e-mail messages over the Internet, but it does not provide any facility for storing messages and retrieving them. SMTP hosts must be continuously connected to one another, but most users do not have a dedicated connection to the Internet.
Post Office Protocol version 3 (POP3) provides mechanisms for storing messages sent to each user and received by SMTP in a receptacle called a mailbox. A POP3 server stores messages for each user until the user connects to download and read them using a POP3 client such as Microsoft Outlook 98, Microsoft Outlook Express, or Microsoft Mail and News.
To retrieve a message from a POP3 server, a POP3 client establishes a Transmission Control Protocol (TCP) session using TCP port 110, identifies itself to the server, and then issues a series of POP3 commands:
stat: Asks the server for the number of messages waiting to be retrieved
list: Determines the size of each message to be retrieved
retr: Retrieves individual messages
Quit: Ends the POP3 session
NOTE
After a POP3 client reads a message in its mailbox on a POP3 server, the message is deleted. Primarily because of this, POP3 is being supplanted by Internet Mail Access Protocol version 4 (IMAP4), which offers better support for mobile users. POP3 is supported by Microsoft Exchange Server.
TIP
To troubleshoot problems with remote POP3 servers, use Telnet to connect to port 110 and examine the results as you try issuing various POP3 commands such as the ones just described.
A computer on a Microsoft Windows NT network that can assume the role of a master browser or a backup browser if required to do so. If a new backup browser is needed, the master browser can appoint a potential browser as a backup browser. If a new master browser is needed, an election takes place to determine which potential browser should assume the role. If a computer running Windows joins a Windows NT network and its MaintainServerList parameter is set to either Auto or Enabled, it informs the master browser that it is a potential browser. The MaintainServerList parameter is configured differently depending on the version of Windows involved:
Windows NT uses the following registry key:
Hkey_Local_Machine System CurrentControlSet Services Browser Parameters
Windows 95 and Windows 98 use the Browse Master property in File and Printer Sharing for Microsoft Networks.
Windows 3. x uses MaintainServerList in the system.ini file.
TIP
You should disable MaintainServerList on machines running Windows 3. x , Windows 95, and Windows 98 because these operating systems are used on client machines that can occasionally be rebooted, causing spurious elections to occur.
See also Computer Browser service
See Plain Old Telephone Service (POTS)
A special set of ROM routines that run whenever a PC is booted. The power-on self test (POST) is designed to test whether system components are functioning properly before attempting to boot the operating system, and checks such things as the RAM, keyboard, and disk drives. If a problem is detected during the POST, the system typically emits a series of beeps and displays a corresponding error message giving some indication of the problem. Specific problems are indicated by different numbers of beeps, but the interpretation of these varies depending on the BIOS used.
TIP
On newer Pentium II or III systems that use the popular AMI WinBIOS, use the following table to interpret the number of beeps in order to troubleshoot the problem.
POST Beep Codes for AMI WinBIOS
| Number of Beeps | Problem | Resolution |
| 1, 2, or 3 | Memory error | Check speed and voltage of dual inline memory modules (DIMMs), try reseating DIMMs, or replace DIMMs |
| 4 | Timer error | Replace motherboard |
| 5 | CPU error | Try replacing CPU, or replace motherboard |
| 6 | Gate A20 error | Try reseating keyboard controller chip, try replacing keyboard controller chip, or replace motherboard |
| 7 | Interrupt error | Replace motherboard |
| 8 | Video memory error | Try reseating the video RAM (VRAM), try replacing the VRAM, or replace video card |
| 9 | BIOS ROM error | Replace BIOS ROM chip |
A built-in group in Microsoft Windows NT and Windows 2000. The Power Users group is a local group that exists only on member servers and workstations. The initial membership of this group is empty. Generally speaking, a power user is a person who is familiar with the advanced features of a program’s user interface. In Windows NT, a power user is a user who has certain rights.
The Power Users group has preassigned rights including the following:
Log on locally
Access this computer from the network
Change the system time
Shut down the system
Power users also have the right to share and manage local disk resources and printers and to create and modify local user accounts on the local machine.
See also built-in group
See Point-to-Point Protocol (PPP)
A protocol for combining multiple physical WAN links into a single logical pathway to increase bandwidth. Microsoft’s Remote Access Service (RAS) for Windows NT and Window 2000 supports combining Plain Old Telephone Service (POTS) and Integrated Services Digital Network (ISDN) lines using PPP Multilink, as does Windows 98.
TIP
PPP Multilink must be enabled on both the dial-up networking client and the RAS server in order to work.
See Point-to-Point Tunneling Protocol (PPTP)
The entire wiring system in a building, including cabling, power lines, wiring closets, distribution centers, wall plates, and fixtures. Premise cabling should be installed according to the Electronic Industries Alliance and Telecommunications Industry Association (EIA/TIA) wiring standards and must comply with all state and municipal building codes and requirements.
How It Works
In computer networking, the premise wiring system is a hierarchical system based on the star topology, starting with the equipment room (main cross-connect) that houses the main telecommunications equipment for the particular building, including servers, Private Branch Exchanges (PBXs), and routers. The equipment room contains the facilities for telecommunications signals to enter and leave the building. It can be one room or several rooms on different floors, depending on the building layout and administrative considerations.
From the equipment room, a vertical backbone cable runs up the building riser or elevator shaft, connecting the equipment room with wiring closets (intermediate cross-connects) on each floor. Additional backbone cabling runs horizontally to secondary wiring closets (horizontal cross-connects) if necessary. No further cross-connects should be used; in other words, the hierarchy should be no more than three cross-connects deep.
The wiring closets contain cabinets or racks with patch panels, hubs, switches, and other equipment. Horizontal wiring runs from the patch panels through wall and ceiling spaces to wall plates and distribution boxes to form local area network (LAN) drops in the work areas where computers are set up. Patch cables or drop cables connect computers in the work area to the wall plates and distribution boxes.
See also cabling
Layer 6 of the seven-layer Open Systems Interconnection (OSI) reference model. The presentation layer structures data that is passed down from the application layer into a format suitable for network transmission. This layer is responsible for data encryption, data compression, character set conversion, interpretation of graphics commands, and so on. The network redirector also functions at this layer.
NOTE
Most real-world protocol suites, such as TCP/IP, do not use separate presentation layer protocols. The presentation layer is mostly an abstraction in real-world networking.
A digital signature and encryption scheme for secure exchange of e-mail and attached documents. You can use Pretty Good Privacy (PGP) to encrypt e-mail messages so that no one but the intended recipient can read them and to digitally sign messages so that the recipient can be sure of the identity of the sender and that the message has not been tampered with during transit.
How It Works
PGP uses the RSA or Diffie-Hellman public key cryptography algorithm and supports 128-bit keys. When you send a digital signature, a hashing algorithm generates a hash from the username and other information, which is then encrypted using the sender’s private key. The hashing algorithm is MD5 when you use RSA and SHA-1 when you use Diffie-Hellman. As in a typical public key cryptography system, the recipient uses the sender’s public key to decrypt the signature and verify the sender’s identity. The sender’s public key is retrieved by the recipient from a public PGP key management server such as the one maintained by Network Associates.
PGP is popular in the Internet community but does not scale well for corporate enterprise applications because its key management facilities are implemented as a distributed “web of trust” rather than the usual hierarchical certificate authority (CA) scheme.
On the Web
•
Network Associates home page : http://www.nai.com
See Primary Rate Interface ISDN (PRI-ISDN)
A Microsoft Windows NT domain controller that contains the master copy of the Security Account Manager (SAM) database. A Windows NT domain has only one PDC, which periodically undergoes directory synchronization to copy its directory database to back up domain controllers in the domain. The primary domain controller (PDC) must be the first computer installed in a domain and defines the domain.
NOTE
If a PDC needs to be taken offline for maintenance or repair or if it unexpectedly goes down, a backup domain controller (BDC) can be promoted to the role of PDC. This is necessary because BDCs contain read-only copies of the domain directory database, so user accounts cannot be modified and passwords cannot be changed unless there is a PDC on the network.
See also backup domain controller (BDC), domain controller
A computer running Microsoft Message Queue (MSMQ) Server that functions as a primary site controller (PSC) for one site and contains information about the enterprise configuration and the certification keys in its MSMQ Information Store (MQIS) database. The primary enterprise controller (PEC) also functions as an MSMQ Routing Server.
Administrators can install only one PEC on an MSMQ network. You must install the PEC before you install any primary site controllers.
In Microsoft Windows NT, the global group that is specified as primary for a particular user account. Users can be members of many different global groups within their domain, but only one of these global groups can be the primary group.
Primary groups are used when users running Windows NT Services for Macintosh or POSIX applications log on to the computer. The user’s primary group is the group that the owner of a particular resource works with most.
A name server that maintains its own local Domain Name System (DNS) database of resource records. A primary name server has a master copy of resource records for each zone over which it has authority. These records are stored locally on the name server in the form of a text file called the zone file. All changes to the resource records for a zone must be made on the primary name server.
Secondary name servers obtain their resource records from master name servers, which can be either primary name servers or other secondary name servers. The usual configuration when name servers are used within a TCP/IP internetwork for name resolution is one primary and one secondary name server, with the primary configured as the master name server for the secondary (which is sometimes called the slave name server). If Microsoft Windows NT is used for the DNS servers, the tool for configuring name servers is DNS Manager, a Windows NT administrative tool. In Windows 2000 the analogous tool is the DNS console.
See also Domain Name System (DNS)
A partition on which you can install a bootable operating system and its associated file system. Primary partitions cannot be subdivided into further segments, as extended partitions can. The partition table on a drive’s master boot record can contain entries for up to four primary partitions or three primary and one extended partition. Only one primary partition at a time can be the active partition (contain the currently running operating system files). In Microsoft Windows NT, the active partition is also known as the system partition. Primary partitions are used in multiboot systems to isolate the files of each operating system from one another.
See also extended partition
A standard form of communication on Integrated Services Digital Network (ISDN) communication systems. Primary Rate Interface ISDN (PRI-ISDN) connections consist of 24 digital channels divided between 23 B channels and a single D channel. The B channels carry the voice or data between the customer premises and the telco’s central office (CO), while the D channel is used for establishing connections and signaling. PRI-ISDN is often referred to as 23B+D because of the channels that it uses.
The bandwidth of each B channel and of the single D channel is 64 Kbps, so the total bandwidth of PRI-ISDN is 1.544 Mbps, which is identical to that of a T1 circuit. By using the bonding protocol, the 23 B channels can be combined to form a single 1.472-Mbps data channel. The European version of PRI-ISDN uses 31 B channels and one D channel, providing the bandwidth of an E1 circuit.
See also Basic Rate Interface ISDN (BRI-ISDN), Integrated Services Digital Network (ISDN)
The main ring used in the Fiber Distributed Data Interface (FDDI), which uses a dual ring topology. The primary ring is the only ring used unless it has a fault, in which case the network reconfigures itself to use the secondary ring with the data traveling in the opposite direction. The dual ring configuration provides FDDI with fault tolerance.
TIP
Run the FDDI primary ring and secondary ring along different physical paths to make the network more redundant. An accident or disaster affecting one of the rings will not affect the other.
See also Fiber Distributed Data Interface (FDDI), secondary ring
A computer running Microsoft Message Queue (MSMQ) Server that functions as the site controller for the first MSMQ site you create. The primary site controller (PSC) maintains a database of information concerning the computers and queues in the site. Each site usually has its own PSC, and you can install only one PSC for a given site.
For load balancing and failure recovery purposes, you can install one or more backup site controllers (BSCs) in each MSMQ site. BSCs contain a read-only copy of the PSC or primary enterprise controller (PEC) database. MSMQ sites do not require BSCs, but it is usually a good idea to install one or more of them in each MSMQ site. You must install a PSC or PEC before you can install any BSCs.
A way of connecting one printer to multiple print devices. In Microsoft Windows terminology, a print device is the physical hardware that does the printing, while a printer is a software interface on a computer that enables jobs to be sent to a print device. Normally, a printer is configured for each individual print device. Using a printing pool, you identify several print devices as a single printer to the operating system. When a client sends a print job to a printing pool, the printer sends the job to the first available print device managed by the printer. Clients can thus print jobs without having to check to see which print device is free.
Printing pools are used in networks with high printing volume and also to provide a form of fault tolerance. Printing pools also simplify the administration of large numbers of print devices. You can create printing pools on print servers running Windows NT and Windows 2000.
NOTE
The print devices in a printing pool must be the same make and model or at least be similar devices that use the same printer driver. Print devices that are pooled can be a mix of local and network interface print devices. Place pooled print devices in close physical proximity to one another so that users do not have to search for the device that printed their job.
TIP
If you don’t have identical print devices and thus cannot create a printing pool, you can take other measures to meet the needs of increased printing volume:
Share an existing printer that is currently not shared for network use.
Configure priorities between printers to enable critical documents to be printed before noncritical ones.
Institute company policies on how to use printers properly, and audit printer usage.
See also printing terminology
In Microsoft Windows, the following are printing-related terms:
Print device: A hardware device that produces printed output, such as a LaserJet, ink-jet, or dot-matrix print device. Most people loosely refer to these devices as “printers,” but the term “printer” has a specific meaning in the Windows operating system, as described below.
Printer: A software interface installed on a Windows computer that allows users and applications to print to a print device. Microsoft uses the term “print device” to refer to the actual hardware device; “printer” refers to the software interface that controls that device. To create a printer, you use the Add Printer Wizard in the Printers folder.
Print server: A computer with which a print device is associated. A print server receives print jobs from clients and sends them to the print device.
Printer driver: A series of files that convert printing commands into machine-specific language for sending them to a print device. Each model and make of print device has its own specific printer driver.
NOTE
Print devices can be further subdivided into two types:
Local print device: A print device that is locally attached to the parallel or serial port on the print server. If a local print device is being used only on the local machine, its software interface is called a “local printer.” If a local print device is shared, clients can access it over the network and its software interface is called a “network printer” from the perspective of the clients.
Network-interface print device: A print device that has its own built-in network interface card (NIC) and can be plugged into the network anywhere that a local area network (LAN) drop is free. A network-interface print device is not connected directly to the print server; it is managed remotely by the print server.
TIP
Keep network-interface print devices on the same network or subnet as their print server to minimize the extra network traffic. Be sure that your print server has sufficient RAM for processing documents and sufficient disk space for spooling print jobs. Dedicating a computer to the role of print server is usually recommended, especially if that computer will manage several print devices.
A built-in group in Microsoft Windows NT and Windows 2000. The Print Operators group is a local group on computers that run Windows NT and a domain local group on a Windows 2000 domain controller. Print operators are users who can administer network printers. The initial membership of this group is empty. The Print Operators group has the following preassigned rights:
Log on locally
Shut down the system
Print operators also have the right to set up and configure network printers.
See also built-in group
A set of permissions assigned to users and groups to control access to the printers on a Microsoft Windows NT print server. Suitable print permissions are an important part of network administration, especially in enterprise-level networks with different administrative levels. There are four levels of print permissions, as described in the following table.
Print Permissions
| Permission | What It Allows Users to Do |
| no access | Cannot connect to or print to a printer |
| | Connect to a printer Print a document Manage your own documents only |
| manage documents | Print permissions plus: Pause and restart any document Delete any document Manage job settings for all documents |
| full control | Manage documents permissions plus: Share a printer Change printer properties Delete a printer Change printer permissions |
NOTE
On a Windows 2000 print server, the full control permission is called “manage printers.” Also, instead of using a no access permission, you permit or deny the manage printers, manage documents, or print permissions. You can, in addition, click the Advanced button on the Printer Properties property page to configure more granular customized sets of printer permissions.
TIP
In Windows 2000, you can remotely administer printers using a Web browser by accessing the Uniform Resource Locator (URL) http://Print_Server_Name/printers. Administrators can configure printer permissions and settings, check the status of printers, and create real-time reports on printer usage.
A server that manages a printer on a network. The printer can be directly connected to a port on the print server (a local printer), or it can have its own built-in network interface card (NIC) and be connected directly to the network (a network printer). Clients that want to print jobs send them to the print server, which queues or spools the jobs and then sends them to the printer. Microsoft Windows NT Server is a good operating system for running a print server on your network.
Instead of dedicating a computer to managing a printer on a network, you can use a stand-alone print server device. These devices generally have a small footprint—some are even pocket-sized—and can be used to attach a printer anywhere in the network. Typically, an RJ-45 port on the device can be plugged directly into an Ethernet hub or into a wall plate in a work area, while an IEEE 1284 port on the device is connected to the printer. Stand-alone print server devices generally have built-in support for a variety of protocols (such as TCP/IP, IPX/SPX, NetBEUI, and Data Link Control) and platforms (such as Windows 2000, Novell NetWare, and UNIX) and support a wide variety of makes and models of printers.
Other features of stand-alone print server devices can include the following:
Support for two or four parallel printer connections
Support for Line Printer Daemon/Line Printer Remote (LPD/LPR) or Dynamic Host Configuration Protocol (DHCP)
Support for Token Ring or AppleTalk networking architectures
Any hardware device that enables two or more computers to directly share one or more attached printers without using a network. Print sharers include the following:
Manual switch boxes, on which a user turns a rotary switch to select which computer controls the printer. The manual switch boxes are usually in a 2-to-1, 4-to-1, or 6-to-1 configuration. A special switch called an X-switch can allow either of two computers to print to either of two printers.
Electronic print-sharing switches, on which users also use knobs or toggle switches to select a computer or printer. These switches have solid-state circuitry inside that does the switching, unlike manual switch boxes, which have simple metallic contacts.
Port-contention or FIFO (first in, first out) switches, which automatically monitor all input ports. When a signal enters an input port from a computer, the switch automatically assigns that port to the output printer port.
Code-operated switches, which examine the input (computer) data ports for an ASCII string indicating which output (printer) port to switch the incoming printer data to.
Scanning switches, which function like port-contention switches except that they sequentially scan the input ports instead of monitoring them all continuously.
NOTE
If more than two computers need to share a printer, the best solution is to connect the computers to a local area network (LAN) and use a print server to set up a shared network printer. The print sharing devices listed previously are intended primarily for non-networked computers that must be directly connected to printers. In a small peer-to-peer networking setting, you can use a machine running Microsoft Windows 95 or Windows 98 that has File and Printer Sharing installed on it to share an attached printer with other workstations. In larger networks, Windows 2000 Server is a better choice.
TIP
Don’t use manual switch boxes with laser printers. The switching mechanism can cause voltage spikes that can seriously damage the printer.
A telephone switch at the customer premises that supports multiple independent telephone extensions. Private Branch Exchanges (PBXs), which are installed by a telco, save businesses the cost of supplying an individual local loop connection for each employee because employees can share external trunk line connections. The PBX provides connectivity between the client’s private telephone system that it supports, and the telco’s public trunk lines. In Europe, a PBX is known as a Private Automatic Branch Exchange (PABX).
How It Works
PBXs were originally switch consoles controlled by human operators, who would plug and unplug patch cords to establish connections for customers. The modern electronic PBX (also known simply as a switch) is a solid-state device that essentially establishes a private switching system that mimics the functions of a telco’s much larger central office (CO) switching facility. PBXs allow businesses to have better control of their own telecommunications equipment, and they reduce costs by more effectively routing local telephone traffic.
Typically, a PBX is leased and installed in the main equipment room of a building or campus by a telco or other service provider. It handles all calls initiated and received in the building. If an outgoing call is directed to another line on the PBX, the PBX routes the call directly to its destination instead of forwarding it to the local CO. Outgoing calls directed to destinations outside the PBX are routed to the CO for handling.
A modern digital PBX can handle data, fax, and other forms of traffic in addition to voice traffic. Telephones and other devices are connected by individual circuits directly to the PBX unit, while trunk lines coming in from the outside terminate at a multitrunk channel band (MCB) unit. The MCB interfaces with the main distribution frame (MDF), which provides the individual circuits that connect the outside world to the PBX unit. The more circuits that the MDF creates from the trunk lines, the more simultaneous outgoing calls can be initiated and received by users of the PBX system. Add-ons for the PBX unit can include call management systems (CMS’s), which provide call notification and control services; call accounting services; and modem pools for remote dial-up access.
Graphic P-11. Private Branch Exchange (PBX).
PBX switches come in various sizes. The smallest is a 3-by-8 switch that supports three business lines and eight extension lines. This configuration permits eight phones to be connected, but only three of them can make or receive calls at a time.
PBXs support a number of features, including the following:
Direct Inward Dialing (DID): A form of call routing that allows outside users to dial directly to any of the extensions
Direct Outward Dialing (DOD): A form of call routing that allows extensions to dial directly to any outside phone number
Station-to-Station Dialing (SSD): Allows any extension to call any other extension without using a business line
Most modern PBXs support digital phone extensions and T1 or multirate Integrated Services Digital Network (ISDN) for their telco connection. PBX boards can also be installed in servers to support computer-telephony integration (CTI). Many products and configurations are available.
NOTE
An alternative to installing a PBX at the customer premises is to lease a Centrex service from the telco’s CO. This service offers similar features to a PBX but from a remote location, and it is managed remotely by the telco.
One of the two databases in the information store on a computer running Microsoft Exchange Server. The private information store stores content for mailboxes homed on the server. It consists of a number of files stored in the \mdbdata directory on the Exchange server. These files include the following:
Priv.edb: The actual database file
Edbxxxx.log: Transaction files used to track changes to the database
Edb.chk: A checkpoint file to keep track of transactions in edbxxxx.log that are uncommitted
Res1.log and Res2.log: Reserved log files used in low disk space conditions
Temp.edb: A temporary file used for storing transactions that are in progress
A feature of Component Services (Microsoft Transaction Server) and Internet Information Services (IIS) that allows multiple critical Web applications to be hosted on a single IIS server. Running each application as an isolated process in its own memory space leads to greater reliability because the failure of one unstable application will not affect any other running applications and cannot crash the IIS server.
A component of the Internet Explorer Administration Kit (IEAK) that is used to manage users’ desktop settings remotely from a central station. Profile Manager integrates with Microsoft’s System Policy Editor and can be used to
Manage system policies for implementing system and user restrictions
Create or import .adm files, which are templates for policy files
Centrally maintain both 16-bit and 32-bit Microsoft Windows policies
Enable or disable individual restrictions
NOTE
In Windows 2000, the functionality of the Profile Manager is incorporated into the Group Policy snap-in.
An ongoing project of the Institute of Electrical and Electronics Engineers (IEEE) for defining local area network (LAN) and wide area network (WAN) standards and technologies. The 802 specifications define the operation of the physical network components—cabling, network adapters, and connectivity devices such as hubs and switches.
Project 802 has a number of subsections, including the following:
802.1: Internetworking standards
802.2: The logical link control (LLC) layer of the Open Systems Interconnection (OSI) reference model data-link layer
802.3: Ethernet (Carrier Sense Multiple Access with Collision Detection)
802.4: Token Bus LAN
802.5: Token Ring LAN
802.6: Metropolitan area network (MAN)
802.7: Broadband technologies
802.8: Fiber-optic technologies
802.9: Integrated voice/data networks
802.10: Network security standards and technologies
802.11: Wireless networking technologies and standards
802.12: Demand priority access technologies
802.14: Cable television access
The Project 802 standards are constantly evolving, and new subcategories are being created to standardize new networking technologies.
A mode of operation of a network interface card (NIC) in which the NIC accepts all frames on the wire, including those not specifically directed to it. A NIC operating in promiscuous mode reads every frame it receives, whether the frames are broadcast, multicast, or directed. In some networks, this can be a security problem because nodes that act “promiscuously” can be configured not only to read frames but also to store them and even retransmit them. Sensitive information can thus be intercepted on the network and retransmitted to remote stations. This problem can occur in both Ethernet and Token Ring networks when NICs are configured to act promiscuously.
NOTE
Network driver interface specification (NDIS), as of version 4, supports a capturing mode called local only, which uses fewer CPU resources than promiscuous mode but supports capturing of all frames for Microsoft Network Monitor.
In Microsoft Windows NT, Windows 95, Windows 98, and Windows 2000, a feature for configuring system and user software settings. You can access the property sheet for an object by right-clicking the object and choosing the Properties command from the context menu. The following screen capture shows the property sheet for a file called test.txt. Property sheets contain various controls such as text boxes, check boxes, option buttons, command buttons, scrolling list boxes, drop-down list boxes, and tabs. Property sheets make Windows easy to use compared to those operating systems such as MS-DOS that use command prompt.
Graphic P-12. Property sheet.
A set of rules for sending information over a network. Protocols can include rules concerning any or all of the following functions:
Data transmission mechanisms
Communication session initialization and termination
Addressing and routing
Authentication and verification
Encryption and compression
Error correction
Protocols are usually classified according to the layer they correspond to in the Open Systems Interconnection (OSI) reference model for networking. Types of protocols include the following:
Data-link protocols: Govern the framing of data, physical addressing of network nodes, and media access control methods. For local area networks (LANs), these primarily include Ethernet, Token Ring, and Fiber Distributed Data Interface (FDDI). For wide area networks (WANs), they include Point-to-Point Protocol (PPP), High-level Data Link Control (HDLC), frame relay, Asynchronous Transfer Mode (ATM), and X.25.
Network protocols: Handle link services and are responsible for addressing, routing, and error checking. Examples include NetBEUI, Internetwork Packet Exchange (IPX), NWLink, and Internet Protocol (IP).
Transport protocols: Enable the establishment of sessions and ensure reliable flow of data. Examples include NetBEUI, Sequenced Packet Exchange (SPX), NWLink, and Transmission Control Protocol (TCP).
Application layer protocols: Enable applications to access network services. Examples include Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP), Telnet, Simple Mail Transfer Protocol (SMTP), Simple Network Management Protocol (SNMP), Network News Transfer Protocol (NNTP), X.400, X.500, Server Message Block (SMB), and Network File System (NFS).
Some protocols have been developed by specific vendors and then accepted as de facto standards by the industry, while others were initially formulated by independent standards bodies and then accepted and implemented by vendors. The most widely implemented protocols are those relating to TCP/IP and the Internet.
A general term for a device that enables communication between networks or transmission systems that use different protocols. Protocol converters are often used in mainframe computing environments; they enable one device to emulate the communication functions of another device. For this reason, a protocol converter is sometimes known as an emulator, and it can be either hardware-based or software-based.
How It Works
One type of protocol converter allows you to communicate asynchronously using a PC to a mainframe host over a synchronous communication link. You can thus use a PC as the front end to the host instead of using expensive synchronous terminals. The PC typically emulates a 3270 terminal for remote connections or a 5250 terminal for local connections.
For example, you can turn a PC into a 5250 terminal by installing a 5250 emulator card. Use twinax cabling to connect the port on the card directly to the AS/400 or System 390 mainframe. The 5250 emulator software running on the PC typically supports multiple concurrent 5250 sessions.
To support this synchronous/asynchronous conversion, the emulation hardware/software must perform several conversions:
Connect the twinax or coax synchronous connection from the host to an asynchronous RS-232 connection for the PC. For a remote connection, the converter might include X.21 or V.35 serial interfaces as well.
Graphic P-13. Protocol converter.
Take the Synchronous Data Link Control (SDLC) data stream from the host and convert it to an asynchronous format.
Perform synchronous EBCDIC to asynchronous ASCII conversion and translate standard input/output into appropriate screen/keyboard mappings.
NOTE
You can also use protocol converters to connect ASCII printers to AS/400 or System/3x mainframe hosts. A protocol converter for this purpose is sometimes called a printer emulation card.
A text file that provides resolution of protocol names into their respective RFC-defined protocol numbers on a TCP/IP network. The entries in the protocol file are friendly names for TCP/IP protocol numbers and can be used for well-known service (WKS) records in Domain Name System (DNS) servers and other Windows Sockets applications.
How It Works
The protocol file is in the following location on computers running Microsoft Windows:
Windows NT and Windows 2000: %SystemRoot%\system32\drivers\etc\protocol
Windows 95 and Windows 98: \Windows\protocol
Each line in the protocol file contains the standard name for a protocol followed by the assigned number as defined in Request for Comments (RFC) 1060, an alias, and an optional comment prefixed with a pound sign (#). The following example comes from the sample protocol file included with Windows 95 and Windows 98:
ip 0 IP # Internet protocol icmp 1 ICMP # Internet control message protocol ggp 3 GGP # Gateway-gateway protocol tcp 6 TCP # Transmission control protocol
See also hosts file, lmhosts file, networks file, services file
A collection of protocols that work together as a group. Examples of protocol suites include the following:
NetWare’s Internetwork Packet Exchange (IPX) and Sequenced Packet Exchange (SPX) and related protocols, such as NetWare Core Protocol (NCP) and Service Advertising Protocol (SAP)
The Internet’s TCP/IP protocol suite, which consists of Internet Protocol (IP), Transmission Control Protocol (TCP), and related protocols such as Address Resolution Protocol (ARP), Internet Control Message Protocol (ICMP), and Hypertext Transfer Protocol (HTTP)
AppleTalk and its related protocols, such as AppleShare, EtherTalk, and LocalTalk
A draft standard from the Internet Engineering Task Force (IETF) that defines ways that Internet service providers (ISPs) can deliver different traffic types to their clients and bill them accordingly. Provider Architecture for Differentiated Services and Traffic Engineering (PASTE) can be implemented without adding overhead to an ISP’s routers, whose tables are often burdened by the rapidly expanding address space of the Internet.
How It Works
Existing technologies such as Cisco Systems’ tag switching require that routers maintain state information for every virtual circuit they detect. PASTE eases this requirement by aggregating traffic flows that share a common path into a trunk. Routers need only maintain tables of trunks instead of tables for virtual circuits, which greatly reduces router overhead. Packets can then join or leave a trunk at any router. PASTE uses the Multiprotocol Label Switching (MPLS) protocol and the Resource Reservation Protocol (RSVP) to provide these differentiated services.
The configuration of options on telecommunications equipment at the customer premises. For example, an analog telephone line can be provisioned with only a few options, such as caller ID and call waiting. An Integrated Services Digital Network (ISDN) line can be provisioned with many more options, and the configuration of the ISDN equipment at the customer premises must match that at the telco’s central office (CO) for communication to function properly. For example, the service profile identifier (SPID), which is a phone number with additional digits prefixed and appended to it, must be configured properly on the customer’s ISDN equipment for the telco’s ISDN switching equipment to recognize the type of equipment that is attached, recognize whether one or more devices is attached, and enable calls to be routed appropriately to the equipment.
A type of proxy server that caches Web pages that users request on the Internet. You can use a proxy cache server like a regular proxy server at the border of a private corporate network in order to cache the Web pages returned from the Internet when users in the private network request them. When users request these pages again, the pages are returned instantly from the cache; a new request need not be sent over the Internet. This speeds up browsing for frequently accessed Web sites and reduces the amount of bandwidth used on the corporate Internet link.
Proxy cache servers can also be used at Internet service providers (ISPs) and at strategic locations on the Internet’s high-speed backbone to provide relief to heavily accessed Web servers and to reduce overall backbone traffic.
NOTE
Microsoft Proxy Server supports two kinds of caching for the Web proxy service:
Passive caching: Web pages that clients request are cached for later retrieval if requested.
Active caching: Proxy Server tries to anticipate which Web pages clients will request, and when the server has idle time and the network is sufficiently quiet, Proxy Server requests the pages and stores them in the cache.
A computer that can act on the behalf of other computers to request content from the Internet or an intranet.
How It Works
Proxy servers act as secure gateways to the Internet for client computers. They are transparent to client computers—a user interacting with the Internet through a proxy server is not aware that a proxy server is handling the requests unless the user tries to access a resource that the proxy server is configured to disallow. Similarly, the Web server receiving the requests from the proxy server interprets these requests as though they came directly from client computers.
Proxy servers can be used to secure private networks connected to unsecured public networks such as the Internet. They have greater functionality than packet-filtering routers because they operate at a higher level of the protocol stack and afford greater control over monitoring and managing network access. A proxy server functioning as a security agent for a private network is generally called a firewall.
Two types of proxy servers are used in network firewall environments: circuit-level gateways and application-level gateways. Circuit-level gateways establish virtual circuits between machines on the internal private network and the proxy server on the border of the private network. The proxy server controls all connections between the internal private network and the external public network. If a client on the private network wants to access the Internet, for example, the Hypertext Transfer Protocol (HTTP) request packet generated by the client’s Web browser traverses the virtual circuit to the proxy server; the proxy server then changes the source IP address of the packet to that of the external (public) network interface of the proxy server and forwards the packet onto the Internet. When a remote HTTP server on the Internet sends a response, the proxy server routes this response back through the virtual circuit to the client that made the request.
An application-level gateway can implement security policies for analyzing packets that reach the external (public) interface of the proxy server from distrusted public networks. These security policies can examine packet addresses and other header information, permit or deny packets on the basis of their contents, and modify the address, header, or contents of packets that they monitor in order to hide key information about the internal network’s applications and services. Application-level gateways provide proxy services only for specifically configured applications and protocols such as HTTP, File Transfer Protocol (FTP), Simple Mail Transfer Protocol (SMTP), and Telnet. For each type of application for which you want to regulate access through the firewall, you must install and configure a related proxy service on the proxy server. Applications and protocols for which a proxy service is not installed cannot be accessed through the firewall.
NOTE
Instead of using a proxy server, you can provide modems for and run telephone lines directly to each user who needs Internet access, but this option is costly. You can also configure a physically separate network with several computers that have shared Internet access, but this is cumbersome for users. Advantages of using a proxy server include the following:
It provides a single, secure gateway to manage.
It can provide different types of access to the Internet as appropriate for each group of users.
It can monitor and track Internet usage for each user.
Many users can share a single high-speed Internet connection.
Microsoft Proxy Server is an example of a proxy server and firewall product that provides a secure gateway for your network to the Internet.
See primary site controller (PSC)
A group of protocols that are part of the X.400 messaging standards. Five P-series protocols relate to messaging systems that support X.400, such as Microsoft Exchange Server:
P1 Protocol: Specifies the layout of messages transferred from one Message Transfer Agent (MTA) to another. This protocol specifies that X.400 messages consist of two parts: a P1 header, which acts as an envelope and must contain a globally unique recipient address for message routing and control purposes, and a P2 message, which is the actual content of the message.
P2 Protocol: Defines the format for transmitting the content of an X.400 message. This format includes a P2 header (which is not used because the P1 header provides the necessary routing information for the message) and a P2 body, which is the actual content of the message and consists of one or more body parts of various types (such as text, images, voice, or telex).
P3 Protocol: Specifies how a user agent (UA) communicates directly with an MTA for sending or receiving a message. This protocol is not used as often as the P7 Protocol for the same reason that Post Office Protocol version 3 (POP3) is used instead of Simple Mail Transfer Protocol (SMTP) to receive Internet mail.
P7 Protocol: Specifies how a UA communicates with a message store (MS) in order to selectively retrieve messages from the store and delete unwanted messages without downloading them.
P22 Protocol: A 1988 revision of the P2 Protocol that clarifies and extends certain features of P2.
See also X.400
See Public Switched Telephone Network (PSTN)
See pointer (PTR) record
A type of recipient in Microsoft Exchange Server that can store messages and documents for sharing with other users in an Exchange organization. Public folders can contain simple messages, attachments, multimedia clips, binaries, and any other type of file. They can also contain custom forms that facilitate contributing and viewing information.
NOTE
To create public folders in an Exchange organization, you should use the client program Microsoft Outlook. Public folders created with Outlook can later be configured using the Exchange Administrator program, which you cannot use to create public folders.
A copy of a public folder’s contents stored on another Microsoft Exchange Server. All replicas of a public folder are equivalent—there is no master replica for a public folder.
TIP
When planning where to host public folders in your Exchange organization, consider the following:
The volume of information that will be stored and how much it will increase over time
How long information should be retained before it is deleted
How many users will access the information and how frequently they will access it
One of the two databases within the information store on a Microsoft Exchange Server computer. The public information store stores content for public folder replicas on the server. The public information store consists of a number of files in the \mdbdata directory on the Exchange server. These files include the following:
Pub.edb: Actual database file
Edbxxxxx.log: Contains transaction files for tracking changes to the database
Edb.chk: A checkpoint file to keep track of transactions in edbxxxxx.log that are uncommitted
Res1.log and Res2.log: Reserved log files used in low disk space conditions
Temp.edb: A temporary file used for storing transactions that are in progress
Also known as asymmetric cryptography, a popular encryption method developed by Martin Hellman and Whitfield Diffie in 1976 that is used for securing transmission of data over distrusted networks such as the Internet.
How It Works
Traditional cryptography involves a private or secret key that was shared by the individuals involved in the transmission. The key is a mathematical entity that the sender can use to encrypt a message and the receiver can use to decrypt it. This traditional form of cryptography is known as secret key cryptography or symmetric cryptography. The main problem with this form of cryptography is the question of how the owner of the key can securely transmit the key. In other words, the main problem is one of key management—how to create, store, and transmit the key to those who will need it to decrypt messages sent to them.
Public key cryptography solves this problem by creating a set of two different keys for anyone needing to transmit encrypted information. A precise mathematical relationship exists between the two keys, which together are called a key pair. Both keys are produced at the same time using a mathematical algorithm such as RSA. As a result, when either one of the two keys is used to encrypt a message, the other can be used to decrypt it.
The two keys in a key pair are as follows:
The private key: Held privately by the owner of the key pair and kept secret from anyone else. The responsibility for safe storage of the private key rests entirely with the key pair owner, who has no need to transmit the private key to others.
The public key: Made available by the key pair owner to anyone who requests it. Because the public and private keys are related mathematically, in principle someone could take another person’s public key, perform complex mathematical calculations on it, and extract the corresponding private key. The solution is to use keys sufficiently long and with a sufficiently complex mathematical relationship so that it is all but impossible to extract the private key from the public one.
Once a key pair is generated for someone, that person can use it to encrypt messages and to digitally sign messages so that the recipient can be sure of the identity of the sender.
Of course, the whole public key cryptography system is ultimately founded on trust. All persons who are issued key pairs must trust the third-party authority who provided the key pairs. This trusted authority is called a certificate authority (CA). Someone who wants to obtain a key pair from a CA must contact the CA and present proof of identity. This could involve a face-to-face meeting, examination of a driver’s license with photograph, or some other method of establishing a user’s identity.
NOTE
Network administrators can use Microsoft Certificate Server, which is included in the Microsoft Windows NT 4 Option Pack, to establish their own CAs. Users can then transmit encrypted and digitally signed e-mail messages by using Microsoft Exchange Server or establish secure Web sites that use the Secure Sockets Layer (SSL) protocol with Internet Information Services (IIS).
See also digital certificate, digital signature, encryption, Secure Sockets Layer (SSL)
A set of services that support the use of public key cryptography in a corporate or public setting. A public key infrastructure (PKI) enables key pairs to be generated, securely stored, and securely transmitted to users so that users can send encrypted transmissions and digital signatures over distrusted public networks such as the Internet. An effective, trustworthy public key infrastructure is essential for secure e-mail and World Wide Web (WWW) transactions, e-commerce, and virtual private networks (VPNs).
How It Works
Generally, a public key infrastructure consists of the following coordinated services:
A trusted certificate authority (CA) that can verify user identities and issue users digital certificates and public/private key pairs. Sometimes the verification of user identities is performed by a separate registration authority (RA), but this service can also be integrated with the CA.
A certificate store in which users can access the public keys of other users for encrypting messages or validating digital signatures. This store is usually based on the X.500 directory recommendations.
A digital certificate and key management system for generating, storing, and securely transmitting certificates and key pairs to users who request them.
Public key infrastructures can have different scopes. For example, a corporate enterprise can use Microsoft Certificate Server to establish a PKI for all its users and for those of partner companies such as suppliers and wholesalers. The PKI system can then be used to secure transactions between users that are sent over the Internet. PKIs can also be established on a national or global scale to support secure e-commerce transactions over the Internet involving users and vendors who are geographically and politically separated. PKIs on this scale consist of a hierarchy of CAs managed by different governments or companies and linked to a trusted root CA (such as the U.S. government). The current leader in worldwide PKI implementation is probably VeriSign, Inc., which is both a vendor of CA software and a CA.
In order for a public key infrastructure to work, it must be implemented in a hierarchical fashion with authorities, super-authorities, and root authorities, similar to the Internet’s Domain Name System (DNS). Standards bodies and cryptography vendors such as PKIx of the Internet Engineering Task Force (IETF), Pretty Good Privacy (PGP), Simple Public Key Infrastructure (SPKI), and Public Key Cryptographic Standards (PKCS) have proposed a global public key infrastructure, but there is no universal standard that has been agreed upon for a public key infrastructure, and implementations of the existing standards are often not interoperable.
On the Web
•
VeriSign, Inc. : http://www.verisign.com
The public telephone network managed by the local telco and long-distance carriers. The Public Switched Telephone Network (PSTN) consists of a digital backbone of switched circuits together with the analog local loop wiring still found in many residences. The PSTN is also known as the Plain Old Telephone Service (POTS), although that term specifically relates to the older, nondigital portion of the PSTN. The PSTN provides the most popular basis for creating wide area networks (WANs) through both leased lines and dial-up lines between local and remote networks. PSTN is often used in wide area networking because of its ubiquitous nature—local loop connections exist almost everywhere in the world.
In Active Directory of Microsoft Windows 2000, the process of making directory objects accessible to users on the network. Objects created in Active Directory are automatically published on the network. For example, when you create a new user object (information about that user, such as the user’s phone number and e-mail address) users on the network can look up that information using Active Directory.
If an object that doesn’t reside in Active Directory (such as a shared folder or shared printer) is published, Active Directory points to its location on the network. Most objects are automatically published in Active Directory if they reside on computers running Windows 2000, but you might have to manually publish the location of other objects, such as shared folders and printers on downlevel computers running Windows NT.
TIP
When you consider whether to publish an object in Active Directory, think about whether the information will be changed frequently. Published information should be relatively static. Information should be published when it will be useful to a large segment of the enterprise community. Structured information is more useful to publish than individual items such as files, which should be published instead in file systems accessed through share points. Applications can publish their connection points and application data in Active Directory.
A common method of converting analog signals into digital signals.
How It Works
Pulse code modulation (PCM) devices receive analog signals with continually varying voltages and quantize these signals into discrete voltages sampled at regular time intervals, typically 8000 times per second, with each sample being 8 bits in size. This provides a total transmission rate of 64 Kbps, as in Integrated Services Digital Network (ISDN) digital telephone communication. The result of this quantization process is a series of discrete voltages over time. The voltage levels correspond to powers of 2 and represent a series of binary numbers so that the output of a PCM device is essentially a binary number.
A typical PCM device consists of a sample-and-hold circuit that samples the analog voltage signal and holds it long enough so that an analog-to-digital converter can convert it into digital (binary) format. A single device plus its associated software that can perform both the analog-to-digital conversion and its reverse is known as a codec or coder/decoder.
See permanent virtual circuit (PVC)
See polyvinyl chloride (PVC) cabling
See Microsoft Personal Web Server (PWS)