Chapter 11: Security
In Brief
As sad as I am to admit this, the attitude of most administrators is "security through obscurity." This expression means that the best way of dealing with security holes is ignoring them, hoping no one will find them, and praying they will go away. Unfortunately, this attitude never works. It seems nowadays there is a new virus or security hole being publicized daily. The days of merely running FDISK /MBR or deleting PWL files are over. Viruses and intruders are more sophisticated than ever. In this chapter, you will learn about the Windows security architecture and how to decrease the chances of unauthorized entry.
Hackers and Crackers
If you can think of system security as a war, then hackers and crackers are your opponents. Before you go into battle, it's always good to know a little about your opponents. Here is the truth about a common myth: Hackers never intentionally damage data. Hackers are knowledgeable computer users whose pure goal is to solve problems and continually learn about the inner workings of operating systems, applications, and transmission methods. Although their methods of obtaining information may be questionable, they tend to create tools to identify or improve upon system weaknesses. Hackers like to document and publicly share their information with all who are willing to learn. Hackers usually receive bad press because people don't understand the difference between the terms "hackers" and "crackers."
Crackers are knowledgeable computer users whose goal is to break into systems and damage or steal data. They tend to reverse-engineer programs and illegally use them for even more illicit purposes. Cracking techniques usually do not involve skillful or complicated methods, but rather crude methods such as stealing files from trash bins or tricking other users into handing them information. Examples of crackers are users who sniff the network for passwords, pirate software, write Trojan horse programs or viruses, or crash the network with broadcasts or email bombs .
| Tip | For more information about hackers and crackers, visit http://www.hackers.com. |
Security Configuration and Analysis Tool
The Microsoft Security Configuration and Analysis tool (MSSCE) provides a centralized method to analyze or modify a system's security settings. Figure 11.1 shows this tool. MSSCE is a Microsoft Management Console (MMC) snap-in that allows you to create or use security templates to apply to your environment. These security settings are stored in configuration files and can be applied to all the machines in your environment.
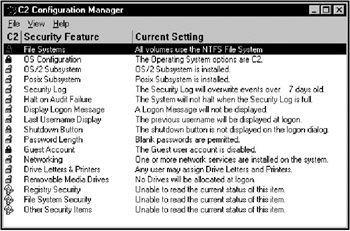
Figure 11.1: The Security Configuration and Analysis tool.
Predefined Security Templates
The MSSCE includes several predefined templates in the %WINDIR%\Security\Templates directory. The security templates included with the MSSCE are:
-
Basicdc.inf ”Default domain controller
-
Basicsv.inf ”Default server
-
Basicwk.inf ” Default workstation
These three basic security templates contain the standard security settings for each system.
-
Compatws.inf ”Compatible workstation or server
The compatibility template contains lower security settings to allow regular users maximum control of installed applications. Applying the compatibility template will remove all users from the power users group .
-
Dedicadc.inf ”Dedicated domain controller
The dedicated template contains security settings for domain controllers that will not be running server-based applications.
-
Hisecdc.inf ”Highly secure domain controller
-
Hisecws.inf ”Highly secure workstation or server
The high security templates provide the maximum security settings for the system. Applying this template on a Windows 2000 system will prevent that system from communicating with other Windows NT systems.
-
Securedc.inf ”Secure domain controller
-
Securews.inf ”Secure workstation or server
The secure templates are the recommended security settings.
Important Security Practices
Here is a list of several security practices to help protect your environment:
-
Administrators should always lock their system when not in use. This should be a top priority for administrators. It takes only a few seconds of distraction for an intruder to go to work under your logged-on account.
-
Do not allow other accounts to access or log on to an administrator's system. If another user can access your system (even if you are not logged on), he or she can potentially extract passwords, grab your files, and more.
-
Always use the latest security patches and service pack. It seems Microsoft is always releasing security patches and service packs to combat system exploits. These patches don't do any good unless they are actually loaded onto your system.
-
Increase the minimum password length. To slow down bruteforce password utilities, you can force users to use longer passwords by increasing the minimum password length.
-
Passwords should be a mix of upper- and lowercase, letters , and numbers . The more complex your passwords are, the longer it takes for a password-cracking program to guess a password.
-
Do not use dictionary-based passwords (for example, MyKids). Dictionary-based passwords are the easiest and usually the first passwords determined through password-guessing utilities.
-
Use the New Technology File System (NTFS). In addition to increased reliability, NTFS provides dramatically increased security compared to the other Windows file systems.
-
Set your system BIOS to boot from the hard drive only. Even if you use NTFS, a hacker can access all your protected files by booting from removable media.
EAN: 2147483647
Pages: 89