6.3 Defining Net Service Names in an LDAP Directory Oracle's documentation on the use of the Oracle Internet Directory/LDAP with Net8 is, to be polite, a bit vague. We're sure it will improve with subsequent releases, but it took quite a bit of experimenting before we figured out just how to configure an LDAP directory to support Net8 name resolution. This section talks about what we learned, and walks you through the process of configuring the OID to resolve the net service names nick and luke shown earlier in Figure 6.2. 6.3.1 Prerequisites and Process As a prerequisite to using LDAP for net service name resolution, you need to have the Oracle Internet Directory (or some other LDAP directory server) installed. You also need to have the LDAP schema for Net8 in place. This schema comprises the LDAP object classes on which the entries defining net service names are based. The LDAP schema for Net8 is installed by default when you install OID. With the prerequisites in place, the process for using OID for name resolution is as follows : -
Create an administrative context, which includes an OracleContext entry. -
Create an LDAP user for use with Net8 Assistant. -
Configure your client to use LDAP. -
Create a net service name using the Net8 Assistant. -
Verify connectivity from the client. Steps 1 and 2 can be performed using the Oracle Directory Manager (ODM). ODM is a GUI utility, similar to the Net8 Assistant, that allows you to create and manage entries in an LDAP directory. Step 3 is performed by editing your sqlnet.ora and ldap.ora files. (You learned how to do that earlier in this chapter in Section 6.2. Step 4 can be done most easily using the Net8 Assistant. Step 5 can be performed using the Net8 Assistant, SQL*Plus, or any other program that allows you to connect to a database. 6.3.2 Creating an Administrative Context All the examples in this chapter use an administrative context based on DNS. The domain used is gennick.org , which requires the following LDAP entry: (dn: dc=gennick, dc=org) Underneath that entry, Net8 expects to find the cn=OracleContext entry. 6.3.2.1 Creating the gennick.org domain Two entries are required to represent the gennick.org domain in an LDAP directoryone for org and another for gennick . Both are domain components , so both must be created using the super class named dc. That will make more sense in a moment. For now, look at Figure 6.5, which shows the screen that you see after you invoke ODM and log on as a directory administrator. Figure 6.5. Oracle Directory Manager's opening screen 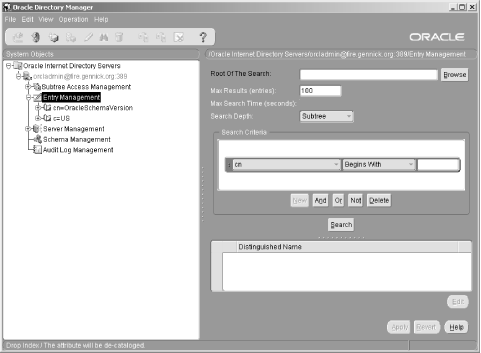 Directory entries that you create all fall under the Entry Management folder. To create a new entry, highlight Entry Management and click the new entry toolbar icon. The new entry icon is the green box with a star in the left corner. You then see the Super Class Selector window shown in Figure 6.6. Figure 6.6. Oracle Directory Manager's Super Class Selector window 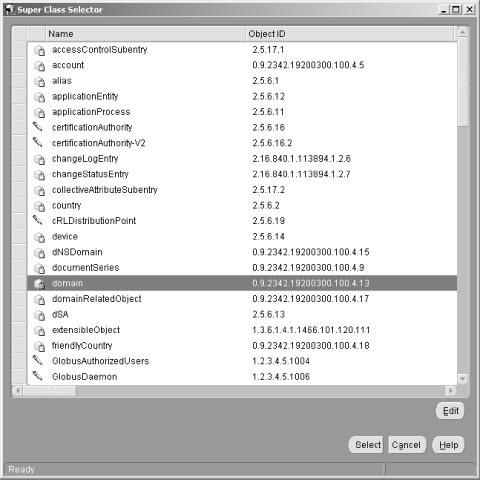 Whenever you create an entry in an LDAP directory, you need to associate it with a class. If you are dealing with a domain component, such as org or gennick, you need to choose the class named domain, which is highlighted in the figure. After highlighting domain and clicking the Select button, you are presented with the New Entry window shown in Figure 6.7. Figure 6.7. Oracle Directory Manager's New Entry window 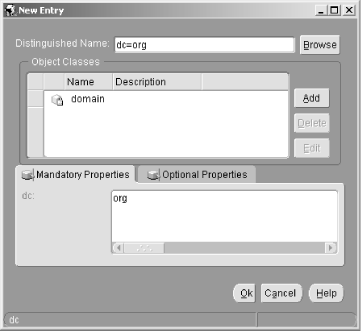 Domain components have a mandatory property named dc. In Figure 6.7 you see that it's been set to org. When creating the second-level domain used in this chapter, you would set dc = gennick. The dc attributes for domain entries are used as part of each entry's distinguished name. One final taskbefore you click Ok to save this new entryis to add Top to the list of object classes. To do that, start by clicking the Add button. That will take you once more to the Super Class Selector window, where you can scroll down and select Top. After adding Top to the list of object classes, click the Ok button to save the new entry. The process for creating the gennick entry is very similar to that of creating the org entry. The major difference is that gennick must fall underneath org in the directory tree. To make that happen, highlight the entry for org, and then click the Create Like toolbar button. The Create Like button is next to the New Entry button and consists of two boxes with an arrow going from one to the other. When the New Entry window opens, modify the distinguished name to read dc=gennick,dc=org, as shown in Figure 6.8. Figure 6.8. Creating the secondary domain named gennick 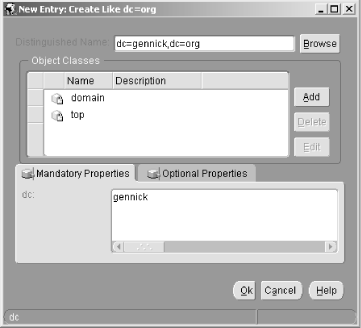 Notice in Figure 6.8 that the dc attribute is simply gennick even though the distinguished name is dc=gennick,dc=org. The gennick domain falls under org by virtue of its location in the tree. That location is determined by the distinguished name, but is not reflected in the dc attribute setting for the entry. As you get deeper and deeper into a hierarchy, the distinguished names get longer and longer. 6.3.2.2 Creating the OracleContext entry After creating the LDAP entries for the domain gennick.org , the final step is to create an OracleContext entry that falls underneath dc=gennick,dc=org. The name OracleContext has a special meaning to Net8 because all net service names fall underneath it. The purpose is to keep the Oracle-related entries under a domain separate from entries that aren't related to Oracle. You create OracleContext like any other entry, but you need to base it on the class named orclContext, as shown in Figure 6.9. Unlike the domain components, which have dc as a mandatory attribute, entries of the orclContext class use cn. The abbreviation cn stands for Common Name. Figure 6.9. Creating the OracleContext directory entry 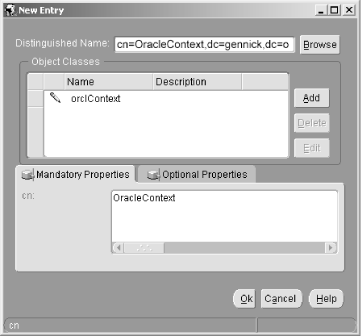 Notice that the distinguished name for the entry shown in Figure 6.9 includes not only cn=OracleContext, but dc=gennick,dc=org as well. That's because the OracleContext entry must fall underneath the entries that correspond to your default administrative context. Figure 6.10 shows the final results of all this effort. In the left pane, you can see the hierarchical structure of the three entries that we created. In the right pane, you can see the complete definition of OracleContextthe final entry under which you can now create net service names. Figure 6.10. LDAP entries for the dc=gennick,dc=org administrative context 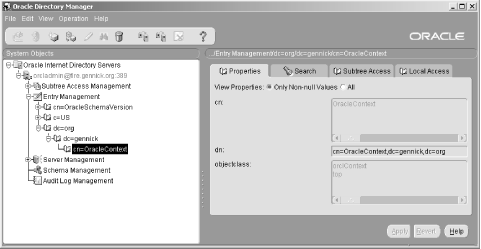 It isn't necessary for you to use an LDAP directory structure that maps to domain components such as those used for the examples in this chapter. You can also use an X.500-style directory structure that corresponds to country (c), organization (o), and organizational units (ou). However, the concepts for either approach are the same. You define a directory hierarchy under which you wish to hang net service name definitions. The distinguished name of the lowest entry in that hierarchy becomes the DEFAULT_ADMIN_CONTEXT setting in your ldap.ora file. Then, underneath that entry, you create another entry for OracleContext. 6.3.3 Creating an LDAP User to ManageNet Service Names Once the proper hierarchy is in place, you can begin to create net service names. While you can create those using the Oracle Directory Manager, we don't recommend doing so. Creating the LDAP representation of a net service name is a much more complex task than adding a few lines to a tnsnames.ora file. It's not a task you'll want to perform manually. Instead, we recommend using the Net8 Assistant. If you're going to use the Net8 Assistant to create net service names in an LDAP directory, you will need to create a directory user that the Net8 Assistant can use when connecting to the LDAP directory. Creating such a user is a two-step process. First you must create the user itself. Then you must grant that user permission to add and edit entries in the part of the LDAP directory tree that you use for net service names. 6.3.3.1 Creating an LDAP user If you have only one admin context, you can create the directory user underneath that context. You may want to create an additional entry named OracleNetAdmins, and collect all the Net8 directory users underneath that. A user is simply another entry in an LDAP directory, but it is based in part on the object class named person. Figure 6.11 shows the definition for a user with a distinguished name of: dn: cn=Jonathan,cn=OracleNetAdmins,cn=OracleContext,dc=gennick,dc=org Figure 6.11. The definition for a directory user 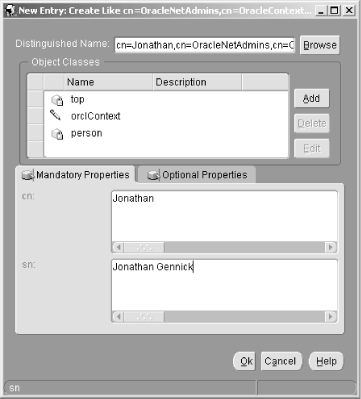 The user shown in this figure was created using the ODM's "Create Like" functionality. The object classes top and orclContext were inherited from the higher-level entry. The person class was added to the list because this entry represented a user, or person. The person object class comes with two mandatory attributes, cn and sn, that you should fill in with the user's login name and full name, respectively. The password attribute is not mandatory and is consequently found under the Optional Properties tab. Because of its placement, it's easy to overlook the password. When creating a user, be sure that you go to the Optional Properties tab and specify a password. 6.3.3.2 Granting access to an LDAP user After creating a directory user, you must give that user some access rights. If you want the user to be able to manage net service names that fall under dc=gennick, dc=org, then you must grant the user access to that part of the LDAP directory tree. To do that, highlight the entry for dc=gennick in the ODM's left pane, and click the tab in the right pane titled Subtree Access. You can then grant a user access to that entry, and on all those entries that fall beneath it. Figure 6.12 shows how you identify the user to whom you are granting access. Figure 6.12. A user being granted access to part of the LDAP directory tree 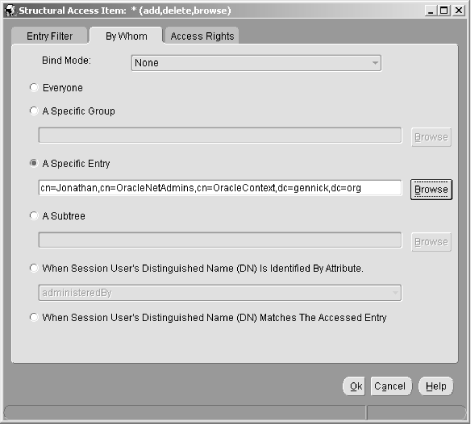 After identifying the user, you need to specify the rights that you are granting to that user. You do that from the Access Rights tab. Figure 6.13 shows a user being granted browse, add, and delete rights. Figure 6.13. Specifying the rights to grant a user 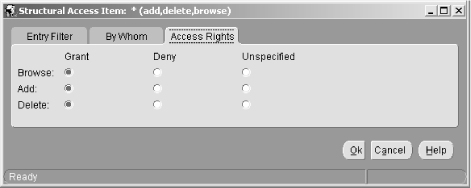 After creating a user and granting access rights, you can use the Net8 Assistant to log in to the LDAP directory and create net service name definitions. 6.3.4 Creating a Net Service Name Probably the easiest way to define net service names in an LDAP directory is to use the Net8 Assistant. Figure 6.14 shows the Net8 Assistant with a service name already defined. Figure 6.14. Net8 Assistant showing a net service name defined in an LDAP directory 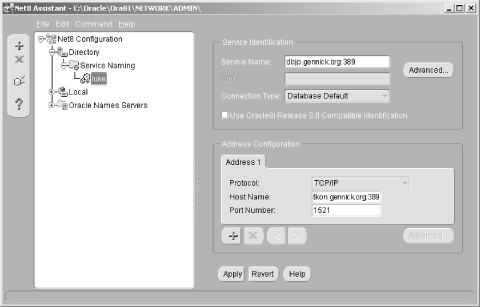 Here, you see the definition for the entry name luke , and you can see that it falls under Directory  Service Naming. This indicates that it's defined in an LDAP directory. Figure 6.15 shows the corresponding LDAP directory entries for luke , as you would see them from the Oracle Directory Manager. Service Naming. This indicates that it's defined in an LDAP directory. Figure 6.15 shows the corresponding LDAP directory entries for luke , as you would see them from the Oracle Directory Manager. Figure 6.15. LDAP directory entries for the net service name luke 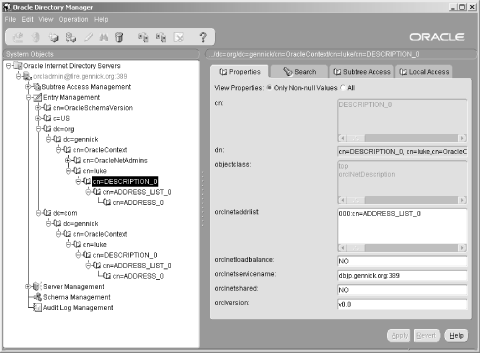 When you create a net service name in an LDAP directory using the Net8 Assistant, the only thing even mildly out of the ordinary is the manner in which you log in to the directory server. Otherwise, the process is the same as if you were creating a net service name in your tnsnames.ora file. When you first open the Directory  Service Names folder from Net8 Assistant, you are prompted to specify a directory service. Then you're prompted for a username and password to use in logging in to that service. Specifying a directory service is easy. Net8 Assistant reads your ldap.ora file and presents you with a drop-down list based on the DIRECTORY_SERVERS entry. Oracle DBAs will find the process of specifying a username a bit unusual, however, because you must specify the username using the LDAP distinguished name. For the user created in the previous section, you must type in the following: Service Names folder from Net8 Assistant, you are prompted to specify a directory service. Then you're prompted for a username and password to use in logging in to that service. Specifying a directory service is easy. Net8 Assistant reads your ldap.ora file and presents you with a drop-down list based on the DIRECTORY_SERVERS entry. Oracle DBAs will find the process of specifying a username a bit unusual, however, because you must specify the username using the LDAP distinguished name. For the user created in the previous section, you must type in the following: cn=Jonathan,cn=OracleNetAdmins,cn=OracleContext,dc=gennick,dc=org Figure 6.16 shows the directory login prompt with this username already entered. Figure 6.16. You must specify a user's distinguished name when logging in to an LDAP directory 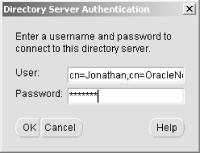 For DBAs used to relatively short usernames, having to type in a long distinguished name will represent quite an adjustment. It takes some getting used to, and at first we couldn't even believe that it was a requirement. But it is, at least in the current implementation, and there seems to be no getting around it. 6.3.5 Testing a Net Service Name The process for testing net service names created in an LDAP directory is no different from that of any other net service name you create. One easy way to test a name definition is to use it with SQL*Plus. For example: sqlplus system/manager@luke In addition, the Net8 Assistant will offer you the opportunity to test any new net service names that you create. When testing a new name, the Net8 Assistant first attempts a connection using the default username and password combination of scott/tiger. If that attempt fails (and it should because you shouldn't allow such default names to remain in use), Net8 Assistant will allow you to enter a different username and password. If you can't connect using the name that you've just created, be sure to double check the protocol address and connect data that you've specified. You should also check the DEFAULT_ADMIN_CONTEXT setting in your ldap.ora file. Remember, the default administrative context is used by Net8 to build up a complete distinguished name with which to query the LDAP directory. |