A Brief Overview of Virtualization in IT
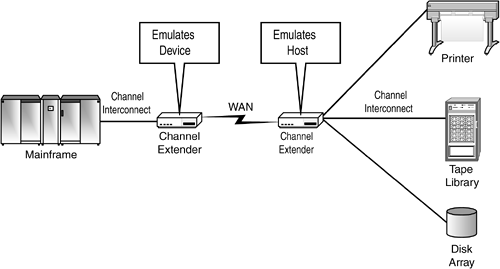
| Virtualization has long been a part of IT infrastructure. In the mainframe world, host systems could be segregated into logical partitions or LPARs, each capable of running its own operating system and applications. Each LPAR was a virtual machine, behaving like an independent entity for all intents and purposes, despite the fact that it shared the same physical platform as every other LPAR. In the early days of PCs, users could augment their slow-performing floppy disk drives by purchasing memory and constructing a virtual disk to which data could be written and read, albeit at much higher speeds than physical targets. "Vdisks" were fairly common in the late 1980s, with chip manufacturers garnering substantial income from memory cards that competed in terms of price with the expensive, pre-standard, hard disk drives of the day. Even in the realm of networks, virtualization found a role. To extend storage devices and other peripherals further away from their host back-plane connection points than manufacturers deemed possible, channel extension vendors devised a number of virtualization-based techniques. One approach involved "spoofing" through the installation of intelligent controllers at the local and remote sites (see Figure 7-1). These controllers, called channel extenders, emulated the communications of the peripheral devices locally, provided wide area network communications access for the I/O traffic, and emulated the host at the remote side so that overall system performance was insulated from the distance-imposed latency of the far-flung configuration. Figure 7-1. Channel/device emulation in a wide area channel extension configuration. From this brief survey, it is obvious that the use of virtual abstractions has served purposes ranging from performance improvement (virtual disk) and fault tolerance enhancement (RAID), to improved topological flexibility (channel extension), to improved resource allocation (LPARs). In these roles, virtualization enables architectural design goals to be achieved using a fixed complement of hardware. Without it, we would need to replicate configurations, or in some cases build specialized devices, for almost every application we field or process we invent or support. Virtual abstractions may also be used to conceal complexity by making many elements appear to be a single element. A file, for example, is a simplified reference to a set of physical blocks containing data used by an application. File systems are a kind of virtualization. Virtualization may also be used, as in the case of LPARs and certain tape virtualization techniques, to "multiply" fixed resource by making a single element appear as a separate and unique resource from the perspective of multiple processes or elements. One leading vendor of tape offers a platform today that identifies itself to all servers as whatever brand of tape the servers prefer. When it receives input streams from each server, it captures the data, schedules and prioritizes it, and formats it for storage on whatever type of library that is physically connected to its back end: In effect, it multiplies the number of tape devices available to servers. |
EAN: 2147483647
Pages: 96