Understanding VPN-1FireWall-1 SVN Components
Understanding VPN-1/FireWall-1 SVN Components
Now that you have seen the major components of the NG AI suite of products, you have likely noticed an underlying theme develop. Everything in the NG AI suite seems to integrate into, requires, or works best in combination with VPN-1/FW1. Although some of the NG AI suite products can operate alone, parts of Meta IP, for example, the product s true power and full feature set is only available when used in conjunction with VPN-1/FW-1. The next few pages look at the individual components of FW-1 itself, and examine how these individual components combine to provide the network security and management tools required to satisfy the SVN specifications.
The GUI, management, and VPN/firewall modules make up the core of VPN-1/FireWall-1. These three modules can reside on a single computer or be built on separate, distributed machines depending on the size and specific needs of your network. The management module provides a centralized point to manage and log data from a single or multiple network security enforcement point. The GUI provides an easy-to-use interface for the management module, simplifying configuration and maintenance. Since the GUI and management modules are what you interact with most when working with VPN-1/FireWall-1, we will explore them before looking at the VPN/Firewall module that does the actual traffic inspection.
VPN-1/FireWall-1 Management Module
At the center of Check Point s three- tier architecture is the management module (SmartCenter server). The management module is most commonly configured using the GUI client and resides on the management server (SmartCenter). The management module not only stores the Security Policy but is also responsible for maintaining the logs, user databases, and the various network objects used in the Security Policy. The management module moves the logging and policy maintenance functions away from the core inspection module. This allows a single SmartCenter to service multiple enforcement points, and allows VPN/firewall modules to perform better by not having to maintain and sort the log files. The management module also checks that the Security Policy is defined correctly and compiled into the format that the inspection module needs. The management module also expands the Security Policy beyond just Check Point VPN-1/FW-1 devices by enabling you to define and push out an access control list (ACL) to any number of supported third-party devices.
Although the management module can be deployed on the same physical machine as the GUI clients and even on the VPN/firewall module, the true benefit of separating the management aspect from the GUI configuration and enforcement point really shows in a larger, distributed environment.
Central Management of VPN-1/FireWall-1 Modules
The management module leverages the Client/Server architecture to enable you to manage an entire enterprise from a single SmartCenter. This configuration provides performance, scalability, and centralized control of your security environment from a single supported platform that could, if needed, be duplicated and made into a highly available service. Figure 1.3 shows a typical distributed configuration of a single management server maintaining multiple FireWall-1 and VPN-1 enforcement points.
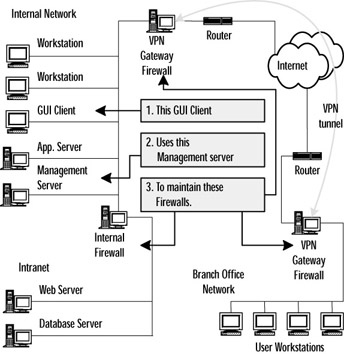
Figure 1.3: Distributed Client/Server Architecture
The key point to notice in the above example is that the management server can be accessed from a workstation that is running the management GUI, and that a single server can manage multiple firewalls. If desired, the management server could be used to manage the ACLs on the routers and other supported network equipment. This enables you, from a GUI client running on your desktop workstation, to securely create and maintain a single Security Policy, stored on a centralized management server and enforced on any number of enforcement points. The enforcement points can be Check Point firewall or VPN modules running on any supported OS or purchased pre-installed onto network appliances, as well as a number of routers, switches, and other network devices from different vendors . This allows a single centrally managed Security Policy to define and enforce the basic security needs of your entire enterprise. Without the management server layer, an administrator would have to connect to each firewall to make a change. This introduces the possibility for policies to become disjointed and security vulnerabilities to be introduced without an administrator realizing it.
| |
Choosing Your OS
VPN-1 and FireWall-1 can be purchased pre-installed on a hardware appliance or as a software application available for a variety of commercial OSs. If you choose to go the software application route, you need to first decide which of the supported OSs to install on. The management GUI is supported on all Microsoft 32-bit OSs (Windows 98SE and later) as well as Sun Solaris SPARC. The management server and firewall enforcement modules can be installed on any of the following:
-
Windows 2000 with Service Pack 1 or greater
-
Windows NT 4.0 with Service Pack 6a or greater
-
Sun Solaris 9 (64-bit only)
-
Sun Solaris 8 (32- and 64-bit)
-
RedHat Linux 7.0, 7.2, and 7.3
-
Check Point SecurePlatform
Choosing the platform that is right for your company has more to do with your ability to support the OS than with actual security. When you choose your OS, you need to consider what your company is best able to maintain and troubleshoot if problems arise. We have all heard that one OS is more secure than another is, but when it comes to the firewall configuration, mistakes can lead to security problems faster than OS vulnerabilities. By working with the OS you are most comfortable with, you reduce the chances of making configuration mistakes, which generally outweigh any perceived benefit from running on a more secure platform. A skilled administrator can make any supported OS just as secure as any other, and after VPN-1/FWl-1 is installed, it will take care of securing the machine via the firewall security policy.
Furthermore, many companies harden the OS before installing the firewall by uninstalling or locking down unneeded services and restricting user and application access to the firewall just to be extra cautious. This type of configuration requires an in-depth knowledge of the OS that is hard to get if the firewall is running on a one of OS in your enterprise.
Optionally, Secured by Check Point Appliances and Check Point s SecurePlatform OS come with web-based interfaces for OS management and configuration. This reduces the need for you to be an expert at securing and navigating the OS and simplifies administration.
| |
SIC
We all know that any time data is in transit over our networks it is vulnerable. Sensitive network data could be recorded in order to reconstruct the session later, or it could even be modified or corrupted while in transit using standard man-in-the-middle (MITM) tactics. For most network data, this is not much of a concern since the risk of loss or corruption is low, or the data is simply not worth the effort involved to secure it (such as users browsing the Internet). However, when working with firewall configuration and logs, the risk is much higher, and trusting the configuration and logs from your firewall is paramount to securing your network. To address this issue, Check Point developed the SIC module.
SIC is used to encrypt the data passed between modules and applications, such as information passed between the GUI client, management server and firewall module for policy downloads and sending log data, as well as for a variety of other communication between devices that work with VPN-1/FW-1. For example, SIC can be used between the firewall module and a Content Vectoring Protocol (CVP) server or a Log Export API (LEA) application, in addition to various other OPSEC products and components.
SIC provides three basic functions that enable you to trust communication between supported devices, most notably between your management server and enforcement points. Along with the encryption that you would expect between devices or modules, SIC also ensures that communication is proceeding only with the host intended by authenticating that host using an internal Public Key Infrastructure (PKI) infrastructure. When running on the server side of the client/server model, SIC checks that the client has been granted access to the function or procedure that it is trying to execute even after the peer has successfully authenticated. By authenticating its peers, applying access control, and encrypting traffic, the SIC module ensures that communication between components is accurate and private. By using SIC s internal PKI solution to authenticate systems to each other and encrypt data over any link, trusted or un-trusted, this enables a much more scalable and manageable infrastructure.
NG SIC is certificate-based and makes use of the management server as a party that all hosts trust. The management server hosts the internal Certificate Authority (CA) that is used to issue new certificates, as well as maintains the certificate revocation list (CRL). The internal CA is also used to service certificate pull requests generally issued by third-party OPSEC applications. This again shows off the central nature of the management server and makes another argument for running the management server on a separate machine, even though it can be hosted with the firewall module, so as to remove this extra functionality and overhead from your Security Policy enforcement point.
SmartUpdate
SmartUpdate is an application, included with the management module, which enables you to maintain and upgrade software and licenses for Check Point, OPSEC applications, and some OSs from a central server. For example, SmartUpdate can be used to install a new feature pack or OS update onto your VPN-1/FW-1 NG AI installation as well as push out updated license information when you need to renew expired licenses or if you license additional features.
SmartUpdate enables you to track OS and application versions from all of your Check Point modules as well as supported OPSEC applications. Figure 1.4 shows a typical SmartUpdate window displaying OS, service pack and IP address information for all the modules currently defined to the management server.
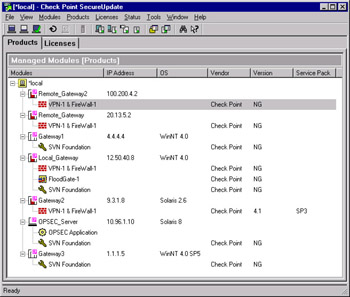
Figure 1.4: SecureUpdate Products Tab
The Licenses tab of SmartUpdate allows you to see the installed license details for all your firewalls and supported OPSEC applications in one convenient location. Aside from showing you the features currently licensed on all your gateways, SmartUpdate can also be used to upgrade those licenses remotely. This feature is extremely useful if you need to change the external IP address and, therefore, to update the license for a remote gateway since, with SmartUpdate, you can change the license properties without the need to reinstall the license, which might otherwise require you to be at the gateway s console. Most commonly, the License tab is used to install new licenses for modules whose existing license is about to expire or when upgrading licensed features, such as adding encryption or adding SecureClient licenses to an existing gateway.
New integration with Check Point s UserCenter has also streamlined the process of downloading new packages and importing them into the SmartUpdate Product Repository. By using this feature, SmartUpdate will go to Check Point s Web site and, after signing in with your UserCenter username and password, download all the new versions of software you require to update your systems.
SmartDefense
In Check Point NG AI, there is a new tab in the SmartDashboard GUI called SmartDefense. SmartDefense brings global security mechanisms that were configured in text files and obscure areas of the GUI (and sometimes not well known, such as Check Point Malicious Activity Detection) into its own tab to provide a single, straightforward interface for configuring these advanced security options. The purpose of SmartDefense is to provide the configuration of active defense against attacks.
SmartDefense provides a unified framework for various security components to identify and prevent attacks. SmartDefense efficiently provides proactive protection, even when not explicitly defined in the Security rule base. In addition to the strict protocol enforcement options provided in SmartDefense, real time attack information and updates can be downloaded directly from Check Point and implemented across the enterprise at the click of a button to protect from new vulnerabilities and attack methods .
SecureXL
SecureXL is a specification used in conjunction with Check Point s hardware partners to help develop the most fully featured, high-performance firewall devices at varying price points. In general terms, SecureXL is helping Check Point service partners develop the hardware and software required to embed VPN-1 and FW-1 into devices that meet the requirements of as many applications as possible.
SecureXL aims to provide smaller companies with affordable firewall appliances as well as develop high-end machines with multi-gigabyte throughput for larger networks. To accomplish this, the SecureXL framework is employing the newest technology developments from the microprocessor field as well as Network Processors (NPs), Application-Specific Integrated Circuits (ASICs), and board-level encryption to develop high performance VPN-1 gateways. A direct benefit from the SecureXL work is the ability to use low-cost encrypting network interface cards (NICs), built to SecureXL specification, to boost VPN-1 encryption throughput.
In addition to encrypting NIC cards, the SecureXL standard allows vendors to increase device performance by moving firewall functions, such as NAT and anti-spoofing , to specialized hardware for processing. Even core firewall processes like access control and the connection tables can be replicated or moved to dedicated devices for improved performance and scalability. For more information, see the Check Point VPN-1/FW-1 performance brief at www.checkpoint.com/products/security/vpn-1_firewall-1_perfdetails.html
The ultimate goal of SecureXL is to develop the security products that enterprise network managers are looking for, at a variety of price points, by using the newest hardware and software technology and customizing the features included. This creates a variety of firewall and VPN solutions that enable you to not only pick the feature set, but in some cases also pick from multiple vendors to ensure that you get the products you need to secure your network, at a price that will fit your budget.
GUI
The GUI is the component of the management module that you will interact with the most. The GUI is made up of several tools and modules, designed to help you create and enforce a Security Policy and monitor the current and historical state of your security infrastructure. As a FW-1 security manager, you will spend most of your time in the two main GUI tools: the SmartDashboard and SmartView Tracker (Log Viewer). These two tools enable you to create the rules that make up your Security Policy and to check the effectiveness of those rules in action. The SmartDashboard contains the Policy Editor that will help you to build your Security Policy from objects that you define, as well as to build in definitions. SmartView Tracker enables you to sort and process data generated by your Security Policy in action on your network, and is explored in detail in Chapter 3.
The SmartDashboard GUI is designed to help you create the most accurate policy possible. Many companies expose themselves to risk, not from a lack of security understanding, but from poorly written firewall rules or policy. The graphical rule base of the Policy Editor, combined with the optional components such as the SmartMap, aim to help you quickly visualize and better understand your network topology and firewall rule base, enabling you to write an effective, enforceable Security Policy.
SmartDashboard
The combination of the Policy Editor, Object Tree, Object List, and Visual Policy Editor make up the majority of what Check Point calls the SmartDashboard. The Smart Dashboard provides you with the tools you need to analyze and manage your company s network security through the creation and maintenance of a Security Policy. The main advantage of the macro-level view provided by the SmartDashboard, is the elimination of having to hunt through menus and other dialogs to find the objects and resources required to efficiently build your Security Policy rules.
The Policy Editor has been designed to help show the relationships between objects better with the use of the SmartMap, as well as generally making the job of building security policies easier by enabling you to drag and drop objects from the Objects Tree, and making detailed object information readily available from the Objects List. Figure 1.5 shows the integration of all these components to create the SmartDashboard.
Policy Editor
The easiest and quickest way to manage your Security Policy is to use the Policy Editor, although a command-line interface is available. The Policy Editor has seen major improvements from previous versions to provide a user-friendly, GUI-based approach to security rule base creation and management. The Policy Editor has been designed to give a more detailed, visual representation of your Security Policy providing fast, easy, and more accurate rule creation.
Depending on the products licensed, all six VPN-1/FW-1 policies are available from the main Policy Editor window. Along with the standard Security and NAT policy tabs, the QoS, SmartDefense, UA WebAccess, and Desktop Security policies are also available. This all-in-one approach to maintaining all the major policies from a single GUI is a direct result of Check Point s SVN architecture that attempts to treat network security as an easy-to-manage, end-to-end solution rather than separate, isolated components. The added advantage of managing all four policies together is the reduction in duplicating objects into multiple applications, since the same set of network and user definitions are used in all four policies. The SVN-inspired SmartDashboard enables you to maintain the entire network, from the Internet-based, VPN-connected user desktop through NAT and QoS rules, right up to your Internet gateway Security Policy using a single, easy-to-use tool.
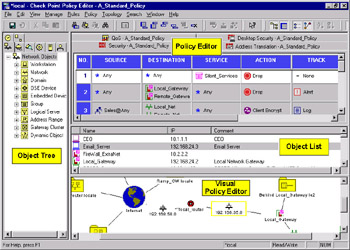
Figure 1.5: SmartDashboard
Expanding on the distributed nature of FireWall-1, Check Point has developed the SmartDashboard to work as a separate product that can be installed on the average workstation as part of the normal GUI tools. This enables you to use the SmartDashboard to work with the Security Policy stored on the management station from another computer known as a GUI client. Using this distributed design enables you to manage your firewall security rules, whether you are sitting at the console of the management server or working from a GUI client on the other side of the country.
Object Tree
The Object Tree provides the security administrator with quick access to all the objects that make up the Security Policy. Normally found running down the left side of the Policy Editor window, the Object Tree displays and sorts all the objects defined for use in the Security Policy. To make what you need easier to find, the Object Tree groups available objects into eight tabs: Network Objects, Services, Resources, OPSEC Applications, Servers, Users, Time Objects, and Virtual Links. For more information on how to use each of these objects, see Chapter 3.
Besides categorizing the policy objects to make it easier to find what you are looking for, the Object Tree also speeds up policy building by enabling you to drag and drop objects directly into policy rules, rather than requiring an administrator to open dialog boxes from the Manage menu.
Object List
The Object List is normally used simultaneously with the Object Tree to show the details of all objects available under the currently selected heading on the Object Tree. The main advantage of the Object List is the ability to see all the objects important properties in a convenient table format rather than having to open each object s properties panel. Using the Object List enables you to quickly ensure that you are working with the object you intend (for example, when selecting workstation objects, you will be able to compare IP addresses and comments for each object, rather than just relying on the object names ). This is especially handy when your object-naming convention is not completely clear, in that you can quickly verify that you are using the proper objects to build a new rule.
Another efficiency the Objects List provides is the ability to sort on any of the columns shown. This allows an administrator to show all network objects in the Objects List, but sort them by IP address, comment, version, or net mask. The same functionality for services allows one to sort by port. As with the Object Tree, you can drag and drop objects from the list directly into new or existing rules.
SmartMap
Check Point designed the SmartMap to help security managers better visualize the network topology contained within the Security Policy. Prior to FW-1 NG (and the VPE beta for FW-1 4.x), I often found myself used a white board or scrap of paper to draw network device connections and services to help build and verify the rule base. With the SmartMap, the whiteboard network diagram is automatically created and updated in SmartMap, providing not only a visual display of the network built from defined objects, but also allowing you to define new groups and other objects easily right in the visualization.
Along with making it easier to visualize the security rules, the ability to build and keep the network diagram with the Security Policy solves a couple of administration issues. First off, white board or even printed network diagrams, although often necessary for visualizing the network layout, are very difficult to keep secure. When network diagrams contain sensitive information, such as Intrusion Detection System (IDS) locations or other sensitive security device IP address information, it is important to keep that information secured. Keeping the diagram with the policy ensures only users allowed to view the Security Policy have access to the diagram. Secondly, if you have multiple security managers, using the SmartMap ensures that everyone is working from the same diagram. This can be very important when the primary security manager is unavailable and a secondary operator must finish or troubleshoot a new service installation. As well, this is extremely useful when one or more of your security administrators work offsite or in another office where SmartMap diagrams may be the most convenient way to share network diagrams.
Because of the tight integration with the Policy Editor and the objects, SmartMap automatically updates the diagram as your addressing changes, removing the need to continually update a shared document, which contains the current network topology. The always up-to-date SmartMap can also be exported to an image file (bitmap or JPEG) as well as directly to Microsoft Visio.
One of the most useful features of the Visual Policy Editor s integration with the Policy Editor is the ability to highlight individual rules from the Policy Editor on the network diagram. This feature is perfect for displaying complex rules to ensure that you have actually created what you expected, as shown in Figure 1.6. To make the visualization easy to read, different colors are used for different actions (accept, drop, encrypt, and so forth), which can be customized to suit your needs.
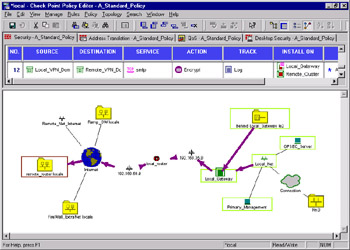
Figure 1.6: Visual Policy Editor Showing Rule
Policy Server
The Policy Server integrates into VPN-1, enabling you to manage the SecureClient software installed on a VPN user s machine from a central location. The Policy Server is responsible for sending SecureClient policy information for the specific desktop security settings to load, pushing down new versions of the client to the desktop, and enforcing SCV to ensure that the SecureClient machine s configuration meets your policy requirements.
In addition to verifying the clients configuration and sending the desktop Security policy, the Policy Server is also responsible for handling logs from the SecureClient machines. As a final step of logging into the Policy Server, the software will package its local alert logs and send them to the Policy Server. The Policy Server then opens these files and sends each alert log entry to the management server to be incorporated into the log database, where it is viewable through the VPN-1/FW-1 Log Viewer. This enables you to view alert data from not only VPN-1/FW-1 and local OPSEC applications, but also from remote VPN desktops with SecureClient installed.
Desktop Security
The Desktop Security policy is created with the Policy Editor on the Desktop Security tab. In addition to the actual policy, which is similar to the main Security Policy, operational settings can be modified from the Desktop Security section of the global policy properties. Once defined, the Desktop Security policy is downloaded to your policy server, making it available to your SecureClient v 4.1 and NG AI users when they next log on.
Desktop Security enables you to control the tiny or personal firewall built into the SecureClient software package. This enables you to extend the security of your network down to encompass the Internet-connected VPN client machines, as specified in the SVN architecture. Part of the Desktop Security policy can also incorporate checking to ensure that a minimum configuration level is maintained on the VPN client machine, by using the SCV module. This enables you to expand the default Desktop Security options to include custom checks that you define, grant, or deny VPN access based on the configuration state of the computer attempting to connect.