LDAP Authentication
LDAP, or the Lightweight Directory Access Protocol, is used for a bevy of purposes. With regards to FW-1, this server object is used for the purposes of user management. A full discussion of the workings of LDAP is beyond the scope of this book, but it is assumed that if you are configuring an LDAP object, then you have access to an existing LDAP server and the necessary information.
LDAP Account Unit
In NG AI, the concept of having multiple LDAP servers with a single shared database is supported more directly and the configuration is streamlined. An LDAP Account Unit can now be defined to include multiple servers that provide access to the LDAP database.
To configure LDAP in FW-1, you need to set up an LDAP account unit. To do so, open the Policy Editor and select Manage Servers and OPSEC Applications New LDAP Account Unit .
Figure 6.18 illustrates the General panel for LDAP configuration.
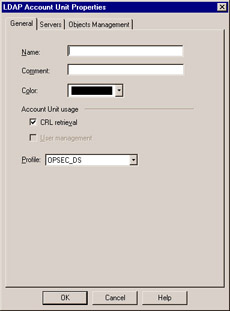
Figure 6.18: LDAP Account Unit Properties
Aside from the common Name , Comment , and Color fields, there some specific options to select. First, define whether this LDAP account unit will perform queries for digital Certificate Revocation Lists ( CRL retrieval ). This is most important when used in conjunction with an external Certificate Authority. Next, define the Profile that the LDAP server will be defined to use. This will take into account any special nuances of Microsoft s Active Directory, Novell s NDS, and Netscape s Directory Server. All other OPSEC-certified LDAP servers should use the OPSEC_DS option.
On the Servers tab, you are presented with a place to list the LDAP servers that will serve the LDAP database defined for this LDAP account unit. Additionally, you can choose one of the servers from the list to be queried by pre-NG AI enforcement modules. The Earlier Versions Compatibility server allows for compatibility with NG FP3 and earlier versions that did not have the capacity to define multiple servers per account unit.
When adding a server to the list, as shown in Figure 6.19, you will be prompted for the Host on which this server will be running, as well as the Port it will be listening on, and the credentials used to connect and query the server. This page is also used to define which permissions are granted (and will be utilized) by the enforcement modules. In the event that the LDAP server is capable of encrypting communications using SSL technology, the Port on the General page will be disabled and the port is defined in the Encryption page of the LDAP Server Properties. Also on the Encryption page is the server s digital certificate fingerprint and the minimum/maximum encryption strength.
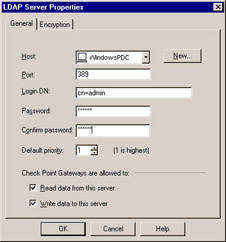
Figure 6.19: LDAP Server Properties
Back in the LDAP Account Unit properties, the Objects Management tab allows an administrator to define which server will be updated (and presumably the update will get synchronized to all other servers in the account unit) in the Manage objects on selection as well as the Branches in use , how many entries to return from a query, and finally whether to automatically log in to the server from the GUI or to Prompt for a password when opening this Account Unit in SmartDashboard. Note: if you do not define the branches in use, you will not be able to manage any users in the account unit.
Account Management Client
The Account Management Client, or AMC, is how FW-1 interacts with an LDAP server. There are several steps to complete before you can make use of the AMC. In the Policy Editor, select Policy Global Properties LDAP Account Management (see Figure 6.20).
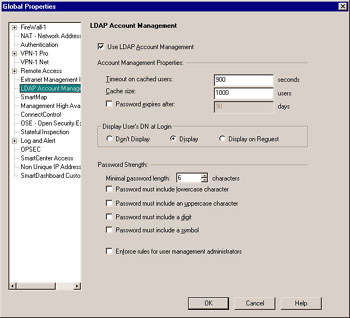
Figure 6.20: LDAP Properties
Here, enable the Use LDAP Account Management field, which indicates that you plan to use the integrated AMC. If required, you can adjust the Timeout and modify the Cache size depending on the number of users you plan to have. If you would like to force users to change their passwords periodically, enable Password expires after , and specify a number of days.
Only normal passwords will expire. Pre-shared secret passwords, such as those used with the IKE encryption scheme, do not expire, no matter what you choose for this setting.
For Display User s DN at Login , choose one of the following:
-
Don t Display If you do not want the distinguished name (DN) to be displayed to users after they log in.
-
Display If you do want the DN to be displayed to users after they log in.
-
Display on Request If you only want the DN to be displayed to users if they request this information.
Displaying a DN at login is important if you would like your users to verify that the account they are attempting to log into actually belongs to them. There may be some cases where, because of duplicate names , users may be confused unless they are permitted to see the full DN.
The Password Strength settings enable you to specify how secure your users passwords must be. It is always a good idea for users to choose hard-to-guess passwords, and these settings force them to do so by using uppercase, numeric, and symbolic characters .
Enabling the Enforce rules for user management administrators option means that all the previous settings also apply to administrators, in addition to normal users. This is a good idea; administrators should not be exempt from proper security practices!
Now that you have configured the general LDAP settings, you need to create an LDAP account unit object, as described in the previous section. You will then be able to use the AMC to manage remote users directly from the Policy Editor.