How to Write a Security Policy
To write an entire Information Security Policy can take months of work with involvement from the Legal and Human Resources departments, as well as various business units. In order to implement Check Point NG AI, you need at a minimum an Executive Security Policy and a Perimeter Network Security Policy. Typically, the Executive Security Policy is a high-level document of about three to five pages that points to relevant standards, procedures, and guidelines. Because the highest levels of management or the board of directors must adopt the Executive Security Policy, it should be written without details about technologies, people, or methods . This will ensure that as technology changes or as people change, the document will not become obsolete. Think of the Executive Policy as a declaration of the importance of security to your organization. However, choose your words carefully because it is a legal document in many respects.
The Executive Security Policy is important because without an executive endorsement of your security policy, enforcement may become difficult. In order to write an effective Executive Security Policy you must identify early on the departments with an interest in maintaining information assets, such as R&D, Finance, and IT. Approach the managers and request their involvement in drafting an executive-level security document. In addition, you will want to include the Legal department and an executive sponsor.
| Note | Executive support and approval is critical to the success of your Information Security Policy. When the CEO has to follow the same rules as everyone else, it makes policy enforcement much simpler. |
The final document should have language such as: Because of the nature of our business, customer non-public information is frequently transmitted or stored on our information systems. As a result, we will employ appropriate controls and safeguards including encryption to ensure that non-public information is adequately protected against unauthorized disclosure while in storage or transit. At this point, that the policy seems rather vague and legal. However, resist the impulse to say, We must use Triple DES encryption on all private data that is stored or transmitted. This is important because technology changes and this document will eventually be presented to management for approval. Management does not want to see you once a month asking for changes to the security policy. As a guiding principle, the Executive Security Policy should address why security is important and delegate the further implementation of appropriate standards, guidelines, and procedures to the appropriate individuals or groups.
| |
Get Trained
Use the Information Security Policy to help you do your job better and to get the things you need. For example, use the policy to ensure that you get security training. Include a statement in the policy that says, To ensure that we are adequately controlling and anticipating current and new threats, the security manager and his or her team must attend security training on a semi-annual basis in the form of conferences, seminars , symposiums, and workshops. As you can see, the Security Policy can be your friend.
| |
Drafting the second part of your overall Information Security Policy, the Perimeter Network Security Policy, is somewhat different. The Perimeter Network Security Policy is a document that includes specific standards, procedures, and guidelines for implementing and maintaining perimeter network security. The first step in drafting a Perimeter Security Policy is to obtain a network map. The network map will help you to better identify resources that need protecting and how to architect your security solution. Depending on the size of your organization, you may elect to do this yourself or to obtain the assistance of individuals with specific knowledge regarding their environment. Although there are a number of software tools to assist you in automatically mapping the network, it will still be necessary to manually validate.
After mapping the network, determine once again the departments or business units with a specific interest in network perimeter security, and assemble the representatives for a meeting. The best approach in this meeting is to identify what is needed and then, by default, disallow everything else. It is at this point that successful security managers recognize the purpose of security to meet business needs. Although it would be great from a security perspective to disconnect the business from the Internet, to stay in business the connection must be maintained . In this meeting, you need to specifically ask the representatives what would need to be changed and configured to allow the business to continue, if you were to put up a firewall today and block everything,. This step is called defining requirements. For example, some of the requirements that might be voiced include the following:
-
We need a Web site that has dynamic content
-
We need to have an e-Commerce storefront
-
We need to be able to get and send e-mail.
-
We need to secure all of our internal information from external attacks.
-
We need to be able to access the Internet securely using HTTP, HTTPS, and FTP from the local area network (LAN).
-
We need to secure our critical information from internal attacks or destruction.
In addition, you will also want to identify any wishes the representatives have. Examples of wishes are as follows :
-
We would like to have Instant Messaging
-
We would like to be able to have sales representatives connect remotely to download order status.
You may find that most needs are simple and can use further refinement. For example, the requirement to send and receive e-mail begs the questions, From where do you need to send e-mail? Do remote users need to send and receive e-mail? Should there be any additional restrictions on e-mail? In addition, you should ask questions about what types of communication to log and how long these logs are kept.
Often you will be faced with end users that ask for more access than they actually need. This is typically rooted in the fact that they do not know, or are not sure, of what access is actually necessary. This can prove to be a trying situation, but it is best to work with these users to investigate what is required and explain why it is important to only allow the minimum access required.
The next stage in the drafting of the Perimeter Security Policy is risk assessment. Every requirement and wish has a risk attached to it. As a security professional, you must be able to identify those risks and communicate them to the involved parties so they can be weighed against the benefits.
| |
Community Involvement
Make sure that everyone who has an interest in the implementation and maintenance of a security policy is involved in its creation. This may involve representatives from Human Resources or even the custodial staff. Involvement from these departments will ease acceptance of the new policy and make the actual implementation much smoother. Sometimes, however, this involvement is legally mandatory if your company falls under HIPAA or other government regulations.
| |
Security Design
After identifying the requirements and risks you are willing to accept, you must design security solutions. Having knowledge of the features and abilities of FW-1 NG AI will help you to determine what you can and cannot do. In addition, be aware of the other types of controls that can be used to maintain perimeter network security. There are three main categories of controls: technical, physical, and administrative. Each category of controls has three functions including preventative, detective, and responsive , as shown in Table 4.1. The firewall is primarily a technical control of a preventative and detective nature. That is to say, the firewall prevents unauthorized access and can be used to detect unauthorized access. However, do not dismiss addressing physical and administrative controls in your Perimeter Network Security Policy.
| Technical | Physical | Administrative | |
|---|---|---|---|
| Preventative | Check Point NG AI VPN-1 | Locked data centers Identification badges | User ID/password policy Change management |
| Detective | Check Point NG AI | CCTV | Log and report review Rule base audits |
| Responsive | Check Point NG AI | High availability | Incident response procedures |
Other policies that FW-1 NG can help enforce are:
-
NAT security
-
Quality of Service (QoS) security
-
Desktop security
-
Monitoring
Firewall Architecture
Before writing the policy, one thing you need to explore is whether you will need to have different policies for different locations or if you will have only one. If you have one security policy, Check Point can enforce the same policy on all firewall modules from a central management station. Otherwise, you will have to maintain a different policy for different locations. Although for business reasons this might be necessary, it can add a level of complexity to your environment that could decrease your overall effective security. If it is necessary, make sure that it is thoroughly documented.
Writing the Policy
Now that you know what is necessary, you can write your Perimeter Network Security Policy. As you can see in Figure 4.1, writing a security policy is a logical progression of steps.
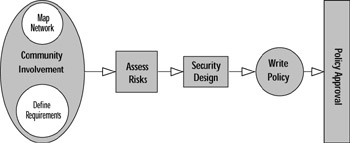
Figure 4.1: Steps to Writing a Security Policy
Briefly, the structure of the policy should include the following:
-
Introduction In this section, state the purpose of this policy. What is the objective of the policy? Why it is important to the organization?
-
Guidelines In this section, detail the guidelines for choosing controls to meet the objectives of the policy. These are the basic requirements. Typically, you will see the word should in these statements.
-
Standards In this section, detail the standards for implementing and deploying the selected controls. For example, state the initial configuration or firewall architecture. This section tends to detail the requirements given in the meeting with the interested departments and business units. This section is written with the words such as, It is the policy that
-
Procedures In this section, detail the procedures for maintaining the security solution, such as how often the logs should be reviewed and who is authorized to make changes.
-
Deployment In this section, assign responsibilities and specific steps for the implementation of the policy. Think of it as a mini project plan. In a Perimeter Network Security Policy, this is the section that translates the standards and guidelines into language that the security administrator can enforce on the firewall.
-
Enforcement Many policies lack this component, however, all policies require a method for enforcement. A popular and effective method for enforcement is auditing. In this section you can state that the firewall rule base would be subject to an external audit yearly. In addition, this section should detail the enforcement and consequences if someone were to circumvent the firewall or its rules.
-
Modification or Exceptions No policy is perfect, and may require modifications or exceptions. In this section, detail the methods for obtaining modifications to the policy or exceptions.
Following is a sample Perimeter Network Security Policy:
Introduction
Due to Company X s required connection and access to the public Internet, it is essential that a strong perimeter firewall exist that sufficiently separates the internal private LAN of Company X and the public Internet. The firewall should provide preventative and detective technical controls for access between the two networks.
Guidelines
The implementation of any firewall technology should follow these basic rules:
-
The firewall should allow for filtering of communication protocols based on complex rule sets.
-
The firewall should provide extensive logging of traffic passed and blocked.
-
The firewall should be the only entry and exit point to the public Internet from the Company X LAN.
-
The firewall OS should be sufficiently hardened to resist both internal and external attacks.
-
The firewall should fail closed.
-
The firewall should not disclose the internal nature, names , or addressing of the Company X LAN.
-
The firewall should only provide firewall services. No other service or application should be running on the firewall.
-
The firewall should provide read-only access for auditors .
Standards
The implementation of any firewall must follow these basic rules:
-
Only the identified firewall administrator is allowed to make changes to the configuration of the firewall.
-
All firewalls must follow the default rule: That which is not expressly permitted is denied .
In addition, the following standards for perimeter networks are as follows:
-
The deployment of public services and resources shall be positioned behind the firewall in a protected service net.
-
The firewall shall be configured to disallow traffic that originates in the service net to the general LAN.
-
Any application or network resource residing outside of the firewall and accessible by unauthorized users requires a banner similar to the following:
A T T E N T I O N! PLEASE READ CAREFULLY.
This system is the property of Company X. It is for authorized use only. Users (authorized or unauthorized) have no explicit or implicit expectation of privacy. Any or all uses of this system and all files on this system will be intercepted, monitored , recorded, copied , audited , inspected, and disclosed to Company X management and law enforcement personnel, as well as authorized officials of other agencies, both domestic and foreign. By using this system, the user consents to such interception, monitoring, recording, copying, auditing, inspection, and disclosure at the discretion of Company X. Unauthorized or improper use of this system may result in administrative disciplinary action and civil and criminal penalties. By continuing to use this system, you indicate your awareness of and consent to these terms and conditions of use. LOG OFF IMMEDIATELY if you do not agree to the conditions stated in this warning.
Procedures
The firewall will be configured to allow traffic as defined below.
-
Transmission Control Protocol (TCP)/IP suite of protocols allowed through the firewall from the inside LAN to the public Internet is as follows:
-
HTTP to anywhere
-
HTTPS to anywhere
-
-
TCP/IP suite of protocols allowed through the firewall from the inside LAN to the service net is as follows:
-
HTTP to Web server
-
Simple Mail Transfer Protocol (SMTP) to mail server
-
Post Office Protocol 3 (POP3) to Mail server
-
Domain Name System (DNS) to DNS server
-
-
TCP/IP suite of protocols allowed through the firewall from the service net to the public Internet is as follows:
-
DNS from DNS server to anywhere
-
-
TCP/IP suite of protocols allowed through the firewall from the public Internet to the LAN is as follows:
-
None
-
-
TCP/IP suite of protocols allowed through the firewall from the public Internet with specific source, destination, and protocols is as follows:
-
SMTP to mail server
-
HTTP to Web server
-
FTP to FTP server
-
Deployment
The security administrator will define the rule base and configure the firewall as defined above, in addition to other industry standard properties (as appropriate).
Enforcement
Traffic patterns will be enforced by the firewall s technical controls as defined by the firewall administrator. Periodically, an external vulnerability assessment will be performed to assure the proper configuration of the firewall. Additionally, an independent third party will annually audit the configured firewall.
Modifications or Exceptions
Requests for modification to the firewall configuration must be submitted via e-mail to the security manager and firewall administrator, accompanied by justification and the duration of the requested change. The security administrator is allowed to make modifications outside the company s change control process in cases where they deem it necessary to prevent or contain disastrous events.
- Article 230 Services
- Article 314 Outlet, Device, Pull, and Junction Boxes; Conduit Bodies; Fittings; and Handhole Enclosures
- Article 356 Liquidtight Flexible Nonmetallic Conduit Type LFNC
- Article 386 Surface Metal Raceways
- Example No. D5(b) Optional Calculation for Multifamily Dwelling Served at 208Y/120 Volts, Three Phase