Understanding Network Security
The Network Security section of SmartDefense provides protection against many of the standard network-based attacks that can affect systems on your network. In contrast to the Application Intelligence section, which is geared toward protection that involves inspection of application content, these defense mechanisms rely on the detection of properties of IP packets and traffic flows.
Denial of Service
SmartDefense offers protection against three types of DoS attack. The motive of any DoS attack is to take advantage of a vulnerability in an application or operating system to cause a system to become unresponsive to legitimate users. By detecting activity that could be indicative of such an attack, you have the ability to deny access to the offending user , leaving the system available for general use.
The three types of DoS attack that can be detected are:
-
TearDrop Detects overlapping IP fragments .
-
Ping of Death Detects fragmented , oversized ICMP requests .
-
LAND Detects packets that are modified to match unusual specifications.
The only option available for each of these attacks is to adjust the action that VPN-1/FireWall-1 will take when a matching attack is detected. Note that even if you choose not to log these attacks, VPN-1/FireWall-1 will still block traffic that is suspected to be a DoS attack.
IP and ICMP
The IP and ICMP section allows you to protect your network from various common Layer 3 and 4 vulnerabilities. A mandatory check is the Packet Sanity verification, which performs a number of routine checks on each packet to ensure that nothing unusual is present in the packet header, size, and flags. The Max Ping Size option allows you to specify the maximum size , in bytes, of ICMP packets, alleviating the risk of having your network congested by oversized and excessive ping floods.
Next , choose the IP Fragments option, as shown in Figure 13.4.
Enabling Allow IP Fragments is a good idea because legitimate packets may need to be fragmented if they exceed the maximum transmission size. The risk is that malicious users may try to hide what they are doing by fragmenting their packets so that SmartDefense does not recognize their attack. A good compromise is to set a limit on the maximum number of incomplete packets and to set SmartDefense to disregard incomplete packets after a certain amount of time (one second is a good default).
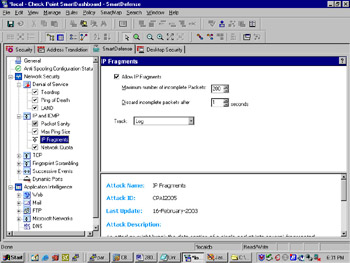
Figure 13.4: IP Fragments
The Network Quota section, shown in Figure 13.5, allows you to protect your network from DoS attacks that are based on sending an excessive amount of traffic through your firewall.
This feature will either drop or track any connections from the same host that exceed the specified number of connections per second. The default is 100, a good starting point; most legitimate network use will not result in more concurrent connections than that.
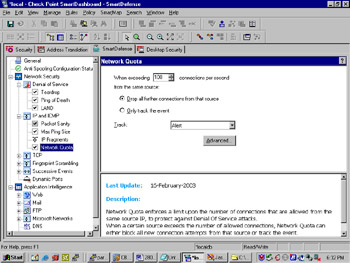
Figure 13.5: Network Quota
TCP
TCP, one of the main Layer 4 protocols that is part of the IP protocol suite, has several inherent vulnerabilities for which you will want to use SmartDefense to protect your network. The first is the SYN attack configuration screen, shown in Figure 13.6.
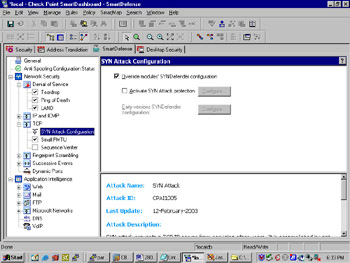
Figure 13.6: SYN Attack Configuration
| |
Unusual Applications
The concurrent connection setting in SmartDefense is one example of a setting that needs to be tuned according to the applications running on your network. You may have an unusual application that legitimately opens a high number of concurrent connections, which would be blocked by SmartDefense s default setting. This is why SmartDefense cannot be expected to work out of the box ”you need to spend the time tuning its settings to your specific network requirements.
| |
By selecting Override modules SYNdefender Configuration , you ensure that the policy you set on the management console will be pushed and enforced by all the enforcement modules. Select Activate SYN Attack Protection , and choose Configure , as shown in Figure 13.7.
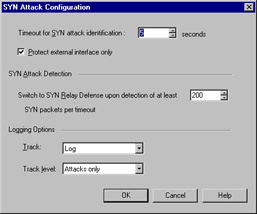
Figure 13.7: SYN Attack Configuration
The Timeout for SYN attack identification is how long SmartDefense will wait before it considers a packet that has not received an acknowledgment to be part of an attack. The Switch to SYN Relay Defense upon detection of at least option specifies how many SYN packets per timeout should be received before switching to SYN relay defense mode. This mode puts the firewall between the external host and the inside host so that unacknowledged packets do not reach the server; the firewall performs the handshake on behalf of the server, thereby shielding it from this type of attack. The default of 200 packets per timeout is a good starting point.
The next option (shown in Figure 3.6 underneath the SYN Attack Configuration option), is to protect against small PMTU attacks. This attack involves the offending host sending a large number of very small packets. The targeted host s resources are tied up in responding to all these packets, so it can no longer serve legitimate requests. To prevent this type of attack, set a minimum packet transmission size (MTU). At least 350 bytes, which is the default, is recommended.
Finally, the sequence verifier (also shown in Figure 13.6), when enabled, allows SmartDefense to keep track of the sequence numbers of packets to ensure each packet s validity. This ensures that packets that are out of sequence, but not meant for legitimate reassembly in the case of packet fragmentation, are not able to enter your network.
Fingerprint Scrambling
A remote host may attempt to collect information about hosts within your network based on how they reply to various types of traffic. This process is known as fingerprinting . The SmartDefense fingerprint-scrambling options aim to eliminate the threat of fingerprinting by rendering unidentifiable the information that hosts send in reply.
Three types of fingerprint-scrambling are available: ISN spoofing, TTL, and IP ID. ISN spoofing involves modifying sequence numbers of the three-way handshake to make operating system detection impossible . TTL, or time to live , removes an external user s ability to determine the number of hops between themselves and an internal host. IP ID instructs the firewall to assign its own identification number to each IP packet, thereby masking the type of operating system an internal host is running, since an external user may be able to determine the type of operating system by the identification number that is assigned.
Successive Events
The successive events section allows you to track repeated events that could be a sign of malicious activity. These events include:
| |
Keeping OS Information Hidden
It is good practice to keep all information about operating system type and version private. A malicious user with knowledge of what operating system your hosts are running is much further along in terms of developing an attack than one who is yet to determine this information. Attacks are often geared toward a specific operating system type or version, so fingerprint scrambling helps keep this information private, lessening the risk of a successful exploit.
| |
-
Address spoofing Occurs when an external user attempts to represent himself or herself as coming from an IP address with authorized access to your network.
-
Local interface spoofing Occurs when an external user attempts to attack the firewall by representing him or herself as coming from an authorized IP address.
-
Port scanning Occurs when an external user scans through multiple TCP or UDP ports on an internal host.
-
Successive alerts Occurs when VPN-1/FireWall-1 generates a certain number of alerts in a certain amount of time.
-
Successive multiple connections Occurs when a certain number of concurrent connections are opened from one external host to one internal host.
Dynamic Ports
The Dynamic Ports section, shown in Figure 13.8, allows you to specify how the firewall should treat applications that attempt to open ports dynamically. An example of such a service is File Transfer Protocol (FTP), which normally attempts to use ports above 1024 for data transfers.
Figure 13.8: Dynamic Ports
The first option, Block data connection to low ports , should be enabled unless you have a specific reason to do otherwise . Low ports (below 1024) should normally be used only by standard services, and so should not be used dynamically. Next, you have the option to either allow or block connections to defined services. A defined service is one that you have explicitly allowed access to in the Rule Base, so here you can choose whether or not these services dynamic port requests will be permitted or denied . Alternatively, you can choose to block dynamic port requests to a list of specified services.