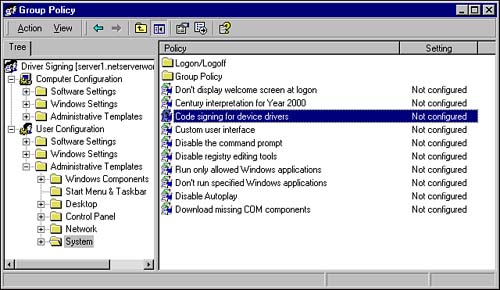
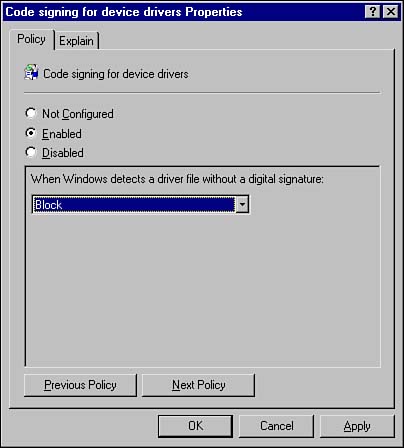
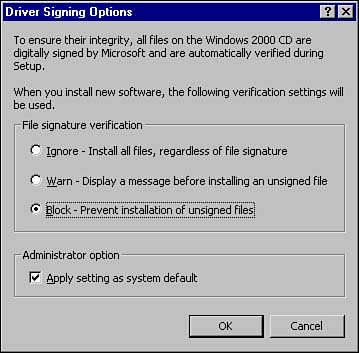
Configuring Driver Signing Options
| Realizing that poorly written drivers were often the cause of kernel stop errors (also known as the Blue Screen of Death) and other system problems, such as lockups and instability, Microsoft introduced digital driver signing in Windows 2000. Digitally signed device drivers are those that have been submitted to the Windows Hardware Quality Lab (WHQL) by vendors and subsequently subjected to compatibility tests administered by the WHQL. Drivers that complete the compatibility testing process successfully are approved by Microsoft and digitally signed. Due to this rigorous compatibility testing, digitally signed drivers can be counted on to be more robust and reliable. Driver files that have been digitally signed can be found on the Windows Update Web site and also on the Windows Hardware Compatibility List. Additionally, only digitally signed drivers are found on the Windows 2000 setup CD-ROM. Driver signing, which is controlled from the System applet for standalone machines and via Group Policy for network machines, is important to ensure that your computers remain fully functional. By enforcing restrictions on the installation of unsigned drivers, you can prevent hardware conflicts and stop errors, both of which are common side effects of poorly written drivers. Poorly written drivers also tend to generate an unusually large number of CPU interrupts, thus interfering with all other operations.
By digitally signing a file, in this case a driver file, one can be relatively certain that the file is trustworthy and authentic . In this way, digitally signing a driver file works in the same fashion as digitally signing your email message that you send to a co-worker. Because any type of computer file can be signed with a digital certificate signature, a means must exist to handle all of the different file formats. This is accomplished via a technique known as catalog file signing , in which digital signing information about files is available without any modification to the files themselves . In catalog file signing, a CAT file is created for each driver or operating system file that is being signed. The CAT file includes a hash of the binary file. A hash is the result of a mathematical operation on some data (in this case, the binary file) that is sensitive to any changes made in the source data. Any change to the binary file can be detected because the hash procedure produces a different value. Other information, such as filename and version number, is also added to the file. A certificate from the publisher, along with a Microsoft digital signature, is included in the catalog file to complete the signing process. The relationship between the catalog file and the driver binary is contained in the information file (.inf) maintained by the system after the driver is installed. The options available for configuring how to handle unsigned drivers include the following:
As previously mentioned, you can configure driver signing from one of two locations depending on the configuration of your network and your preferences. Regardless of the location from which you choose to configure driver signing, you still have the same three choices available. The next section examines the process of configuring driver signing via Group Policy. Configuring Driver Signing via Group PolicyIf you have a Windows 2000 Active Directory domain, you should take advantage of Group Policy as often as possible. Using Group Policy Objects to configure your network and your computers gives you previously unavailable management abilities with very little overhead. Group Policy allows you to have granular control over the who, what, when, where, how, and why of configuring network settings. As an example of dealing with driver signing, assume that you work for a company that has the following departments:
In this example, you are faced with three different types of clients and thus three different driver signing options you can configure via Group Policy for their respective OUs. In this case, you should consider configuring driver signing as follows :
As you can see in the preceding example, you may need to configure different driver signing policies for different groups of users. Group Policy Objects (GPOs) applied to the applicable organizational units makes this an easy task. The process to configure driver signing via Group Policy is fairly simple and is outlined as follows:
The Group Policy settings you configured will take effect as soon as Group Policy has been refreshed the next time users log on to the system. Now all users in the Accounting OU will be prevented from installing any device drivers that are not digitally signed. Applying driver signing options via Group Policy is the quickest and easiest way to have them applied uniformly to a large number of users. However, if you only have a few computers to work with or need a specific computer configured in a certain manner, you can opt to configure driver signing from the Control Panel, which is discussed in the next section.
Configuring Driver Signing Locally via the Control PanelAs an alternative to Group Policybased driver signing, you can configure driver signing from the Control Panel locally on each machine. This is not a good approach for large networks, but it works well in small ones with few machines or peer-to-peer workgroups. The process to configure driver signing is as follows:
In just three easy steps you've now configured driver signing for a specific computer. Although this process is simple, you can see how you would quickly become overwhelmed if you had to perform this configuration on several hundred or even just several dozen computers.
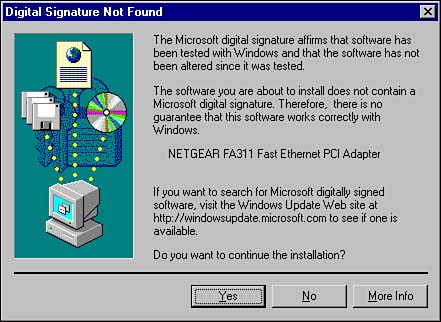
Working with Digitally Signed DriversAfter you've set the driver signing options, you're pretty much done. Try to install an unsigned driver when you are configured for Warn, and you will get a warning dialog box similar to the one shown in Figure 4.4. Figure 4.4. A warning dialog box appears when trying to install an unsigned driver.
This section examined the concept of digital signatures and how you configure driver signing options for the installation of new device drivers on your computers. You've seen how to configure driver signing quickly and easily across an entire OU (domain or site) and also how to configure it on a computer-by-computer basis. The next section explores how you can ensure that your new hardware is ready for use with Windows 2000before you install it. |
EAN: 2147483647
Pages: 155