Developing a Strategy for Delegation
| Delegation is the process of decentralizing network administration by assigning some of the administrative duties to other individuals or groups in the business. Individuals or groups can be assigned specific administrative privileges to certain objects in the Active Directory structure without having control over all the objects. For example, an administrator from one location can be given control over objects within that location and that location only. This is a welcome change from NT 4.0, in which a user who is given privileges to administer user accounts can administer all user accounts in the domain. Creating a strategy for delegation determines at which level in the Active Directory structure administrative permissions should be assigned: site, domain, or OU. The level at which the permissions are applied is determined by the scope of the administrative duties. Keep in mind that it is most common to delegate authority at the OU level because it is much easier to manage. If you start delegating authority on specific objects and object attributes, you'll soon find it difficult to track the permissions that have been assigned (remember, your goal is to make administration easier, not more complex).
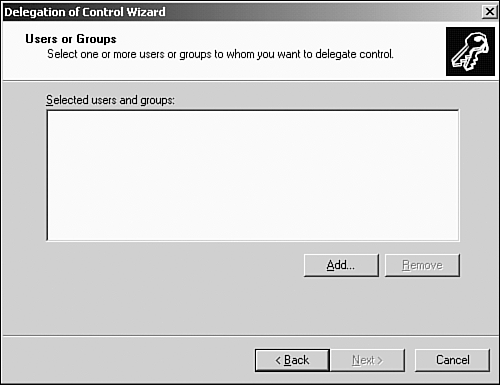
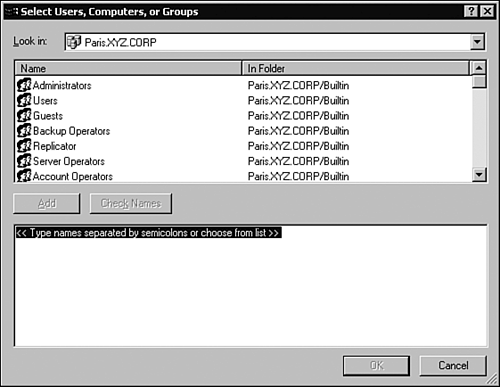
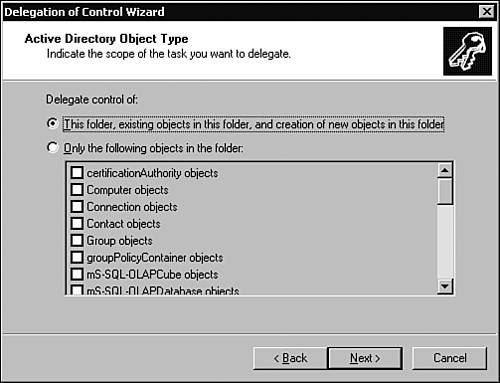
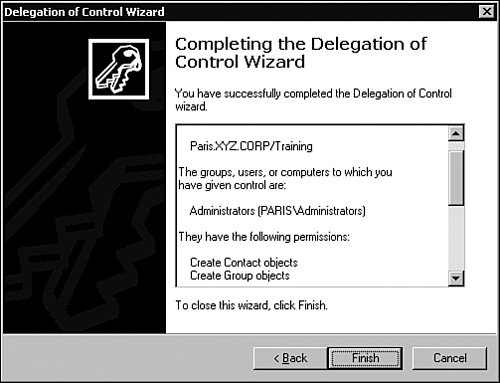
This section of the chapter covers the Delegation of Control Wizard, inheritance and inheritance modifications, designing an OU hierarchy for delegation, and design guidelines. The Delegation of Control WizardAnyone who has worked with Windows should be familiar with wizards and what they are used for. Wizards walk you through the process of completing a task, such as adding a printer or creating a user account. The Delegation of Control Wizard serves the same purpose: It walks you through the process of assigning administrative control over an OU or a container. Within the wizard, you'll assign the user or group specific rights to an OU or other container object. Keep in mind that the rights you assign then apply to all objects in the OU or container. Use the following steps to delegate control using the Delegation of Control Wizard:
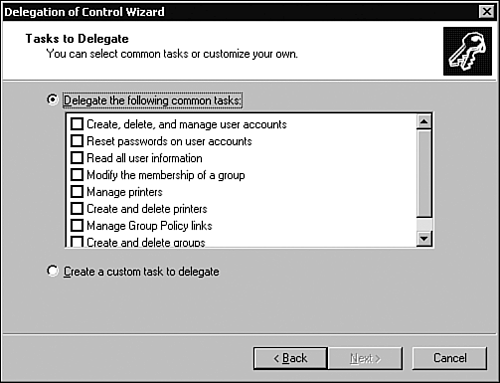
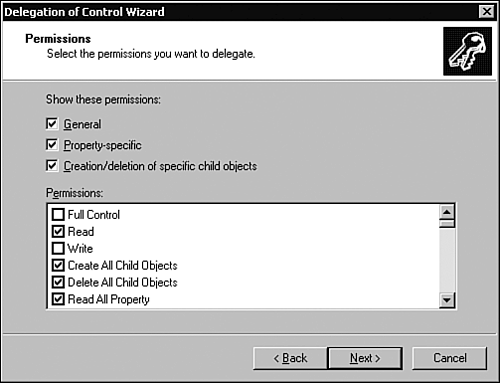
Table 5.3 summarizes the three options presented in the permissions window (shown in Figure 5.13). Table 5.3. Permissions Window Options
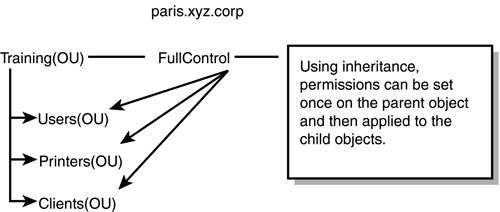
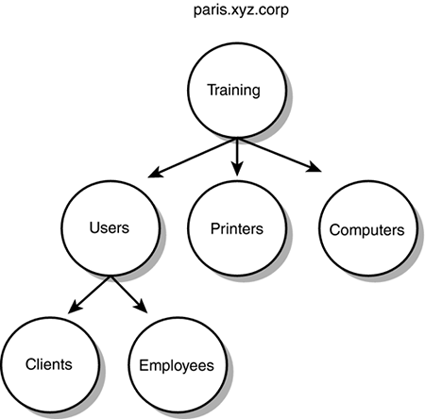
Inheritance and Inheritance ModificationPermissions in Active Directory are typically inherited from parent container to child container. This behavior is appropriate in most circumstances. However, sometimes a child object must be managed independently of the parent. In such a case, use inheritance modification to override the default inheritance rules. InheritanceInheritance in Active Directory enables permissions that have been set on a parent container to apply to the child containers within the hierarchy. It is the same idea as folder and file permissions: When you set permissions on a folder, you have the option of specifying whether those permissions should apply to the subfolder and files beneath it. The permissions only have to be set once, thus simplifying the process of administration. With inheritance, a user or group can be assigned permission to a container and all the objects it contains. Permissions can be set once on a container, as opposed to having to set the permissions on each individual object, and they can save administrators a lot of time and effort. For example, within the paris .xyz.corp domain shown in Figure 5.15, an OU has been created for the training department (parent object). Child objects have been created within the Training OU for administrative purposes. If a group of users in the Paris domain need administrative privileges over the Training OU and all its child objects, permissions need to be set only once as a result of inheritance. Figure 5.15. Using inheritance, permissions can be set once on the parent object and applied to the child objects.
Inheritance ModificationConversely, if you do not want permissions to apply to all the child objects within a parent object, you can modify inheritance. Using inheritance modification, you can specify which child objects should inherit permissions and which ones should not. Using the example in Figure 5.15, if it is determined that the Full Control permission set on the Training OU should not apply to the Clients OU, inheritance modification could be used to block it. Blocking inheritance is as simple as clearing the Allow Inheritable Permissions from Parent to Propagate to This Object check box. Use the following steps to block inheritance on a child object:
Designing an Organizational Unit Hierarchy for DelegationOUs are created in a domain to logically group objects for administrative purposes. After OUs are created, a user or group can be assigned the task of administering the objects contained within. Creating OUs enables you to limit the scope of administrators' control and provides a finer granularity of control when assigning administrative rights and permissions to other individuals and groups. The OU structure that is designed should be relative to the way administration is currently dispersed throughout the business; it is also dependent on how the administrative tasks are delegated. Here are some questions to keep in mind:
The OU structure that's designed should be based on the current delegation of tasks. For example, if the XYZ Corporation has divided the administrative tasks into different job roles, this should be reflected in the OU structure implemented (see Figure 5.16). This enables the corporation to continue with its current strategy of distributing administrative authority. Figure 5.16. The OU hierarchy should represent the current strategy for assigning administrative authority. Because the XYZ Corporation divides the administrative tasks into separate roles, OUs can be created for each of the roles. The individual or group responsible for an administrative role can be assigned delegation of control over the appropriate OU. When you're designing the OU hierarchy, keep in mind that the structure should allow the business to continue to use the same strategy of assigning administrative control that it's currently using. One of the important features of using OUs is that they can be nested within one another, which becomes a benefit when delegating control. Objects in one OU can be subdivided in child OUs. Referring to the Paris domain in Figure 5.15, a hierarchy of OUs is created by nesting the OUs within one another. You might be asking yourself why you would want to do this, but it makes perfect sense for delegating authority. If an OU is created to hold all user accounts, you might not want to assign one user or group control over all of them. In this case, you can divide the user accounts into child OUs (Clients and Employees), which would be contained in the parent OU (Users). This way, a user or group can be assigned administrative permissions over certain user accounts without having control over all of them.
Design GuidelinesWhen designing Active Directory for delegation, keep the following guidelines in mind:
|
EAN: 2147483647
Pages: 148