VPN Topologies
| All VPNs have a few basic components in common:
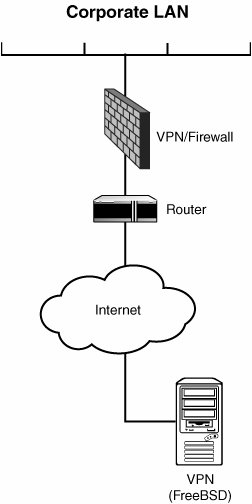
The details of these configurations, however, can vary quite a lot. Figure 31.3 shows the kind of topology likely to be used by employees on the road. A single machine uses a standard dial-up ISP (such as found in a hotel or an airport) to connect to the Internet. This machine then contacts the corporate VPN server, which has an IP address that's not translated and is therefore accessible directly from the Internet. This VPN server performs the necessary authentication and serves up the client's tunnel IP address, allowing it to communicate with the machines inside the NAT network. Figure 31.3. A single client machine connects to the Internet and communicates directly with the corporate VPN server to set up a tunnel. A more ambitious layout is shown in Figure 31.4. Here, the VPN client is actually a FreeBSD machine serving as a NAT gateway and firewall for a home (local) network, the kind likely to be used by an employee who frequently works from home. The FreeBSD machine creates a permanent tunnel to the private network over the Internet but is itself operating as a router managing a network of machines of various types. Each of these machines has the VPN client machine set as its gateway router; if one of the machines tries to open up a connection to the private network, the FreeBSD machine will have a permanent route (the VPN tunnel) into which to send the connection. Normal requests to the Internet will be passed upstream to the regular ISP's router, unaltered. The machines on the local network do not need to undergo any special configuration in order to interoperate seamlessly with the machines at the corporate site. This topology enables large companies to maintain multiple branch offices in widely separate locations around the country or the world, while at the same time allowing employees at any location to access the resources at any other location as though they are all plugged into the same switch at the central office. Figure 31.4. Two networks are connected by a permanent VPN tunnel; the machines on either network can now all freely communicate with each other with no additional configuration on the individual machines. The same principles underlie both the simple and the more complex topologies just described. Next in this chapter, you learn the techniques for putting these principles into action. First, we look at how to configure FreeBSD as a VPN client to connect to a remote VPN server, regardless of whether your topology involves a local network. Afterward, you learn how to create a VPN server so other machines can tunnel into your own private network. |