Lesson 3: Analyzing Security Configurations
|
| < Day Day Up > |
|
Over time, security configurations degrade unless they are maintained. When new vulnerabilities are discovered, updates must be applied to protect against attacks. When administrators troubleshoot problems, they might leave a computer in a less secure state than it was in when they began the troubleshooting. Fortunately, Microsoft provides tools to analyze Windows Server 2003 and other recent Windows operating systems for potential security vulnerabilities. This lesson will cover the most important tools for analyzing security configurations.
After this lesson, you will be able to
-
Use the Security Configuration And Analysis tool to determine what active computer settings do not meet those specified by a security template.
-
Use the Microsoft Baseline Security Analyzer (MBSA) to identify potential security vulnerabilities in Windows Server 2003 and other recent versions of Windows.
-
Use the MBSA command-line interface to create an Extensible Markup Language (XML) file containing detailed information about a computer’s potential security vulnerabilities.
Estimated lesson time: 30 minutes
Security Configuration And Analysis
The Security Configuration And Analysis snap-in gives you an immediate, detailed list of security settings on a computer that do not meet your security requirements. Recommendations are presented alongside current system settings, and icons or remarks are used to highlight any areas where the current settings do not match the proposed level of security. Security Configuration And Analysis uses a database to perform analysis and configuration functions. Using a database gives you the ability to compare the current security settings against custom databases that are created by importing one or more security templates.
To analyze a computer’s security settings by comparing it to a security template:
-
Create a new Microsoft Management Console (MMC) console, and add the Security Configuration And Analysis snap-in.
-
Right-click Security Configuration And Analysis, and then click Open Database.
-
In the Open Database dialog box, type a name for the new database, and then click Open.
-
In the Import Template dialog box, select a security template to import. Click Open.
-
If you want to import more than one security template, right-click Security Configuration And Analysis, and then click Import Template. Select the template to import, and then click Open. Repeat this process for each security template you want to import.
-
Right-click Security Configuration And Analysis, and then click Analyze Computer Now.
-
In the Perform Analysis dialog box, click OK.
After the analysis is complete, examine the results by expanding the nodes contained within the Security Configuration And Analysis node.
You can also apply security settings by using the Security Configuration And Analysis tool, though it is generally more effective to apply security settings by using GPOs. To apply settings from one or more security templates to a computer:
-
Create a new MMC console, and add the Security Configuration And Analysis snap-in.
-
Right-click Security Configuration And Analysis, and then click Open Database.
-
In the Open Database dialog box, type a name for the new database, and then click Open.
-
In the Import Template dialog box, select a security template to import. Click Open.
-
If you want to import more than one security template, right-click Security Configuration And Analysis, and then click Import Template. Select the template to import, and then click Open. Repeat this process for each security template you want to import.
-
Right-click Security Configuration And Analysis, and then click Configure Computer Now.
-
In the Configure System dialog box, click OK.
The best way to familiarize yourself with what the Security Configuration And Analysis snap-in can do is to use the tool. Exercise 2 in this lesson guides you through the process of analyzing a test computer’s security configuration.
Microsoft Baseline Security Analyzer—Graphical Interface
MBSA includes graphical and command-line interfaces that can perform local or remote scans of Windows systems. MBSA runs on computers running Windows 2000, Windows XP, and Windows Server 2003 and will scan for common system misconfigurations in Microsoft Windows NT 4.0, Windows 2000, Windows XP, Windows Server 2003, IIS 4.0 and 5.0, SQL Server 7.0 and SQL Server 2000, Internet Explorer 5.01 and later, and Office 2000 and Office XP. MBSA will also scan for missing security updates for the following products: Windows NT 4.0, Windows 2000, Windows XP, Windows Server 2003, IIS 4.0 and 5.0, SQL Server 7.0 and SQL Server 2000, Internet Explorer 5.01 and later, Exchange Server 5.5 and Exchange 2000 Server, and Microsoft Windows Media Player 6.4 and later.
MBSA can determine which critical security updates are applied to a system by referring to an XML file that is continuously updated by Microsoft. The XML file contains information about which security updates are available for particular Microsoft products. This file contains security bulletin names and titles, and detailed data about product-specific security updates, including the files in each update package and their versions and checksums, registry keys that were applied by the update installation package, information about which updates supersede others, related Microsoft Knowledge Base article numbers, and much more.
When you run MBSA for the first time, it will automatically download a copy of this XML file so that the tool can find the security updates that are available for each product. However, you must be connected to the Internet for this download to be successful. MBSA downloads the XML file in a compressed, digitally signed .cab file, verifies the signature, and then decompresses the file to the local computer on which MBSA is running. After you run MBSA, it displays a detailed list of potential vulnerabilities, as shown in Figure 4.12.
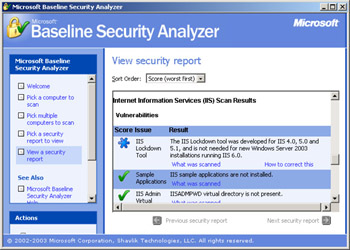
Figure 4.12: Microsoft Baseline Security Analyzer IIS results
| See Also | To download MBSA and read more about it, visit http://www.microsoft.com/technet/security/tools/mbsahome.asp. |
Microsoft Baseline Security Analyzer—Command-Line Interface
Always use the MBSA graphical interface when manually scanning a system. However, if you administer more than a handful of systems, you will want to be able to automate security analysis by using scripts. Fortunately, MBSA provides a command-line interface named Mbsacli that is specifically designed to be used within a script.
Mbsacli is automatically installed with MBSA, but it is not added to the default path. To run the program, you must open a command prompt and switch to the directory into which you installed MBSA. By default, this path is C:\Program Files\Microsoft Baseline Security Analyzer.
One of the most useful features of Mbsacli is to create an XML file containing the results of an MBSA scan. Although you can use a recent Web browser to view the XML file, they are rather difficult for a human to read. They are more useful when a developer, or an administrator with scripting skills, creates a program that parses and analyzes them. You can use this functionality to integrate MBSA data into your organization’s custom management tools.
To scan all computers in the 192.168.1.0 network, run the following command from the C:\Program Files\Microsoft Baseline Security Analyzer directory:
Mbsacli –r 192.168.1.1-192.168.1.254
For a complete description of Mbsacli command-line options, run Mbsacli /? from a command line.
| Note | Mbsacli is a replacement for Hfnetchk. Mbsacli supports an Hfnetchk mode when used with the /hf parameter. |
Practice: Analyzing Security Configurations
In this practice, you will use MBSA and the Security Configuration And Analysis snap- in to analyze the security settings of a computer and identify potentially insufficient policies.
Exercise 1: Scan a computer with MBSA
In this exercise, you will use MBSA to scan a computer. You should have Internet connectivity to take advantage of all of the features of MBSA, but, for security reasons, do not connect the test systems running Windows Server 2003 to the Internet. Instead, download and install MBSA on an existing Internet-connected computer with Windows 2000, Windows XP, or Windows Server 2003.
-
Start the Microsoft Baseline Security Analyzer tool.
-
Click Scan More Than One Computer.
-
On the Pick Multiple Computers To Scan page, examine the settings. Note that you can choose to scan an entire domain, or you can scan by using an IP address range.
-
In the left pane, click Welcome.
-
Click Scan A Computer.
-
On the Pick A Computer To Scan page, select the local Internet-connected computer.
Note the scanning options that you can select, including checking for known vulnerabilities in Windows, IIS, or SQL Server, checking for weak passwords, and checking for security updates that haven’t been applied. By default, the Use SUS option is not selected. When selected, you can use a Software Update Server (SUS) to determine which security updates need to be applied to the computer.
See Also For more information on SUS, refer to Chapter 5, “Planning an Update Management Infrastructure,” and Chapter 6, “Assessing and Deploying an Update Management Infrastructure.”
-
Click Start Scan.
-
MBSA might take several minutes to scan your computer.
-
The View Security Report page appears. Examine the results for your computer.
If you haven’t scanned this computer with MBSA previously, you almost certainly have failed some critical checks, which will be marked with a red X. For each of these line items, click Result Details to identify exactly what was missing and to read more information on how to resolve the problem.
Exercise 2: Analyze a computer with Security Configuration and Analysis
In this exercise, you will analyze Computer1’s security settings by using the Security Configuration And Analysis snap-in.
-
Log on to the cohowinery.com domain on Computer1 using the Administrator account.
-
Create a new MMC console, and add the Security Configuration And Analysis snap-in.
-
Right-click Security Configuration And Analysis, and then click Open Database.
-
In the Open Database dialog box, type newdb, and then click Open.
-
In the Import Template dialog box, select C:\Windows\Security\Templates\ Hisecdc.inf. Click Open.
-
Right-click Security Configuration And Analysis, and then click Analyze Computer Now.
-
In the Perform Analysis dialog box, click OK.
-
Expand Security Configuration And Analysis, and then expand Account Policies.
-
Click Password Policy.
-
Notice the policies listed in the right pane. The policies that do not meet or exceed the settings specified in the Hisecdc.inf security template are marked with a red X, as shown in Figure 4.13.
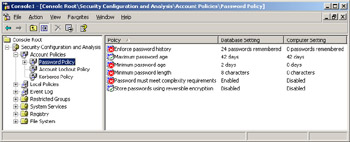
Figure 4.13: Security Configuration And Analysis identifying deficient settings
Lesson Review
The following questions are intended to reinforce key information presented in this lesson. If you are unable to answer a question, review the lesson materials and try the question again. You can find answers to the questions in the “Questions and Answers” section at the end of this chapter.
-
Which command would cause Mbsacli to analyze all computers on the network 10.236.122.0/24 subnet?
-
mbsacli /r 10.236.122.1-10.236.122.254
-
mbsacli /i 10.236.122.0/24
-
mbsacli /r 10.236.122.0
-
mbsacli /i 10.236.122.0 255.255.255.0
-
-
Which of the following functions can be performed with the Security Configuration And Analysis console? (Choose all that apply.)
-
Create an XML file containing a summary of a computer’s security settings.
-
Compare the current configuration settings against a security template.
-
Identify which GPO is responsible for a specific policy setting.
-
Apply a security template to the local computer.
-
Lesson Summary
-
The Security Configuration And Analysis console can be used to apply settings from a security template. However, it is more commonly used to determine which active security settings do not match those specified in a security template.
-
MBSA identifies potential security vulnerabilities, including critical updates that have not been applied, on one or more systems.
-
Mbsacli provides a command-line interface with functionality that is similar to that of MBSA. Mbsacli can be used to create XML files that summarize security vulnerabilities on one or more systems.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 217
- ERP Systems Impact on Organizations
- ERP System Acquisition: A Process Model and Results From an Austrian Survey
- The Effects of an Enterprise Resource Planning System (ERP) Implementation on Job Characteristics – A Study using the Hackman and Oldham Job Characteristics Model
- Relevance and Micro-Relevance for the Professional as Determinants of IT-Diffusion and IT-Use in Healthcare
- Development of Interactive Web Sites to Enhance Police/Community Relations
- Chapter II Information Search on the Internet: A Causal Model
- Chapter IV How Consumers Think About Interactive Aspects of Web Advertising
- Chapter VI Web Site Quality and Usability in E-Commerce
- Chapter VII Objective and Perceived Complexity and Their Impacts on Internet Communication
- Chapter XII Web Design and E-Commerce